Enterprises following traditional security systems to detect cyberattacks can only detect known attacks such as DoS or DDoS. Although firewalls and other IDS tools have threat detection advantages, the use of only preknown rules or signatures will not detect all of today's zero-day intrusions. As the traffic generated each day in an enterprise network is high, detecting zero-day intrusions, internal threats, and IDS using signature-based tools can be resource intensive. What network admins should rely on is network behavior anomaly detection. These solutions help detect traffic patterns so that the unusual behavior of the network can be taken into account as an event needing immediate action.
Security Analytics is a security monitoring module of NetFlow Analyzer that enables the Continuous Stream Mining Engine which classifies and groups events. It delivers a detailed view of the network's security posture by providing a view into information about the network's anomalies, thus helping security teams take better actions.
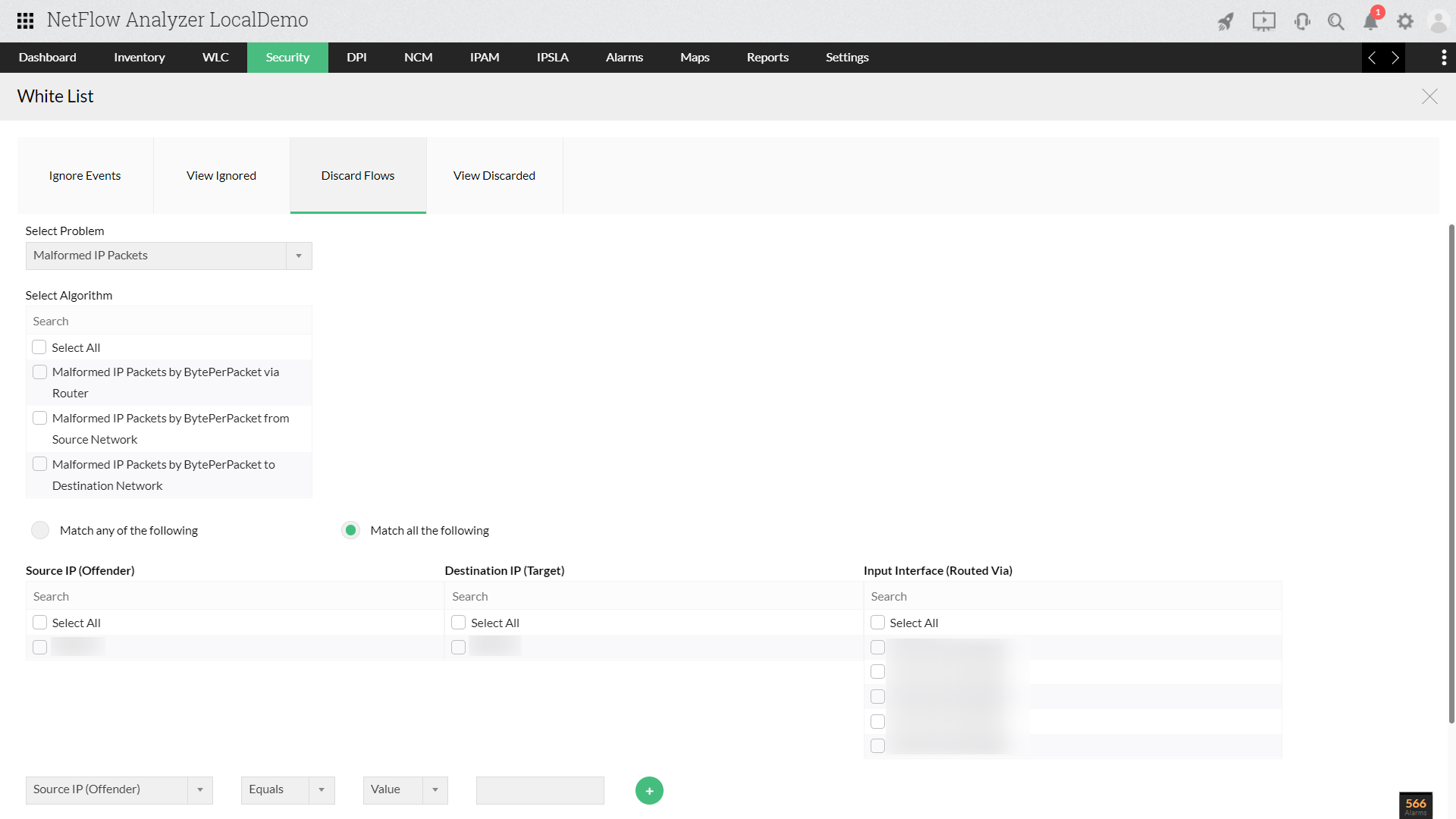
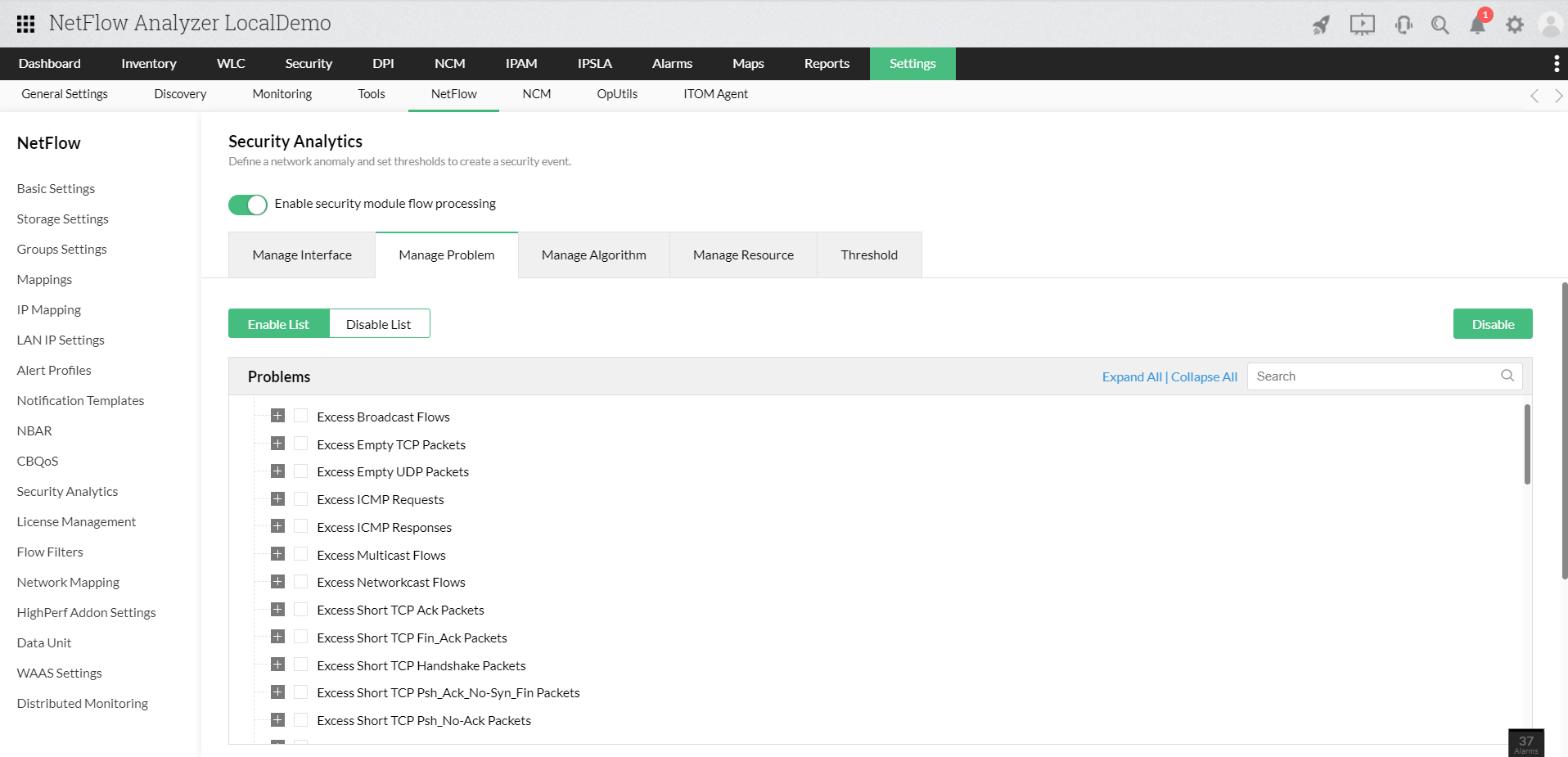
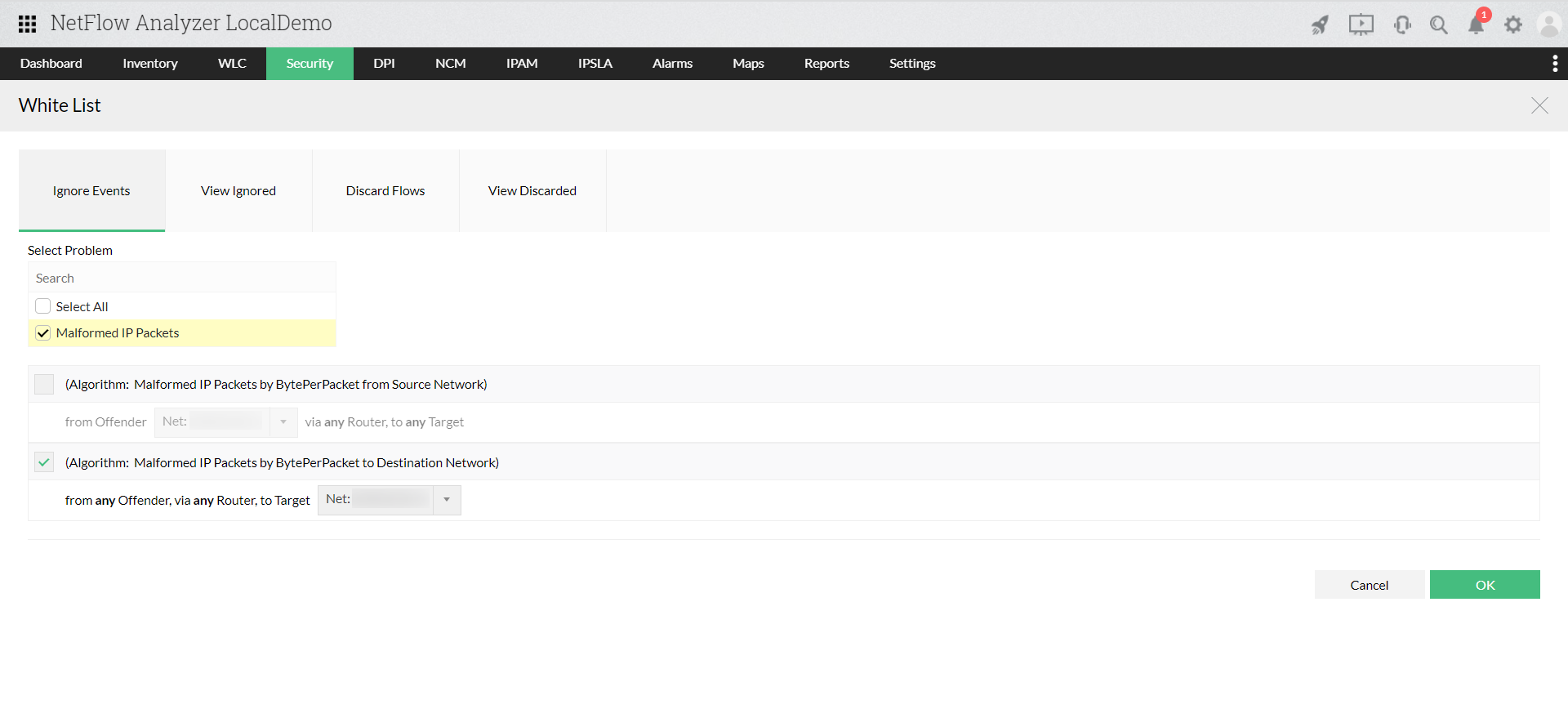
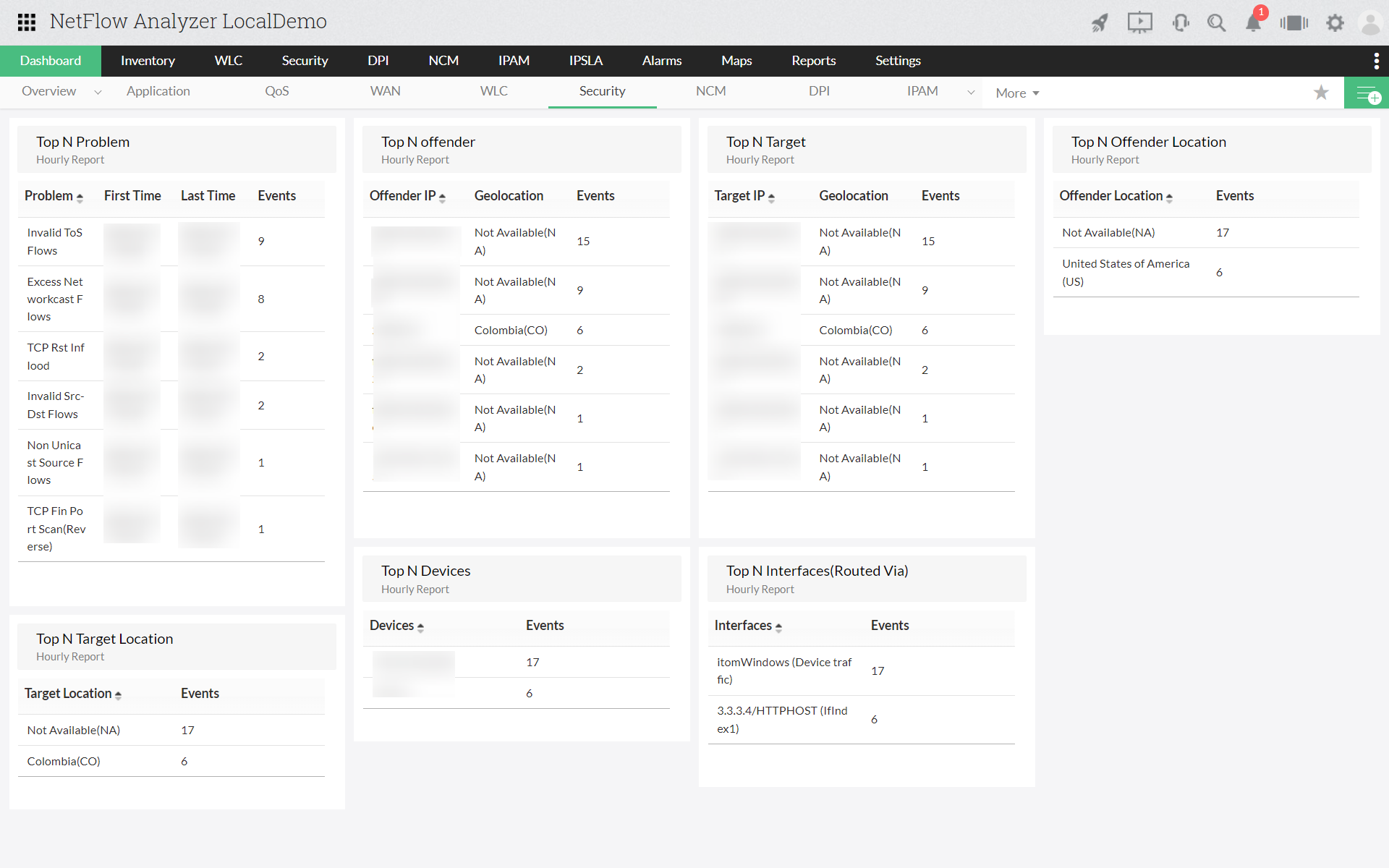
This displays a list of grouped threats or anomalies as a problem and further, the problems are categorized in to three major problem classes (Bad Src-Dst, DDoS, Suspect Flows). Read more...
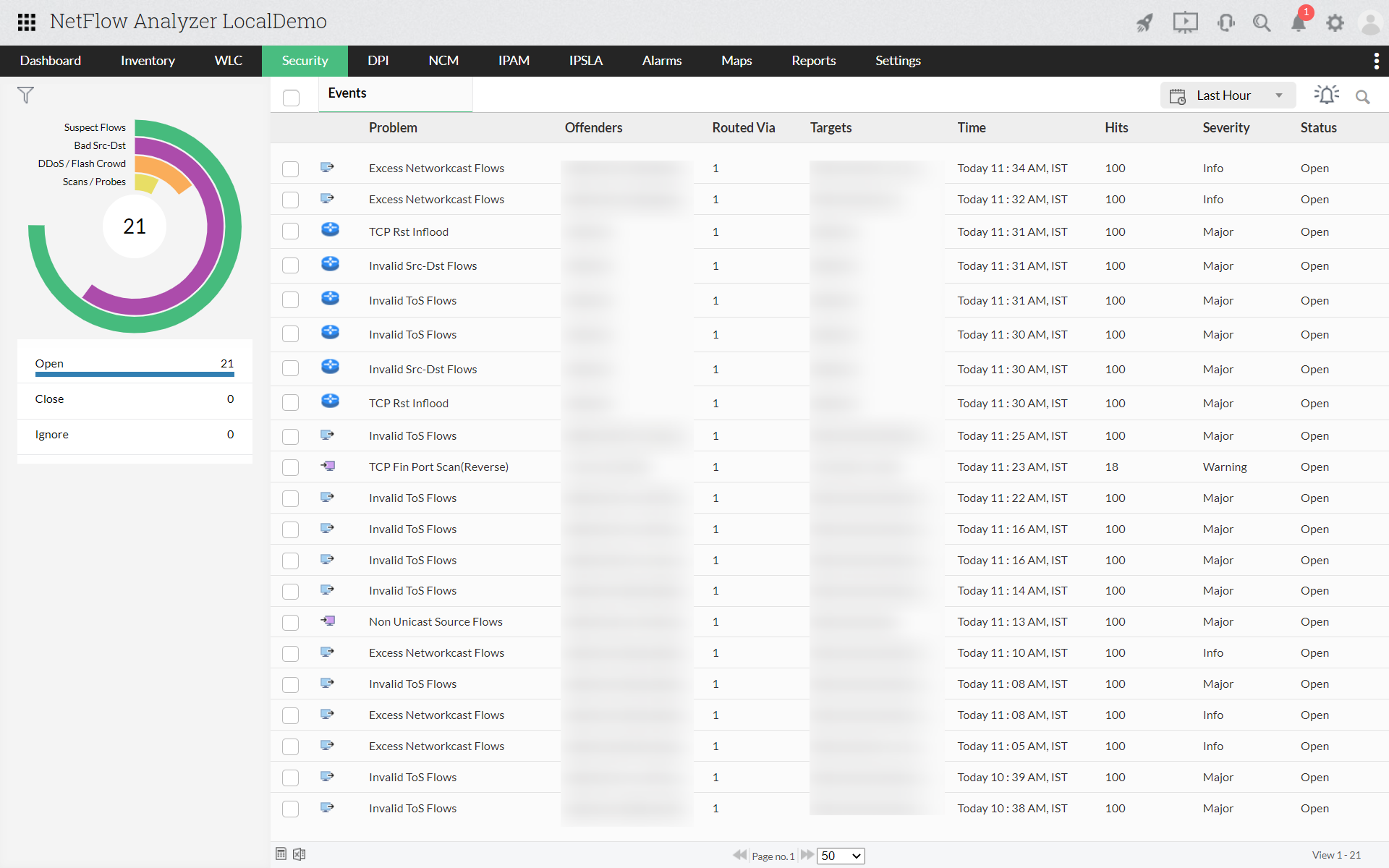
The ‘Event List’ in Security module lists, classifies and organizes all the events that might become attacks. Also, Security module assigns severity of an event; this allows you to prioritize your actions. Read more...
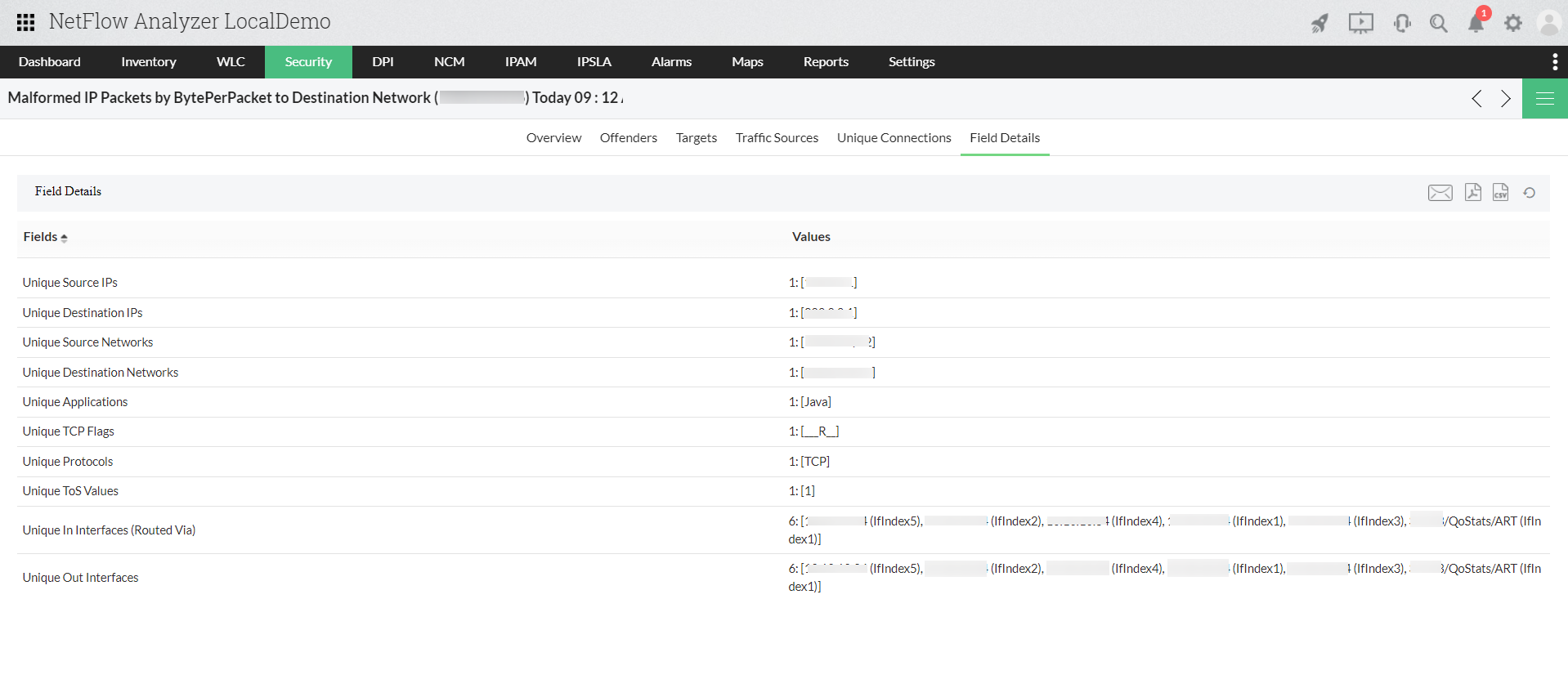
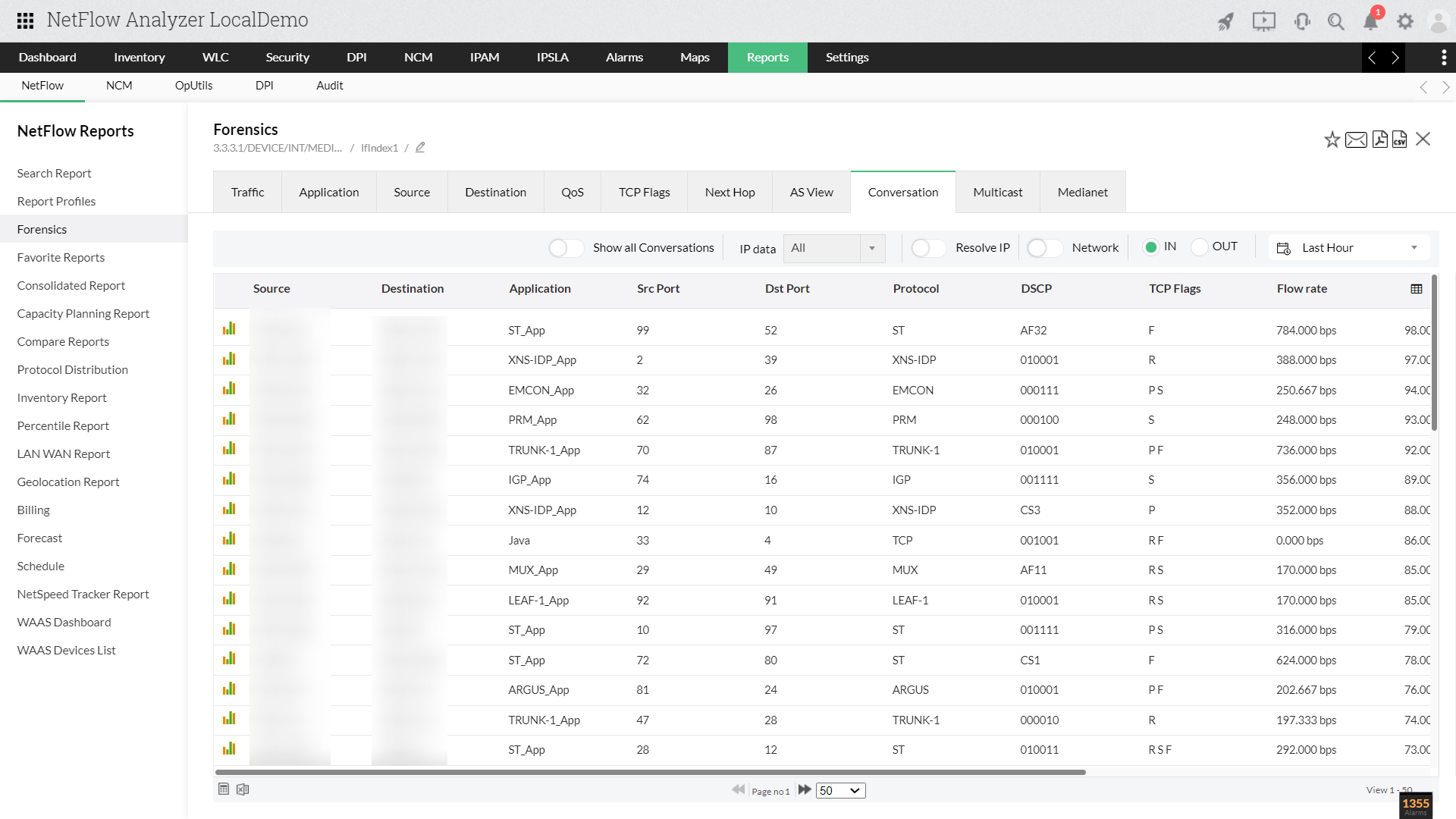
Event details gives a thorough detail about the problem. The details include network, port, protocol, TCP flag and much more. Clicking on the router name gives details with mapped destination, such as source IP and the application, port, protocol etc. used. This report can be exported as a pdf or can be mailed with just a single click.