- Home
- Logging Guide
- Comparing inbound and outbound firewall rules
Comparing inbound and outbound firewall rules
In this page
- What is inbound traffic?
- What is outbound traffic?
- Inbound firewall rules and configuration tips
- Outbound firewall rules and configuration tips
Every organization should carefully configure its firewall rules to monitor the incoming and outgoing network traffic and to minimize the risk of falling victim to attacks.
In order to manage inbound and outbound firewall rules effectively, it is important to understand the difference between inbound and outbound traffic.
What is inbound traffic?
Traffic that doesn't originate from within your network but wants to enter the perimeter of your network is inbound traffic. This traffic can be directed from a web browser, an email client, an application requesting for a service like FTP or SSH, etc to your network.
What is outbound traffic?
Contrary to inbound traffic, outbound traffic originates from within your network. This traffic is from your network users to access websites, and other resources that fall outside your network perimeter.
What are inbound firewall rules?
- Inbound firewall rules protect your network by blocking the traffic from known malicious sources and thereby prevent malware attacks, DDoS attacks, and more.
- Malicious traffic can be blocked based on ports, type of traffic, or IP addresses.
Tips to configure inbound firewall rules:
- Always check the origin of traffic—source IP, the country from which it's originating, does it emerge from a single source or multiple sources, which ports they request access to and so on.
- Write an inbound rule to deny any kind of access to malicious IPs.
- Make use of threat intelligence feeds to find out if an IP is malicious or not.
- Check if the malicious IP has targeted any application on a device connected to your network by performing port scanning or detecting anomalies occurring in applications that contain vital information.
- Ensure that the host-level firewall is configured in critical servers and databases containing sensitive information so that any type of deviant communication through vulnerable ports is blocked in particular hosts. This is to reinforce security at the intranet level if the attacker is an insider.
What are outbound firewall rules?
- Outbound firewall rules are firewall policies that define the traffic allowed to leave your network through secured ports to reach legitimate destinations.
- They stop requests sent to malicious websites and untrusted domains.
- Configuring outbound firewall rules can prevent data exfiltration.
- Outbound firewall rules can be fine-tuned to analyze the contents of emails or files containing sensitive information that are sent from your network.
- They closely monitor transmission protocols like Internet Message Access Protocol (IMAP), Post Office Protocol Version 3 (POP3) and Simple Mail Transfer Protocol (SMTP).
Tips to configure outbound firewall rules:
- Always monitor the traffic that leaves your network. Get to know the source of the outbound traffic.
- Check if the destination of traffic is known to be malicious.
Regularly monitor the traffic going out of your network. Baseline the normal behavior pattern and set up alerts in your security solution to notify about any unusual spike in the volume of traffic, or data that goes out of your network.
A typical firewall should regulate both inbound and outbound traffic by employing both inbound and outbound firewall rules. Any changes to these rules can cause chaos within the network. Therefore, it's essential to monitor the changes happening to these rules and ascertain if they are legitimate.
EventLog Analyzer, a comprehensive log management solution helps you to monitor the changes happening to these firewall rules and other firewall configurations in real-time. Get detailed reports on who made the change, when it was it made, and from where to ascertain its legitimacy. Further, get instant email and SMS notification for any unauthorized changes. Click here to learn more about the solution.
Leverage firewall features with EventLog Analyzer for secure network defense
ManageEngine EventLog Analyzer enhances the firewall features by integrating centralized log management, real-time monitoring, advanced log analysis and threat detection capabilities. It compiles and combines firewall logs in one place, enabling thorough monitoring and analysis.
- Streamline firewall log audits
- Monitor firewall traffic
- Audit firewall VPN logs
- Get real-time alerts
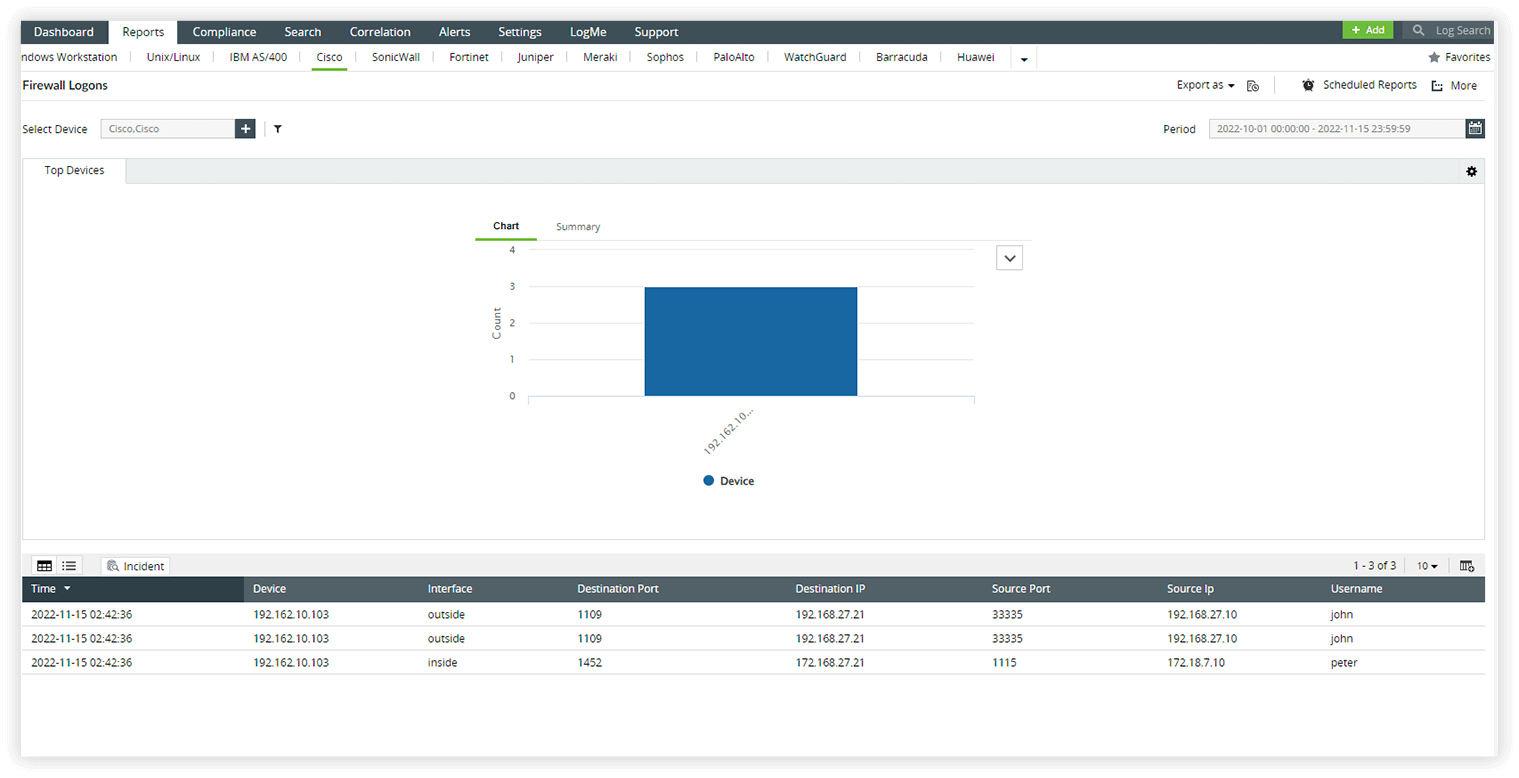
- Simplify log management by automatically collecting and analyzing logs from firewall vendors like Sophos, Barracuda, Cisco, Check Point, Juniper, and more.
- Monitor logon and logoff events, configuration changes, and user privileges to enhance security.
- Strengthen access control by closely monitoring firewall logs and proactively identifying security risks.
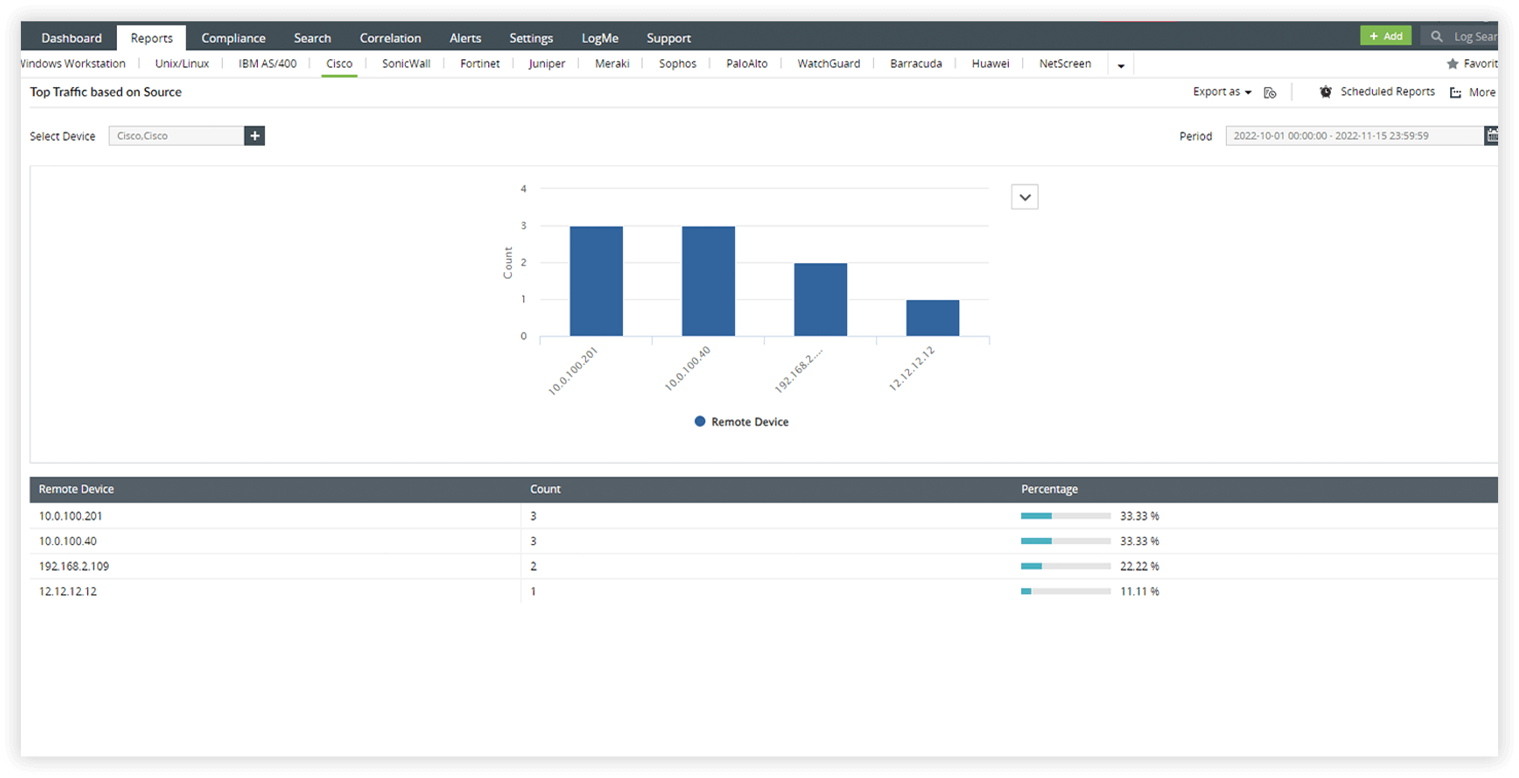
- Gain insights into denied connections by users, servers, and firewall traffic through intuitive reports.
- Detect highly active hosts and external threats with real-time alerts and detailed reports on Firewall Denied Traffic.
- Uncover unsafe applications, suspicious users, and network anomalies using individual user action alerts and category-based trend reports.
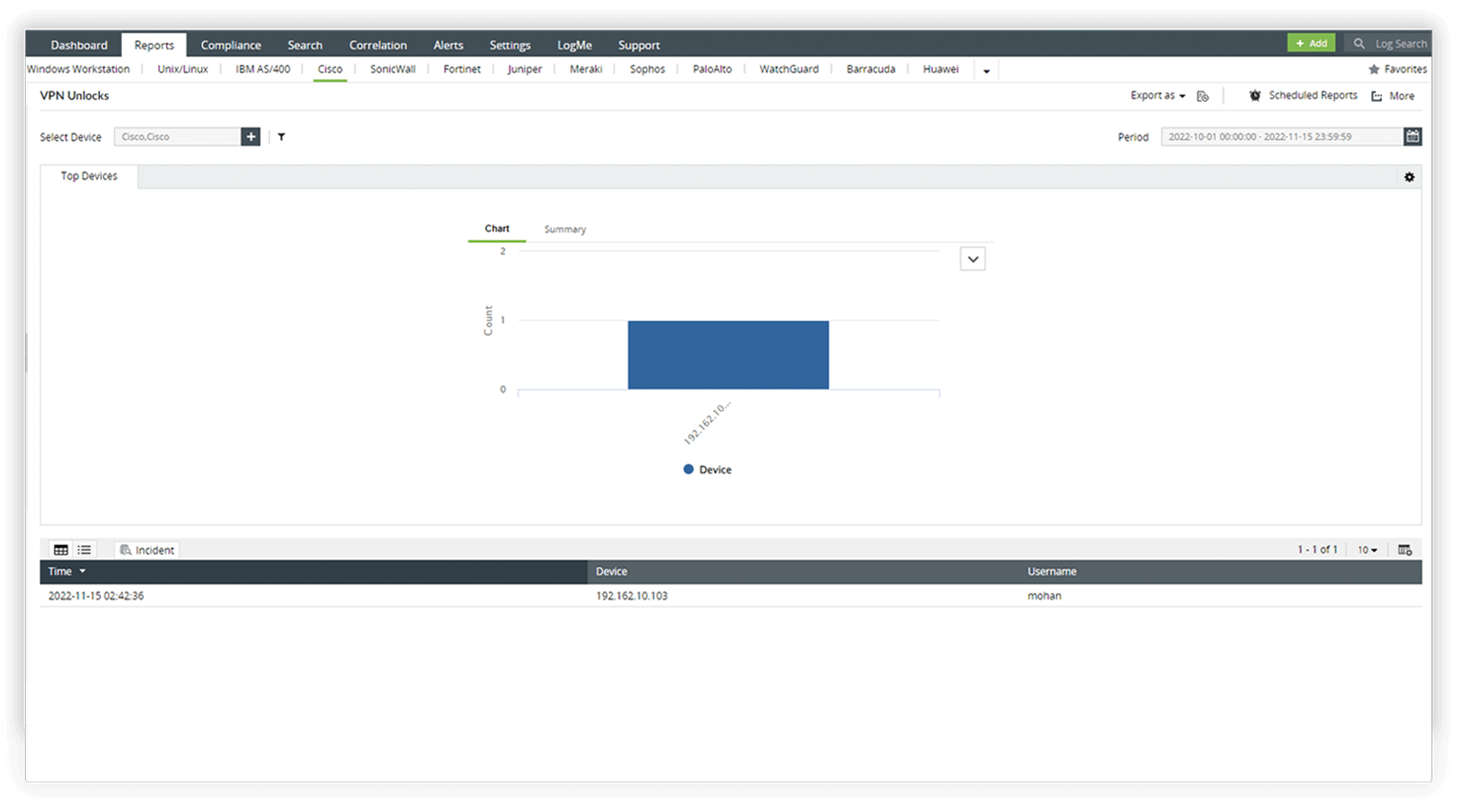
- Monitor important VPN activities such as lockouts, subsequent unlocks, and other firewall VPN activities.
- Conduct reviews of VPN user details, performs audits on VPN logins, and analyzes login patterns to identify trends.
- Ensure secure VPN usage through comprehensive monitoring, user audits, and analysis of login patterns.
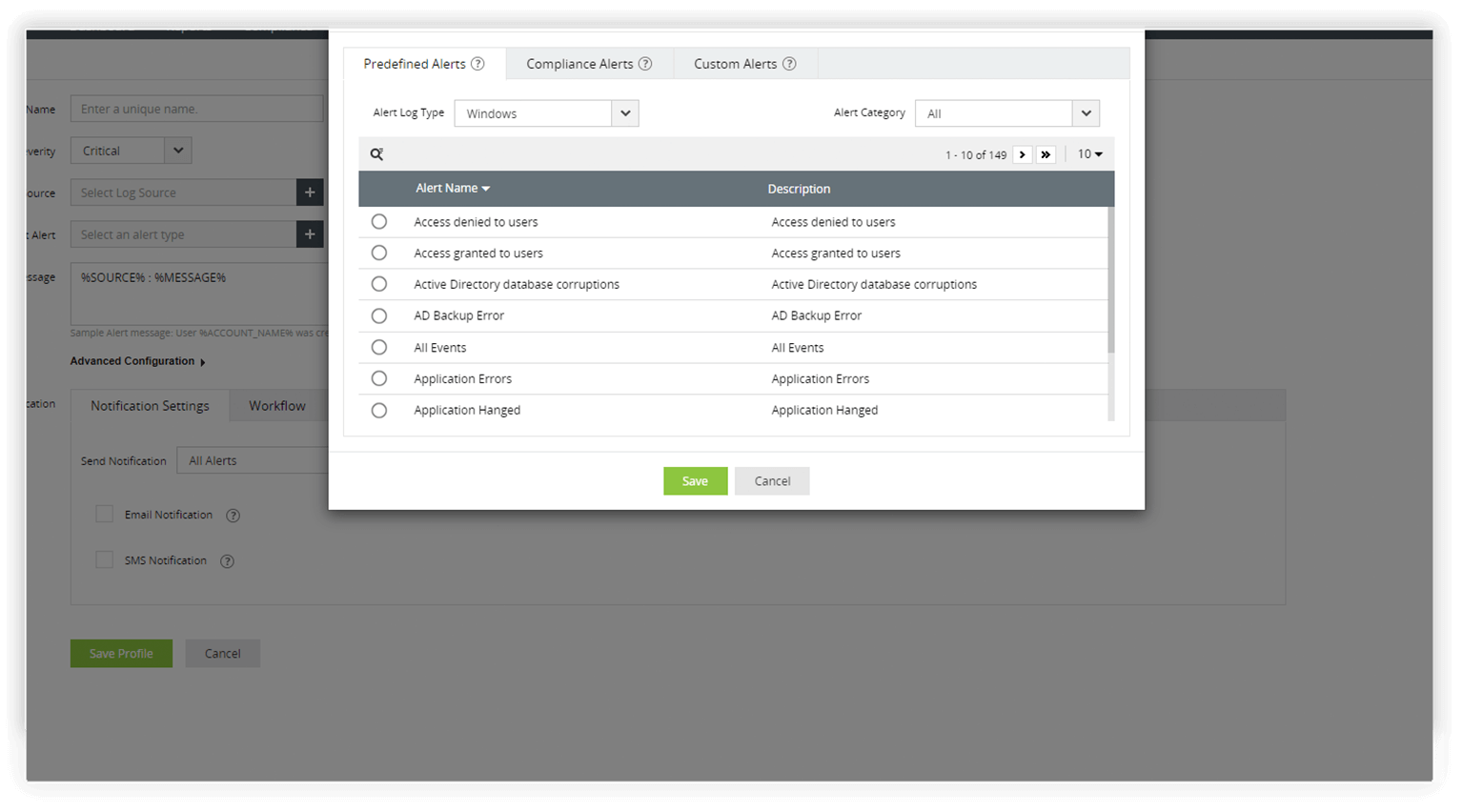
- Take control of your firewall security with EventLog Analyzer's correlation rules which detect complex attack patterns.
- Gain instant alerts when a suspicious activity is detected. You can also use the predefined workflows in the solution to act as the first response to any attack.











