- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
OAuth, an authorization protocol that provides applications with access to resources of other third-party applications, can also be used to authenticate users. With simple configuration steps, ADSelfService Plus supports SSO to all OAuth- and OIDC-enabled cloud applications.
How do OAuth and OIDC protocols work?
Since OIDC is built as an authentication layer on top of the OAuth 2.0, both protocols function quite similarly to each other with slight deviations towards the end of the code flow process.
In OIDC, when a user wants to access an application or SP, it initially takes the user to the IdP's login page for authentication and communicates certain parameters, like the redirect URI, response type, and scope. After the user successfully authenticates their identity with the IdP, they are redirected back to the application.
Simultaneously, on the servers' secure back channel, the IdP passes an authorization code to the SP, which it later exchanges for the access token and ID token. The ID token helps the SP understand the identity of the user who has just logged in. The access token is used if the client application needs to access more details about the user, like their profile picture for instance.
The flowchart below gives a better understanding of the SP-initiated SSO flow for OIDC.
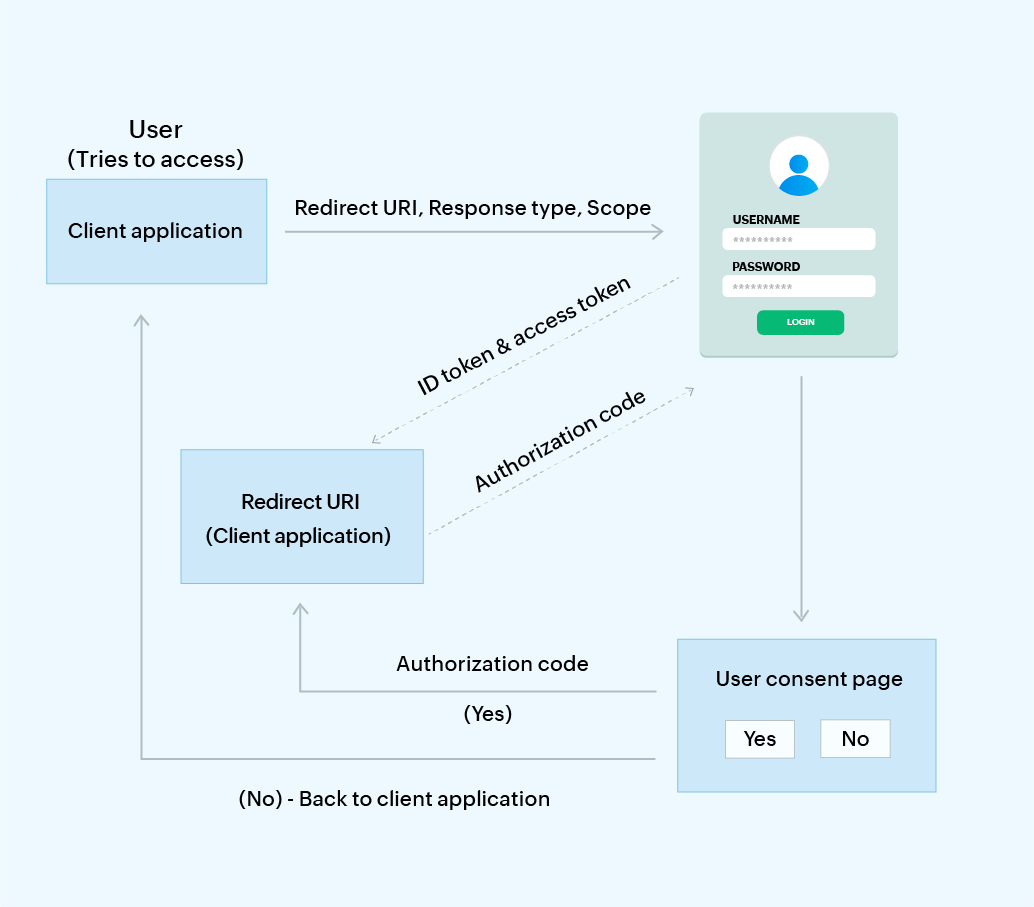
The OAuth 2.0 authorization code flow works identical to OIDC's code flow mentioned above. However, in the final step, the SP receives the access token and refresh token from the IdP over the back channel instead of the ID token. The refresh token is used to get a new access token once it expires without making the user authenticate again with the IdP.
OAuth and OIDC SSO using ADSelfService Plus
ADSelfService Plus provides a range of commonly used OAuth and OIDC applications that are pre-integrated to make SSO configuration easy. Admins can also add any custom OAuth or OIDC-enabled application, which users can then access using SSO. It offers granular policies for admins to easily configure user access to applications. Options to configure IdP details such as authorization endpoint URLs, token endpoint URLs, and user endpoint URLs are provided for both custom and pre-integrated applications.
There are two ways through which users can log in to an application or a service using ADSelfService Plus' OAuth and OIDC SSO, as explained below:
IdP-initiated SSO flow
- With IdP-initiated SSO, users first authenticate themselves and log in to ADSelfService Plus, which is the IdP.
- Once logged in, the user clicks the desired application from ADSelfService Plus' app catalog.
- The respective application then opens in a new tab and the user will be logged in automatically without having to authenticate again.
SP-initiated SSO flow
- With SP-initiated SSO, the user initially tries to access the required application by visiting the application's landing or login page.
- The user is then redirected to ADSelfService Plus and is presented authentication factors as configured by the admin.
- Upon successful authentication in ADSelfService Plus, the user is taken back to the application and is granted access.
A user-friendly console enabling hassle-free SSO configuration
Configure pre-integrated applications
Conveniently categorized
Choose from a range of pre-integrated applications that have been categorized for convenience.

Fig. 2: Pre-integrated OIDC applications in ADSelfService Plus
1. Conveniently categorized: Choose from a range of pre-integrated applications that have been categorized for convenience.
Configure advanced IdP details
In-depth configuration
Configure IdP details such as client ID, issuer, authorization endpoint URL, and user endpoint URL here.
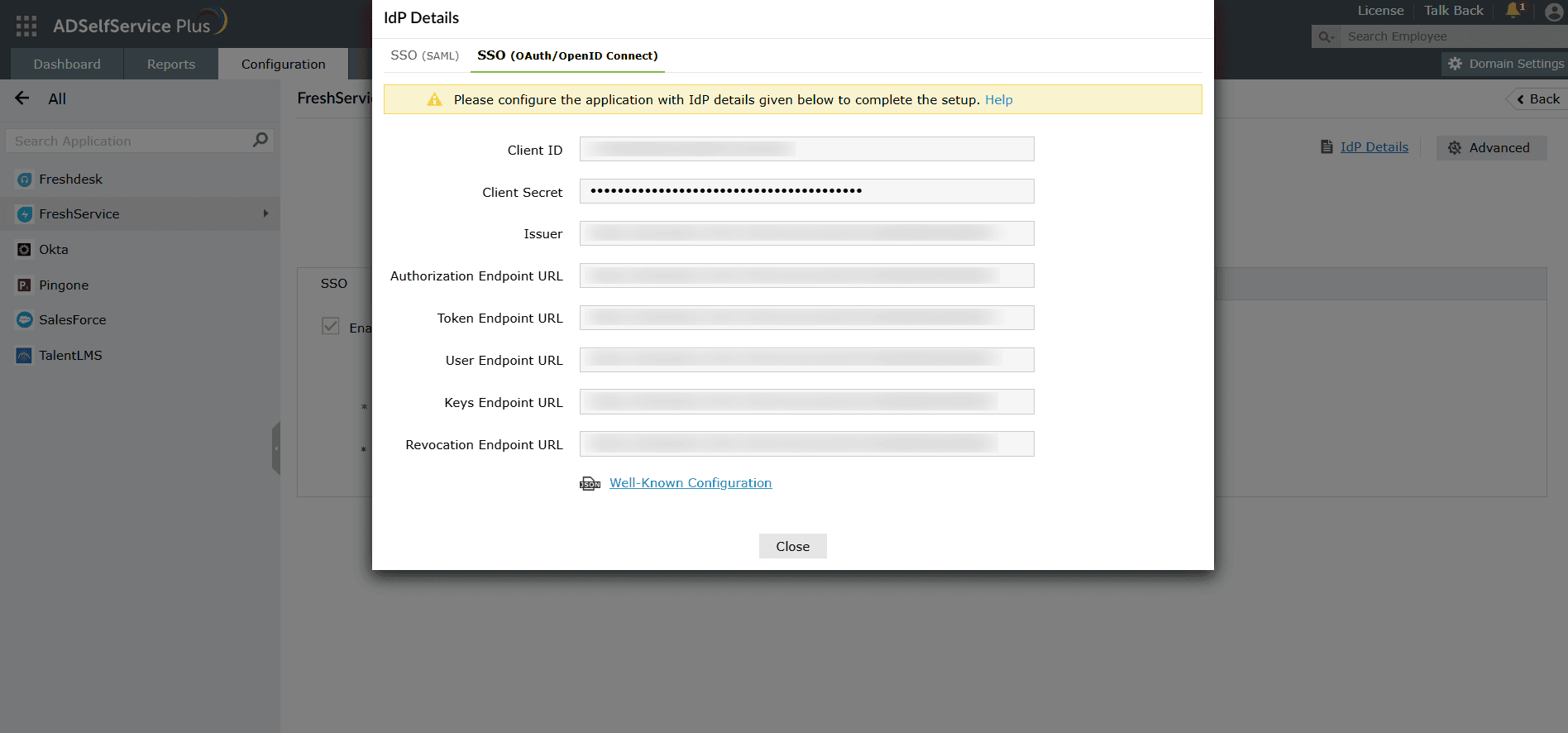
Fig. 3: OIDC SSO configuration in ADSelfService Plus
1. In-depth configuration: Configure advanced IdP details such as authorization endpoint URLs, token endpoint URLs, and user endpoint URLs by clicking this button.
Configure custom applications
Custom app configuration
Choose between widely used protocols, including SAML, OAuth, and OIDC SSO, to provide SSO for custom apps.
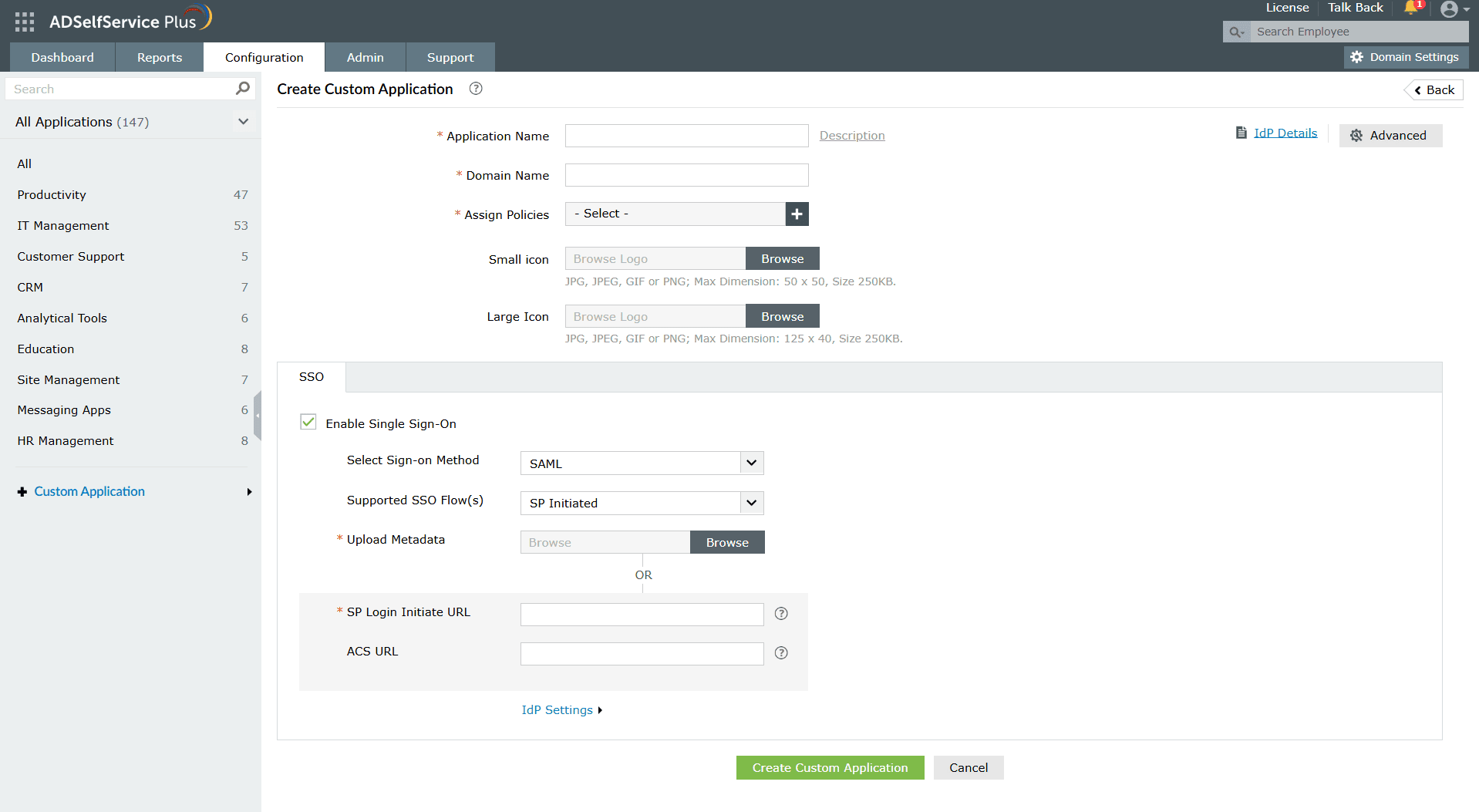
Fig. 4: Custom app SSO configuration in ADSelfService Plus
1. Custom app configuration: Choose between widely used protocols, including SAML, OAuth, and OIDC SSO, to provide SSO for custom apps.
Benefits of OAuth and OIDC SSO in ADSelfService Plus
- Support for any OAuth/OIDC-enabled application: Provide SSO support for any OAuth/OIDC-enabled application. Configure SSO easily from a pool of pre-integrated applications or add custom applications.
- Improved security: Implement MFA for SSO-based application logins, adding another layer of security to usernames and passwords.
- One-click access: Help enhance the user experience and eliminate password fatigue by providing seamless, one-click access to applications.
- Reduced IT workload: Help IT admins reduce password-related help desk workloads and manage identities across multiple services better.
Sit back and let ADSelfService Plus take care of your SSO needs.
Get your free trialPassword self-service
Free Active Directory users from attending lengthy help desk calls by allowing them to self-service their password resets/ account unlock tasks. Hassle-free password change for Active Directory users with ADSelfService Plus ‘Change Password’ console.
One identity with Single sign-on
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications with their Active Directory credentials. Thanks to ADSelfService Plus!
Password/Account Expiry Notification
Intimate Active Directory users of their impending password/account expiry by mailing them these password/account expiry notifications.
Password Synchronizer
Synchronize Windows Active Directory user password/account changes across multiple systems, automatically, including Office 365, Google Workspace, IBM iSeries and more.
Password Policy Enforcer
Ensure strong user passwords that resist various hacking threats with ADSelfService Plus by enforcing Active Directory users to adhere to compliant passwords via displaying password complexity requirements.
Directory Self-Update & Corporate Search
Portal that lets Active Directory users update their latest information and a quick search facility to scout for information about peers by using search keys, like contact number, of the personality being searched.










