- Home
- Logging Guide
- Structured logging
The complete guide to structured logging: Enhancing security visibility
In this page
- Why do we need logging?
- What are the different types of logging?
- What are the elements of a structured log data?
- What are the best practices for structured logging?
- How to leverage EventLog Analyzer for structured logging
When it comes to detecting and responding to security incidents, the first thing you will hear any IT technician say is, "Send me the logs." Logs are an invaluable asset and play a crucial role in monitoring and analyzing the overall security posture and performance of an application or an organization's IT infrastructure. They provide a detailed record of system events, user activities, network traffic, and application behavior, offering insights into potential threats or unauthorized access attempts. While organizations have historically relied on traditional logging, this approach offers limited visibility, consumes time, and complicates the process of understanding network events. This is where structured logging can help.
Read on to know more about structured logging, its best practices, and more to revolutionize the way you capture and analyze log data.
Why do we need logging?
Logging is a fundamental and essential aspect of cybersecurity which helps to enhance security in an organization. It aids in processes such as spotting anomalies, suspicious user behavior, and security incidents; intrusion detection and prevention; malware analysis; and so on. It also allows developers and system administrators to gain insights into application behavior, detect issues, and diagnose problems effectively.
What are the different types of logging?
There are three different types of logs: structured, unstructured, and semi-structured. They differ in their format and system of data organization. Let us take a closer look at each log type:
1. Structured logs:
Structured logging involves capturing log messages in a standardized format, using a predefined schema or format such as JSON or XML. While traditional logs are generally unformatted plain text messages, structured logs store data in a machine-readable manner, which improves its readability and searchability, eases analysis, and enables better integration with other tools and systems. Here's an example of a structured log:
{ "timestamp": "2023-06-22 12:34:56",
"level": "INFO",
"message": "User logged in",
"user_id": "steve_rogers",
"source": "login-service"
}
2. Unstructured logs:
Unstructured logs do not follow a specific format or schema, unlike structured logging. They often consist of plain text messages as logs without a standardized format. Unstructured logs can contain valuable information, but are harder to parse and analyze. They may require manual parsing techniques, such as regular expressions, to extract relevant information. For example:
2023-06-22 12:34:56 INFO: User logged in [User ID: 12345]
3. Semi-structured logs:
Semi-structured logs, as the name suggests, are a combination of structured and unstructured logs. They have some level of organization, but may lack a fully defined format. Semi-structured logs contain key-value pairs, tags, or metadata within the log message. While they may not have a proper structure like structured logs, they still provide some level of parsing and analysis capability, compared to unstructured logs. For example:
2023-06-22T12:34:56.789Z [INFO] [login-service]: User logged in {User ID: 12345}
While structured logs have a predefined format, unstructured logs lack a standardized structure, and semi-structured logs fall someplace in between, offering partial organization or metadata within log entries. It is important to note that the choice of the log format depends on the specific requirements of the application.
What are the elements of a structured log data?
Log data or entries are individual records of captured events or messages, following a specific format. A typical log entry comprises several elements and it can vary based on the application, system, or logging framework. Here are some common elements that are generally included in a structured log entry:
- Timestamp is an indication of the date and time of the log entry. It allows admins to understand the flow of events and pinpoint when an event took place.
- Log level is the categorization of log entries based on their significance. It aids the filtering process and helps users differentiate amongst informational messages, warnings, errors, and critical issues. Here are some of the commonly used log levels:
- DEBUG is used for detailed information during development and debugging processes. This level is typically suited for developers.
- INFO is used to notify any information about the system's behavior, such as startup messages, configuration details, or other important events.
- WARNING indicates potential issues or situations that might require attention. This level highlights conditions that may lead to an error when unattended.
- ERROR indicates specific errors that occurred during the application's execution that need investigation or intervention, but does not necessarily cause the application to stop functioning.
- CRITICAL indicates severe errors or failures that require immediate attention and is used when the application ceases to function or is impacting the overall system stability.
- Log message is the actual information or description of the log data. It contains relevant details about what happened, errors that occurred, or other relevant information.
- Log source or logger name indicates the source that generated the log entry. It helps identify log entries generated from different parts of the system.
- Log context is the additional information that is included in the log entry, such as user IDs, request IDs, session IDs, or other relevant metadata. It provides a better picture of the event and helps in debugging and troubleshooting.
- Stack trace or exception details are usually included in case of an error or exception log. These help in root cause analysis by identifying the code path and the exact location where an error has occurred.
- Log ID or correlation ID may be included to track and correlate logs across different components or services in distributed systems or microservices architectures. It helps admins identify related logs and understand the flow of events across the system.
- Log contextual tags or labels are allowed by some logging frameworks to provide additional information or categorization of logs, such as the module, component, or specific feature related to the event.
Log entries are customizable based on the application's requirements, the logging system used, and the information needed for analysis, troubleshooting, or compliance purposes.
What are the best practices for structured logging?
To create effective and meaningful structured log data, it is important to adhere to the standard best practices. Listed below are some of the recommended practices for structured logging:
- Craft meaningful log messages by providing concise and relevant information about the event or error being logged. This helps admins understand log entries and detect security events of interest at the earliest opportunity.
- Use appropriate log levels (e.g., DEBUG, INFO, WARNING, ERROR) to indicate the severity and importance of every log entry and to ensure consistency and effective log filtering.
- Avoid sensitive or personally identifiable information (PII) like passwords, credit card details, or personal information to ensure that your logging mechanism does not accidentally store sensitive information.
- Implement a centralized log analysis and storage system by leveraging log management tools to aggregate logs from multiple sources, perform real-time monitoring, and leverage advanced log analysis features for better insights and issue detection.
- Review and analyze logs regularly to help detect performance blocks and potential security breaches and identify areas for optimization or improvement.
By following these best practices, you can leverage the benefits of structured logging to enhance visibility, troubleshooting, and monitoring capabilities in your applications or systems.
How to leverage EventLog Analyzer for structured logging
ManageEngine EventLog Analyzer is a centralized log management and analysis tool that is designed to help organizations manage logs, detect security incidents, troubleshoot issues, and meet compliance requirements. You can leverage the following features of EventLog Analyzer for structured logging:
- Custom log parsing
- Correlation and contextual analysis
- Visualizations and dashboards
- Alerts and notifications
- Compliance and reporting
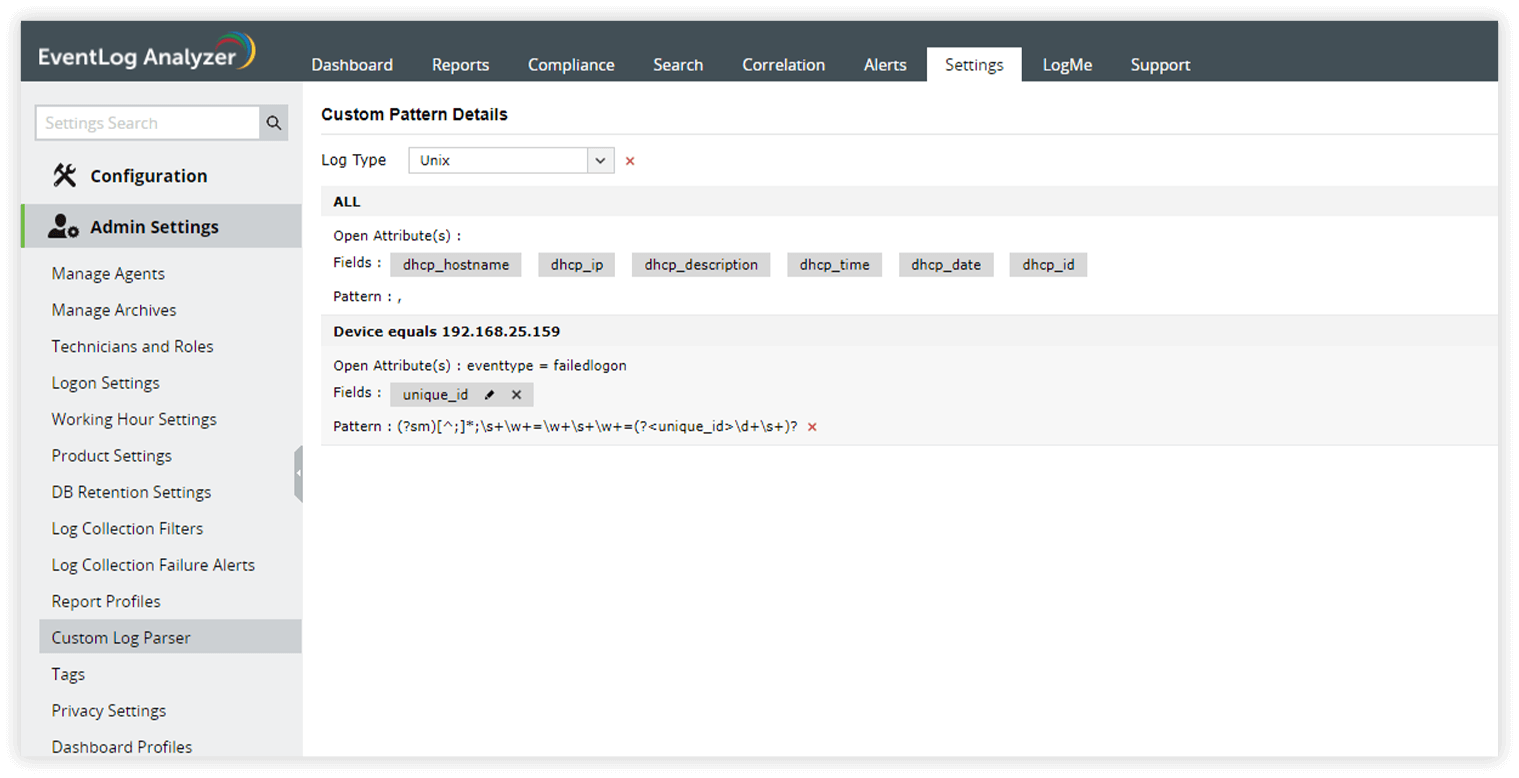
- Extract information from logs effectively, regardless of their format, and ensure consistency in the log data for streamlined analysis and correlation. In case the specific log format is not supported, create custom log parses using regular expression patterns.
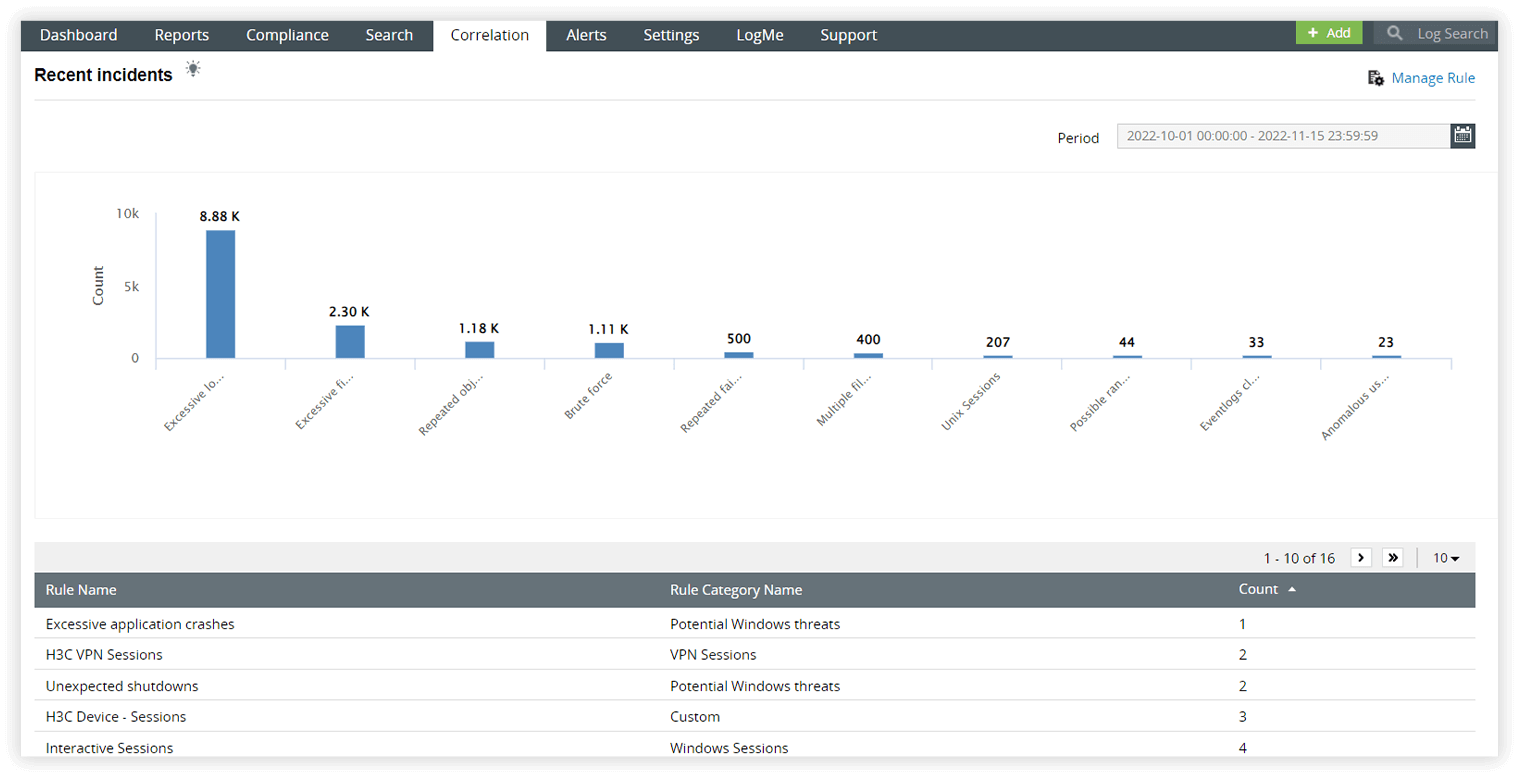
- Detect attack patterns across network devices and get prompt alerts to potential threats with correlation analysis. The intuitive rule builder interface empowers you to identify and respond to network attacks using the contextual information available in structured logs from related log entries.
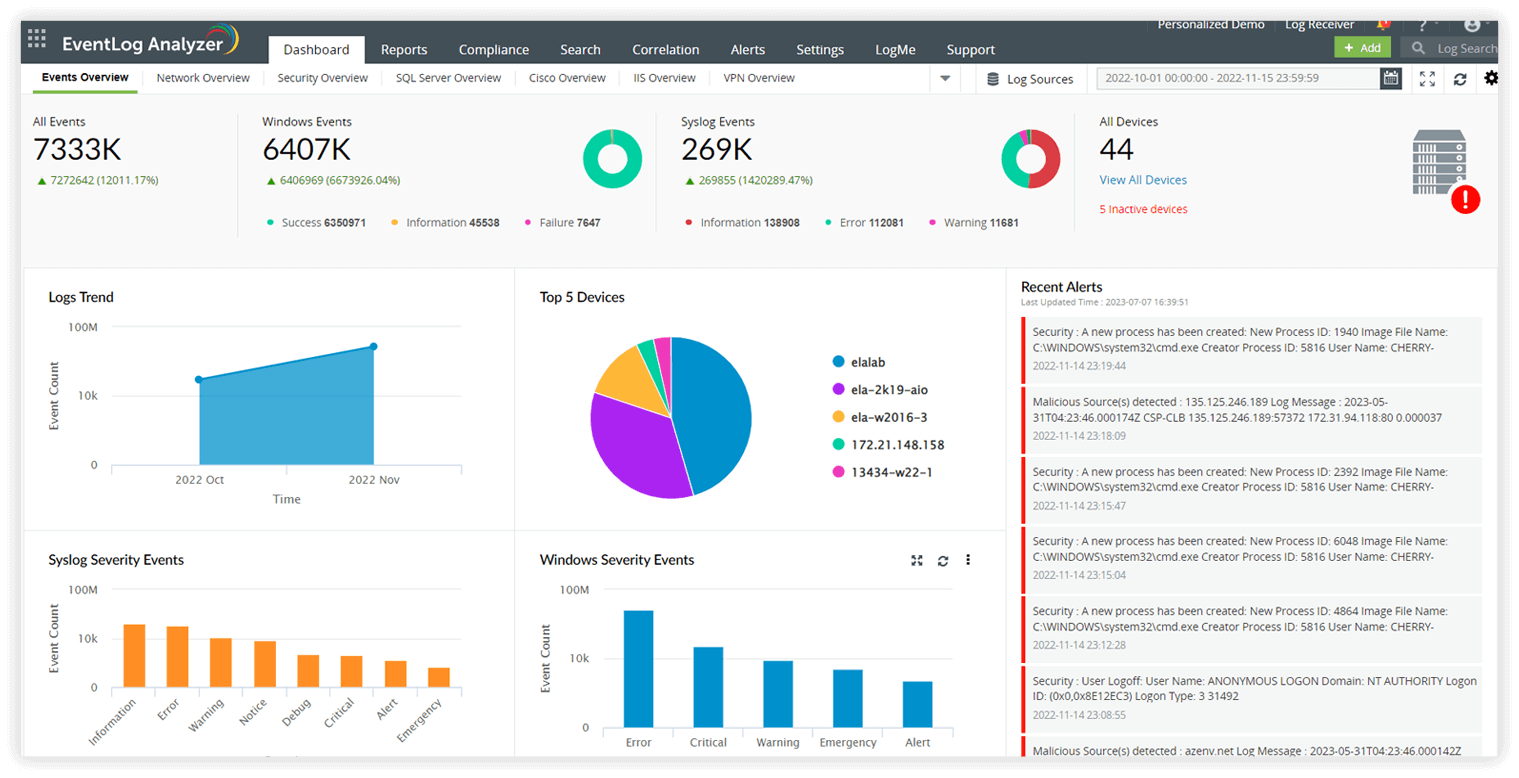
- Create meaningful charts, graphs, and dashboards based on the structured log data. Customize the dashboard to highlight important log metrics or trends, providing a clear overview of log events and facilitating quick analysis and decision-making.
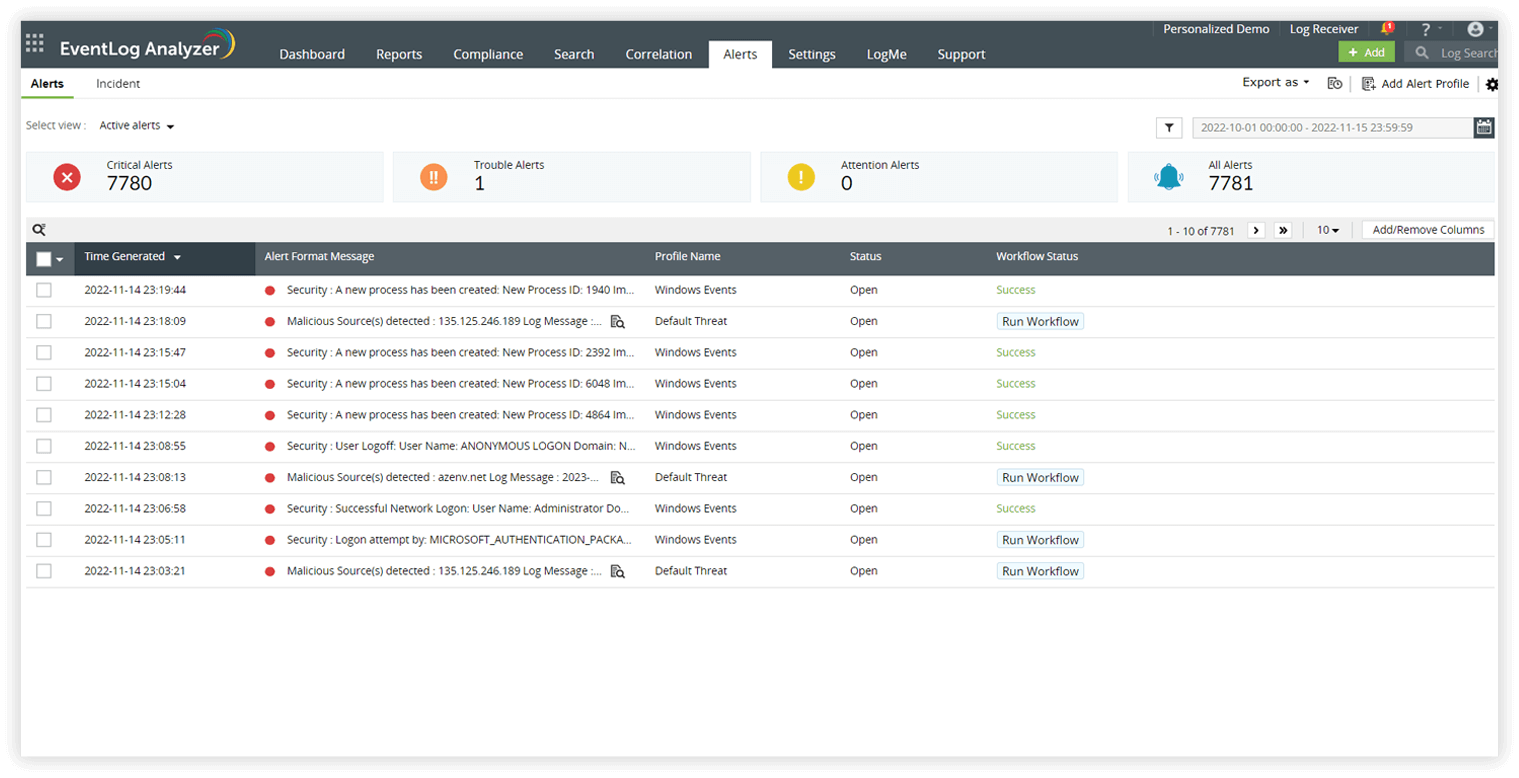
- Get real-time alerts and notifications for critical log events and security incidents via SMS or email based on specific conditions or events in the structured logs, allowing you to prioritize your alerts and resolve them promptly.
- Meet regulatory obligations by providing an audit event sequence and identifying areas of risk by collecting and analyzing event logs. Compliance reporting in EventLog Analyzer helps generate predefined compliance reports for regulations like the GDPR, PCI DSS, FISMA, and more.
ManageEngine's EventLog Analyzer can accurately extract and interpret data from log entries of all types. The solution correlates contextual information present in structured logs, allowing for in-depth analysis and troubleshooting. Leveraging EventLog Analyzer for structured logging enhances the efficiency of your log analysis, adds another layer to your network security, and facilitates compliance reporting in diverse IT environments.











