Port scanning starts with a simple question: Which services are exposed on a device? To answer that, you first need a clear understanding of how ports and services operate. This section will help you with the fundamentals.
Key takeaways from this article:
- What it is: A method to identify which ports and services are exposed on a device.
- Why it matters: Helps detect risks, validate firewall rules, and prevent unauthorized access.
- How it works: By probing ports with TCP/UDP requests and analyzing the responses to classify their state.
What are network ports?
Let’s first distinguish between switch ports (physical interfaces on a network switch) and software ports (used by devices and applications).
A switch port is a physical interface on a network switch. This is where end devices, servers, VoIP phones, printers, or uplink cables are plugged in. Switch ports handle the forwarding of Ethernet frames at Layer 2 and determine how traffic flows within the local network.
Switch ports also have configurable attributes such as:
- Speed and duplex
- VLAN assignment
- PoE provisioning (if supported)
- Port security
- Link status and utilization
A network (software) port is a logical communication endpoint that helps devices send and receive data for specific applications or services. Every network connection uses a port number to identify which service or application should process the incoming request.
Software ports work primarily over two transport protocols:
- Transmission Control Protocol (TCP): Reliable, connection-oriented communication.
- User Datagram Protocol (UDP): Fast, lightweight, and connection-less communication.
Port numbers range from 0 to 65,535 and fall under three main categories:
| Port range | Name | Purpose |
|---|---|---|
| 0 – 1023 | Well-known ports | Standard services like HTTP, DNS, SMTP |
| 1024 – 49151 | Registered ports | Vendor-specific apps and tools |
| 49152 – 65535 | Dynamic / private ports | Temporary client-side connections |
How services map to ports
Each service or application listens on a specific port. Knowing common port-to-service mappings helps identify system roles during a scan.
| Port number | Protocol | Purpose |
|---|---|---|
| 80 | TCP | Web traffic (HTTP) |
| 443 | TCP | Secure web traffic (HTTPS) |
| 22 | TCP | Secure shell (SSH remote login) |
| 53 | TCP / UDP | DNS queries, name resolution |
| 3389 | TCP | Remote Desktop Protocol (RDP) |
| 25 | TCP | SMTP email delivery |
| 161 | UDP | SNMP device monitoring |
Port states explained
When scanned, a port typically falls into one of three primary states:
| Port state | What it means | Risk perspective |
|---|---|---|
| Open | A service is listening and reachable. | Needs validation: Is it expected and secure? |
| Closed | No service is listening, but the device is reachable. | Low risk; but may reveal the host exists. |
| Filtered | Firewall/ACL is blocking access or dropping probes. | Security control is active, but may hide risky services. |
Unfiltered ports
While most scanners classify ports into the three primary states - open, closed, and filtered, the term unfiltered isn’t included in this main group because it is specific to certain advanced scan types (like ACK scans) and doesn’t indicate whether the port is actually open or closed.
An unfiltered port means the scanner can reach the port, but it cannot determine its exact state. The port is responsive, but the scan type used doesn’t provide enough information to confirm whether it is open or closed. This state usually appears during firewall analysis, where the goal is to understand filtering behavior rather than service availability.
Networks rely on ports to enable communication between devices and applications. Every service like web, email, DNS, or SSH runs on a specific port. But when these ports are left open or exposed without proper monitoring, they create opportunities for unauthorized access and exploitation.
This is where port scanning plays a critical role.
What is port scanning?
Port scanning is the method of probing a device or network to identify which communication ports are open, closed, or filtered, and to determine which services are actively running on those ports.
By sending specific TCP or UDP requests to targeted port numbers and analyzing the responses, a port scan reveals how a device is configured, what applications are exposed, and where potential entry points exist.
In simple terms, port scanning helps you discover which doors in your network are open and whether they should be.
Beyond discovering open ports, it’s important to understand how port scanning differs from other related scanning methods.
How port scanning works
Port scanning follows a structured, multi-stage process designed to detect which network services are accessible on a target device or subnet.
- Identify target hosts: The scanner determines which IP addresses to probe - a single host, a range, or entire subnets.
- Select ports: Specific ports or port ranges are chosen based on what services need to be checked (e.g., 22 for SSH, 443 for HTTPS).
- Send probes: The scanner sends TCP, UDP, or ICMP-based requests to the target ports.
- Analyze responses: Each port reply is observed and interpreted to classify its state as open, closed, or filtered.
This step-by-step evaluation builds a clear picture of the device’s service exposure and its network security posture.
Port scanning vs network scanning vs vulnerability scanning
Port scanning is often confused with network scanning . While they complement each other and are commonly performed together, they serve different purposes in improving network visibility, one focuses on identifying devices, while the other focuses on identifying services running on those devices.
- Network scanning identifies which devices are present and gathers basic attributes like IP, MAC address, and OS hints, essentially answering who is on the network.
- Port scanning goes a layer deeper by revealing the services running on those devices and the ports exposed to communication, answering what they are running.
- Also, there is vulnerability scanning. Vulnerability scanning goes a step further by evaluating those discovered services for exploitable weaknesses or misconfigurations, answering if is it secure.
| Scan type | What it identifies | Primary purpose | Key questions answered |
|---|---|---|---|
| Network scanning | Discovers devices on the network and collects attributes like IP address, MAC address, and basic OS details. | Improves network visibility by mapping who is connected. | Who is on the network? |
| Port scanning | Identifies open, closed, or filtered ports and the services running on them. | Reveals communication endpoints and service exposure. | What are those devices running? |
| Vulnerability scanning | Checks discovered services and configurations for security weaknesses, missing patches, or exploitable flaws. | Assesses security posture and identifies risks. | Is it secure? |
Port scanning acts as the critical bridge between discovering a device and evaluating its risk posture.
Are all port scans a threat? Legitimate vs malicious port scanning
Port scanning by itself isn’t harmful, the intent behind it is what makes it defensive or offensive . IT and security teams rely on port scans for asset discovery, troubleshooting, service checks, firewall testing, and compliance validation. These scans help administrators reduce risk by identifying exposed services before attackers do.
On the other hand, cybercriminals use the same scanning techniques for reconnaissance. They look for outdated services, weak or misconfigured ports, and potential entry points for lateral movement or data exfiltration.
In other words, admins use port scanning to reduce risk. Attackers use it to find risk.
Why port scanning matters in security
Port scanning is one of the earliest and most critical phases in both defense and attacks. Attackers start with scans during reconnaissance to map reachable hosts, identify outdated services, and locate weak entry points for exploitation and lateral movement.
Security teams rely on the same technique proactively, detecting misconfigurations, validating access controls, and remediating exposures before attackers can weaponize them.
Because both sides depend on this step to understand network exposure, continuous monitoring of open ports becomes non-negotiable.
What makes port scanning essential
- Eliminates blind spots by revealing every accessible service.
- Detects unauthorized or rogue applications running on endpoints.
- Validates firewall and ACL configurations against policy.
- Identifies high-risk open ports before threat actors exploit them.
- Troubleshoots service availability issues quickly.
- Supports compliance requirements for controlled port exposure.
In short, visibility is the first step in defense. If you don’t scan your own ports, someone else will.
How scanners interpret TCP/IP responses
Port scanners rely heavily on TCP handshaking behavior to determine port state:
| Response | Scanner interpretation |
|---|---|
| SYN/ACK returned | The port is open and accepting connections. |
| RST/ACK returned | The port is closed but reachable. |
| No response / ICMP unreachable | The port is filtered by firewall or ACL. |
With UDP scanning, responses are less predictable, making interpretation more challenging. If there’s no response from the target, the port could be open or the packet may have been silently dropped by a firewall.
However, if an ICMP “Port Unreachable” message is returned, the port is considered closed. This ambiguity is why UDP scanning tends to be slower and less reliable compared to TCP-based scans.
Impact of firewalls, filtering, and IDS
Real-world networks introduce defensive mechanisms that influence scan accuracy and stealth:
| Control | What it does | Scan impact |
|---|---|---|
| Firewalls / ACLs | Block or drop packets | Ports appear filtered or hidden |
| Rate limiting | Slows repeated requests | Scans take longer, results delayed |
| Intrusion Detection Systems (IDS) | Flag unusual traffic patterns | Scans get detected or blocked |
| Packet inspection | Deep validation of traffic intent | Probes may be rejected or altered |
Types of port scanning techniques
Port scanning uses different probing methods depending on how much detail is needed, how defensive the target network is, and whether stealth is required.
Below are the most widely used scanning techniques categorized for clarity.
TCP-based port scanning techniques
TCP is the most widely used protocol for port scanning because its three-way handshake provides clear insight into how a port responds to connection attempts.
TCP connect scan
It initiates and finalizes the TCP three-step handshake of SYN, SYN-ACK, and ACK to ensure the port is actively responding to connection attempts.
- Highly accurate and reliable.
- Easily logged and detected by firewalls and intrusion detection systems.
TCP SYN (half-open) scan
Sends a SYN and interprets the response, but stops before the handshake completes.
- Stealthier and faster than full-connect scans.
- Commonly used in penetration testing to avoid raising alerts.
TCP ACK scan
Sends ACK packets to evaluate firewall behavior rather than service availability.
- Useful for discovering whether ports are filtered vs unfiltered.
- Does not confirm if a port is open or accepting connections.
TCP Window scan
Analyzes variations in TCP window sizes in ACK responses to infer port state (mainly on older stacks).
- Niche scan type due to reduced reliability on modern OS implementations.
- Historically used for more granular filtering analysis.
Stealth and evasion scans
Stealth and evasion scanning techniques modify TCP flags and packet behavior to bypass basic filtering and avoid detection. For instance, FIN, NULL, and Xmas scans send packets that violate the traditional SYN-based connection flow, exploiting subtle differences in how legacy or misconfigured systems respond to unexpected flags.
More advanced methods such as packet fragmentation, decoy hosts, or spoofed source addresses, attempt to obscure the true origin of the scan and disrupt correlation by firewalls or intrusion detection systems. While attackers commonly rely on these techniques to minimize visibility during reconnaissance, defenders use them to validate detection capabilities and strengthen perimeter enforcement against stealthy threats.
UDP Scanning
UDP scanning targets connection-less services such as DNS, DHCP, and SNMP to identify hosts running critical infrastructure protocols. Unlike TCP, UDP does not use handshakes, which makes interpreting scan results more challenging, a lack of response could indicate that the port is either open or that the packet was silently dropped by a firewall.
ICMP Port Unreachable messages can help validate closed ports, but these responses are often rate-limited, slowing down the process and reducing accuracy at scale. Despite these limitations, UDP scanning remains essential for uncovering exposure in widely used services that operate without TCP’s stateful communication.
Advanced port scanning techniques
Beyond traditional probes, several advanced port scanning techniques provide deeper context about the target environment.
- Idle (zombie) scans: can mask the scanner’s identity entirely by leveraging a third-party “zombie” host, making the activity challenging to trace.
- Service and version detection: This method examines application banners and protocol responses to identify the exact software and version running behind a port, enabling precise vulnerability assessment.
- OS fingerprinting: Can help analyze characteristics such as TCP/IP stack behavior, window size, and TTL values to infer the operating system of the host.
Together, these specialized methods extend port scanning from basic visibility into rich situational awareness and risk prioritization.
Comparing port scanning techniques
| Technique group | Stealth | Accuracy | Best for |
|---|---|---|---|
| TCP connect | Low | High | Trusted enterprise scanning |
| SYN / half-open | Medium | High | Routine security assessments |
| FIN / NULL / Xmas | High | Medium | Firewall/IDS evasion validation |
| UDP scans | Medium | Medium | Monitoring UDP-based services |
| Zombie / OS / Version | Very high | High | Threat hunting + advanced defense |
3 ways to detect and defend against port scanning
Attackers often start by scanning networks for weaknesses, organizations must be able to spot and block unauthorized scans before they turn into full-scale intrusions. A layered defense ensures that exposed services remain visible only to trusted users and tools.
- Firewall rules and intelligent rate limits: Modern firewalls can identify unusual scanning behavior, such as sequential access to many ports or repeated failed connection attempts. By enforcing deny-by-default policies, filtering unused ports, and applying connection throttling, you can reduce the success of aggressive scanning attempts. Limiting inbound traffic to essential services only dramatically reduces your exposed attack surface.
- IDS/IPS and anomaly detection: Intrusion Detection and Prevention Systems (IDS/IPS) analyze network traffic in real time to identify scan signatures, unexpected TCP flag combinations, or traffic spikes targeting port ranges. When paired with behavior-based analytics, they can catch stealthy scans like FIN, NULL, or Xmas attempts that bypass basic firewall rules.
- Log analysis and proactive alerting: Every scanning attempt leaves patterns in firewall logs, connection logs, and event telemetry. Centralized log monitoring with alerting policies helps teams detect early probing activity, giving them time to investigate and respond. Integrating SIEM solutions helps correlate scan activity with other suspicious events, a key component of zero-trust readiness.
Best practices for safe and compliant port scanning
Port scanning is a powerful technique, but it must be conducted responsibly to protect system performance, user privacy, and legal compliance.
The following best practices ensure that scanning strengthens security without causing operational issues.
1. Maintain a clear inventory of allowed ports and services: Admins should continuously audit which ports are permitted, what services run on them, and whether those services are justified, especially on production servers. This information must be visible and up to date in the organization’s asset inventory. Tracking expected vs. actual port states helps identify unauthorized services, unexpected exposures, and configuration drift early, before they become security risks.
2. Always operate with authorization: Port scanning without permission can violate security laws and trigger incident responses. Instead of relying on manual approvals often impractical in large enterprises, use a port scanning tool that supports role-based access control (RBAC) and policy-driven authorization. This ensures only approved users can initiate scans, limits who can target sensitive ranges, and enforces scanning boundaries automatically. The general rule remains the same: scan only the networks and assets you own, and never probe external IPs unless the stakeholders have explicitly allowed it.
3. Choose the right targets at the right time: Scanning production servers during business hours may impact performance or traffic flow. Align scans with operational windows, change control policies, and maintenance cycles to avoid disruptions.
4. Limit scan intensity and speed: Aggressive scans can overwhelm network equipment, trigger firewall defenses, or flag false positives.
Adjust rate limits and use progressive scanning:
- Scan critical services first.
- Start with common ports.
- Increase coverage gradually.
This keeps scanning safe, predictable, and workload-friendly.
5. Interpret results correctly: An open port does not automatically mean a vulnerability, it may be a legitimate service required for operations. Likewise, filtered ports may still be reachable under certain routing paths or ACLs.
Accurate interpretation considers:
- Service purpose.
- Patch level and configuration.
- Exposure to untrusted networks.
Security decisions require context, not assumptions.
6. Document findings and drive remediation: Port scanning should feed directly into ongoing security hardening:
- Log exposed services.
- Tag risks clearly based on severity.
- Track remediation steps and ownership.
- Rescan to validate closure.
This ensures security improvements are measurable and continuous, not one-time exercises. In short, scan responsibly, analyze carefully, and act on insights. The goal is not to find open ports, but to secure the ones that matter.
How OpUtils helps with port scanning
OpUtils includes a lightweight, on-premises Port Scanner that helps administrators quickly detect open services, validate device security, and troubleshoot connectivity issues across their network. It is designed for real-world IT operations where speed, accuracy, and visibility matter more than complex scanning profiles.
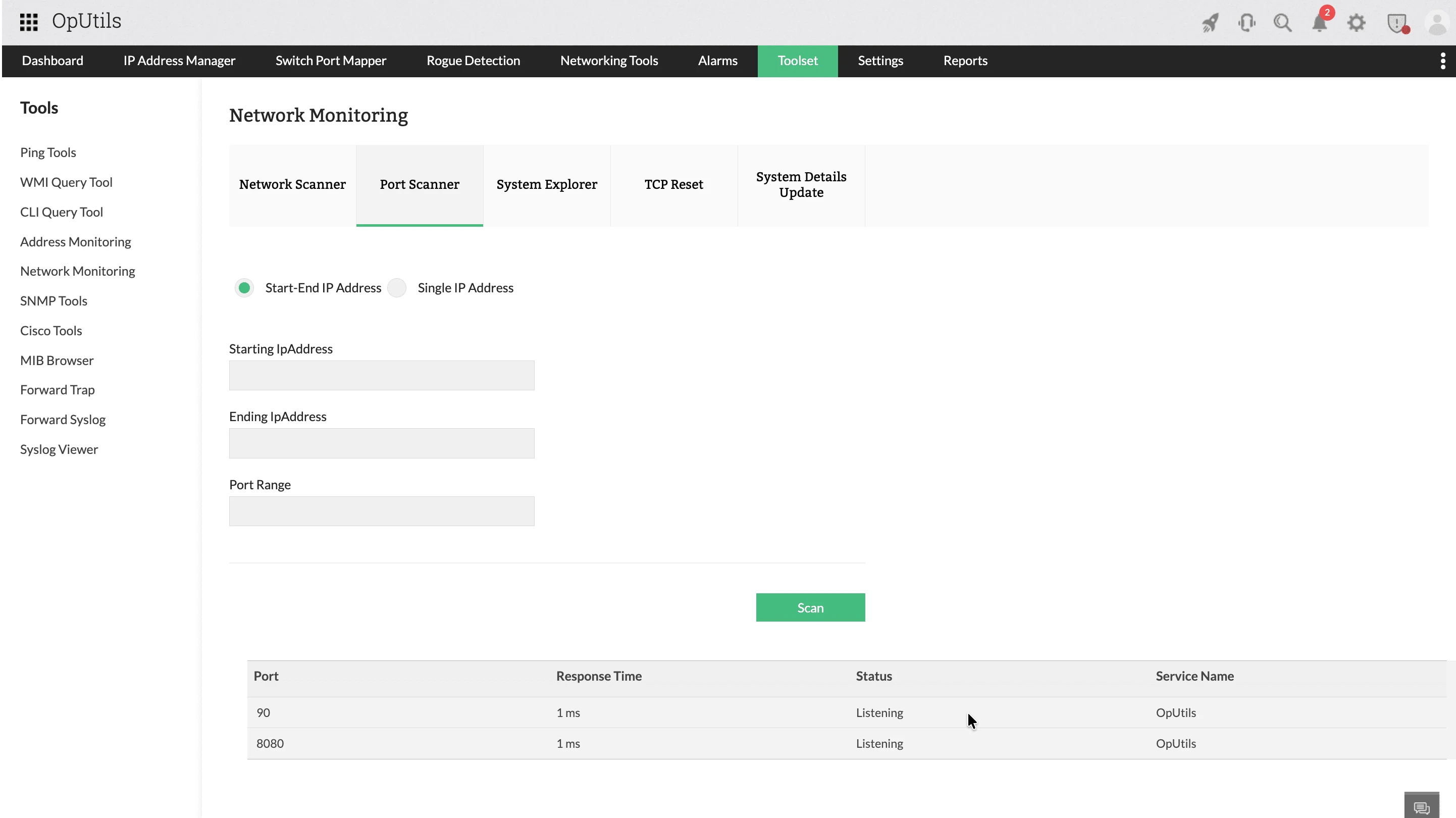
Scan single IPs or full IP ranges
The Port Scanner allows you to scan:
- A single IP address for quick diagnostics.
- A start-end IP range to assess multiple hosts in one run.
This flexibility makes it useful for both ad-hoc troubleshooting and broader service discovery exercises.
Customizable port ranges
Admins can define any port range to scan from a few critical ports to the full 0 - 65535 spectrum. This gives complete control over:
- Checking specific services (e.g., 22, 53, 80, 443, 3389).
- Validating firewall/ACL changes.
- Detecting unauthorized services.
- Troubleshooting application-level connectivity.
- Clear, actionable scan results .
Each scan returns a structured table showing:
- Port number.
- Response time.
- Port state (open, listening, closed).
- Detected service name, where available.
These insights help identify misconfigurations, unnecessary exposures, and service outages immediately.
Accurate Layer-2 and Layer-3 device discovery
Before ports are scanned, OpUtils already knows which devices exist in the network with the help of its built-in IP scanning and ARP -based L2 discovery capabilities. This prevents scanning dead addresses and reduces false positives.
It correlates:
- IP addresses
- MAC addresses
- Switch port details
- Vendor information
- Subnet /VLAN details
With this device context, port scan results clearly show which service runs on which port for each device.
Scheduled scans and role-based access
OpUtils lets you automate port scans at periodic intervals to continuously track service exposure. Role-based controls ensure that only authorized users can initiate or view scans, supporting internal security and compliance needs.
Correlation with rogue detection and switch port mapping
When combined with other OpUtils modules:
- Rogue Detection flags unknown devices that obtain an IP address during network discovery.
- Switch Port Mapper shows exactly where the device is physically connected.
- Admins can quickly verify if suspicious hosts are legitimate or unauthorized.
This correlation drastically improves incident response time.
Seamless DDI integration
Because OpUtils includes IP address management capabilities:
- Each port scan result is tied to a specific IP assignment.
- DHCP lease info and DNS records help identify device roles.
- Conflicts, stale records, and mismatches become easier to spot.
Port scanning becomes more reliable when backed by accurate IPAM data.
Audit-ready reports
OpUtils generates reports that help with:
- Security audits
- Compliance checks
- Firewall rule verification
- Change management documentation
Admins can track how exposure changes over time and ensure that risky ports are closed or justified.
Fully on-premises deployment
Since OpUtils is deployed entirely on-premises:
- Scanning stays inside the network.
- No data leaves your environment.
- It remains compliant with internal and government regulations that restrict external scanning tools.
This makes it ideal for regulated industries, isolated networks, and environments that do not permit cloud-based scanning.
Interested in trying it out? Download our 30-day free trial and explore OpUtils port scanning capabilities all by yourself.
FAQs on port scanning
1. Is port scanning legal?
Port scanning is legal only when you have explicit authorization. Scanning your own network or approved assets is permitted. Scanning external networks without consent can violate laws like the Computer Fraud and Abuse Act (CFAA) and may be treated as reconnaissance by attackers.
2. Are open ports always dangerous?
Open ports aren’t inherently dangerous. They simply indicate that a service is listening for connections. The risk arises when that service is unnecessary, outdated, misconfigured, or exposed to the internet without proper controls. This is why organizations should routinely review which ports are open and ensure they align with the system’s intended role.
3. Can I block or prevent port scans?
You can’t completely prevent port scans, but you can reduce their visibility and impact by using firewalls and ACLs, rate limiting, intrusion detection and prevention systems, geo/IP filtering, network segmentation, and deception techniques like honeypots. Together, these measures make scanning harder, slower, and far less informative for attackers.
4. Does port scanning slow down networks?
Light, well-configured scans have minimal impact. However, aggressive or high-intensity scans can increase CPU load, trigger IDS alerts, or stress fragile OT/IoT devices. Adjusting scan speed, timing, and concurrency prevents disruptions.
5. How often should I scan?
Most organizations scan:
- Continuously or daily for critical servers and internet-facing systems.
- Weekly or monthly for internal networks.
- Immediately after changes such as firewall updates, software deployments, or onboarding new devices.
6. Which ports should be prioritized?
Prioritize ports associated with high-risk services:
- Remote access: 22, 23, 3389
- Web: 80, 443, 8080
- Databases: 1433, 3306, 1521
- File sharing: 445, 139
- Mail: 25, 587, 110, 143
Then scan service-specific or custom ports based on the device’s purpose.
7. Can port scanning detect malware?
Indirectly, yes. A port scan can highlight unusual open ports, unexpected services, or changes in how a device behaves, all of which can hint at malware or unauthorized remote-access tools. For instance, if a regular workstation suddenly exposes an SSH or RDP port, that’s a clear sign something needs attention. You’ll still need dedicated malware-detection tools to confirm it, but port scans can give you the first warning.
8. How do honeypots and deception tools help against port scanning?
Honeypots and tarpits create fake services that attract malicious scanners, slow their probing, and gather intelligence. Fake banners and decoys mislead attackers about the real environment, giving defenders early visibility into reconnaissance attempts.
9. How has modern infrastructure changed port scanning?
Port scanning now behaves differently due to:
- Cloud networks, where security groups and ephemeral assets limit traditional scanning.
- OT/IoT systems, which require very low-intensity scans.
- IPv6, which shifts focus from brute-force sweeps to inventory accuracy.
- Continuous monitoring, where scanning is automated and tied to SIEM/SOAR.
Scanning has evolved from a one-time recon technique into an ongoing operational and security control.
Have more questions? Request for a one-on-one demo and we will connect you with the right product expert.
Ensure simplified port scanning with OpUtils
Try OpUtils for free today

