There are two ways of generating DPI forensics report:
Change Management
Monitors the configurations for changes. Any change made to an existing configuration along with the time and date of change is notified immediately via email. It also allows you to carry an audit on the change such as who did what and when. This helps you to find out the errors in the configuration and act accordingly.
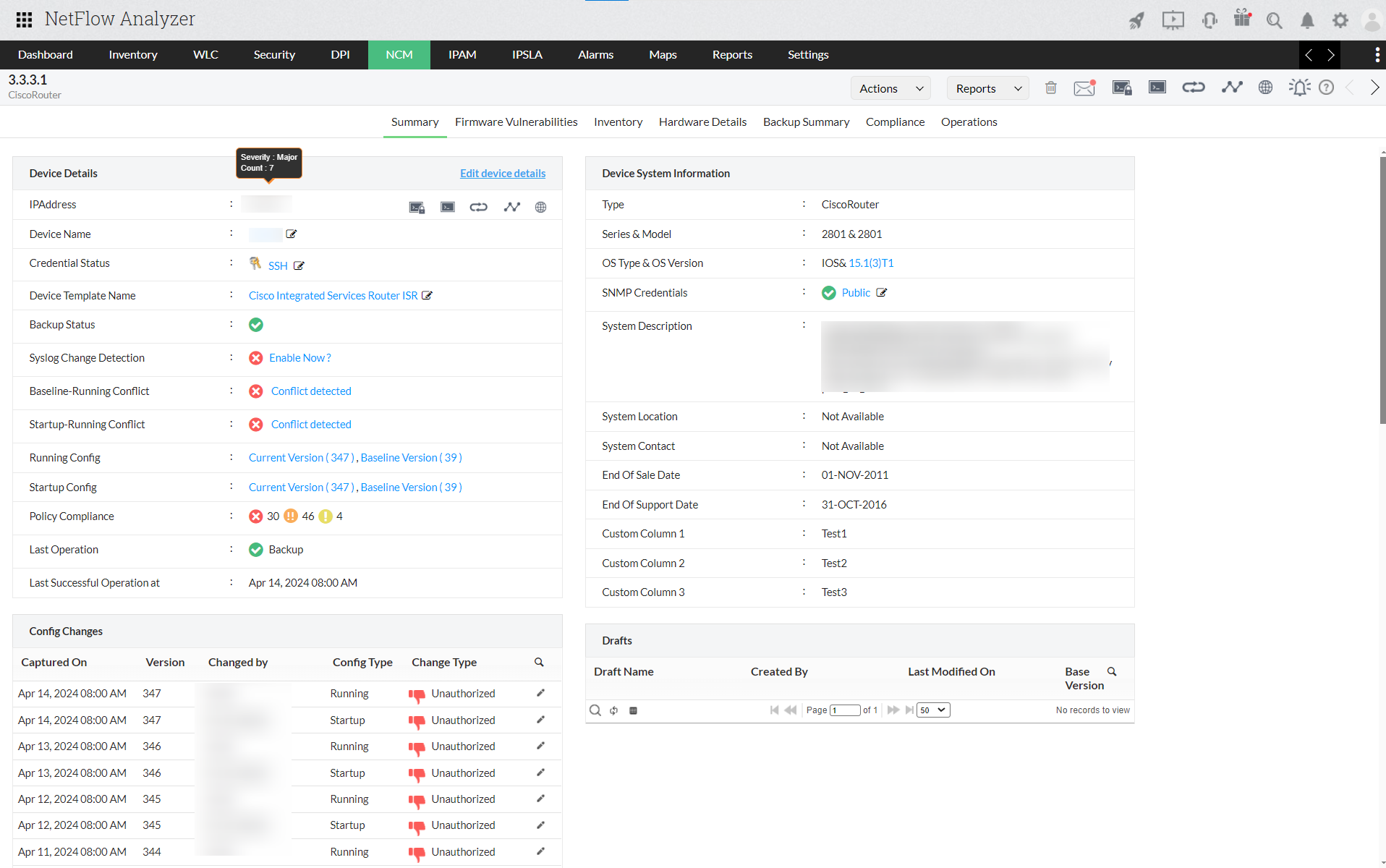
Configuration Management
Push periodical backups, and revert configurations without logging in to the end devices. It communicates to the devices via SNMP, CLI and Telnet protocols to do these actions. This process is quick and helps you manage configurations much easily and quickly.
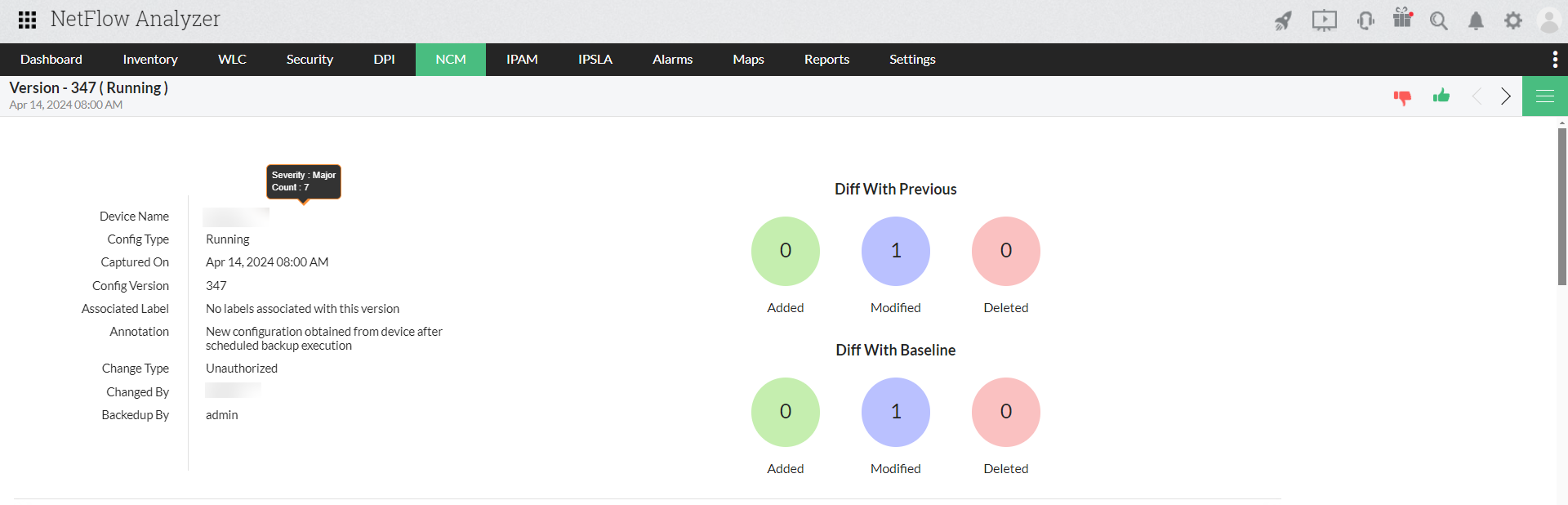
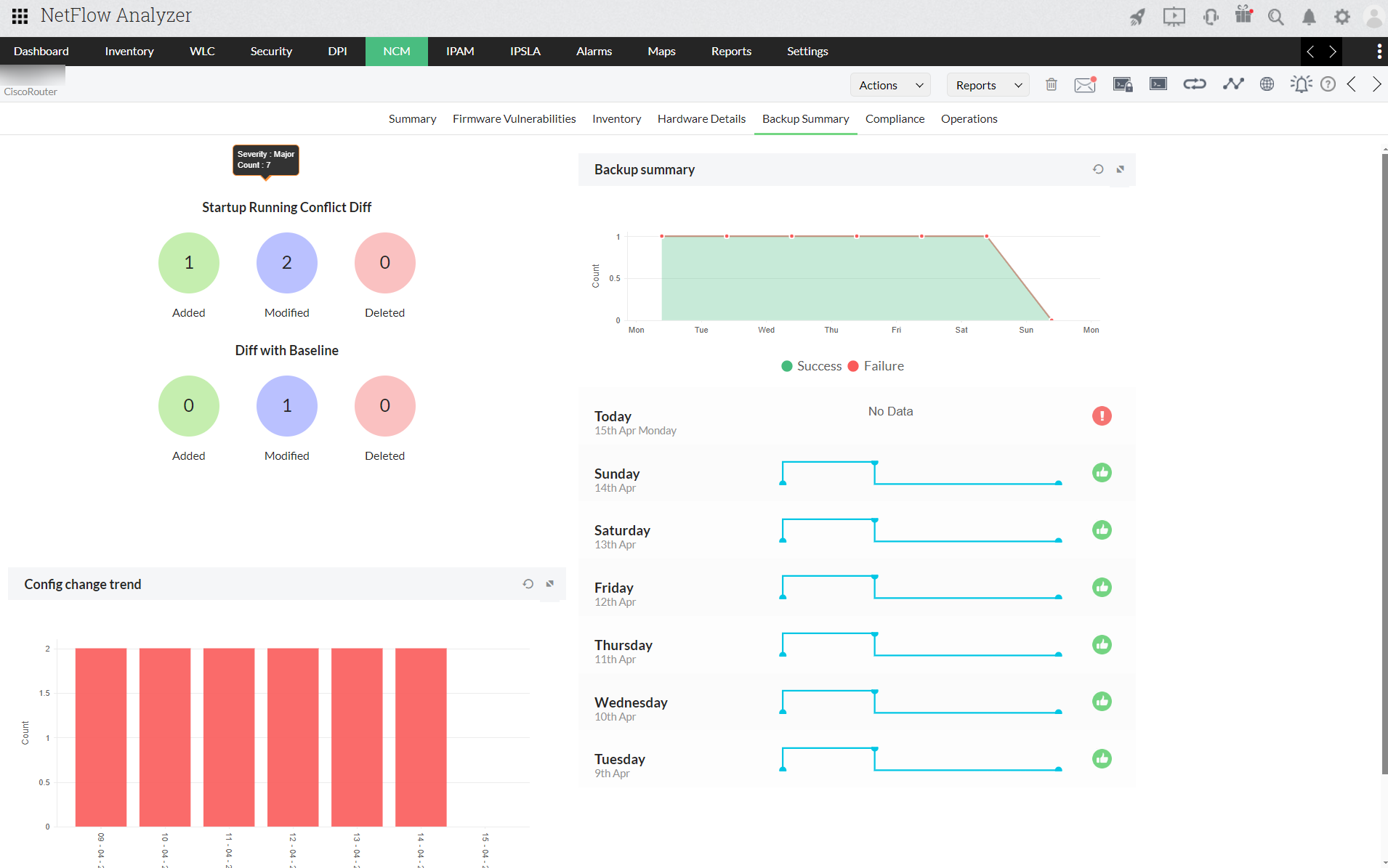
Backup of configuration files
Backup your device configuration periodically helps to restore back to your existing configurations or reverting form any faulty configuration. Know your device name along with date and time of backup and status with NCM add-on.
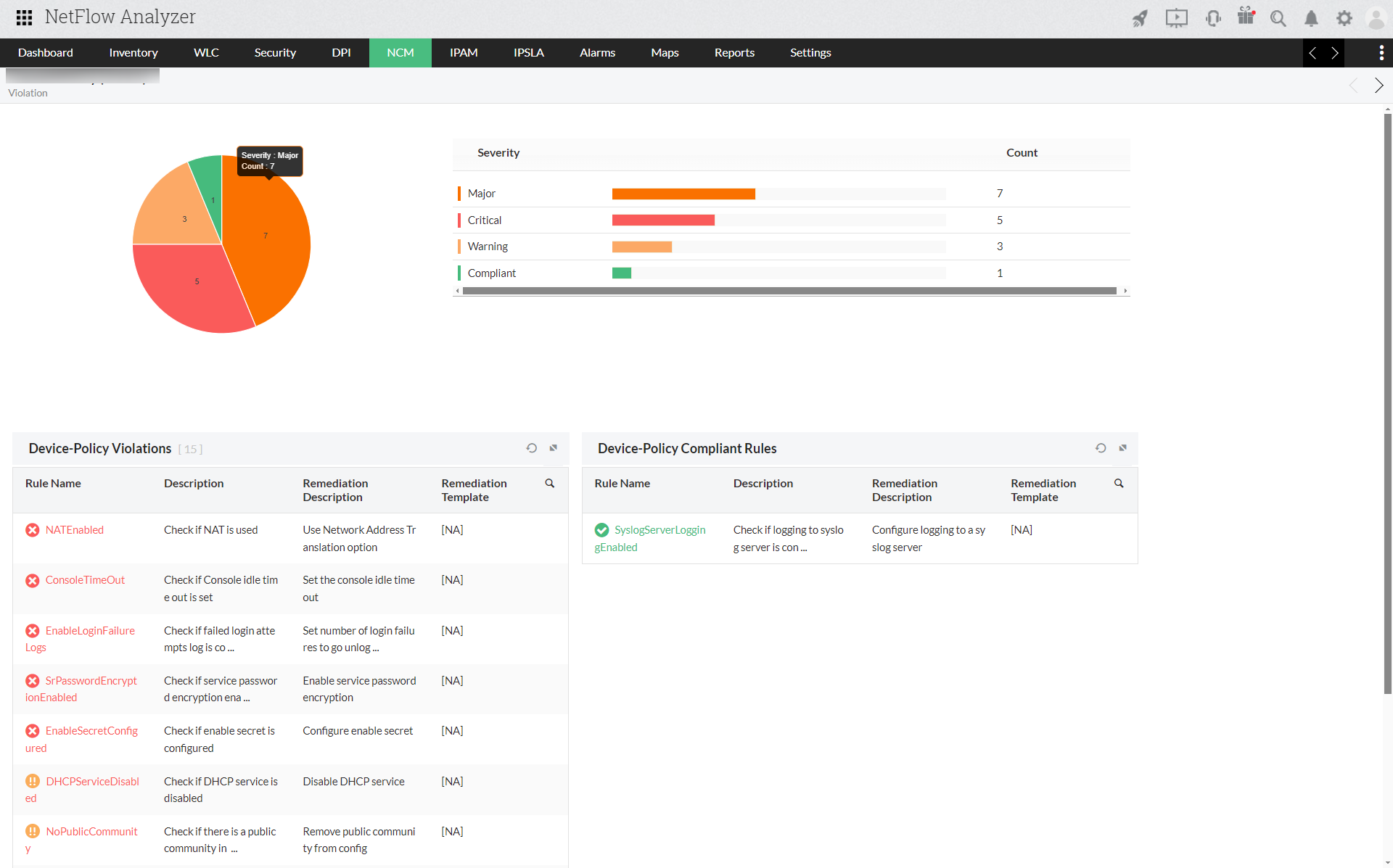
Compliance Audit
Define and enforce standards that ensure the presence or absence of certain strings, commands or values. The NCM add-on scans the configuration for compliance to the rules/ policy defined and reports violations. It also allows you to generate reports on policy compliance and violations.
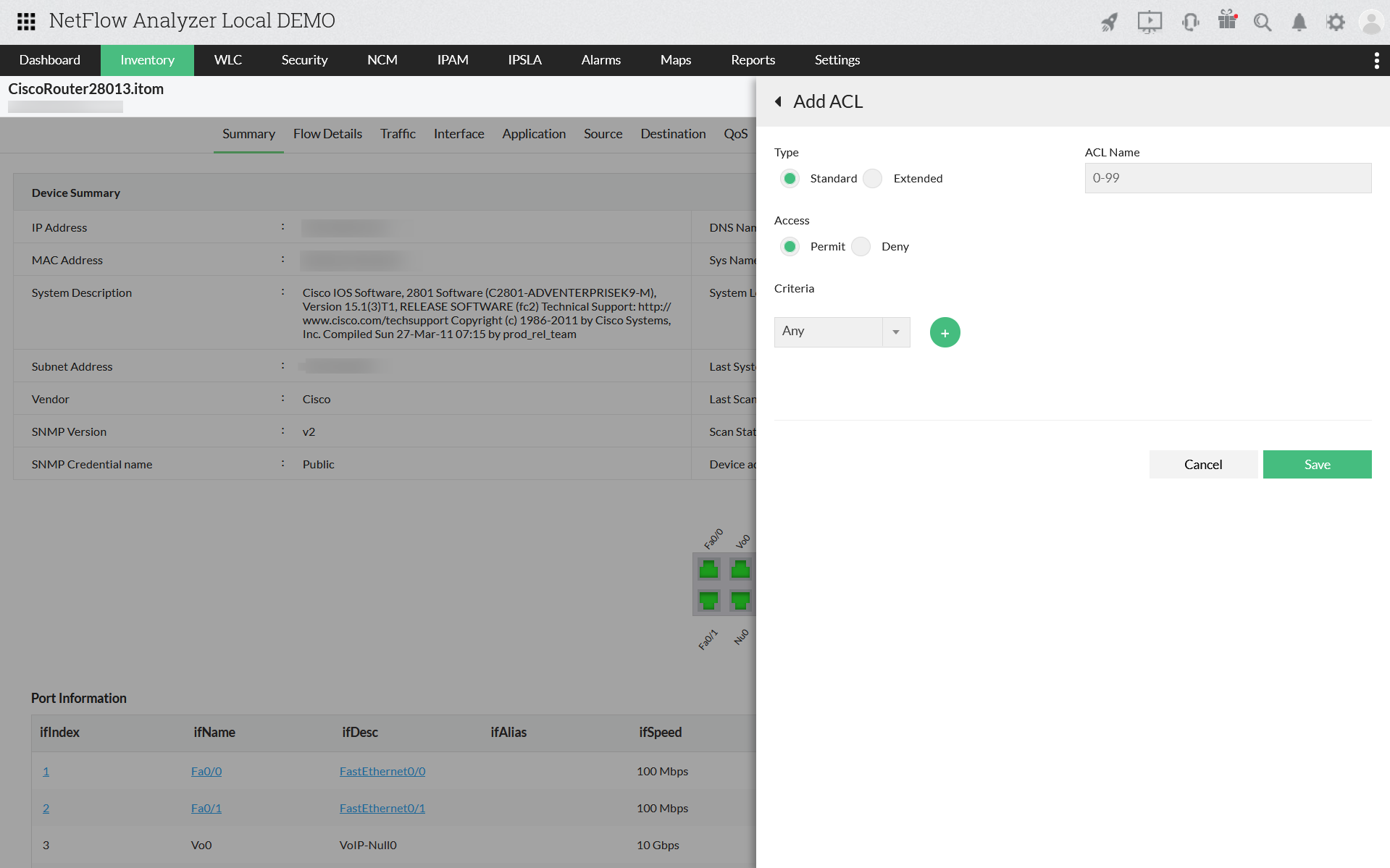
Apply ACL and create/edit QoS policies
Manage service policies of your devices to ensure that the business critical applications get the optimum priority. View all the QoS configurations, review new and edit the existing policy to optimize bandwidth usage.
Refer the below link to add a new device in NCM:
Refer the below link to create an Access Control List (ACL) in NetFlow Analyzer:
Thank you for your feedback!