The NIS2 Directive establishes EU-wide cybersecurity legislation, building on the original Network and Information Security (NIS) Directive. Its primary goal is to standardize cybersecurity measures across all EU Member States, fostering a unified approach to protecting digital infrastructure. NIS2 seeks to align efforts across the EU in addressing the increasing threat of cyberattacks by promoting best practices and consistent security standards.
To be compliant with the NIS2 Directive, organizations must enforce the security requirements discussed in the sections below.
The NIS2 Directive aims to enhance Europe’s resilience to current and emerging cyberthreats by introducing new mandates for organizations across these four main areas:
Organizations must take measures such as incident management, stronger supply chain security, enhanced network security, better access control, and encryption to minimize cyber risks.
Corporate leadership is required to oversee, approve, and participate in cybersecurity training. If security incidents are not properly addressed, the management team may face penalties.
Essential and important entities must promptly report significant security incidents within the NIS2-mandated specific notification deadlines, such as the "early warning" requirement within 24 hours.
Organizations must prepare a business continuity plan for major cyber incidents, covering system recovery, emergency procedures, and establishing a crisis response team.
Beyond the four key requirement areas, NIS2 requires essential and important entities to implement these baseline security measures targeting specific cyberthreats:
Organizations must have risk assessments and security policies tailored to their information systems. These assessments should thoroughly evaluate potential threats, vulnerabilities, data sensitivity, system architecture, and attack vectors.
Organizations must implement measures like MFA, continuous authentication solutions, and text encryption, as needed.
An incident response plan must be developed to address potential security breaches quickly. It should outline rapid actions to mitigate risks and protect sensitive assets from unauthorized access or compromise.
Organizations must set up policies to evaluate the effectiveness of their security measures regularly. This includes routine audits to assess security protocols, identify vulnerabilities, and ensure the overall strength of your security infrastructure.
Security procedures must be implemented for employees who have access to sensitive data, and policies must be established for data access. Organizations must maintain an overview of all relevant assets to ensure they are utilized and managed effectively.
Policies must be created for using cryptography and encryption to manage sensitive data, outlining guidelines for protecting data at rest, in transit, and during processing.
A backup and recovery plan to maintain business operations following a security attack must be developed. Regular backups must be conducted, and a strategy for managing access to IT systems during and after an incident must be established.
Organizations must ensure the secure procurement, development, and operation of systems and establish policies for managing and reporting any vulnerabilities that might arise.
Organizations must implement stringent security measures for supply chains tailored to the vulnerabilities of each direct supplier and evaluate the overall security levels of all suppliers.
Organizations must provide training to both management and employees to improve their understanding of cybersecurity.
| NIS2 requirement | Requirement description | How ADSelfService Plus helps meet the requirement |
| Cybersecurity risk-management measures | ||
| Article 21.2.g | Shall implement basic cyber hygiene practices and cybersecurity training. | ADSelfService Plus promotes good password hygiene using strong password policies with settings pertaining to password length, special character usage, character repetition, and common pattern restriction. These settings are enforced during every end-user password change and reset action, which is secured using strong MFA methods.It also employs a password strength meter and informs the password complexity rules to employees, helping them understand what constitutes a strong password and encouraging them to choose accordingly. |
| Article 21.2.i | Shall implement human resources security, access control policies, and asset management. | With ADSelfService Plus, you can configure conditions to automate access decisions based on IP address, geolocation, time of access, and device used. You can also configure stringent MFA settings based on AD OUs and groups, ensuring that only authorized users can access necessary resources after successful identity verification. |
| Article 21.2.j | Shall use MFA or continuous authentication solutions (such as secured voice, video, and text communications) and secured emergency communication systems within the entity, where appropriate. | ADSelfService Plus provides strong, adaptive MFA with 20 different authentication factors, including the Fast Identity Online (FIDO) passkeys and biometrics, to safeguard identities and resources within the system. It enables you to configure two or more MFA factors, and the success of all factors is mandatory before access is granted. |
ADSelfService Plus provides adaptive MFA and strong password policies, ensuring your organizational identities are effectively secured for a comprehensive Zero Trust environment. The following are some highlights of ADSelfService Plus' Password Policy Enforcer and adaptive MFA capabilities:
Configure the minimum password length and the inclusion of alpha-numeric characters in passwords.
Restrict users from reusing any of their last four passwords during password creation.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
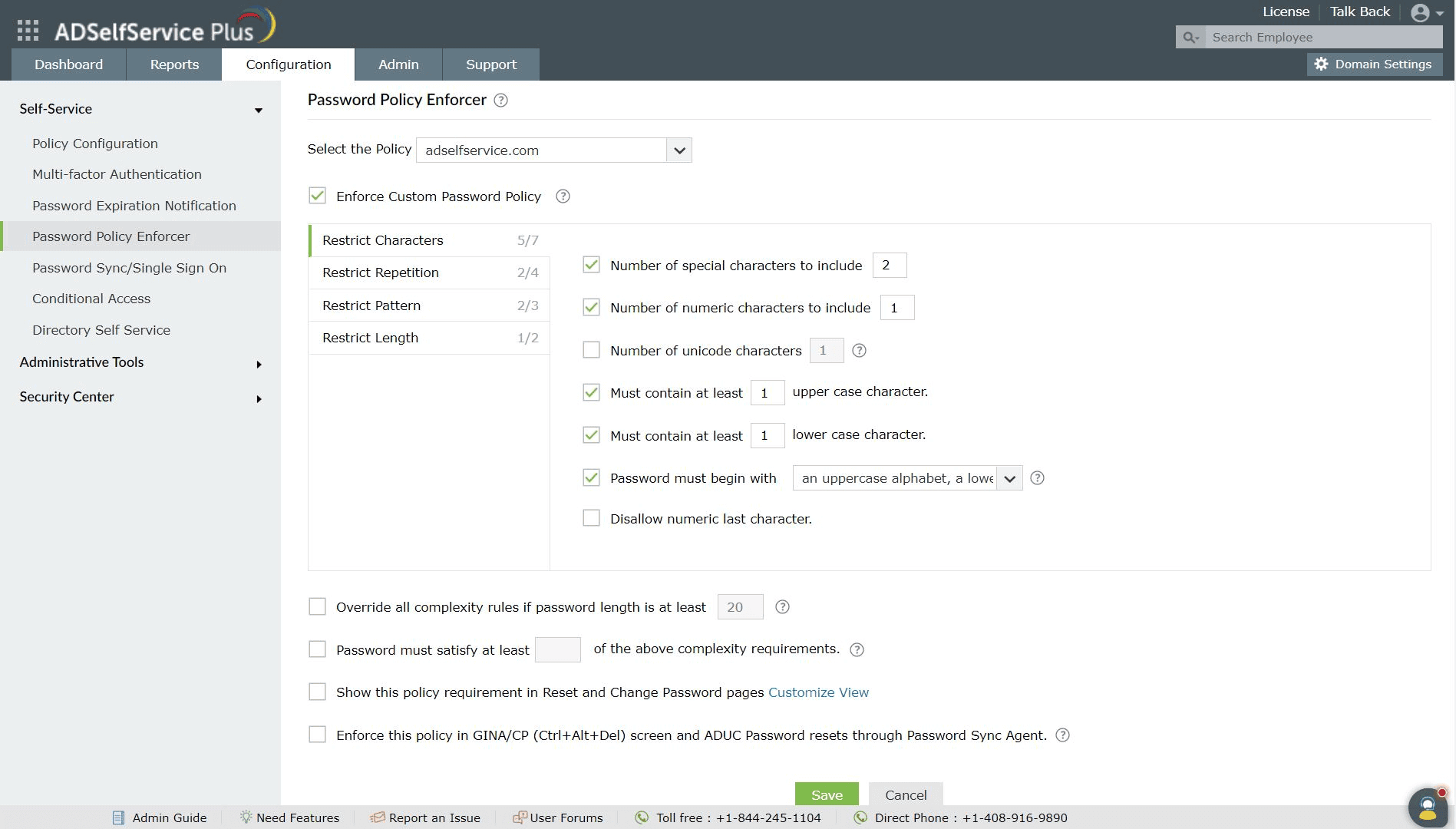
Configure the minimum password length and the inclusion of alpha-numeric characters in passwords.
Restrict users from reusing any of their last four passwords during password creation.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
Secure user access to all enterprise applications and endpoints in your network using MFA.
Choose from 20 different authenticators to verify your users' identities.

Secure user access to all enterprise applications and endpoints in your network using MFA.
Choose from 20 different authenticators to verify your users' identities.
Set up different MFA flows for different groups or departments in your organization.
Free Active Directory users from attending lengthy help desk calls by allowing them to self-service their password resets/ account unlock tasks. Hassle-free password change for Active Directory users with ADSelfService Plus ‘Change Password’ console.
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications with their Active Directory credentials. Thanks to ADSelfService Plus!
Intimate Active Directory users of their impending password/account expiry by mailing them these password/account expiry notifications.
Synchronize Windows Active Directory user password/account changes across multiple systems, automatically, including Office 365, G Suite, IBM iSeries and more.
Ensure strong user passwords that resist various hacking threats with ADSelfService Plus by enforcing Active Directory users to adhere to compliant passwords via displaying password complexity requirements.
Portal that lets Active Directory users update their latest information and a quick search facility to scout for information about peers by using search keys, like contact number, of the personality being searched.