What is Active Directory?
Active Directory (AD) is the primary directory service for more than 90% of organizations around the world.
It stores details about users, their passwords, and their access privileges. Whenever a user attempts to log on to a domain-joined machine by supplying their credentials, it is AD that verifies their identity and authenticates them. AD also authorizes users when they try to access network resources. It checks if they have adequate permissions to access a resource; if yes, they get access; if not, they don't get access.
Active Directory threats
While organizations leverage AD to manage permissions and access to network resources, it is not always straightforward as there are numerous settings and configurations. If you use it correctly, AD is a powerful tool. At the same time, a misconfiguration can lead to gaping weaknesses that can be exploited. Some examples are:
- Exposure of sensitive information to unauthorized users.
- Addition of a non-privileged user into a privileged group.
- Modification of GPOs.
- Higher privileges being granted to users who don't need them for their jobs.
- Back doors for external attackers to exploit.
- Compromise of an administrator or high-privilege account.
- AD attacks such as Kerberoasting, SMB relay, and Link-Local Multicast Name Resolution (LLMNR).
The above are just some of the security weaknesses that can arise if AD is not configured properly.
Active Directory auditing
Weaknesses in your AD can also lead to compliance violations. Numerous compliance mandates such as the PCI DSS, HIPAA, SOX, FISMA, the GDPR, and the GLBA require that you log the events that occur in your AD. You may need to access these logs to interpret a particular sequence or pattern of events during a forensic analysis.
It is your responsibility to protect your Active Directory and secure your network. You can accomplish this by auditing and tracking changes in your Active Directory, including changes to users, computers, groups, OUs, and GPOs.
There are primarily two types of solutions that can help you audit your AD:
An on-premises AD auditing tool
This will be AD auditing software that's installed within your network, on your own server.
A cloud-based AD auditing tool
This will be AD auditing software that's deployed in the cloud as a SaaS solution. In fact, some next-gen cloud SIEM solutions also provide AD auditing capabilities, which can help you cater to a wider range of use cases.
Benefits of Active Directory auditing from the cloud
Auditing Active Directory from the cloud has the following benefits:
- Access from anywhere
- Higher availability and performance
- Log storage in a centralized data center
- Flexibility and agility
- Quick deployment and results
Advanced AD monitoring
The following capabilities help organizations leverage AD auditing to enhance business performance.
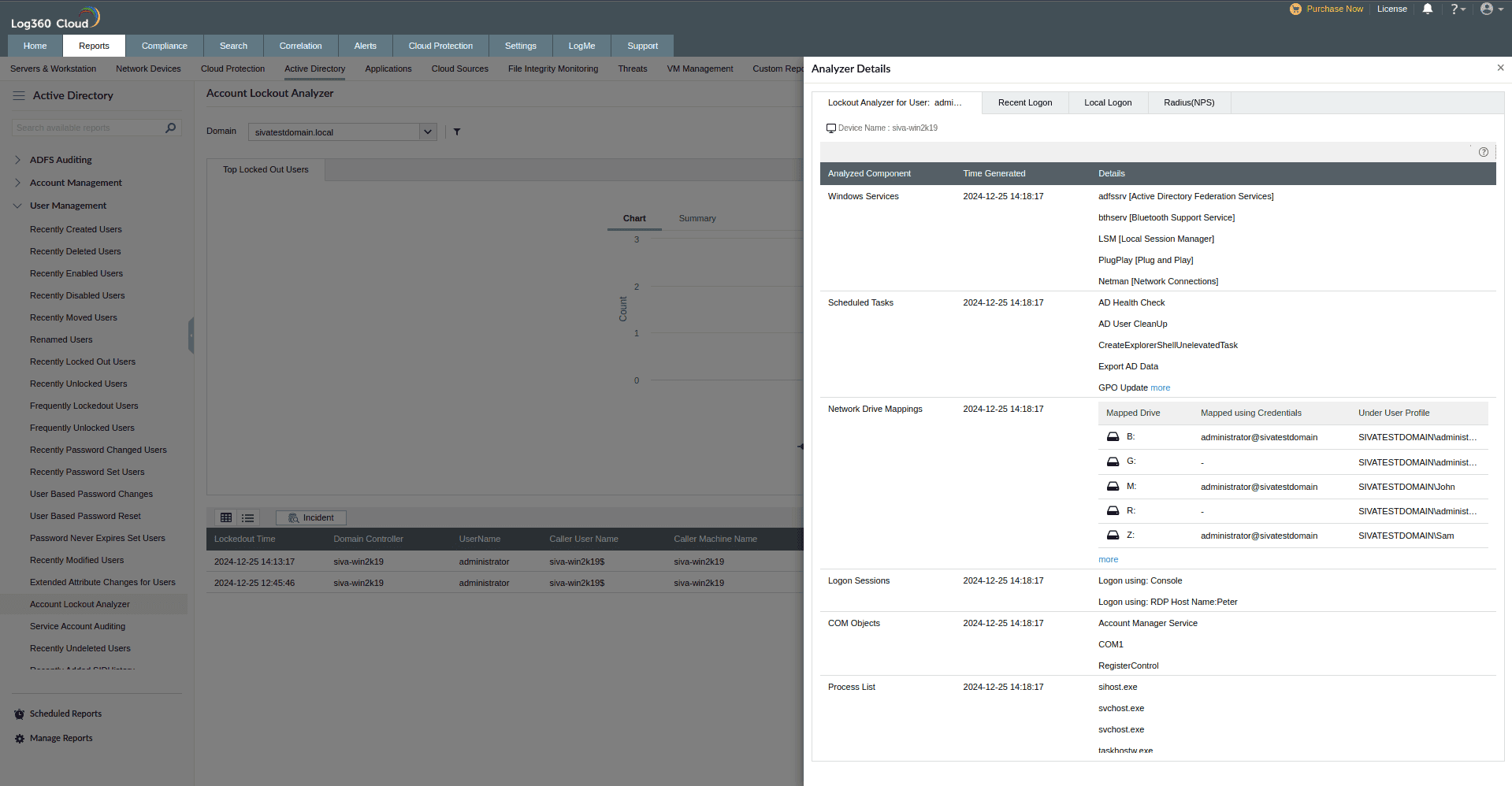
User work hours monitoring
User work hours monitoring is essential to calculate the billable hours of an employee on an average work day. Though employee work hours can be calculated by tracking the check-in and check-out times, actual productivity of a user can only be estimated by advanced time tracking.
Therefore, tracking user activities on a workstation is essential to arrive at the actual working hours and idle hours of the employee. This includes tracking events such as logon/logoff, console locking/unlocking, remote session connections/disconnections, and screensaver usage. Tracking these events not only helps in understanding employee productivity but also in identifying employee work patterns.
For businesses operating across different time zones, tracking work hours can be challenging. To address this, work hours monitoring can be customized for remote and onsite employees working across multiple time zones.
Further, the user work hour monitoring reports can be generated on a daily and weekly basis for effective and efficient tracking of employee productivity.
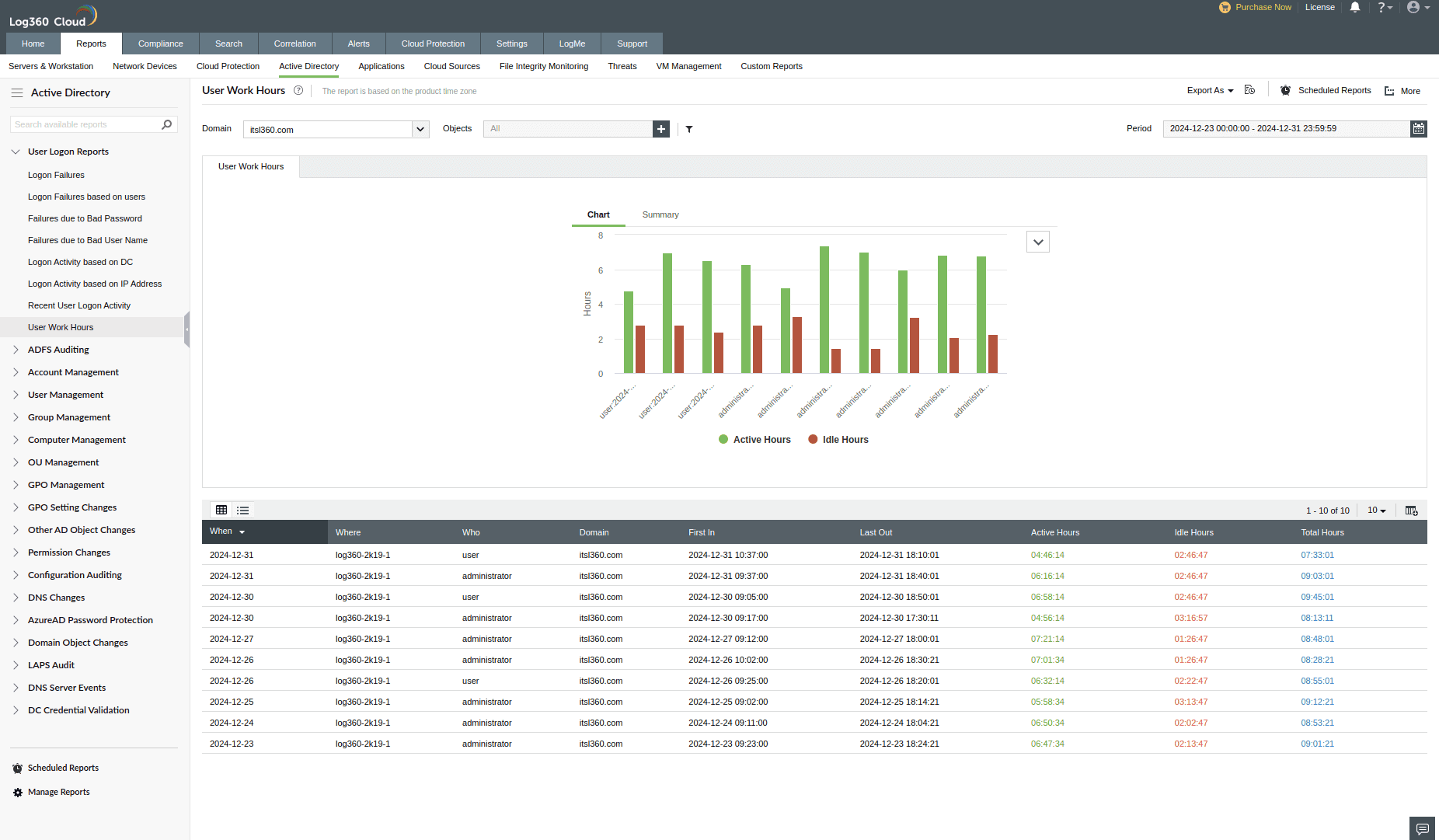
Account lockout analyzer
Account lockouts are critical security features in Active Directory (AD) that help prevent unauthorized logons and brute-force attacks. However, account lockouts can also occur due to other factors, such as expired passwords or misconfigurations, which may disrupt business operations.
Thus, analyzing account lockouts and identifying the source of authentication failure is essential to troubleshoot unnecessary lockouts. Monitoring account lockout events at the domain level and in the local machine is required to identify abnormal lockout events. Additionally, tracking previous logon attempts, logon failures, and the cause of logon failure can help identify specific patterns in lockouts.
While analyzing locked-out accounts, it is crucial to examine the associated machines and their Windows components like services, mapped drives, and logon sessions to troubleshoot the root cause and recover the account.
Further, with predefined alert profiles, account lockouts can be notified in real-time, enabling prompt action to reduce downtime.
AD auditing use cases
In today's world, AD auditing from the cloud gives you higher flexibility, agility, and scalability. Furthermore, you can administer your AD without worrying about storage.
Explore how you can track the following from the cloud:
1) Tracking user authentications on domain controllers
Whenever a user logs on to their domain-joined machine, it generates two events:
- A logon event at their local machine
- An authentication at the domain controller that verifies the logon
You must monitor authentication events that are recorded at the domain controller. This will be a combination of both successful and unsuccessful authentications.
You will need a report that gives you details about the domain controller where the authentication occurred, the machine where the actual logon attempt occurred, the time of the logon, the user account involved, and the reason for the logon failure if any.
Why you should track user authentications on domain controllers
By tracking logon authentications, you can check which user account logged on or attempted to log on to which machine. This is important from a compliance, administration, and security point of view.
Compliance: Regulations, such as SOX, HIPAA, the PCI DSS, the GLBA, and the GDPR, require you to record and track user logon activity. Furthermore, you should be able to access logon activity logs on demand.
AD administration: A report on user logons can help you troubleshoot and fix AD configuration errors. For example, a user account could authenticate successfully onto a machine that does not belong to them, while your organization (in principle) does not allow such logons. You can see this error and fix it.
Security: A successful user authentication is a part of most attack kill chains. This authentication can be done by a rogue insider or it could be the work of an external attacker who has compromised an account. You can see such logon authentications and spot patterns of a possible attack.
2) Tracking user logons on particular workstations
A user will log on to their machine multiple times during their workday. Most of these logons in an organization will happen at the beginning of the day or just after lunch time. Whenever a user logs on to their workstation, it starts a session that runs until a logoff occurs.
You must track user activity on particular workstations for the following reasons:
Compliance: Regulations such as the GLBA and FISMA require you to track local logon and logoff activities at workstations.
AD administration: You can investigate local logon failures and other password-related issues. Furthermore, you can also track user work hours and productivity by tracking the duration of sessions.
Security: You can track instances of possible lateral movement. For example, a replay attack happens when a user logs on to a machine through another machine. This can be tracked if you have an audit-ready report that gives you all the relevant details. You can also track continuous failed interactive logons by user accounts, which could be indicative of a brute-force attack.
Often, you need to correlate the information from user authentications done by the domain controller with the information from user logons at a workstation to get a complete picture of what's going on.
3) Tracking user creations, deletions, and modifications
In a usual user life cycle, user accounts are created, deleted, and modified. A user account is usually created when a new employee joins an organization. A user account is first disabled and then deleted when an employee leaves the organization. It is modified when attributes of the user account change. For efficient AD administration, all of these changes must be tracked. You will need a group of reports that will give you details about:
- The user account that was created, deleted, or modified.
- The account that created, deleted, or modified the other user account.
- The time of the event.
- The domain controller where the account was created.
- The newly modified attributes of the user account, if any.
4) Tracking changes to security groups and organizational units
Security groups are created in AD to manage the permissions of users and computers. Instead of assigning permissions to each user or computer separately, you will find it more efficient to create a group for those accounts that require the same level of privileges.
Once a group is created, you can enable certain permissions to users, computers, or other groups that belong to the group. They can then access a particular resource like a shared folder.
Organizational units, on the other hand, define administrative boundaries within your Active Directory. They usually mimic the organizational structure of an organization. OUs can contain users, groups, computers, and other child OUs. Group Policy Objects (GPOs) are linked to OUs.
You need details about the group or OU such as creation time; users, computers, groups or OUs added within; and the administrator account that added these objects. Tracking all of this will enable you to defend against privilege escalation and other attack kill chains.
Example:
Suppose that an attacker:
- Gets initial access to Active Directory.
- Is able to change a security group into a distribution group.
- Adds a newly created user account into the distribution group.
- Changes the distribution group back into a security group, gaining heightened privileges for the user account.
You must be able to track such changes in Active Directory in real time.
5) Tracking changes to GPOs and domain policies
GPOs are a list of policy settings that are applied to an administrative boundary such as the complete domain or an organizational unit. The policies contained within a GPO will apply to the entire OU or domain to which it is linked.
You must therefore be able to track GPO settings and link changes. This will ensure efficient AD administration and security. In case there are GPO configuration errors, you can identify and fix them. In case an adversary changes the nature of GPOs within your AD environment, you can view that too.
6) Tracking privilege escalation and permission changes
You must be able to track permission changes that take place in your Active Directory in real time. These permission changes can happen at different levels, such as:
- The entire domain.
- Organizational units.
- Schema.
- GPOs.
- Users.
- Groups.
And more.
A permission change at any of these levels can be the handiwork of an adversary looking to escalate privileges. Or it could be the case of a grave configuration error that needs to be fixed immediately. Either way, you need to know about this, and take action to plug such a loophole.
AD auditing with Log360 Cloud
Out-of-the-box reports and alerting
Leverage over 100 AD reports to monitor changes to users and computers, account lockouts, configuration changes, and GPOs and get alerted in real-time.
Compliance
Ace compliance to regulatory mandates with audit-ready reports for SOX, HIPAA, the GDPR, the PCI DSS, ISO 27001, and more.
Easy deployment and management
Automatically discover DCs in your network, and quickly get started with auditing. Access your reports from anywhere while worrying less about log storage.
Get started with secure AD auditing in the cloud.
Try Log360 Cloud now.
FAQ
- How does event log collection occur?
-
Different cloud-based Active Directory auditing tools collect activity logs in different ways.
Log360 Cloud uses the WMI protocol to fetch logs from the Event Viewer of domain controllers and workstations.
- Where are the logs stored in a cloud-based AD auditing solution?
-
Depending on where the user of the AD auditing solution is logging on from, the collected logs will be stored in the nearest data center. Currently, Log360 Cloud is operational from the following data centers:
- US
- Europe
- Australia
- India
- Is a cloud auditing solution more or less expensive than an on-premises solution?
-
This is dependent on the amount of storage you need. Estimate the sizing requirements for log storage with Log360 Cloud's storage calculator.