Firewall Security Audit Tool
Firewall Analyzer is designed to generate detailed compliance reports for firewall devices, aiding in comprehensive firewall security audits. These reports help configure firewall rules to prevent unauthorized access, allowing only essential network hosts. As an effective firewall rule audit tool, it identifies all firewall security related issues.
Key Features of Firewall Analyzer as a firewall security audit tool
- Firewall Security Audit report:The firewall rule audit tool provides a detailed firewall security audit report, identifying security issues and offering a firewall rules audit checklist. This checklist serves as a benchmark for auditing firewall rules and assessing their impact and severity.
- Firewall Configuration Analysis: It audits the entire firewall configuration, categorizes threats, and recommends best practices to enhance security. The software assesses the ease of fixing identified issues and suggests necessary configuration changes.
- Issue categorization: Issues are rated across five categories: critical, high, medium, low, and information. This categorization helps prioritize actions based on the severity of the issues.
Report Structure
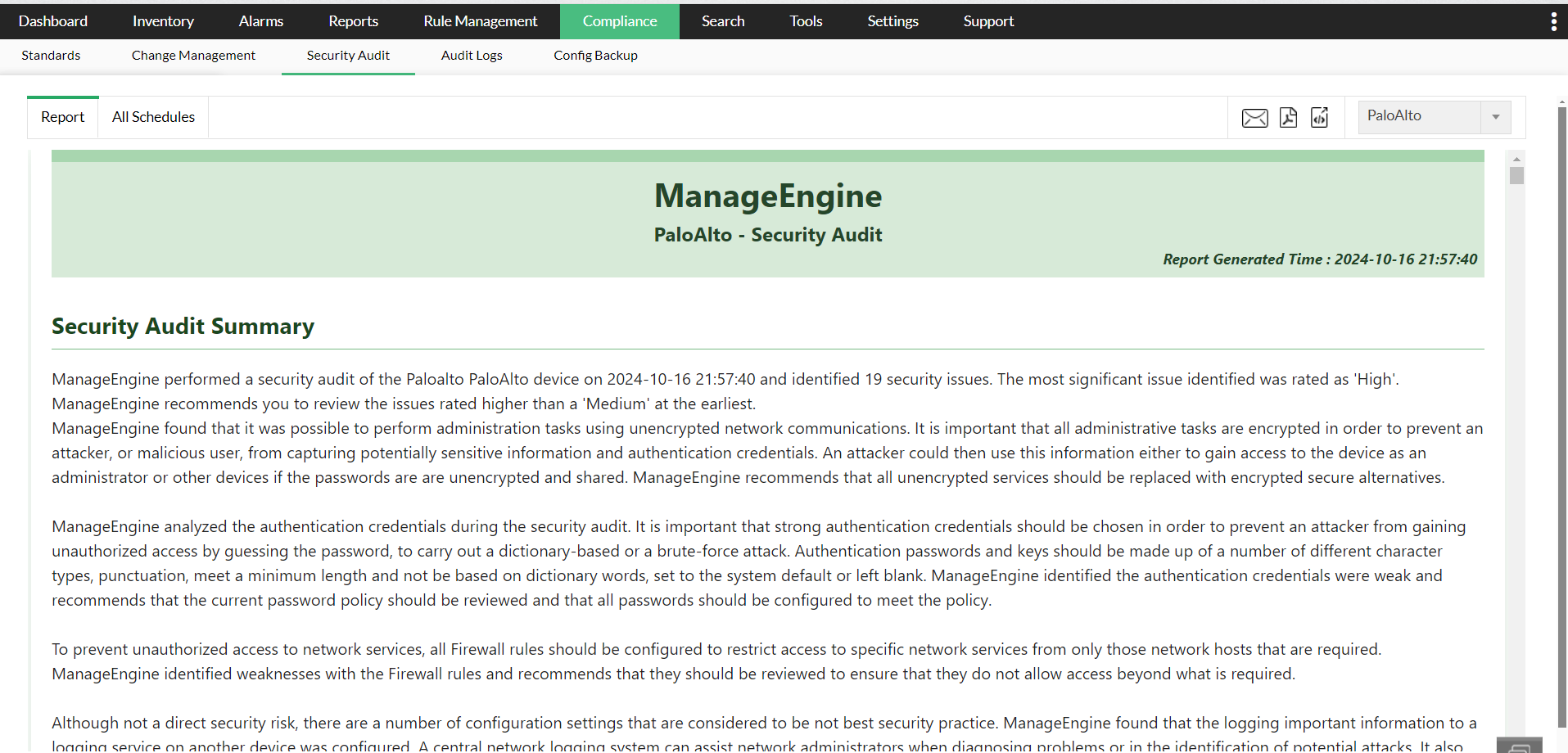
The compliance report generated by Firewall Analyzer is divided into three main sections : Security Audit Report section, Security Best Practices Section and Device Configuration Section.
Security Audit
- Issue identification: A detailed description of the identified issue.
- Impact assessment: Evaluation of the issue's potential impact.
- Exploitability: An analysis of how easily the issue can be exploited.
- Recommendations: The suggested measures to mitigate the issue.
- Overall rating: A combined rating based on the above factors.
Security Best Practices
- The overview section offers a summary of recommended best practices for firewall security, including insights from auditing firewall security. This section outlines general principles and strategies that organizations should follow to enhance their firewall configurations and overall network security.
- The recommendations section provides specific guidance on implementing best practices across different areas, such as software settings, service configurations, interface management, filtering rules, authentication mechanisms, logging practices, and encryption protocols.
Device Configuration
This section details the current settings and configurations of your firewall devices, incorporating insights from the firewall audit software . It provides a snapshot of how your firewalls are currently configured, which is crucial for understanding the context of identified security issues and recommendations.
Report Generation
- Periodic Firewall Compliance report generation: Reports are generated at regular intervals, with the UI displaying the generation time.
- Instant Firewall Compliance report generation: Users can generate compliance reports on demand.
Configure credentials / associate device profile to fetch Firewall configuration and rules
The firewall configuration analyzer module configures the device credential or assigns a credential profile to the device. On assigning a device profile or configuring device credentials, the compliance report will get generated automatically. Thus Firewall Analyzer acts as an efficient firewall configuration tool.
Refer Firewall compliance management software page for more details about other firewall security standards compliance.
Importance of firewall security audits
Security audits play a pivotal rule in enhancing your network defenses by highlighting the vulnerabilities and sharing the status of compliance with regulatory mandates. This allows your network security admins to take adequate counter measure to bolster your organization's network security.
- Proactive threat identification: Firewall security audits take a proactive approach to cybersecurity. By identifying new and evolving threats, they ensure your firewall rules and threat signatures are up-to-date.
- Enhanced security posture: Audits go beyond threat identification. They meticulously examine firewall rules to confirm accuracy and prevent potential tampering. Additionally, audits involve a comprehensive analysis of firewall logs, enabling the early detection of anomalous activity that might indicate a security breach.
- Compliance assurance: Many industries are subject to stringent data security regulations. Firewall security audits play a vital role in ensuring your firewall configuration aligns with these regulations. This mitigates legal risks and potential fines associated with non-compliance.
- Optimized network performance: Audits can also streamline firewall rules by identifying unnecessary ones or any configuration errors. This bolsters network performance and reliability and minimizes the likelihood of costly security incidents and network downtime.
In summary, a comprehensive approach to audit firewall rules ensures an enhanced security posture and optimized network performance.
FAQs - Firewall Rule Audit
What is Firewall Rule Audit?
+
A firewall audit is a thorough check of a firewall’s setup and rules. It aims to find security holes, ensure compliance with regulations, and optimize performance. Key tasks include reviewing firewall rules, checking configurations, analyzing logs for suspicious activity, and ensuring all changes are documented and authorized.
Why Firewall Rule Audit is important?
+
Firewall Rule Audit ensures your firewall setup is secure and efficient. Performing firewall rule audit can enhance network security, reduce the risk of breaches, and maintain regulatory compliance, safeguarding sensitive data and business operations effectively.
How to perform Firewall Rule Audit?
+
To conduct a firewall rule audit, document all rules and identify redundant or unused rules. Check the order of rules to prevent conflicts. Verify compliance with policies and regulations and analyze firewall logs for suspicious activity. Adjust rules as needed to enhance security and performance. Document findings and actions for stakeholders' awareness and future reference.
Featured links
Other features
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.