Configuring SAML SSO for Cisco Meraki
These steps will guide you through setting up the single sign-on functionality between ADSelfService Plus and Cisco Meraki.
Prerequisite
-
Login to ADSelfService Plus as an administrator.
- Navigate to Configuration → Self-Service → Password Sync/Single Sign On → Add Application, and select Cisco Meraki from the applications displayed.
Note: You can also find Cisco Meraki application that you need from the search bar located in the left pane or the alphabet wise navigation option in the right pane.
-
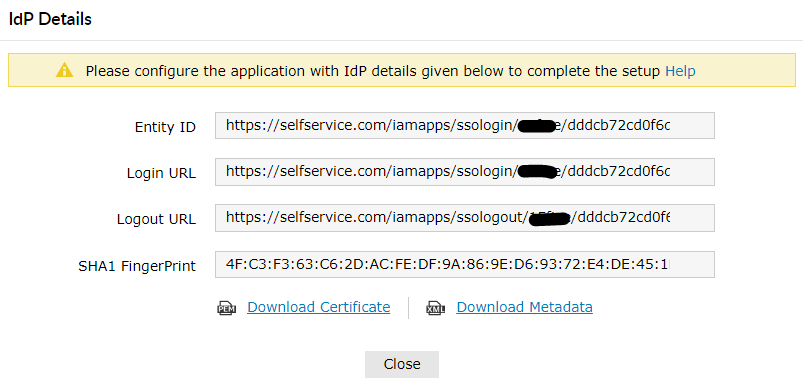
Click IdP details in the top-right corner of the screen.
- In the pop-up that appears, copy the Login URL, Logout URL and Sha1 FingerPrint .
Cisco Meraki(Service Provider) configuration steps
-
Login to Meraki with an administrator’s credentials. (https://<subdomain>.meraki.com)
-
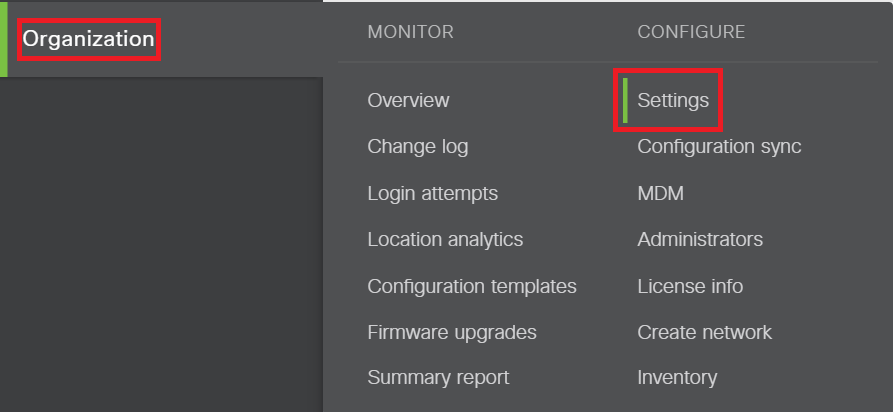
Navigate to Organization → Settings → SAML Configuration.
-
Paste the logout URL copied in Step 4 of Prerequisite in the SLO logout URL field.
-
Paste the SHA1 FingerPrint value copied in Step 4 of Prerequisite in X.509 cert SHA1 fingerprint field.
-
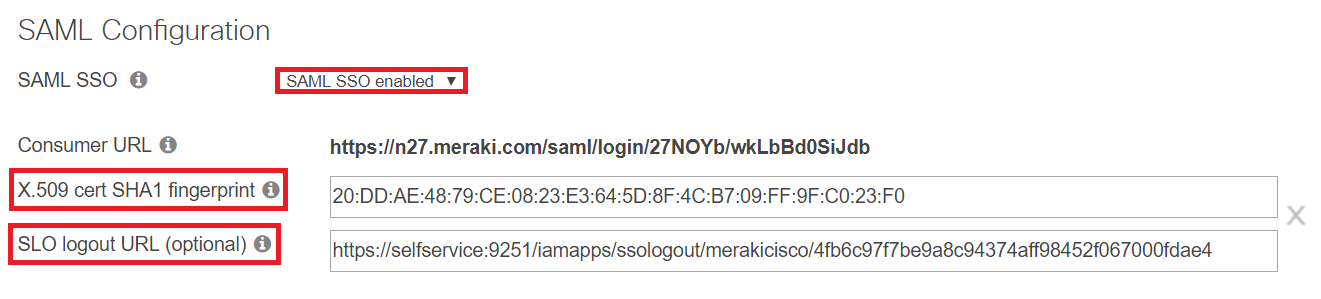
Copy the Consumer URL. We will need this in a later step.
-
Click Save Changes.
Important :
Please make sure in Cisco Meraki the role (Organization > Administrators) maps to the department attribute and the username maps to the mail attribute in Active Directory.
ADSelfService Plus (Identity Provider) configuration steps
-
Now, switch to ADSelfService Plus’ Meraki Cisc configuration page.
-
Enter the Application Name and Description.
-
In the Assign Policies field, select the policies for which SSO need to be enabled.
Note:ADSelfService Plus allows you to create OU and group-based policies for your AD domains. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy.
-
Select Enable Single Sign-On.
-
Enter the Domain Name of your Cisco Meraki account. For example, if you use johndoe@thinktodaytech.com to log in to Cisco Meraki, then thinktodaytech.com is the domain name.
-
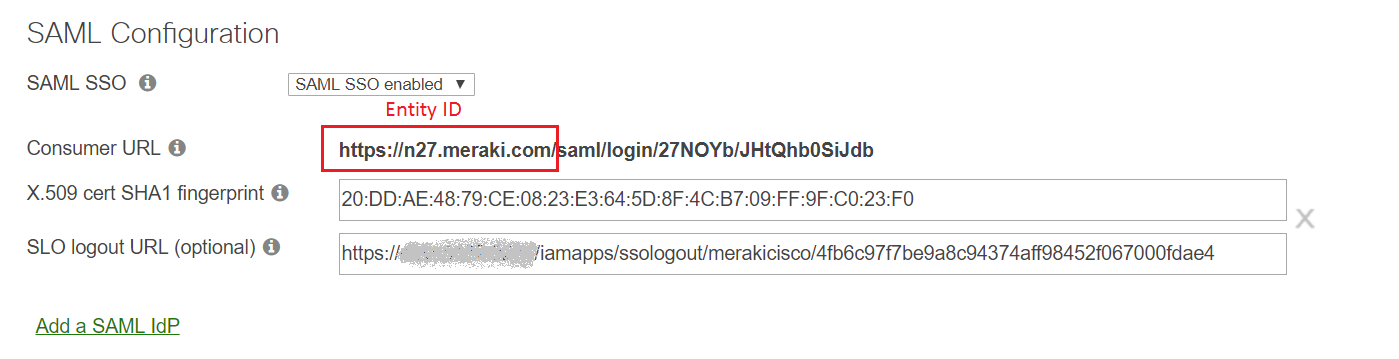
Paste the Consumer URL from Step 5 of Cisco Meraki configuration in the ACS URL field.
-
Paste the domain and subdomain part (as shown in the image below) of the Consumer URL in the Entity ID field.
- In the Name ID Format field, choose the format for the user login attribute value specific to the application.
Note: Use Unspecified as the default option if you are unsure about the format of the login attribute value used by the application
-
Click Add Application
Note:
For Meraki Cisco, single sign-on is supported only for IDP initiated flow.
Don't see what you're looking for?
-
Visit our community
Post your questions in the forum.
-
Request additional resources
Send us your requirements.
-
Need implementation assistance?
Try OnboardPro



