- Free Edition
- What's New?
- Quick Links
- Log Management
- Application Log Management
- Application log monitoring
- IIS log analyzer
- IIS web log analyzer
- IIS FTP log analyzer
- IIS log parser
- VMware log analyzer
- Hyper V event log auditing
- SQL database auditing
- SQL server auditing
- MySQL log analyzer
- Apache log analyzer
- DHCP server auditing
- Database activity monitoring
- Database auditing
- Oracle database auditing
- IT Compliance Auditing
- IT Compliance Auditing
- SOX Compliance Audit
- GDPR Compliance Audit
- ISO 27001 Compliance Audit
- HIPAA Compliance Audit
- PCI Compliance Audit
- FISMA Compliance Audit
- GLBA Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- CCPA Compliance Reports
- CCPA Compliance Software
- NERC Compliance Audit Reports
- Cyber Essentials Compliance Reports
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
- PDPA compliance audit reports
- CMMC Compliance Audit
- SIEM
- Security Information and Event Management (SIEM)
- Threat Intelligence
- STIX/TAXII feed processor
- Server Log Management
- Event Log Monitoring
- File Integrity Monitoring
- Linux File Integrity Monitoring
- Threat Whitelisting
- Advanced Threat Analytics
- Security Log Management
- Log Forensics
- Incident Management System
- Application log management
- Real-Time Event Correlation
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Linux Log Analyzer
- Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Cisco Logs Analyzer
- VPN log analyzer
- IDS/IPS log monitoring
- Solaris Device Auditing
- Monitoring user activity in routers
- Monitoring Router Traffic
- Switch Log Monitoring
- Arista Switch Log Monitoring
- Firewall Log Analyzer
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet log analyzer
- Endpoint Log Management
- System and User Monitoring Reports
- More Features
- Resources
- Product Info
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Auditing database activities is an important part of strengthening database security. This involves identifying vulnerabilities, such as default or weak login credentials, excessive user and group privileges, and unpatched databases. Attackers exploit such vulnerabilities to achieve their own goals, like privilege escalation, SQL injection, and DoS attacks. As a result, there is an increased need to audit important database activities for security and compliance reasons.
EventLog Analyzer provides a comprehensive MySQL database auditing solution that helps IT administrators implement better protection methods, detect suspicious activity early, and trigger appropriate responses.
Ensure database security with EventLog Analyzer
EventLog Analyzer is a comprehensive log management, auditing, and IT compliance management solution that automatically imports, analyzes, and generates reports on all types of MySQL logs.
MySQL log management
The first step in auditing MySQL databases is to collect their logs. EventLog Analyzer can automatically import and analyze logs from all server instances in the network.
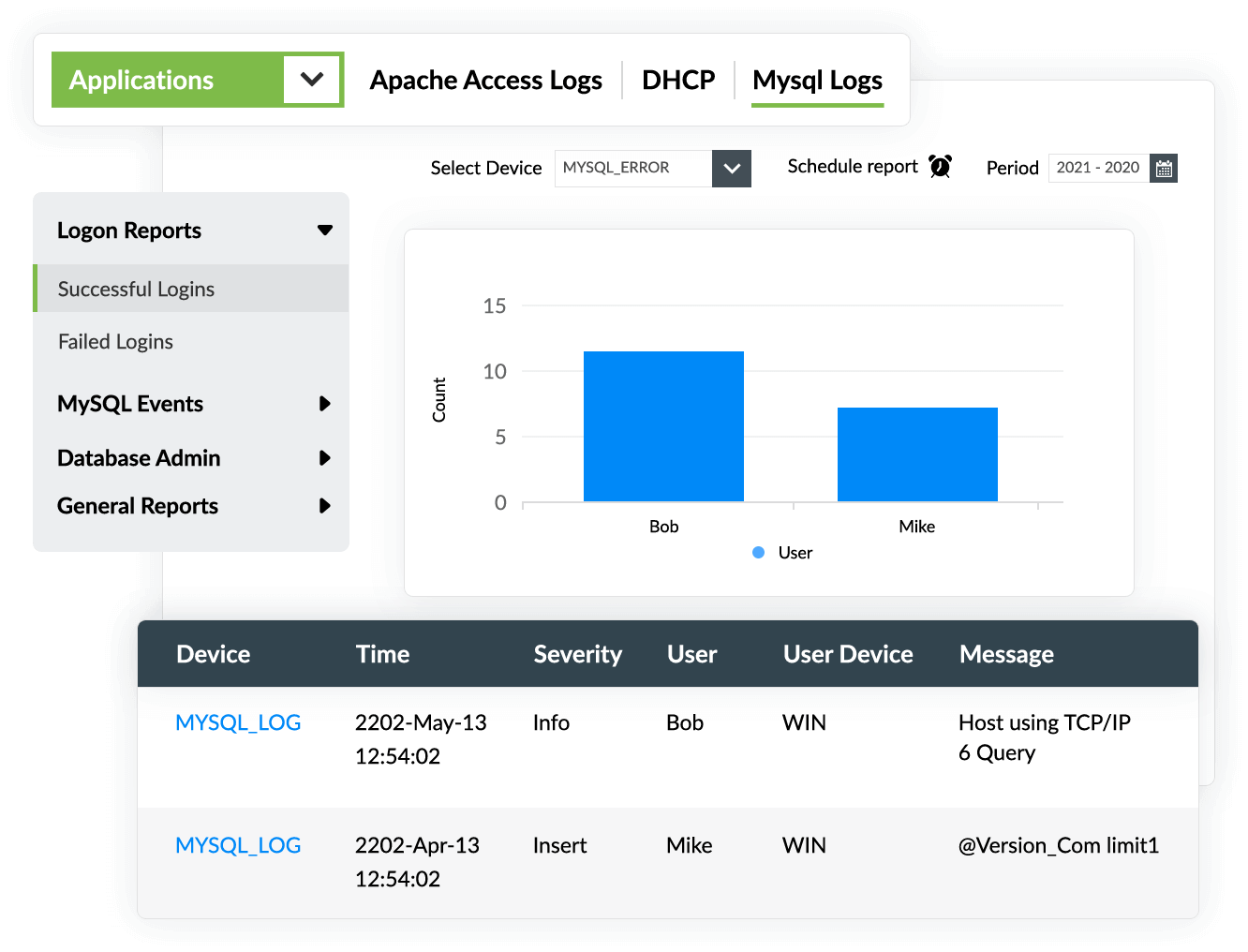
Out-of-the-box MySQL audit reports
EventLog Analyzer provides crucial audit reports that give detailed information on login events, general DDL and DML statements, server events, and database administrative statements.
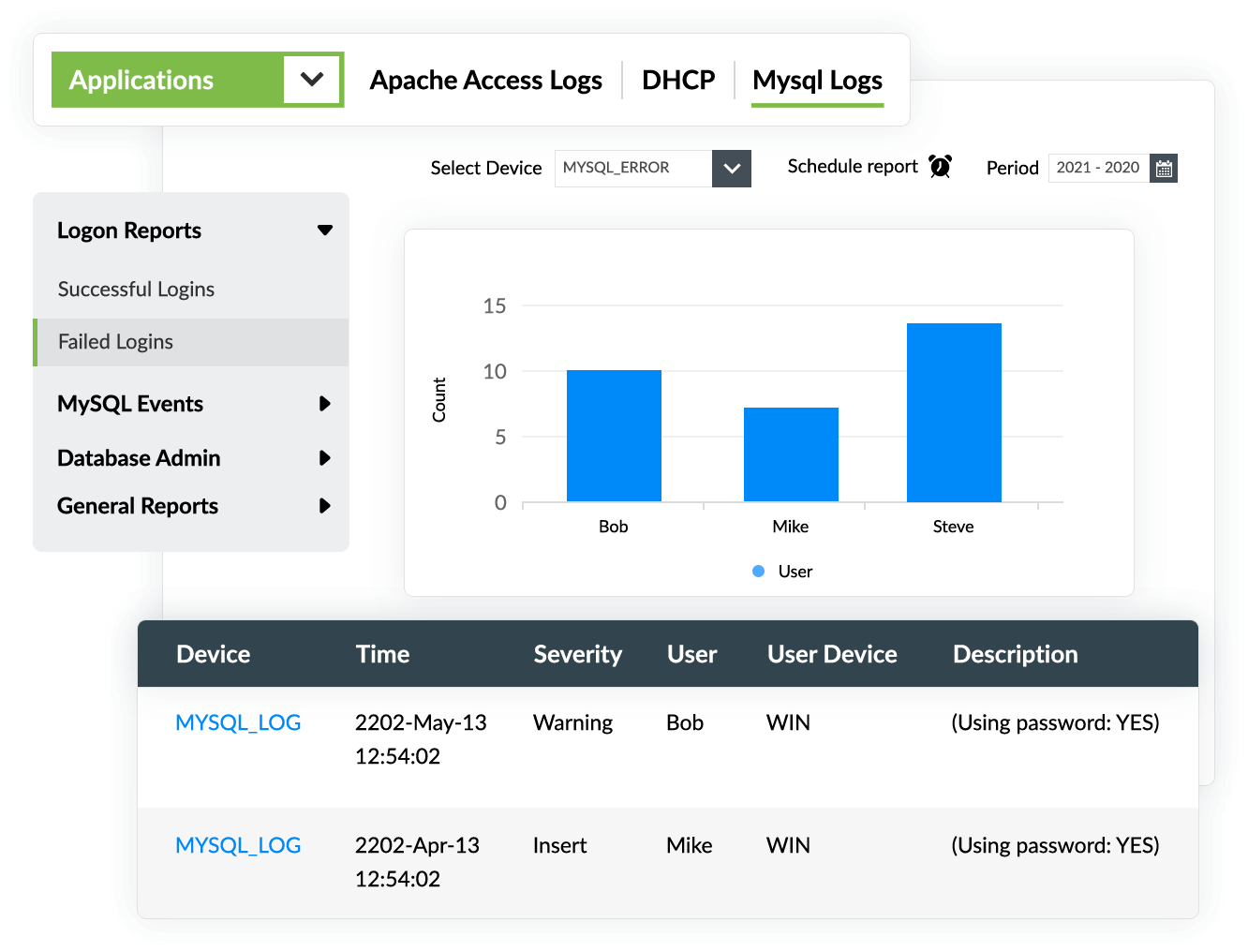
Real-time alerts
EventLog Analyzer provides real-time alerts on security incidents, such as privilege escalation, changes to audit policies, and repeated login failures. By monitoring these changes, you can ensure database security easily.
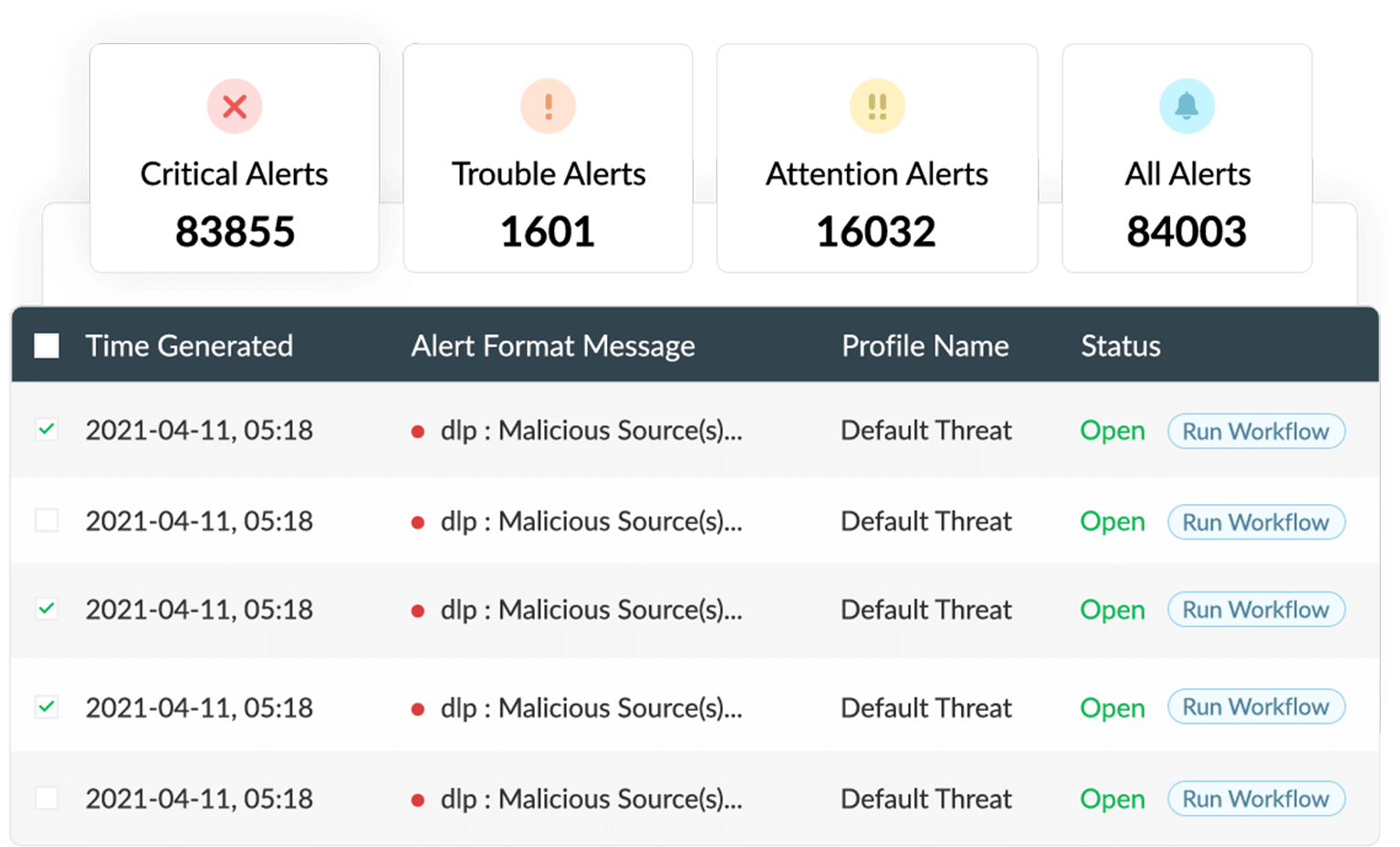
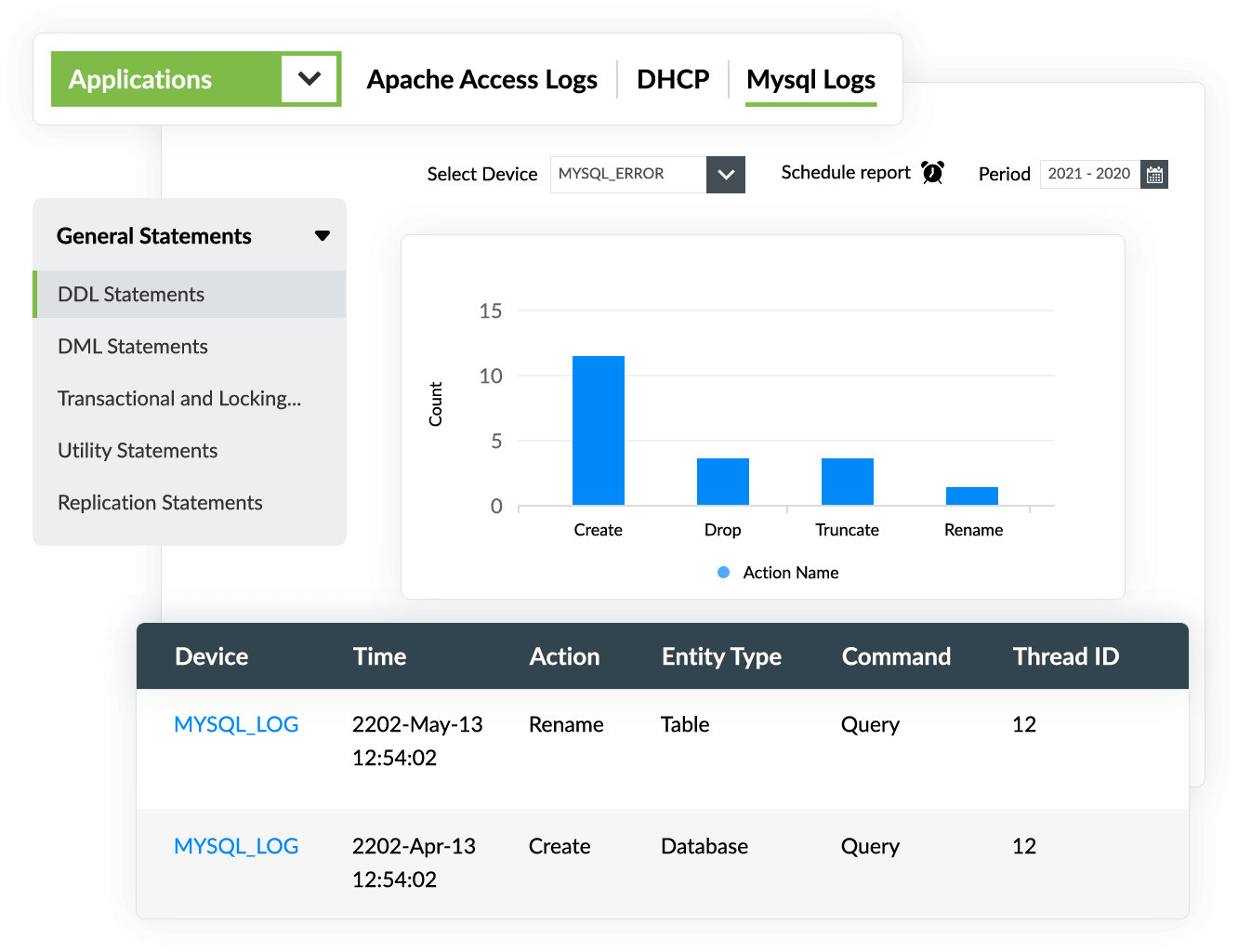
Auditing DDL operations
With EventLog Analyzer, you can monitor and investigate DDL actions, such as create, drop, truncate, and rename, that were executed in your database. Gain in-depth insights into each action, such as the time it occurred, who executed the command, and how frequently it was executed, with EventLog Analyzer's comprehensive reports.
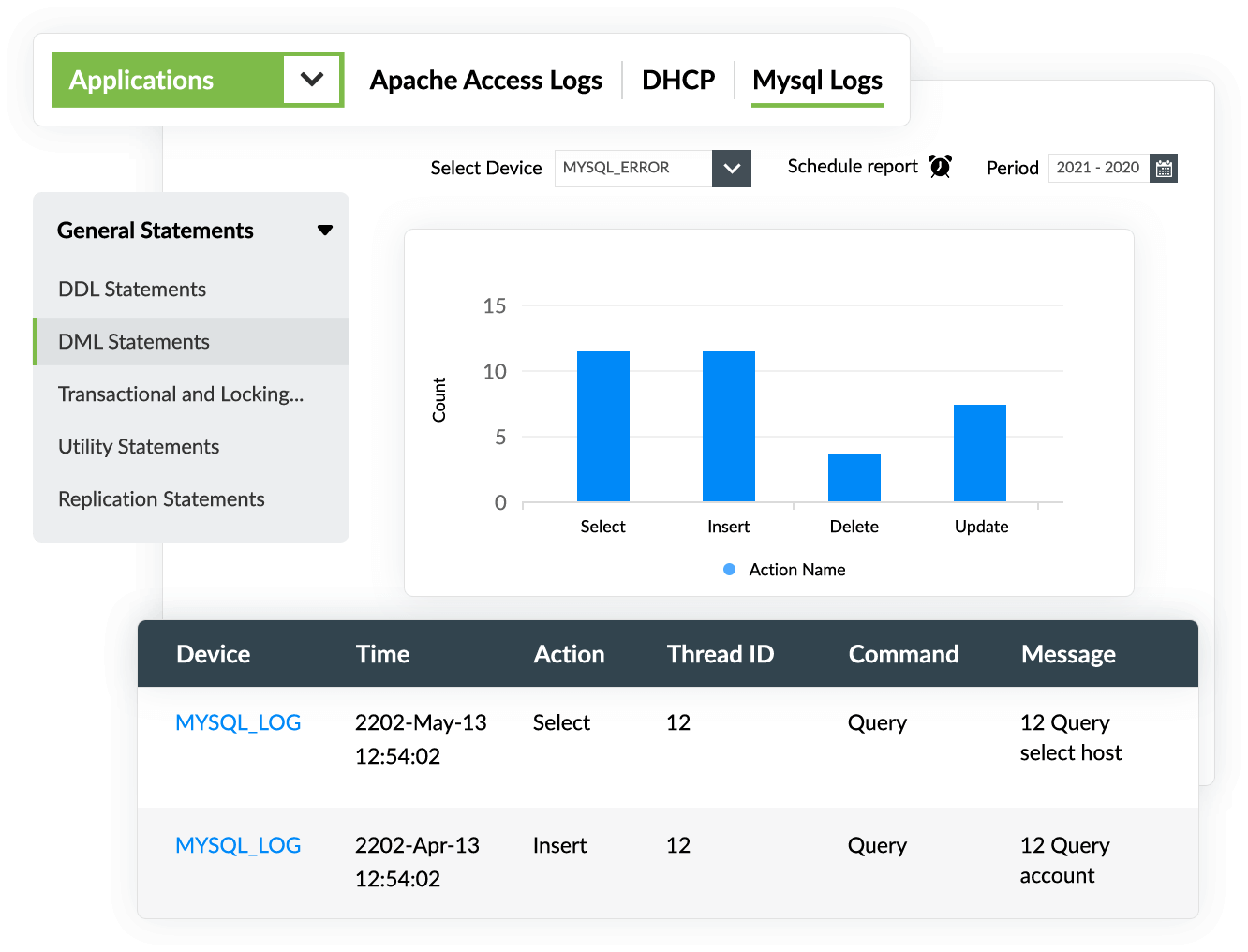
Auditing DML activities
In addition to auditing DDL operations, EventLog Analyzer monitors and analyzes DML actions, such as select, insert, delete, and update, that were executed in your database. EventLog Analyzer's exhaustive reports detail the query executed, when it occurred, and the number of times it was executed.
Related solutions offered by EventLog Analyzer
Microsoft SQL Server monitoring
With EventLog Analyzer, you can securely collect and audit logs from your Microsoft SQL servers to detect security threats, prevent unauthorized access to confidential information, and comply with various data privacy regulations effortlessly.
Oracle Database auditing
Protect your Oracle Database servers from internal and external security threats by auditing their logs using EventLog Analyzer. Monitor database server changes, unauthorized user activities, unauthorized access to sensitive data, SQL injection, and DoS attack attempts.
Apache server log analysis
Collect, parse, and analyze Apache web server logs efficiently with EventLog Analyzer. Enhance your network security with in-depth analytical reports and receive alerts immediately via email or SMS when a security threat is detected on your Apache server.
IIS server log monitoring
Mitigate security threats with EventLog Analyzer's comprehensive, graphical reports that provide in-depth information on user logins, error events, potential security attacks, unauthorized file operations, and more occurring on your IIS web servers and FTP servers.
Network device monitoring
Monitor security events on your perimeter network devices, such as routers, switches, firewalls, and IDS/IPS tools, using EventLog Analyzer. Secure your organization's network against security threats with real-time alerts and automated response workflows.
5 reasons to choose EventLog Analyzer for MySQL database auditing
1. Monitor database activity
EventLog Analyzer raises alerts and executes response actions in real time when critical activities, such as changes to access permissions and confidential data, occur on your MySQL database servers.
2. Detect attack patterns
EventLog Analyzer has over 30 predefined correlation rules for correlating and detecting attack patterns in logs from multiple devices across your organization's network.
3. Search and analyze raw MySQL logs
EventLog Analyzer's powerful log search engine helps you search through thousands of raw MySQL log files to detect and mitigate security threats. It also performs forensic analysis on logs to find the root causes of security breaches.
4. Manage incidents
Assign tickets to security administrators and efficiently respond to security incidents on your MySQL server using EventLog Analyzer's incident management system.
5. Comply with data privacy regulations
Fulfill the requirements of various data privacy regulations, such as the GDPR, HIPAA, the GLBA, the PDPA, and the CCPA, using EventLog Analyzer's audit-ready compliance reports.
Frequently asked questions
MySQL log files are a security administrator's best friend. Whether it is an unintentional error, a security breach, or a system crash, logs can provide answers. MySQL has several log types that provide insights into different occurrences on the MySQL server. The error log and the query log are the most important ones that should be added to your monitoring list.
- MySQL error log: The error log contains a record of all the issues encountered during the MySQL server's startup, run, and shutdown times. Analyzing these server events can help you identify the causes of slowdowns, crashes, or other unusual behavior in MySQL.
- MySQL query log: The general query log contains information on the general occurrences on the MySQL server, such as when clients connect or disconnect, and records the SQL statements received from clients. This information is useful when you are trying to see what a suspicious client is sending to the server.
Manually examining these logs is time-consuming. EventLog Analyzer provides you with a reliable database monitoring system that simplifies your database management and auditing.
The major reason to continuously audit your MySQL database is to detect security threats in their early stages. Further, compliance regulations like HIPAA, SOX, and the PCI DSS require organizations to track access to sensitive information. Regulations such as the GDPR require organizations to report data breaches to authorities within a specific time frame.
To meet these compliance demands, an audit trail is crucial. Auditing user access to critical data speeds up the incident detection and incident response processes. Continuous auditing also allows organizations to identify the causes of their security and data integrity issues and to find ways to fix them.
In addition to collecting, parsing, and analyzing your MySQL database logs, EventLog Analyzer provides intuitive graphical dashboards and reports that provide details about the security events occurring in your MySQL database. You can easily investigate various events, such as login and logout events, server events, database access attempts, and changes to database schema.











