Configuring MFA for FTD VPN using RADIUS
This guide provides steps for enabling multi-factor authentication (MFA) for Cisco's Firepower Threat Defense (FTD) using ManageEngine ADSelfService Plus.
To enable RADIUS-based authentication for Cisco FTD, the MFA for VPN supports the following authentication methods in addition to the default username and password-based authentication:
- Push Notification Authentication
- Fingerprint/Face ID Authentication
- ADSelfService Plus TOTP Authentication
- Google Authenticator
- Microsoft Authenticator
- Yubico OTP (hardware key authentication)
The RADIUS-based MFA process for Cisco FTD using ADSelfService Plus
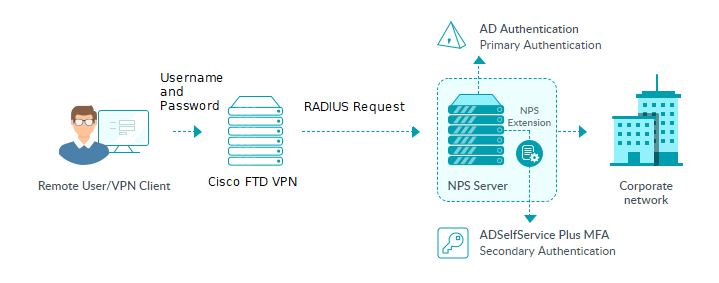
Configuration process
Prerequisites:
Step 1. Configuring MFA in ADSelfService Plus
- Log in to ADSelfService Plus as an admin.
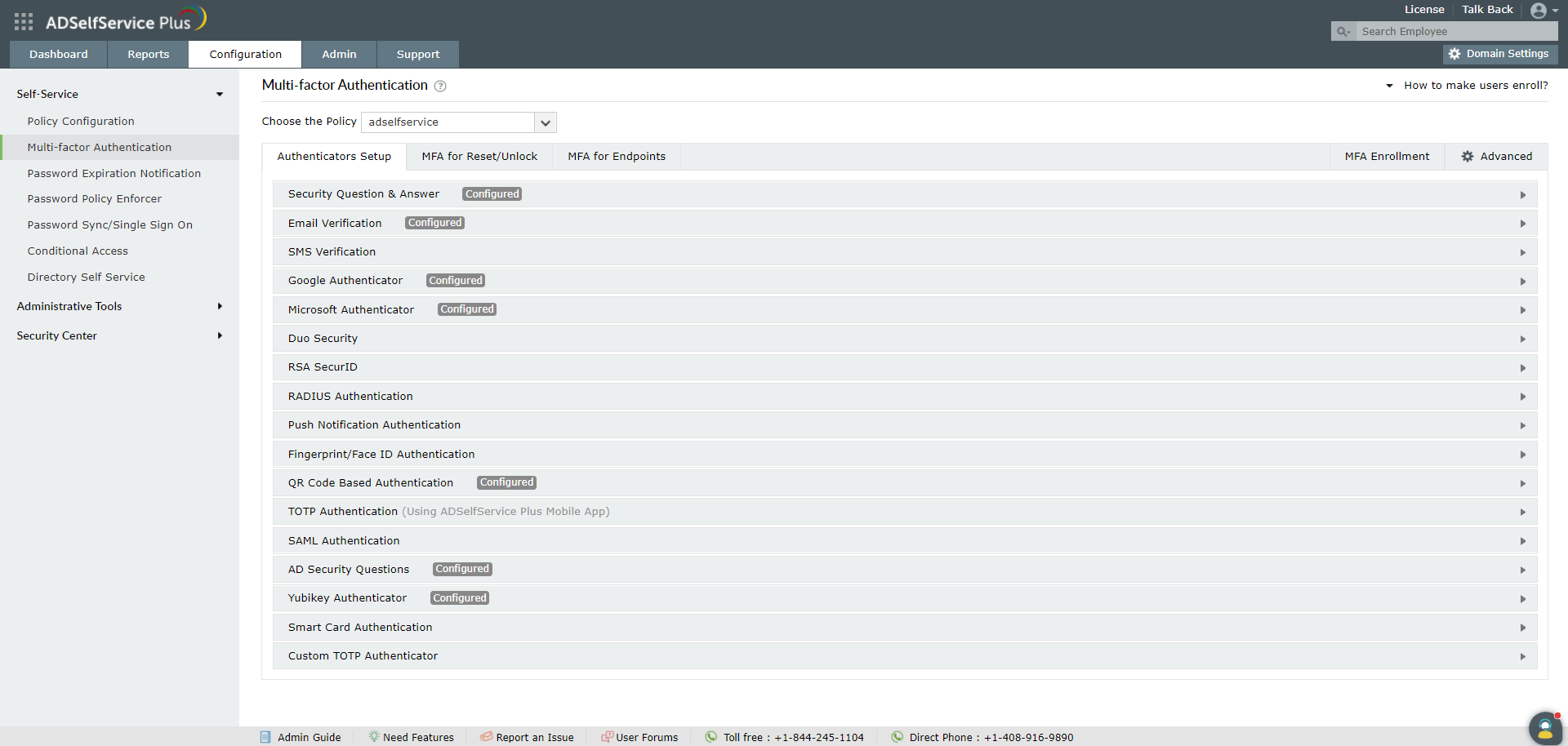
- Go to Configuration → Self-Service → Multi-Factor Authentication → Authenticators.
- Configure the authentication methods required.
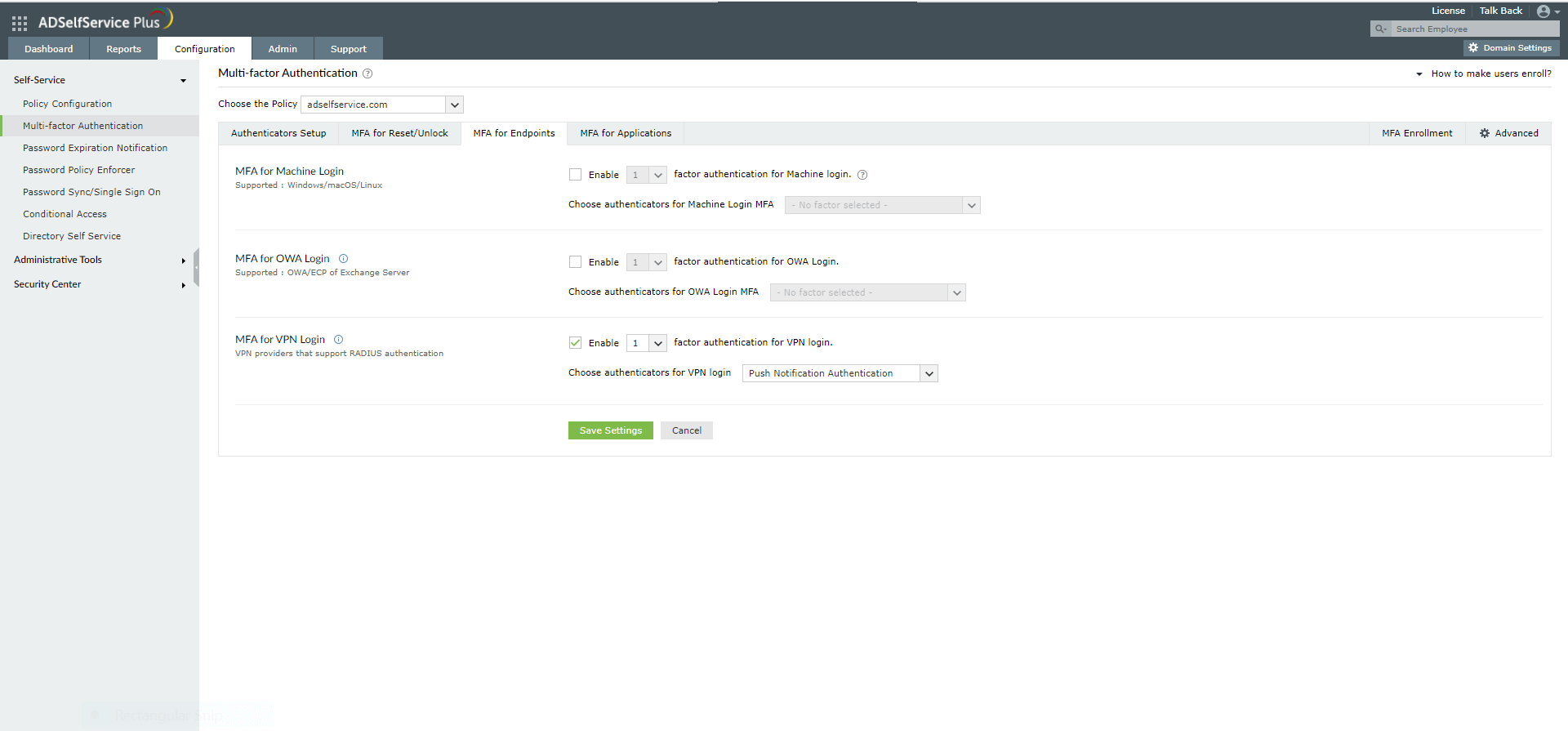
- Go to MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This policy will determine the users for whom MFA for VPN and endpoint login will be enabled. To learn more about creating an organizational unit or a group-based policy, click here.
- In the MFA for VPN Login section, select the checkbox next to Select the authenticators required. Choose the number of authentication factors to be enforced. Select the authentication methods to be used. The authentication methods listed can also be rearranged by dragging and dropping at the necessary position.
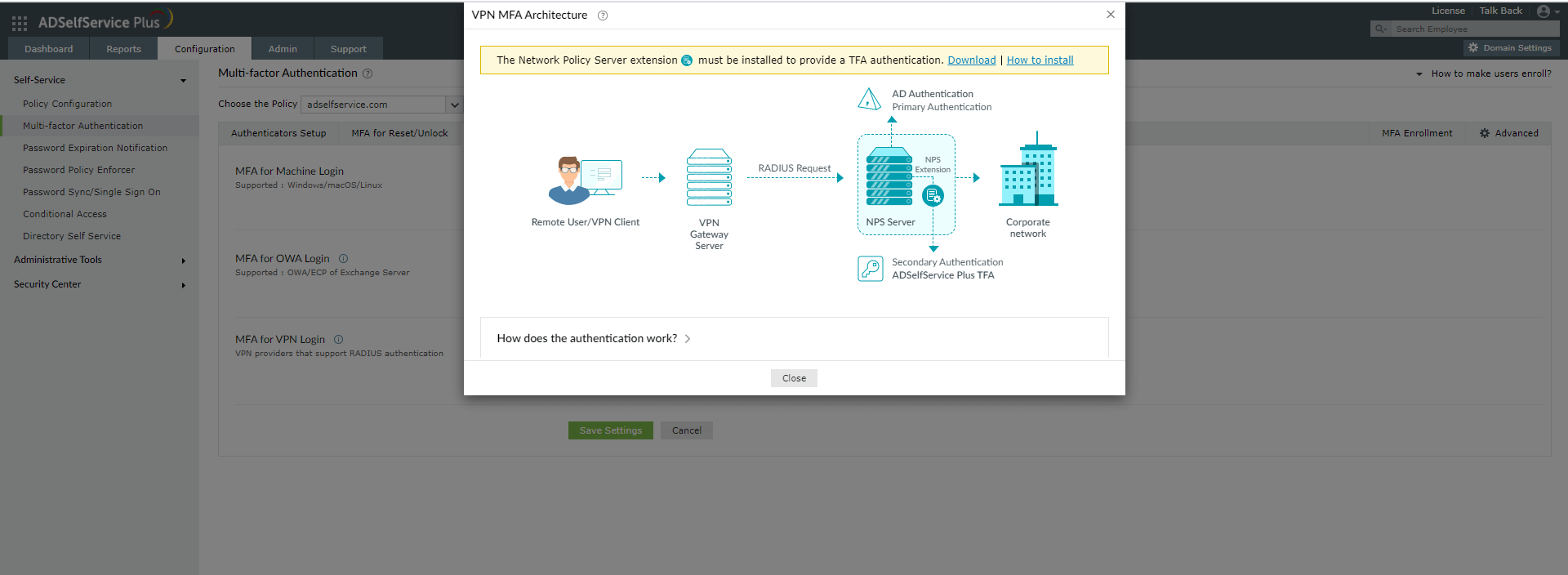
- Click the help icon next to MFA for VPN.
- Download the NPS extension using the Download link provided in the pop-up that appears.
Step 2. Install the NPS Extension
- Copy the extension file (ADSSPNPSExtension.zip) to the Windows server, which you have configured as the RADIUS server. Extract the ZIP file’s content and save it in a location.
- Open Windows PowerShell (x64) as administrator and navigate to the folder where the extension files content is located.
- Execute the following command:
PS C:\> .\setupNpsExtension.ps1 Install
Note: If the NPS extension plug-in has to be uninstalled or updated to newer versions and configuration data, enter Uninstall and Updated respectively instead of Install.
- After installation, you will be prompted to restart the NPS Windows service. Proceed with the restart.
- Configure a RADIUS client in the NPS service for ADSelfService Plus. Set a shared secret during configuration for future use.
Step 3. Configure the Cisco FTD using FMC
- Log in to the Firepower Management Center (FMC) console that manages your FTD SSL VPN devices.
- Go to Objects → Object Management → RADIUS Server Group and click Add RADIUS Server Group.
- Enter the following information under Add RADIUS Server Group:
- Name: Enter any name without any spaces.
- Description: ADSelfServicePlus RADIUS server group.
- Group Accounting Mode: Leave as Single.
- Retry Interval: Leave as 10.
- Realms: There is no need to select a realm.
- Under RADIUS Servers, click the green plus sign to add an NPS server.
- Enter the information below under New RADIUS Server:
IP Address/Hostname: The hostname or IP address of your NPS server.
Authentication Port: 1812 (or whichever port you specified in your authproxy.cfg file).
Key: The exact shared secret set during RADIUS client configuration.
Confirm Key: Reenter the shared secret.
Server Accounting Port: Defaults to 1813 (this value does not matter because the NPS Extension does not support RADIUS Accounting).
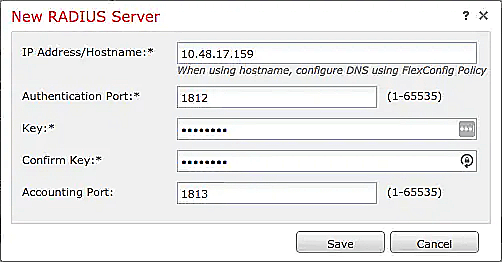
Timeout: Set a minimum of 60 seconds.
Connect using: Depending on connectivity from the FTD to the NPS server, elect either Routed or Specific Interface.
Redirect ACL: Select or add the redirect ACL (only if using FTD with ISE).
- Once you have added the NPS server to the group, click Save to create the new RADIUS server group.
- Go to Devices → VPN → Remote Access.
- Click on the VPN configuration for which MFA should be configured.
- Under Connection Profiles, click the pencil icon on the far right to select the connection profile that you want to start using the RADIUS server group.
- Under Edit Connection Profile, click AAA.
- Modify the Authentication Server value to the RADIUS server group created earlier.
- The Authorization Server or Accounting Server does not have to be selected.
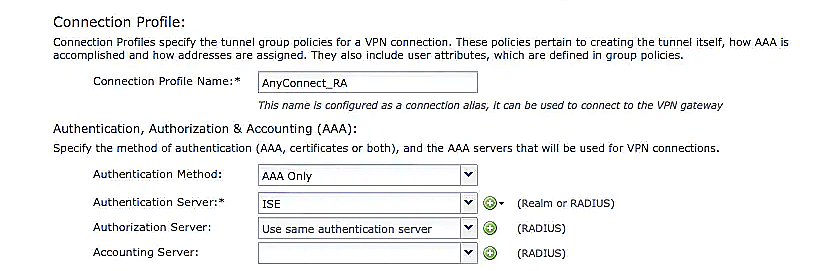
- Do not configure the Password Management settings.
- Click Save under Edit Connection Profile.
- Click Save next to You have unsaved changes.
- Click Deploy.
- Select the FTD device(s) to which you want to push the new Remote Access VPN configuration with MFA.
- Click Deploy.
- Upon deployment completion, the status Deployment to device successful will be displayed.
Features of ADSelfService Plus
Highlights of ADSelfService Plus
Allow Active Directory users to self-service their password resets and account unlock tasks, freeing them from lengthy help desk calls.
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Active Directory credentials.
Intimate Active Directory users of their impending password and account expiry via email and SMS notifications.
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Strong passwords resist various hacking threats. Enforce Active Directory users to adhere to compliant passwords by displaying password complexity requirements.
Enable Active Directory users to update their latest information themselves. Quick search features help admins scout for information using search keys like contact numbers.