This document addresses an authentication bypass vulnerability (CVE-2021-44515) in ManageEngine Endpoint Central MSP and elaborates an incident response plan if your system is affected.
Vulnerability ID: CVE-2021-44515
Severity: Critical
Update Release Date: 3rd December 2021
An authentication bypass vulnerability in ManageEngine Endpoint Central MSP was identified and the vulnerability can allow an adversary to bypass authentication and execute arbitrary code in the Endpoint Central MSP server.
Note: As we are noticing indications of exploitation of this vulnerability, we strongly advise customers to update their installations to the latest build as soon as possible.
We have developed an Exploit Detection Tool that will help you identify whether your installation has been affected by this vulnerability. You can download the tool here
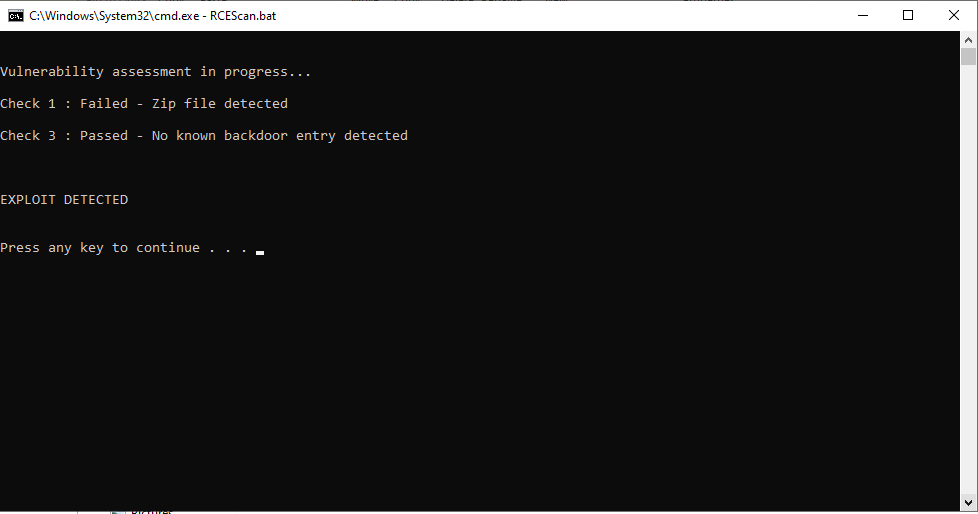
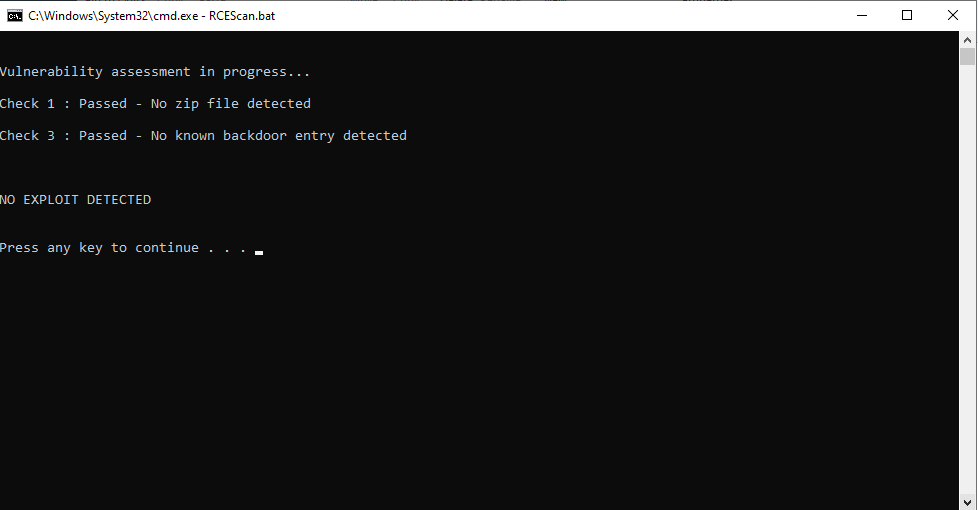
1. Disconnect the affected system from your network.
2. Back up the Endpoint Central MSP database using these steps.
3. Format the compromised machine. Note: Before formatting the machine, ensure that you have backed up all critical business data.
4. Download and install Endpoint Central MSP.
5. Restore the backup and start the server.
6. Once the server is up and running, update Endpoint Central MSP to the latest build using the following steps:
Recommendation: Initiate a password reset for all services, accounts, Active Directory, etc. that has been accessed from the service installed machine. It is better if AD administrator passwords are also reset.
Update Endpoint Central MSP to the latest build using the following steps:
Keywords: Security Updates, Vulnerabilities and Fixes, CVE-2021-44515, authentication bypass