The absence of an efficient user activity monitoring system is a major reason why many organizations become susceptible to insider threats, or external attackers who compromise the organization's machines and gain access to its internal systems. It is crucial for an organization to deploy a user activity monitoring solution to track the activities of its users continuously, and to defend against security breaches. This solution should provide valuable information to help investigate any security threat and provide a complete timeline of the attacker's activities.
ManageEngine EventLog Analyzer is a log management, auditing, and IT compliance management solution that helps you centrally monitor all your network activities and comply with various IT regulations. This solution helps you log and track your organization users' activities, provide you with comprehensive audit trails and reports, and alert you immediately if any suspicious activity has been detected.
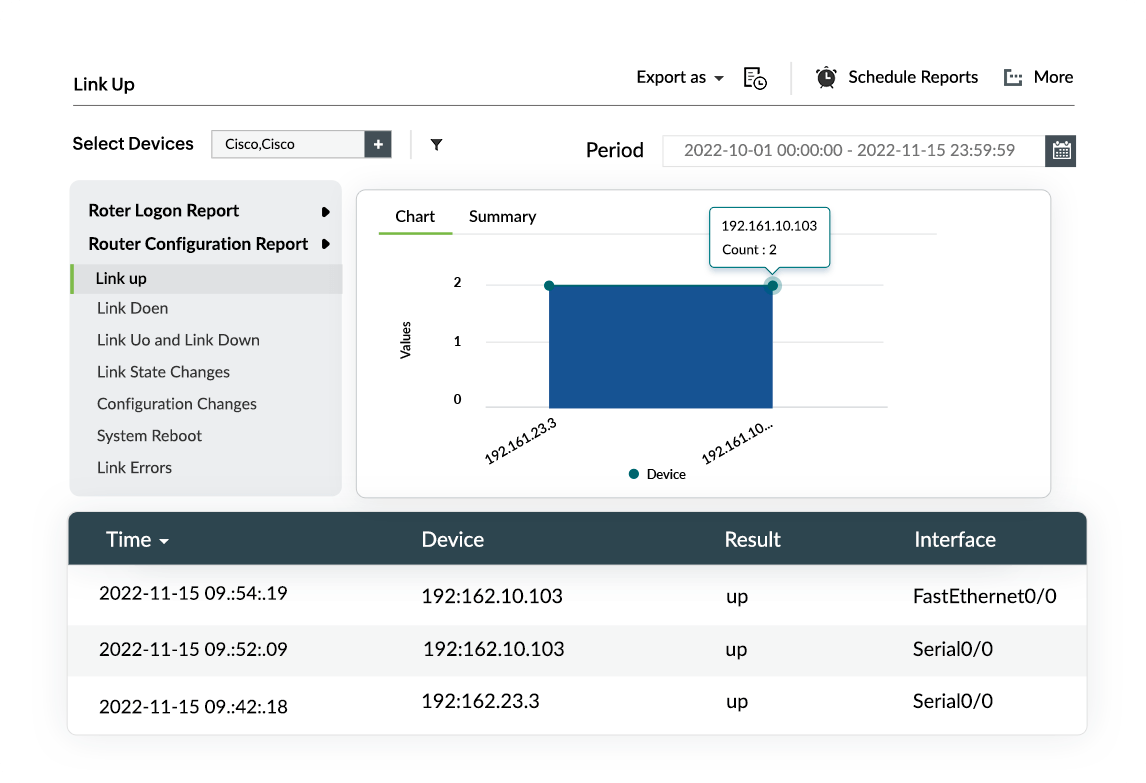
Tracking configuration changes made by users is crucial to ensure network security. Misconfigurations or changes made with malicious intent could lead to security vulnerabilities that can allow a hacker to gain easy access into the organization network. EventLog Analyzer's graphical reports help you track configuration changes in your network devices in real time.
Software Installed | Failed Software Installations Due To Privilege Mismatches | Windows Updates Installed | Registry Changes | Windows Backup and Restore | Firewall Rule Added | Firewall Rule Deleted | Firewall Settings Changes | Router Configuration Changes | Router Commands Executed
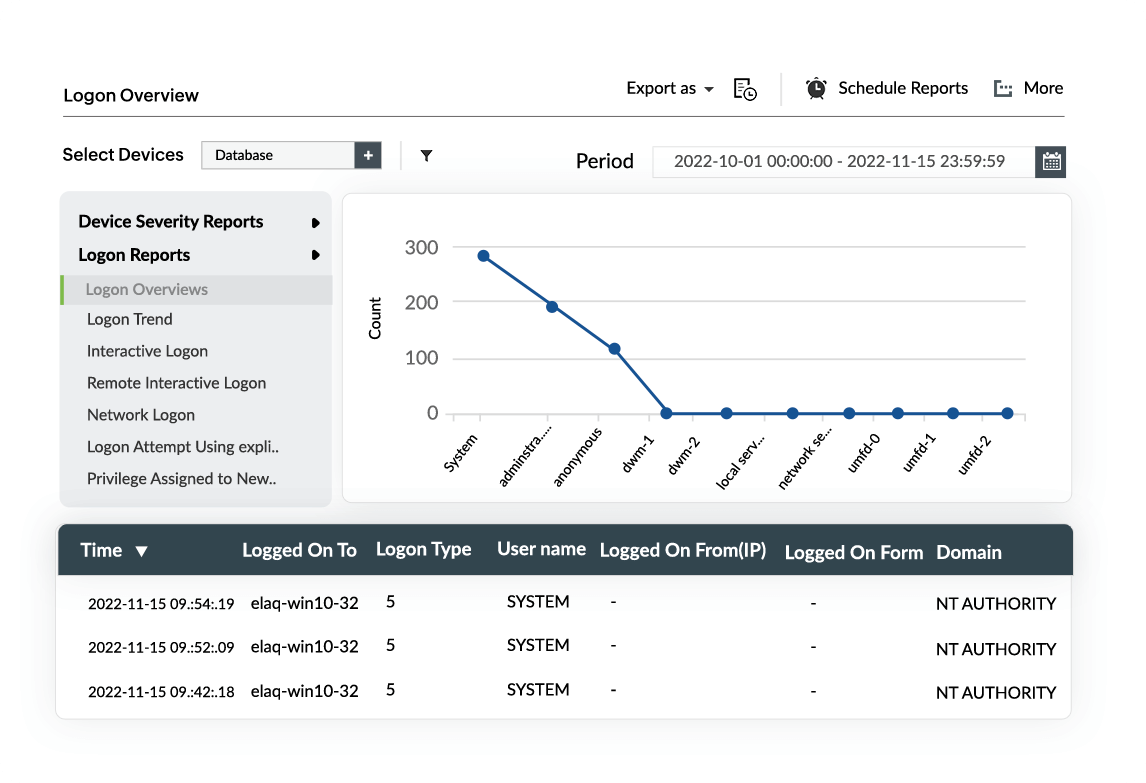
As users who logon or logoff at unusual times can indicate suspicious behavior, auditing user logon activities in real time is vital for identifying insider threats. EventLog Analyzer features multiple built-in logon and logoff reports that help you monitor user logon events in real time.
Unix Logons | Unix Logoffs | Unix Failed Logons | Router Logons | Router Failed Logons | Firewall Logons | Firewall Failed Logons | Session Activity Monitoring Reports
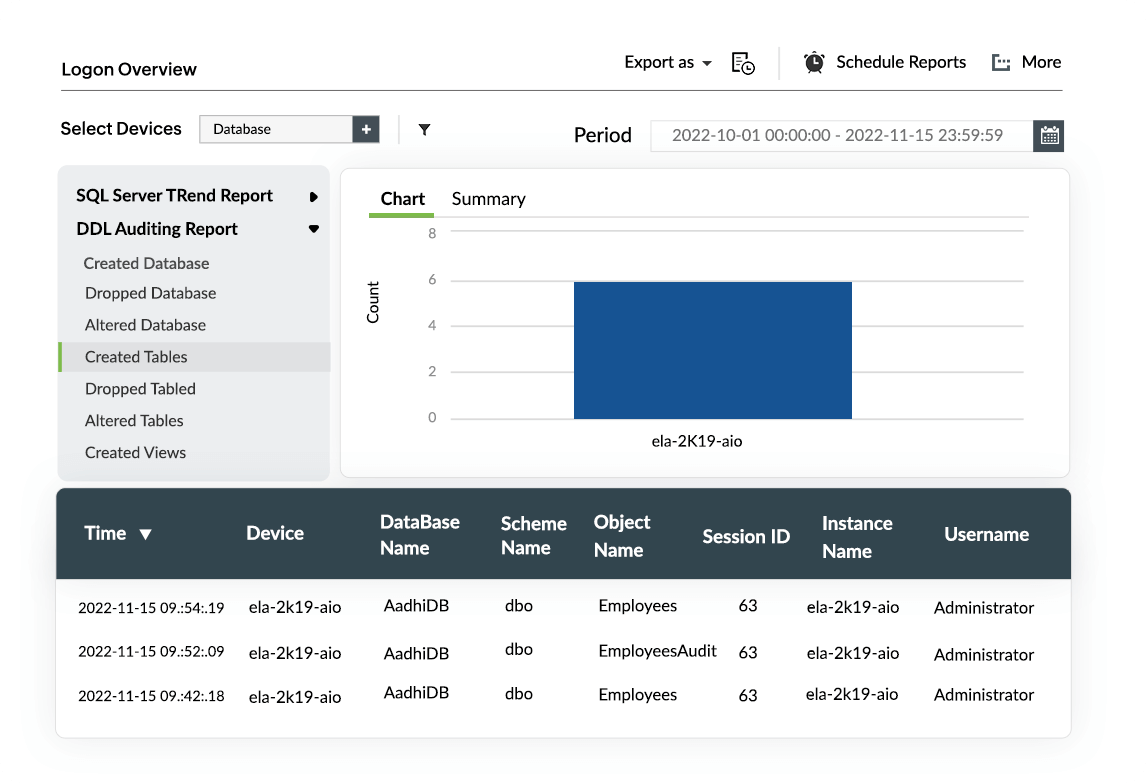
Track and prevent unauthorized access to confidential information stored in critical databases and file servers using EventLog Analyzer. You can set up real-time alerts and response actions so they are executed when activities such as modifications to access permissions and changes to sensitive data occur on your servers.
DDL Audit Reports | Privilege Abuses | Admin Authority Changes | Permission Changes | Owner Changes | Database Backup Report | Database Permission Denied | Access Violation | File Permission Changes

Tracking configuration changes made by users is crucial to ensure network security. Misconfigurations or changes made with malicious intent could lead to security vulnerabilities that can allow a hacker to gain easy access into the organization network. EventLog Analyzer's graphical reports help you track configuration changes in your network devices in real time.
Software Installed | Failed Software Installations Due To Privilege Mismatches | Windows Updates Installed | Registry Changes | Windows Backup and Restore | Firewall Rule Added | Firewall Rule Deleted | Firewall Settings Changes | Router Configuration Changes | Router Commands Executed

As users who logon or logoff at unusual times can indicate suspicious behavior, auditing user logon activities in real time is vital for identifying insider threats. EventLog Analyzer features multiple built-in logon and logoff reports that help you monitor user logon events in real time.
Unix Logons | Unix Logoffs | Unix Failed Logons | Router Logons | Router Failed Logons | Firewall Logons | Firewall Failed Logons | Session Activity Monitoring Reports
Protect your database servers from security threats by collecting and auditing their logs using EventLog Analyzer. You can efficiently monitor changes in your databases, detect unauthorized access to confidential data, track SQL injection threats, and thwart DoS attack attempts.
Learn moreConfigure alert profiles and get notified in real time through email or SMS when any user performs anomalous or suspicious activity in your network.
Utilize EventLog Analyzer's more than 40 predefined correlation rules that enable you to correlate logs from multiple devices and detect potential threats in your network.
Simplify forensic investigation and find the root cause of a security threat using EventLog Analyzer's powerful log search capabilities that help you search through thousands of raw log files swiftly and efficiently.
Automatically assign tickets to security technicians, and respond to security incidents quickly using EventLog Analyzer's built-in incident management dashboard.
Configure EventLog Analyzer with external help desk software such as Jira Service Desk, Zendesk, ServiceNow, ManageEngine ServiceDesk Plus, Kayako, or BMC Remedy Service Desk to assign tickets to the ideal security technician to achieve a quick resolution.