Microsoft Entra ID MFA (formerly Azure AD MFA) is a cloud-based identity verification feature in Microsoft Entra ID that secures user and application sign-ins by prompting them for an additional authentication factor, like a unique six digit code, fingerprint, or a compliant device for the sign-in process, making it significantly harder for attackers to gain access.
Microsoft Entra ID MFA can also make use of a combination of other factors such as the location of sign-ins, the time of signing in, and the role of the user to verify the authenticity of the sign-in request, making it more secure even when some of the usual factors are compromised.
Microsoft Entra ID MFA can secure more than your Microsoft Entra ID sign-ins. It can also secure your organization's applications against unauthorized access. Here’s a closer look at what Microsoft Entra ID MFA can secure.
For the users in an organization, especially those relying on a cloud directory like Microsoft Entra ID, it is essential to trust in authentication factors that cannot be cloned, guessed, or replicated digitally. Leveraging unique, non-replicable authentication methods ensures robust security and is a staple requirement for an IAM environment.
Microsoft Entra ID MFA is seamlessly integrated with Microsoft Entra ID, which brings in comprehensive security advantages for your Microsoft 365 users. These include:
When users undergo Microsoft Entra ID MFA, their identity will be verified by using two or more of the following verification methods:
Administrators can configure verification methods for the entire tenant or for specific groups. If administrators do not enforce a particular method, users can select their preferred authentication method using the Microsoft Entra Self-Service Portal.
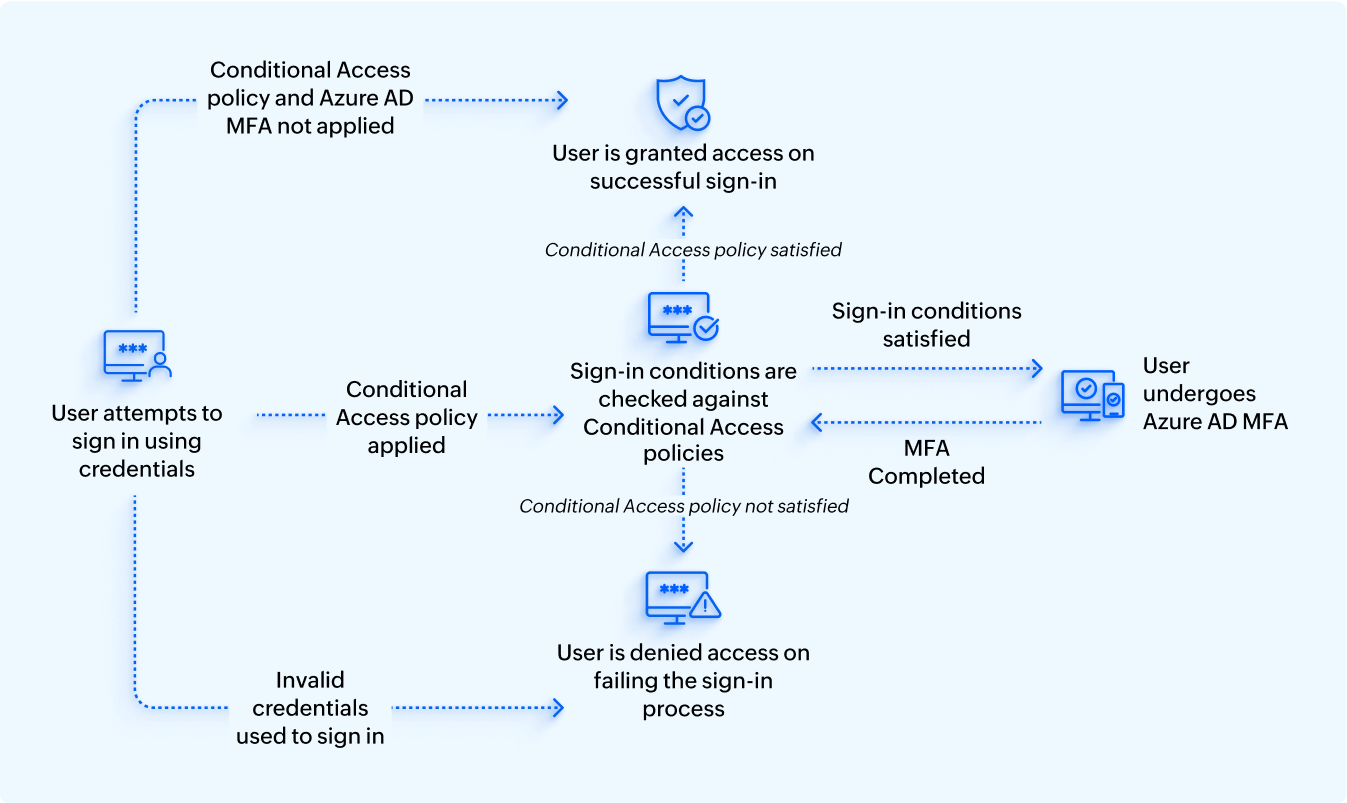
The verification methods can also be applied on a basis of other factors, such as sign-in location or user roles,to control the access granted based on these factors. This is achieved using Conditional Access policies.
Microsoft Entra ID Conditional Access policies are a set of rules that control the access a user is granted based on physical factors and not authentication methods. This guarantees that only authorized users using compliant devices from approved locations can access crucial resources.
For example: If a user is trying to sign in from their typical sign-in location using their compliant device, they will be authenticated with the default configuration. However, when they try to login from a different location or a different device, they will be made to undergo a second authentication prompt to ensure that their default authentication methods are not compromised. These can also be applied when accessing certain resources or applications, too. If the user is accessing an application before or after a certain time period, the policy can be configured to block access for them until they retry it during the specified time period.
You can also use Conditional Access policies to disable MFA prompts when users log in under conditions that you can trust or for low-risk users who access a resource frequently.
Some common use cases where Conditional Access policies can be implemented include:
If you wish to enable MFA only for the above-mentioned scenarios for your entire tenant, you can enable security defaults to implement MFA using Microsoft Authenticator as the second authentication factor.
Microsoft Entra ID MFA can be enabled for all users in your organization. However, the extent of its application is determined by the licenses applied to your users.
Users who are assigned the Global Administrator role can enable Microsoft Entra ID MFA with two-step verification at no additional cost.
Using Conditional Access policies requires the Microsoft Entra ID P1 license as a minimum requirement. Implementing MFA with risk-based policies that identify high-risk users and sign-ins dynamically requires the use of Microsoft Entra ID Protection, which requires a Microsoft Entra ID P2 license. When said licenses required for Conditional Access policies expire, the policies aren't automatically disabled or deleted. However, you can no longer update them.
For users of Microsoft Entra ID Free licenses, you can use security defaults to prompt all users for MFA, but you don't have granular control over enabled users or scenarios.
With all of the features of Microsoft Entra ID MFA on the table, we can now visualize how the entire process of verifying user identities works.
Microsoft Entra ID MFA can be implemented in four different ways depending on the requirements of your organization. These are:
ManageEngine ADSelfService Plus offers adaptive MFA with 20 different authenticators, including Microsoft Entra ID MFA. You can use MFA to protect on-premises and cloud application logins, computers, VPNs, OWA, and self-service password management tasks. With ADSelfService Plus, you can customize the MFA authentication process for various user accounts based on their OU and group memberships, allowing you to secure your privileged accounts and activities against cyberthreats.
Microsoft Entra ID MFA is a cloud-based identity verification feature in Microsoft Entra ID that enhances security by requiring users to use multiple forms of identification during the sign-in process. This increases the difficulty for attackers to obtain unauthorized access.
Verification methods include Microsoft Authenticator, Windows Hello for Business, FIDO2 passkeys, certificate-based authentication, external authentication methods, OAuth hardware and software tokens, SMS, and voice calls.
Microsoft Entra ID MFA primarily secures user-sign ins into Microsoft 365 applications and admin portals. It also secures access to registered on-premises, third-party, and custom applications and VPNs and network accesses.
Microsoft Entra ID MFA can be implemented using four methods:
To implement Microsoft Entra ID MFA, users must have the appropriate licenses. To implement Conditional Access policies, a Microsoft Entra ID P1 license is essential, while risk-based policies necessitate a Microsoft Entra ID P2 license. For tenants with Microsoft Entra ID Free licenses, security defaults can be enabled to implement tenant-wide MFA implementation.
You can skip authenticating some users with Microsoft Entra ID MFA by creating a Conditional Access policy that grants them access to the required applications without a second factor of authentication. It is recommended to use it sparingly, with conditions like approved locations and login within business hours.