A. .If you plan to take the trail installation as it is to production, all you need to do is register the license. Click the Register link on the top right corner in the Web console, browse and select the license file that you received from us and get going.
If you are planning to move the trial onto a new server to host it in production, here are the steps you need to follow:
Note:
The procedure is same to move even your registered installation from server to another.
Again, the procedure is same for migrating from 32 bit to 64 bit OS and vice versa.
A. Please visit this page
https://www.manageengine.com/remote-monitoring-management/service-packs.htmlfor all information related to applying service packs.
A. Steps to enable or disable SSL in RMM Central:
For RMM Central build 8050 and above.
This will enable the self signed SSL certificate for RMM Central. RMM Central webclient can be accessed in the same port number with https://
To Disable the SSL :
This will disable the self signed SSL certificate for RMM Central. Hence the web-client can be accessed in the same port number with http://
For Builds older than 8050. (We have removed apache in build 8050)
Now you can try connecting to the web client with https i.e https://IPAddress:Port Number
Eg: https://192.168.223.23:80
Note: The above steps will work with RMM Central build 7010 and above.
Attachments:
A. To change the timezone in RMM Central,
Q.How to remove the Intro tab in RMM Central?
A : You will mostly need this tab during evaluation to help you set up and configure the application to monitor your network. To remove the Intro tab in RMM Central
1)connect to the DB bin:\>mysql.exe -u root -P 13306 RMMCentralDB (mysql.exe is under /rmmcentral/mysql/bin) 2)Execute this command. mysql>update panelprops set attribvalue='false' where nodeid='opmintro' and attribname='tab'; Now logout and login.
Service Packs and Hot Fixes are released from time to time and contain issue fixes, enhancements, changes, and new features.
A: Service Packs and Hot Fixes are released from time to time and contain issue fixes, enhancements, changes, and new features.
A: 1. Stop the RMM Central server and make sure the Java.exe processes are not running in the task manager.
2. Take a backup of your existing RMM Central installation by executing the BackupDB.bat in the RMM Central\bin\backup
3. This creates a backup file in the RMM Central\backup folder with the current date like for example 'BackUp_OCT10_2011_02_39_44_8812.zip' .Wait till the backup completes.
4. Once the backup process is complete, select Start --> Programs --> ManageEngine RMM Central --> DB Manager --> DB Configuration.
5. A DB Configuration window pops up. Select MSSQL option and click OK. Configure the following information:
DB Host : The name or the IP address of the machine where MSSQL is installed.
Port: The port number in which RMM Central must connect with the database. Default is 1433.
User Name and Password: The user name and password with which RMM Central needs to connect to the database.It would be better if you could provide the "sa" user name and password as RMM Central uses metadata, to create the tables.
6. These steps will automatically create the database in the MS-SQL.However the tables will be created only after successful start of RMM Central. So Start RMM Central with MS-SQL as the back end and shut it down after the successful startup.
7. Now run the RestoreDB.bat file under \RMM Central\bin\backup folder on the ...\RMM Central\bin\backup>RestoreDB.bat "D:\backup\BackUp_OCT10_2011_02_39_44_8812.zip"
8. Once the restoration is complete, start RMM Central. This should restore the data in MS-SQL database.
A: RMM Central is available in English, Spanish, Chinese Simplified, Chinese Traditional, Japanese, French, German, and Italian languages and it can be selected during installation. Below are the steps to change RMM Central from one language to other supported language(English to Spanish).
1. By default the language will be set for English.
2. All supported Languages directory is maintained under RMM Central\ancillary directory.
3. copy the serverparameters.conf from the respective language directory, for ex : Spanish \RMM Central\ancillary\sp\html and replace them under RMM Central\conf\ .
cn - Chinese [chinese simplified]
de - German
en - English
fr - French
it - Italian
jp - Japanese
sp - Spanish
tw - Taiwanese [chinese traditional]
kr - Korean
Restart RMM Central.
A: If the time on RMM Central is different from the Server time, follow the steps given below to fix the issue:
1. Save the attached file and rename it to time.jar and place it under \RMM Central folder.
2. Open a command prompt and go to \RMM Central folder and execute the command below by providing your exact time zone difference from the GMT.
cmd:/> jre\bin\java -Duser.timezone=GMT-9:00 -cp time.jar Time
Modify the query according to the time zone difference in your region. Here I am executing the query for changing the RMM Central time to Alaska Time zone which is GMT -9.
3. Take a back up of wrapper.conf located under \RMM Central\conf folder.
4. Open the wrapper.conf and search for Java Additional Parameters and at the end of the additional parameters, add the entry below.
wrapper.java.additional.12=-Duser.timezone=GMT-9:00
After modifying it, the changes will look as below.
# Java Additional Parameters wrapper.java.additional.1=-Dcatalina.home=apache/tomcat wrapper.java.additional.2=-Dmysql.home=mysql #wrapper.java.additional.3=-Dwebserver.port=80 #wrapper.java.additional.4=-Dresource_check="80,8009" wrapper.java.additional.3=-Djava.library.path=lib wrapper.java.additional.4=-Dwebserver.rootdir=apache wrapper.java.additional.5=-Djava.rmi.server.codebase=apache/tomcat/conf/workers.properties wrapper.java.additional.6=-Dcom.adventnet.me.opmanager.showprogress=true wrapper.java.additional.7=-Dcom.adventnet.me.opmanager.service=true wrapper.java.additional.12=-Duser.timezone=GMT-9:00
5. Save it and start RMM Central as a service which will fix the problem.
Note: 1. The above changes will be in effect only if RMM Central is started as a Service.
2. "wrapper.java.additional.12=-Duser.timezone=GMT-9:00" - This line needs to be place at the end of the file and also change the line number(eg: 12) accordingly.
Steps to correct the time difference issue in RMM Central-NFA plugin
1. Goto RMM Central\Netflow\bin folder and edit the "run.bat" in a text editor and search for the following line:
set JAVA_OPTS=%JAVA_OPTS% -Dprogram.name=%PROGNAME% -Djboss.server.type=com.adventnet.j2ee.deployment.system.AdventNetServerImpl
Change the above line as follows:
set JAVA_OPTS=%JAVA_OPTS% -Dprogram.name=%PROGNAME% -Duser.timezone=GMT-9:00 -Djboss.server.type=com.adventnet.j2ee.deployment.system.AdventNetServerImpl
2. Restart RMM Central service and the Netflow module would show the correct time. Note:GMT-9:00 timezone is shown as an example.Please modify it as per your timezone.
Attachment: time.jar 606 B
You can create a discovery rule to associate process monitors, alert notifications and group devices automatically while adding devices to RMM Central.
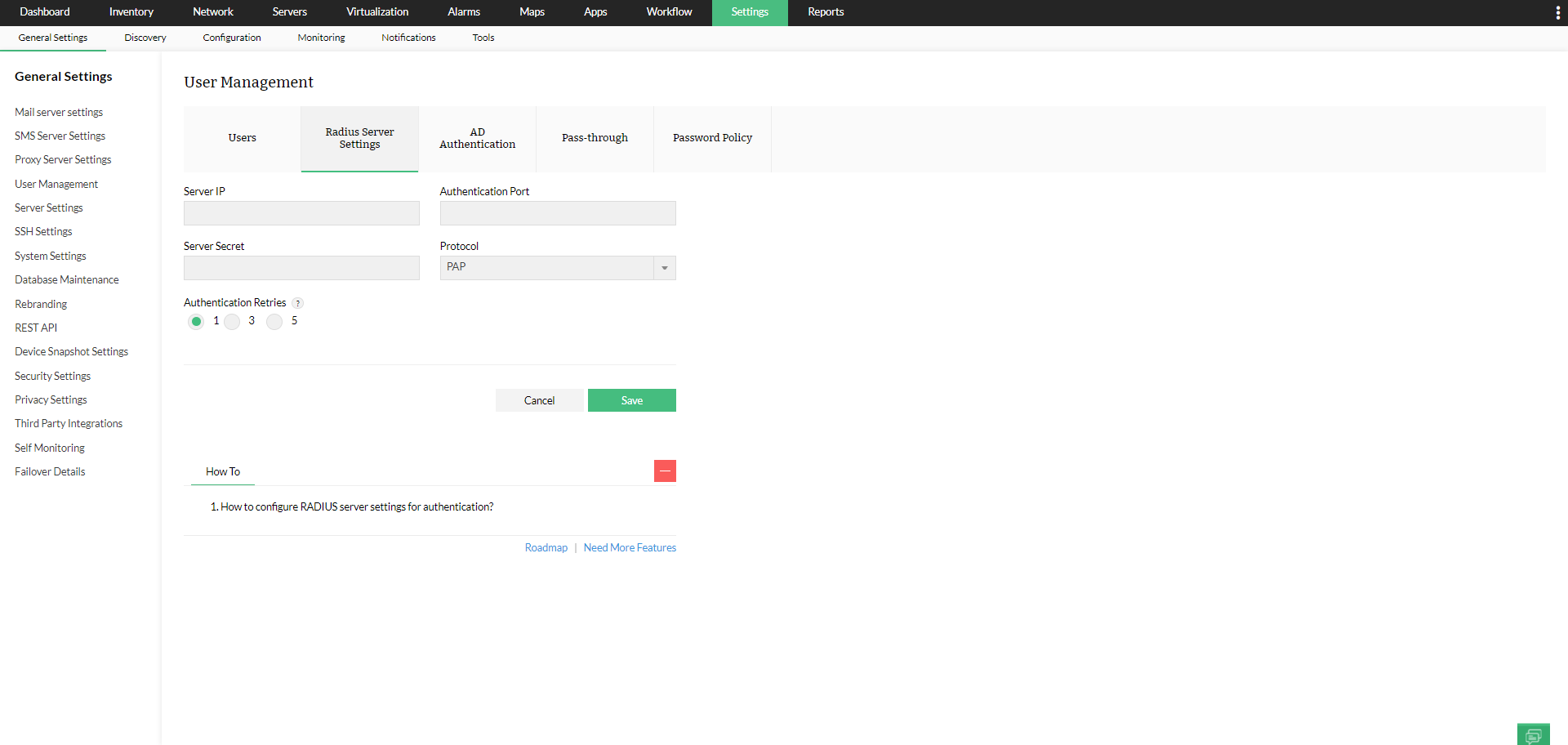
To configure radius server settings, go to Settings -> General Settings -> User Management and enter the required details:
Go to Settings -> General Settings -> User Management -> Add domain or edit an existing domain.
Enter the domain details and check the "Enable Auto Login" option.
In AD Auto-login, the login can be chosen to be allowed for 'All Users' or 'Select AD Groups'. In the case of 'All Users', privilege chosen will be applicable for all the users. In the case of 'Select AD Groups', the specific group names have to be mentioned in the Privilege box, and for those users belonging to that group the corresponding privilege will be assigned during their first login.
A. .SNMPv3 is a user based security model. It provides secure access to the devices by a combination authenticating and encrypting packets over the network. The security features provided in SNMPv3 are Message integrity, Authentication and Encryption. If you select SNMPv3 as the credential type, then configure the following parameters.
Note: Only after configuring Authentication it is possible to configure Encryption.
A.
The Snmpv3 communication between two SNMP Entity starts with handshake process. This process contains two steps, first one is Discovery and second one is TimeSynchronization process. And for snmpv3 communication, the manager needs to know the agent's details inorder to communicate with the agent.
1. SnmpEngineTime.
2. SnmpEngineBoot.
3. SnmpEngine ID.
As per standard, the above information is retrieved from the Cisco router by using Discovery and TimeSynchronization process.
The net-snmp will accomplish both discovery and timesync process in a single request instead of two requests as the discovery response itself contains EngineTime, EngineBoot and EngineID. This behavior is implemented in our SNMP layer and will be rolled out in our next release. However, as per RFC3414, Cisco device should respond for discovery and timesync requests.
For your clear understanding, the discovery & timesync process is explained below:
Discovery Process:- First the Manager (RMM Central) sends a discovery packet to the Agent to get the Agent's Authoritative EngineID value. For further communication, this EngineID value is used. As per RFC3414, the Discovery PDU packet is issued with following parameters:
i) EngineID value as zero length
ii) Security level is noAuthNoPriv
iii) UserName may be zero length or dummy userName.
For this request, the Agent responds with EngineID and UknownEngineID counter value. Instead of empty string, we use the userName as "initial". I would like to clarify that why RFC is recommend to use the userName is empty string, for discovery process is as follows Refer RFC3414 [Page 16] - The msgUserName specifies the user (principal) on whose behalf the message is being exchanged. Note that a zero-length userName will not match any user, but it can be used for snmpEngineID discovery. The reason is that the UserName of the request PDU is not matched with configured user details in the SNMP Entity (agent) while processing the Message. As per RFC3414, the processing of SNMP packet is as follows:
i) First, the SNMP Header field is decoded
ii) SecurityParameters fields are extracted from the Packet. First Authoritative EngineID value is extracted from the packet. If the EngineID is zero length, agent takes this request as Discovery and it responds with EngineID value with usmStatsUnknownEngineIDs counter value
iii) Refer the RFC3414 [Page 25] Processing an Incoming SNMP Message. b) the usmStatsUnknownEngineIDs counter is incremented, and an error indication (unknownEngineID) together with the OID and value of the incremented counter is returned to the calling module. Note in the event that a zero-length, or other illegally sized msgAuthoritativeEngineID is received, b) should be chosen to facilitate engineID discovery. Otherwise the choice between a) and b) is an implementation issue. The SNMP request packet is sent with zero length engineID value, so the cisco device(agent) should properly respond for this request irrespective of whether or not the userName is initial or empty string. It is a good practice to send with empty string. This is already implemented in our SNMP library.
TimeSynchronization Process:
The time synchronization packet is issued with given username and securitylevel as Auth_Priv. The agent responds with enginetime and engineboot and with USMStatsNotInTimewindow conter value. Note that the UserName from the second packet onwards, configured userName whose behalf the request to be issued will be set in the request packet. In this process, the authentication i.e authProtocol/ authPassword are verified.
A. In RMM Central versions 12.5 and above (PgSQL 10.10 or above), the configuration changes (if any) can be done in the zz_itom_ext.conf file under <RMM CentralHome>\pgsql\ext_conf.
Note: DeviceName/IP header is a must for CSV file and other header fields are optional.
For RMM Central version 125174 and above, follow the below steps to import devices from a CSV file
Note: DeviceName/IP header is a must for CSV file and other header fields are optional.
To discover devices from a selected range specify the start and end ip address and select the netmask for the devices to be discovered within that range.
To ignore VLAN interfaces,
Note: To disable Virtual LAN globally, try interface template.
For the all the devices by default RMM Central sends one packet with time out as 1 sec. So if the WAN link stays busy, it is expected that RMM Central will show that the devices on the other side as down. You can resolve this problem by increasing the ping time out, if needed even the packets sent to check the availability. However this facility will be common for all the device i.e. it is a global configuration.
Solution:
BY default these are the list of interface types( type number and name) which are considered as WAN interfaces inside RMM Central.
18 DS1
20 Basic ISDN
21 Primary ISDN
22 Serial
23 PPP
32 Frame Relay DTE
33 RS-232
37 ATM
44 Frame Relay DCE
45 V35
49 AAL5
63 ISDN
64 V11
94 ADSL
96 SDSL
166 MPLS
To include any other type of Interface as a WAN interface to get SLA dashboard "WAN links by availability" report, we need to add the specific type into a table called "WANINTFTYPES"
For example to add an Ethernet/Fast Ethernet (which is of type 6) as a WAN interface, connect to the DB and run this query:
To connect to the Database (Mysql):
1) Open the command prompt
2) Go to the Mysql\bin directory and type the following
RMM Central\mysql\bin>mysql -u root -P 13306 opmanagerdb
3) execute the following statement
4) mysql > insert into wanintftypes values(6);
5)exit
Stop and Start RMM Central and generate the report for Wan links. You can see all the Ethernet interfaces included in the report.
You will need to configure the VMware credentials for discovery before you actually proceed to discover. Here are the steps in detail:
You might also want to configure WMI credentials for the VMs if you want to add any custom WMI monitors or Windows service monitors etc..
After successful discovery, you will find the VMs and Host under the Virtual Devices category under Maps.
Pre-configuring a set of credentials in RMM Central helps applying them to multiple devices at a time, saving a lot of manual effort.
1.Go to Settings --> Discovery --> Credentials
2.Click New in this screen
3.Configure the following parameters and click Add to add the credentials:
Using Quick Configuration Wizard
You can also use the Quick Configuration Wizard to associate a service to several devices at one go. Here are the steps:
Hyper-V devices are automatically discovered by RMM Central and classified under the Virtual Devices map. Hyper-V is discovered in RMM Central using WMI credentials.. So all you need to do is
Class A Network
The entire class A predominantly begins with 10.and is private, to be used in LANS When discovering Class A networks, do the following:
The Host Address Range for Class A Network: 10.0.0.1 – 10.255.255.254.
Class B Network
When discovering class B networks, the procedure is the same. Make sure you select the netmask as 255.255.0.0. The Host Address Range for Class B Network: 172.16.0.1 – 172.16.255.254
Class C Network
When discovering class C networks, the procedure is again the same. Make sure you select the netmask as 255.255.255.0.
Prerequisites:
Must be pingable
Must have SNMP enabled
Before you add, quickly run this check:
Check 1
Check 2
Proceed
Now, add the router for discovery. It will be properly classified and monitored.
We have seen what are unknown devices. Let us see what you need to do to resolve the problem.
To reduce the number of devices getting classified as 'Unknown', configure the correct credentials even before initiating discovery. Doing this saves a lot of time and effort on re-work.
Resolving Unknown devices in the devices already discovered
SNMP-enabled devices
If the device supports SNMP, enable SNMP and rediscover the device. Despite this, if you face issues, troubleshoot as follows:
Similarly, for switches and printers too, enable SNMP in the device and rediscover.
CLI / WMI-enabled devices
If you have decided to disable SNMP authentication on Unix-based servers, configure Telnet or SSH credentials and associate the credentials to the servers. Similarly, for Windows devices, configure WMI credentials and associate the credentials to the devices. Re-discover the devices with the new credential
Devices in an ICMP disabled environment will not be reachable from the RMM Central server. Such devices can be added by the following methods:
To set the DNS name of a device as its display name, enable the "Use DNS as Display Name" option under Discovery Settings. You can also update the device displayname post discovery.
Note: Enabling this option will only modify the newly added devices. The existing devices will not be affected.
To discover VLAN interfaces, go to the device snapshot page, select a network device and click on 'right corner icon' for more actions -> VLANs -> Discover VLANs.
VLAN discovery can be done only in Switch and Router category devices and VLAN enabled interfaces will be discovered only if the SNMP agent responds to the OIDs from this page.
Go to Settings -> Discovery -> Discovery Rule Engine. Choose the appropriate discovery rule that you wish to associate to the existing devices and click on the Run Now option on the top right corner. Select the devices and click on Run to apply the chosen discovery rule to the existing devices.
Device Templates contain information to classify devices and associate monitors to them automatically. WLC Device model, although a device template internally, RMM Central allows you to choose the device template that corresponds to your device prior to discovery. RMM Central provides support to many WLCs, if your device is not on the list, click on Request here and fill up the form to enable us to develop support for your WLC.
Wireless LAN Controller and Access Points categories are automatically assigned during WLC discovery. They cannot be assigned manually like other categories.
Only the access points that are subjected to Advanced monitoring will be displayed in the Inventory page. Advanced monitoring will allow you to monitor multiple functionalities such as availability, health, signal, alerts, notifications, etc. of your Access Points.
Interface discovery for approved devices can be performed either from the Device Snapshot page or from the Interface Discovery(only for versions 125174 and above) page.
Interfaces can be configured to generate the following types of alerts
To configure interface alerts, go to Configuration > Interface Templates and click on the a template. Specify the Condition and Threshold Value for the alert to be generated.
For Bandwidth exceeded alert: Go to Settings > System Settings > and enable Alert when interface bandwidth exceeds its speed to receive bandwidth alerts.
Interface down alert is automatically triggered when an interface is down. This alert cannot be disabled.
In RMM Central, you can calculate the interface traffic using different OIDs via a Performance Monitor. The Interface traffic is calculated using the following formulae.
In Traffic(bps) : Rx Traffic : InOctets*8*1000/deltatime.
Out Traffic(bps) : Tx Traffic : OutOctets*8*1000/deltatime.
By specifying the correct Vendor name and OID, you will be able to create a custom performance monitor that will help you in monitoring the interface traffic of any interface in particular. To create a performance monitor,
Once the polling is started, the newly created monitor will calculate the interface traffic and display it in the form of graphs and tables.
RMM Central automatically updates all the VMs created under a Host or under the vCenter environment, but they are not monitored by default. To enable monitoring of new VMs by default, the 'Auto VM Discovery' option must be enabled for the corresponding credential profile. It can be done by two ways:
UCS discovery in RMM Central is performed similar to the discovery of other devices.
You can use the Device Templates available in RMM Central to associate specific monitors to a device type.
To associate a monitor to an existing template:
When creating Performance monitors, RMM Central allows you to monitor each instance of the variable as a separate monitor, providing more freedom over setting thresholds for individual instances.
RMM Central allows this to be performed for custom SNMP and WMI monitors.
For custom SNMP monitors:
You can configure thresholds in bulk from the Application Monitors window in RMM Central. To do so:
You can automate adding monitors to specific devices using Discovery Rule Engine. RMM Central has a default rule in Rule Engine to associate MSSQL monitors to relevant devices. In case it is not available, you can configure it as below
In case you wanted to associate the MSSQL monitors to already discovered devices, you can do so by selecting any of the rules and clicking 'Re Run' from the Discovery Rule Engine page.
RMM Central's Notification Profiles allows you to configure profiles to get notified when specific events occur in the network, including when any of the AD/Exchange/MSSQL services in your network goes down. The following example explains about configuring notifications for AD services going down.
To configure an URL template, follow these steps:
You can use Discovery Rule Engine to associate URL monitors to devices during their discovery. To configure this, follow the steps below:
If you want to run this rule for devices that you've already discovered, you can do so by selecting the necessary rules and using the 'Re Run' option.
RMM Central allows you to automate associating File monitors during discovery using the Discovery Rule Engine. Before you configure the rule, make sure that you have added the File monitoring template already in Settings → Monitoring → Files.
To receive notification when any of the File Monitor thresholds are violated:
You can use Discovery Rule Engine to automate association of Folder monitors to specific devices during discovery. To know in detail on how to do it, refer to our help documentation on Discovery Rule Engine in RMM Central.
To set up a notification profile for folder monitor-related alerts, follow these steps:
RMM Central's file monitoring agent allows you to monitor your log files for occurrence of a string/combination of strings such as error messages during execution or exceptions, and raise contextual alerts based on the string found and the number of times it has been found in a particular log file. You can provide multiple conditions and choose whether you want to be alerted when all/any of the conditions are satisfied.
You can also use Regular Expressions as criteria, and RMM Central will raise alerts when content that satisfies the provided RegEx is found.
You can know about Agent-based file monitoring in detail in this help document: Monitoring log files using agentWhen the agent installed in any device goes down, RMM Central alerts the user through web alarms. If you want to get notified through a different medium, you can set up a notification profile as follows:
You can enable or disable Eventlog for multiple devices using the Quick Configuration Wizard.
Discovery Rule Engine in RMM Central can be used to associate Eventlog monitors to devices during discovery.
RMM Central's process monitoring allows you to have a look over all processes running in any of your network devices. To configure process monitoring templates:
You can also associate process monitors to any device from its Snapshot page by clicking Monitors → Process monitors → Actions → Associate monitor.
You can use workflows to automate several actions in RMM Central, including starting/stopping/testing processes. To set this up:
Head to our documentation on Workflows to know in detail about automating actions in RMM Central.
Using Discovery Rule Engine, you can automate association of process monitors as follows:
You can configure notification profiles to be intimated on a medium of your choice when the process monitors raise any alerts.
To disassociate a Windows Service monitor from several devices at once:
If you want to delete it from an individual device, you can also do it from the Device Snapshot page by clicking Monitors > Windows Service Monitors and tapping the 'Delete' icon next to the monitor you want to disassociate.
Using Workflows, you can automate actions like Start/Stop/Pause Windows Services.
RMM Central's Notification Profiles has an option to get you notified when any of the Windows Service monitors raise an alert.
To configure a notification profile for receiving alerts when a service is down:
The source and the destination devices should be IP SLA enabled Cisco devices. Make sure to discover the source device in RMM Central and configure the correct SNMP credentials (with read and write community). To add a new VoIP monitor,
The collected data will be updated after every poll.
RMM Central primarily relies on Cisco's IP-SLA for monitoring the VoIP and the prerequisite therefore is, that the device should be a Cisco Router and must have IPSLA agent enabled on it. From IOS Version 12.3(14)T all Cisco routers support monitoring of VoIP QoS metrics. Cisco's IPSLA, an active monitoring feature of Cisco IOS software, facilitates simulating and measuring the above mentioned parameters to ensure that your SLAs are met. Cisco IP SLA provides a UDP jitter operation where UDP packets are sent from the source device to a destination device. This simulated traffic is used to determine the jitter, the round-trip-time, packet loss and latency. This data is gathered for multiple tests over a specified period to identify how the network performs at different times in a day or over a few days. The VoIP monitor gathers useful data that helps determine the performance of your VoIP network, equipping you with the required information to perform network performance assessment, troubleshooting, and continuous health monitoring.
The source device (Cisco device with IPSLA agent enabled) should be discovered in RMM Central and properly configured with the correct SNMP credentials. For example, if you want to monitor the latency and availability of the branch office from your main office, you will need to have an IP SLA agent enabled Cisco router in your main office and this router should be discovered in RMM Central. To add a new WAN RTT monitor,
The data will be collected and updated after every poll.
If you want to administratively disable an interface, it is possible with RMM Central in just a few clicks. Here are the steps:
The interface gets disabled and the interface's status is changed to Down. To enable the interface again, go to its snapshot page and click the Enable button under the Interface tab.
You can configure thresholds for multiple interfaces of the same type by editing the relevant interface templates.
You can modify the IP Address to look at from the database, so that RMM Central uses the secondary interface to monitor the service running on this interface alone.
Here is the procedure to do this.
1. Connect to mysql database using the following command:
cmd> cd [RMM CentralHome]\\mysql\\bin
cmd> mysql.exe -u root -P 13306 RMM CentralDB
2. Use the mysql update command to change the IP address to look at:
mysql> update InetService set TARGETADDRESS=1.2.3.4' where TARGETADDRESS='5.6.7.8';
1.2.3.4 is the secondary interface of the device
5.6.7.8 is the primary interface of the device. RMM Central should have discovered the device through this interface.
And update the TARGETADDRESS only for the interface on which a particular service runs.
Try using the following command:
mysql> update InetService set TARGETADDRESS='1.2.3.4' where TARGETADDRESS='5.6.7.8' and NAME='machine-name-or-ip-address_ServiceName_Portnumber';
where machine-name-or-ip-address refers to the machine name or ip address of the device to be monitored ( it is mostly the primary interface in case of ip address)
ServiceName is the name of the service to be monitored which can one among Web, FTP, Telnet, MySQL etc.. as specified under Services -> Monitoring --> Service Monitors
Portnumber is the port on which the service runs like 80, 21, 23, 3306 etc...
You can monitor only the required VMs on a Host. RMM Central discovers all the VMs during the initial discovery and lists them under the inventory in the host snapshot page. Click on the relevant icon to monitor the required VMs on the host. RMM Central maintains this configuration when a HA, vMotion, or rediscovery happens.
Use the Mib Browser from the Admin tab or the MibBrowser.bat/sh utility in /rmmcentral home/bin folder to check the compliance. Select RFC1213 or RFC2096 from the dropdown and then select your device. RFC1213:
If the device does not support this OID, it will error out. RFC2096:
If the device does not support this OID, it will error out. If you do not see a MIB for RFC2096, you can download and upload it into RMM Central. Google will provide a link to the MIB or check for its availability in http://oidview.com.
The SNMP OID that returns temperature on Cisco devices is .1.3.6.1.4.1.9.9.13.1.3.1.3.1. Not all catalyst devices support this. This variable is implemented in CISCO-ENVMON-MIB. Load the mib in the MibBrowser and check if the device responds to a query to this variable.
RMM Central identifies the Windows server as a DomainController during the initial SNMP-based discovery. Based on the SNMP response, it automatically classifies the device under the Domain Controller category and is grouped under the map of the same category. Upon classification as a DC, the DC gets added with the AD dashboard. If it has correct WMI credentials, all the AD dashboard monitors will automatically populate the values. In your case, since the device is already discovered, enter the correct WMI credential and manually change the category to Domain Controller.
Open a CLI session on the destination router and enable the EXEC mode as follows:
Router>enable
Start the global configuration mode:
Router#configure terminal
Enable the IP SLA responder:
Router(config)#ip sla responder
Router(config)#ip sla monitor responder
(Note: Enter any one of the command to enable IP SLA responder as it varies according to the IOS versions.)
Repeat the above steps for all the destination routers on which you want to monitor VoIP performance.
Define a template with the required VoIP settings to be used for monitoring performance. The VoIP template comes with pre-populated default values. Incase you would like to effect some changes to the values before initiating monitoring, make the changes as follows:
Defining Thresholds for the monitored parameters: You can define a threshold template so that the VoIP performance parameters can be better suit your company SLA's (Service Level Agreements). Alerts are triggered based on the thresholds configured so that you can take corrective actions in time. Here are the steps to define a threshold template:
To monitor the folder on both local or remote server you should specify the path as follows: Drive:\FolderName ( Example C:\FolderName )and you can view our File & Folder monitor
More details in the User Guide:
File monitor http://help.opmanager.com/file_monitoring_template
Folder monitor http://help.opmanager.com/folder_monitoring_template
To create a custom dial graph, please follow the below steps. Lets take your scenario, where you want to point the custom monitor to the dial graph for a Firewall device. Here are the steps.
1. Open the file rmmcentral_snapshot_dial.xml and scroll to Firewall section.
2. Add PARAM type and pollKey for each dial names. where, PARAM type is the device type. eg: Juniper pollKey is the custom monitor name. eg: JuniperCPU Similarly you can do this for other device types like Servers, etc.. Replacing the custom monitor to the Pollkey can point the monitor value to the dial graph
3. I have added a custom monitor called JuniperCPU.
For eg:
<CATEGORY name="Firewall"> <DIAL name="CPUUtilization" displayName="webclient.devices.details.cpu" dialType="meter" shortKey="CPU"> <PARAM type="sonicwall" pollKey="CPUUtilization"/> <PARAM type="Juniper" pollKey="JuniperCPU"/> <PARAM type="Fortigate" pollKey="FortigateFirewallCPUUtilization"/> <PARAM type="Netscreen" pollKey="NetscreenFirewallCPUUtilization"/> <PARAM type="Cisco PIX" pollKey="CiscoFirewallCPUUtilization"/> <DEFAULT pollKey="CPUUtilization"/> Similarly, you can add the entries for DISK and Count Utilization.
4. Save the file and Restart RMM Central to take effect.
Note: Backup rmmcentral_snapshot_dial.xml before modifying. Similarly you can associate custom monitor for other categories like Server,Routers etc.
RMM Central supports DNS environment. If the device is added with DNS name, all the queries will be sent only to the name and not IP. We can configure RMM Central to poll only by name and not by IP address. Open serverparameters.conf under /RMM Central/conf in a wordpad and find this entry PING_USING_IPADDRESS true change it to PING_USING_IPADDRESS false
Restart RMM Central. Try adding one such device using Admin-->add device(use DNS name).
When you configure a WAN RTT monitor, RMM Central starts collecting data every 5 minutes. At each poll, if the latency and availability threshold values are violated, RMM Central triggers an alarm. After 5 minutes, if the latency threshold of the monitor is violated, an alarm is listed in the WAN RTT Monitors dashboard.
RMM Central does not support SNMP V3 for WANRTT yet.
We have plans to use only the read community for WANRTT configuration (Import option for the existing monitors using read community which is also under development phase). RMM Central uses SNMP write to configure IPSLA (WAN RTT)settings in the source router. Though it is similar to "Write" command, some models(IOS versions) do not work with this. So once you configure a new WAN RTT monitor, login to the source router and run "write" (or equivalent command in new versions).
You can use our WAN RTT Monitor add-on to monitor the latency of end routers.
We use Cisco IP SLA to monitor the latency and raise alerts based on the thresholds you configure in RMM Central. To know more about Cisco IP SLA, look at the link given below: http://www.cisco.com/en/US/docs/ios/ipsla/configuration/guide/ The WAN RTT (Round Trip Time) Monitor will help you,
a) Monitor latency between end points across WAN
b) Raise alerts based on the Round Trip Time thresholds. The thresholds are customizable.
c) Monitor Latency for each HOP between the end points.
d) Custom reports to identify the problem quickly.
e) Auto-Configuration of Cisco IP SLA monitors to the router, without having you to log on to the router.
You can use our WAN RTT Monitor add-on to monitor the latency of end routers.
We use Cisco IP SLA to monitor the latency and raise alerts based on the thresholds you configure in RMM Central. To know more about Cisco IP SLA, look at the link given below: http://www.cisco.com/en/US/docs/ios/ipsla/configuration/guide/ The WAN RTT (Round Trip Time) Monitor will help you,
a) Monitor latency between end points across WAN
b) Raise alerts based on the Round Trip Time thresholds. The thresholds are customizable.
c) Monitor Latency for each HOP between the end points.
d) Custom reports to identify the problem quickly.
e) Auto-Configuration of Cisco IP SLA monitors to the router, without having you to log on to the router.
Follow the detailed instructions provided in the link below:
http://www.vmware.com/pdf/vsp_4_snmp_config.pdf
Intructions to enable SNMP on ESXi 4.1 using remote CLI are available in the link below:
http://www.fatmin.com/2010/08/enabling-snmp-in-esxi-41-using-the-remote-cli.html
To configure thresholds for multiple monitors at once, you can use the Quick Configuration Wizard. Go to Settings → Configuration → Quick Configuration Wizard and select Threshold Settings. After providing the necessary filter criteria (Monitor type, Protocol, Category and Filter by), all applicable monitors will be listed. You can choose multiple monitors and click "Configure" to configure negative thresholds for the selected monitors.
The import/export template option is useful when you want to share a custom template you created with the community or import a template from the community.
Exporting templates:
If you want to share it with the community, for now, you can post it on our forums, or email it to us. You can also upload it via this form.
Importing templates:
To associate the templates,
There should be a Security Event generated when that AD account logs in. We can create an EventLog rule and in the match string, give the account name for the exact filter. Follow the steps below:
You can change this setting by changing the Availability Interval of any device. In the Snapshot page of any device, click on "Edit device details" under Device Summary, or go to Menu → Availability Monitoring and select the desired polling interval value for the device.
RMM Central script monitoring provides a lot of flexibility to achieve some network monitoring tasks which is otherwise not available in a solution out-of-the-box, or even with integrated solutions.
Usecase
This usecase demonstrates how RMM Central uses Script monitors to find the sum of the values of two monitors on a monitored database server and alerts if the collective size exceeds a certain threshold. The monitor by default returns multiple instances (SQL instances on a DB server), and this usecase derives a sum of the size of two specific instances. You can extend the same procedure to perform several other tasks my querying a database (in this example, the rmmcentral database) through a script.
Prerequisites
MySQL .Net connector: http://dev.mysql.com/downloads/connector/net
The custom script
Attachment:CPU Util Sum.xml
Here is the video capture leading you through a step-by-step configuration:
If you are unable to view the embed above, visit this link: https://www.youtube.com/watch?v=0BB4uvc8i1k
The DHCP scope monitoring OIDs are present in the DHCP mib.Hence the following DHCP mib and MSFT mib has to be placed in the RMM Central\mibs folder.Find them attached in this KB article.
The OIDs are .1.3.6.1.4.1.311.1.3.2.1.1.3 for FREE IPs and .1.3.6.1.4.1.311.1.3.2.1.1.2 for IN USE IPs in a network address
Verifying the OIDs
Run the mibbrowser.bat in the RMM Central\bin folder and load the DHCP mib.
Fill the details of the HOST,community with the details of the DHCP server
Paste the OID for FREE IPs in the ObjectID field and click on Operations -> Get
If you get the output of the FREE IPs available in every network in the DHCP pool,create custom SNMP monitors using the procedure in the how-to link below
https://www.manageengine.com/network-monitoring/custom-SNMP-monitors.htm
As you can see the OIDs above are numeric as well as tabular hence they give output for multiple networks in every poll.
Updating changes in Database
Once you have created the SNMP monitors (Free IPs and IN USE IPs) in the Windows template and applied it to servers,type the following in the browser
http://RMM Central server:port/SubmitQuery.do
Paste and run the following query after inputting the DHCP server name and DHCP monitor name.
update polleddata set saveabsolutes='true' where name like '%DHCP monitor name%' and agent like '%DHCP server name%'
For example :
update polleddata set saveabsolutes='true' where name like '%DHCP FREE IPs%' and agent like '%fscvopdhcp01%'
Repeat the same procedure for DHCP IN USE IPs monitor as well.
Note: Please make sure you backup RMM Central before running the above query.
Attached Files :
DHCP Scope monitor.png 85.85 KB
If you have any questions about RMM Central, feel free to raise a support request and we’ll get back to you.
Create a CSV file and add all the custom field information including the serial numbers of your devices. Go to Settings > Configuration > Custom Fields > Import values > upload the CSV file. The updated changes can be viewed from the individual device snapshot page under the Custom Fields section.
You can associate a Windows service monitor or a TCP service monitor to several devices using the quick configuration wizard.
Repeat process to associate other services to multiple servers.
To regenerate SSL in RMM Central, go to Settings -> General Settings -> Security Settings and click on the edit button next to 'SSL Certificate Details'.
Prerequisite: Mail Server has to be configured. To configure Mail Server Settings, click here.
An alarm can be suppressed by three methods.
Device Specific:
Alarm Suppression for Group devices:
Settings Option
Inventory Page
Note: The suppressed alarm and the suppression time will be displayed on the device snapshot page.
Here are a few things that you can do to avert false positives:
To increase the size to say, 300 characters,
C:\\..\\RMM Central\\mysql\\bin>mysql.exe -u root -P 13306 RMM CentralDB
ALTER table Alert modify MMESSAGE TEXT;
Yet another frequently asked/discussed requirement is the ability to forward alarms in RMM Central as traps to another trap destination. Requests are also raised to know if the incoming trap can be redirected to another application. YES, both are possible. Here is how you go about the forwarding:
Forwarding Traps
Here, RMM Central simply forwards the SNMP Trap to another manager/device. Forwarding traps from RMM Central involves a couple of configuration changes in two files. Refer the table below:
1. Effect the following configuration changes:
| File name & path | Existing entry | Modified entry |
|
/opmanager/conf/trap.forwarder |
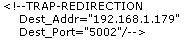 |
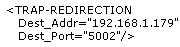 (replace with the correct IP address and port) |
| /opmanager/conf/trap.filters | 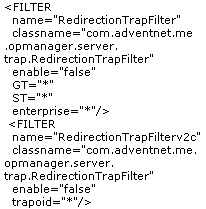 |
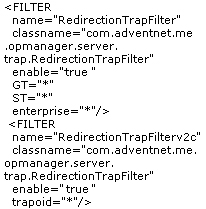 |
2. Save the file and restart RMM Central.
RMM Central starts forwarding the incoming traps to the destination IP address and the Port mentioned in the trap.forwarder file.
Forwarding RMM Central Alarms as Traps
You might want to forward the alarms in RMM Central as traps to another destination/trap receiver. Here is how you do it:
1)Ensure Net-SNMP is installed on the RMM Central server.
2)Create a batch file sendtrap.bat to invoke the snmptrap command. Place this file in /rmmcentral folder. The syntax for this command is as follows:
snmptrap options hostname community trap parameters...
For Version 1, the required trap parameters are:
where
| -v 1 | The SNMP version |
| -c | The community string and the default SNMP community string is public |
| %1 | The manager name, viz., the hostname or the IP address of the manager that must receive traps. |
| .1.3.6.7.2.1.3.1 | Specify the appropriate enterprise OID |
| %2 | The agent-name, that is the hostname or the IP address of the device for which an alarm is generated. |
| .1.3.6.7.2.1.3.1.1.2 | Replace with the appropriate specific OID |
| 1 | The generic type number |
| 6 | The specific type number |
| 10000 | The sysUptime in milli-seconds |
| s | Refers to the data type of the OID (string type) |
|
"%3,%4,%5,%6" (replace the % symbol with $ if you are doing it on a Linux box) |
The message from RMM Central that can contain one or more of the following variables:
|
3)Configure a 'Run Program' notification profile specifying the following:
Command Name: sendtrap.bat
Program Arguments :[manager-name] $source $displayName $strModTime $category $severity $message
4) You can associate this notification profile to devices using the Quick Configuration Wizard. Whenever an alarm is generated on the managed devices, a trap is sent to the other monitoring server.
To receive alerts from the device, make sure you configure the routers to send traps to RMM Central (you will not receive alerts from the device if the trap host is not configured in the source router). Telnet the router and type the following command:
snmp-server host (rmmcentral server IP) traps (host community string) rtr For instance, if the RMM Central host IP Address is 192.168.18.128, and the community string is private, the command would be: snmp-server host 192.168.18.128 traps private rtr
This should be possible with Syslog monitoring.
https://www.manageengine.com/network-monitoring/syslog-monitoring.html
http://help.opmanager.com/add_syslog_rules
The other option is to configure the router or switch to send a trap notification whenever a login occurs.
RMM Central processes traps from devices into meaningful alerts.
Though the trap OID is the same, there must be some difference in the varbinds which shows the AP's names. RMM Central can process that value (failure component) and create a new alarm for each Access Point. Refer to the following link for steps to know about trap processing in OManager.
http://help.opmanager.com/processing_traps
Many users get confused with 'sysuptime' from RFC1213 MIB, but it is not representative of the system uptime. It is the time in hundredths of a second since the network management portion of the system was last re-initialized.
You have to use hrsystemuptime to find the system uptime. You can add this as a new monitor to the existing device templates through Add Monitor -> Add Bulk option. [ Use the add bulk option to include mathematical expressions to the monitor ].
hrsystemuptime OID is ".1.3.6.1.2.1.25.1.1.0". You have to divide this by 8640000 to give the system uptime in days.
See the attached image to findout the expression to be used and the value that i got from this OID for an SNMP node.
To this, you can configure thresholds.
Make sure the right monitor is added for the server. Either WMI or SNMP, you have these set of monitors.
You can set thresholds for all the monitors and get the alert once it is violated.
As per the design RMM Central triggers 3 alarms for the device down state - when it misses 1 poll (attention), 3 poll (trouble) or 5 poll (critical). It sends only one email notification based upon the option selected for when the Device misses poll(s) in the Notification Profile.
The following are the possible reasons for the multiple email notification,
a) Admin --> Alarm Escalation - Check whether you have enabled any Alarm Escalation for the device.
b) Notification Profile - Check whether you have enabled when the Device misses poll(s) on multiple notification profile and associated the device.
Here are the steps to make RMM Central send alarms when data is not collected:
RMM Central can be configured to send 'Data not collected' alerts when monitoring and data collections stops for some reason. This requires a little tweak to a configuration file. Here are the steps:
'Data not collected' alarms is now generated when data collection fails for some reason.
Users can send alarm details as an email message in RMM Central.
The powered off VM needs to be configured for alarm suppression to disable any further alarms. To configure alarm suppression, follow the mentioned action in RMM Central : VM snapshot -- Actions -- Suppress Alarms, or Settings -- Configuration -- Quick Configuration Wizard -- Associate an Alarm Suppression rule to several devices.
A. Both Zoho Maps and Google maps are available in the Maps section (Maps > Maps). In the toggle switch, choose Zoho Maps/Google Maps.
A. Go to Maps > Maps and click on the dialogue box in the top right corner to access the Filter by Type feature. Select the device type by which filter has to be applied.
A. Go to Maps > Maps and click on any existing device on the Map (Zoho/Google). Click the Delete button and press Ok on the popup to delete the device from the Map.
A. Go to Maps > 3D floor views. Click on Create New to create a 3D floor view.
A. Go to Maps > Rack Views. Click on the required Rack and click on the QR code icon on the top right corner of the screen. Specify the values for width, height and devices per row and click Generate. The QR code will be generated and displayed in a pop up window. You can print this QR code / save it as PDF.
Any layer 2 map discovered in RMM Central can be exported into Microsoft Visio. Visio uses simple graphics and layouts to represent flowcharts and decision diagrams and are also used for network diagramming. This export process is greatly simplified by the introduction of an exclusive add-on. Learn More
The powered off VM needs to be configured for alarm suppression to disable any further alarms. To configure alarm suppression, follow the mentioned action in RMM Central : VM snapshot -- Actions -- Suppress Alarms, or Settings -- Configuration -- Quick Configuration Wizard -- Associate an Alarm Suppression rule to several devices.
This can't be edited. However, you can save it as a Business View and edit/modify the device and link positions.
RMM Central lets you create powerful dashboards with over 90 widgets to choose from. The widgets display different fault and performance data with provision to drill-down. To know your network health at a glance, all you will need is a quick look at your favorite network management console , RMM Central :)
We have had a few users asking us in our forums or writing to us at support to know if RMM Central widgets can be embedded into their web pages. Yes, RMM Central provides the flexibility of embedding widgets or dashboards into a web page, making it easier for a user or a group to access a specific set of information without having to log in and log out every time.
You can embed a widget or a dashboard using an <iframe>. For the benefit of those who have not seen the procedure posted in our forums, here are the steps:
Embedding a Widget
The code snippet to embed a widget is given below:
<iframe src="http://OpManagerServerName:Port/generateWidget.do?widgetID=194&widgetWidth=520" width=520 height=400 frameborder="1" scrolling="no">
In the above snippet, replace the src name with the actual host name and the port number on which RMM Central is hosted and the ID of the widget that you want to embed. Mouse-over the edit icon on the top right corner of the widget to see the ID.
Embedding a Dashboard
You can embed the default dashboards or create a new dashboard and embed.
Here is the snippet to embed a dashboard:
<iframe src="http://OpManagerServerName:Port/customDashboard.do?methodCall=showCustomDashboard&dashboardID=303" width= height=in_pixelsin_pixels frameborder="1">
The snippet to access the dashboard without having to log-in every time is:
<iframe src="http://OpManagerServerName:Port/customDashboard.do?methodCall=showCustomDashboard&dashboardID=303&reqUserName=guest_user&reqPassword=guest_password" width=in_pixels height=in_pixels frameborder="1">
where the user name and password are passed as additional arguments.
Replace the user name, password and the dashboard ID. Access the required dashboard from the WebClient to see the ID passed in the url.
In VoIP Monitor, business views help you to know the status of the device and call path between devices at a glance. Whenever a new VoIP monitor is created, a business view (image shown below) of it also gets created automatically with the default background and device icons. However, later you can modify the background and device icons if required.
In the business view, mouse-over the device icon or name/IP and call path to view its details. Click on the device icon or call path will open the snapshot page of the device or the call path respectively.
Accessing VoIP Monitor Business Views
From Home --> Dashboards --> Custom --> click on Create New Dashboard, or alternatively click on the green 'Create/edit Dashboard' button on the top right. Configure the following details:
The default dashboards in RMM Central cannot deleted. You can delete the custom dashboards. Here are the steps:
To add a new widget to a dashboard follow the steps given below:
To delete or edit a widget,
To embed a NOC view link, follow the steps below:
Learn more here.
Prerequisite: Mail Server has to be configured. To configure Mail Server Settings, click here.
Prerequisite: Mail Server has to be configured. To configure Mail Server Settings, click here.
To make report generation more simpler and user friendly, RMM Central lets you generate utilization, discards, traffic and error reports for multiple interfaces with ease. These reports can be customized to display interface data in the form of graphs and tables for custom time intervals.
To generate a traffic and utilization report for a specific set of interfaces,
Graphs will have the data displayed with time in the x-axis and traffic/utilization in the y-axis. The Table view will have the minimum, maximum and average values of the traffic and utilization of all the selected interfaces individually.
To configure CustomFields for a device:
Now the Notification Profile is active only during your business hours as configured.
To associate Notification Profiles to Datastores:
Now the Notification Profile is associated to the Datastores selected.
If you have installed NetFlow plug-in, then follow steps given below. These steps should be followed only if OpManger is SSL enabled.
The NetFlow plug-in will also be SSL-enabled now.
RMM Central shows the connectivity between a switch and other connected devices in the network in Switch Port Mapper. You get the details such as the MAC address, IP Address and DNS names of the devices connected to the switch. You need to provide the details such as the community string and port number of the switch and if needed, the details of the server or router that may contain the layer 3 details. To view the switch port mapping details, follow the steps given below: