Users generally find it a hassle to remember multiple usernames and passwords to access the different websites and applications that they use for both personal and official purposes. Single sign-on (SSO) removes the need for multiple user IDs and passwords by allowing users to access multiple resources using one set of credentials.
With SSO, organizations usually rely on a trusted third party to confirm that users are who they claim to be.
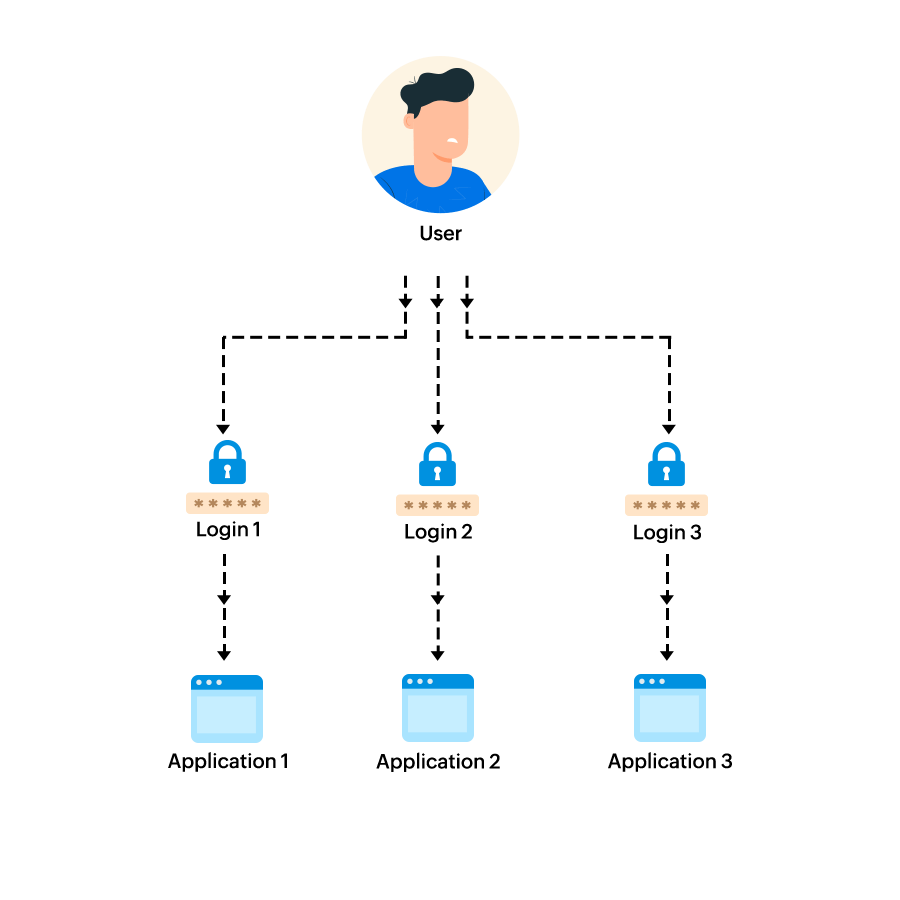
In the absence of SSO, organizations have to maintain databases containing the credentials of all approved users, one for every application or resource that users need to access. When a user enters their username and password, the credentials are compared with the information in the database. If it matches, the user is given access to that application.
To understand how SSO works, one must understand the role of an identity provider (IdP), the system that performs user authentication, and a service provider (SP), the enterprise application or website to be accessed by the user. Only when a trust relationship is established between the SP and the IdP can SSO be enabled across them.
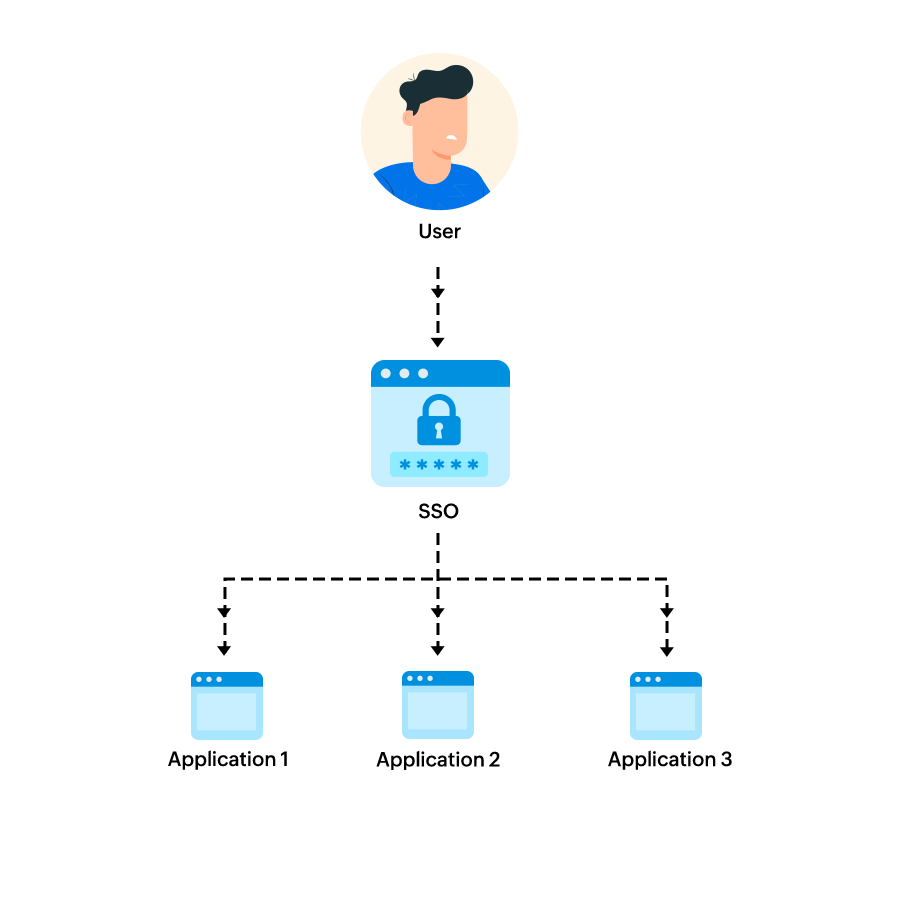
When the same user tries to access a different trusted resource, the new resource only checks the user's identity with the IdP. No additional login is required, as the user has already been authenticated and the IdP verifies the user's identity.
SSO uses standard identity protocols like OAuth, WS-Federation, OpenID, and SAML to pass tokens. These identity protocols have significant differences.
This is among the most widely used protocols. A typical SAML workflow consists of an IdP, SP, and user. User information is sent as an assertion. First, a SAML request passes from the SP to the IdP through the user's browser, and then a SAML response passes from the IdP to the SP through the user's browser.
This protocol permits the authorization server to issue access tokens to third-party applications, with approval from the owner of the resource, without giving out credentials. These access tokens are used by third-party applications to access resources hosted by the resource server.
Users of one organization can access resources of another organization by means of a trust relationship established between the two organizations. It is very similar to how SAML works but with a simpler set of messages.
With OpenID, a user's password is only used by the relaying party, a third party, to authenticate and authorize the user. Once authorized, the user can access multiple applications without having to share their credentials with every application. The user information is passed as an ID token.
Password vaulting is the process of storing user credentials for multiple enterprise applications in a software vault and securing them with a single password. Password vaulting is sometimes incorrectly referred to as SSO. With password vaulting, the user has to enter their credentials each time they move to a different application. In SSO, however, once a user logs in through an SSO solution (IdP), they can access all the company-approved applications and websites without logging in multiple times.
Federated SSO allows users to access resources across organizations. Say a user who works at company A needs access to resources from company B. Company B is a client of company A and has a federated relationship with it. Thanks to the help of federated SSO, the user is able to sign in to company B's website using company A's authentication; there’s no need for them to create a new account for company B.
The user's credentials are recognized by the federation server and it passes the authentication token to other organizations in the federation to authorize the user.
SSO is greatly beneficial to both users and IT administrators
in any company.
When users do not have to remember multiple passwords, they are less likely to create weak passwords for easy remembrance. They are also less likely to write down passwords or spend significant time scouring through their list of passwords to access different applications.
Users do not have to remember multiple credentials to access different websites, applications, and resources. One set of credentials is all they need to remember.
Having to use only one set of credentials to access a host of applications makes it less likely for employees to frequently knock on the doors of IT administrators to reset their forgotten passwords. Users also won’t have to wait for IT administrators to act on their requests.
SSO solutions with features like multi-factor authentication (MFA) can provide additional layers of security and ensure that the users accessing resources are who they claim to be. The addition of a strong password policy will further strengthen security.
Various surveys show that a significant number of calls received by IT administrators are related to forgotten passwords. Thanks to SSO, IT admins can focus on more important tasks instead of dealing with the frequent password reset tickets raised by employees.
ADSelfService Plus is an integrated Active Directory self-service password management and SSO solution. It streamlines and enhances the login experience for users via SSO and uses MFA to provide greater security. ADSelfService Plus uses the secure and widely adopted industry standard SAML 2.0 to provide SSO.
Users can log in to a website using SSO through two ways:
IdP-initiated SSO SP-initiated SSOWhen SSO is enabled, while authenticating themselves using Windows Active Directory domain credentials, users also have to additional authentication steps set by the administrator. These factors can be SMS- or email-based verification codes, or third-party authentication providers like Yubikey, Google, and Microsoft authenticators.
With ADSelfService Plus, administrators need not create individual identities for each user. Users’ identities already present in Active Directory can be utilized for authentication. With Active Directory's OU- and group-based structure, policies can be created to determine who gets to access various cloud applications. Access to certain applications can be restricted to users belonging to certain groups.