Onboarding Oshkosh Corp: Their journey of choosing Log360 and implementing centralized network monitoring

About Oshkosh Corporation
Oshkosh Corporation, a long-standing Fortune 500 company, has been at the forefront of designing and manufacturing specialty vehicles and equipment for over a century. Serving defense, firefighting, and emergency response industries worldwide, the company drives innovation in electric vehicles, intelligent systems, and autonomy, with a strong emphasis on safety, sustainability, and operational efficiency.
-
Organization
Oshkosh Corp -
Country
USA -
Industry
Manufacturing
About the organization
Oshkosh Corporation, a long-standing Fortune 500 company, has been at the forefront of designing and manufacturing specialty vehicles and equipment for over a century. Serving defense, firefighting, and emergency response industries worldwide, the company drives innovation in electric vehicles, intelligent systems, and autonomy, with a strong emphasis on safety, sustainability, and operational efficiency.
This case study document compiles the security requirements of Oshkosh Corp., what led them to choose Log360, and their experience with custom onboarding and post-implementation of the solution.
Breaking down the business requirements
Oshkosh Corp. was looking for a SIEM solution to centralize network monitoring and support their periodic audit processes. The following outlines their key requirements:
- Collect and store logs in a centralized location: Aggregate and archive logs from diverse sources for streamlined access and compliance.
- Removable disk auditing: Tracking and auditing removable media usage to prevent unauthorized data transfers and ensure data security.
- Reports on AD changes: Detailed reporting on AD changes to maintain a clear audit trail and detect any unauthorized modifications.
- Privileged user activity monitoring: Monitoring of privileged users to track their actions and safeguard against potential insider threats.
The Solution: Log360
1. Why Log30?
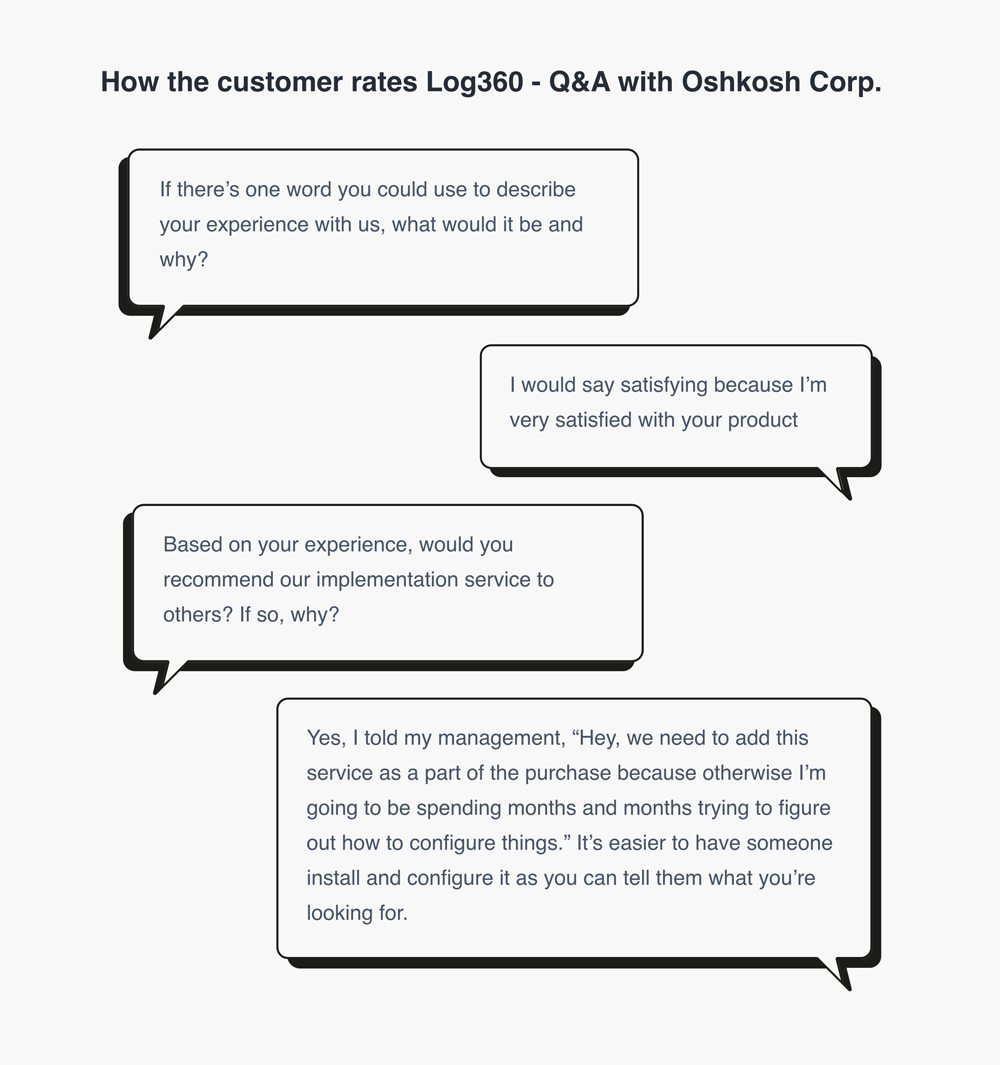
"One of the things that attracted me to your product is that, unlike others on the market, you offer a demo of the full integration. This allows me to check online, find exactly what I need, and truly see if it will do what I want."
While searching for a SIEM solution, Oshkosh Corp. evaluated several options, including Splunk. However, their choice of Log360 was solidified by:
- The confidence they gained from the thorough online demo of the features that enabled them to effectively assess and present why the product met their needs to senior management.
- The availability of onboarding process and custom installation services. This significantly accelerated their implementation timeline, reducing the usual configuration period from months to just a few weeks, all while ensuring a smooth and reliable setup.
2. Addressing security needs
During the final review discussion, Calvo highlighted how the solution transformed their security management. With Log360, they gained centralized visibility into all network devices and their communications, along with the ability to detect unauthorized use of removable disks and software installations. A critical security policy in their environment mandates that only administrators can install software. By integrating Log360, they now have clear oversight of software installations, including who is responsible. Additionally, features like intuitive dashboards, real-time alerts, log search, and forensic analysis are a huge benifit.
3. Continuous monitoring and compliance audits
Oshkosh Corp. required real-time continuous monitoring to ensure that essential security controls were consistently enforced. Previously, their weekly audit process was labor-intensive, involving manual checks of individual systems and review of logs. With the implementation of Log360, this process has been streamlined significantly, as the reports are now readily available, making audits far more efficient.
"Log360 gives me the reports that I need to complete the compliance audits on a weekly, monthly, and quarterly basis, so then I can show an auditor, 'Hey, we are doing that, here's the reports, and we are monitoring, and we're making sure there's no anomaly within the system,"
About custom onboarding
Custom onboarding is a ManageEngine service that provides solution implementation to clients upon request. This service includes installation and customized configuration of ManageEngine solutions. It enables clients to seamlessly begin work without worrying about the complexities of installation, deployment, and product use. Every client environment is unique and requires additional support beyond the basic installation and standard features. With custom onboarding, clients have the option to engage a team of product experts to manage the installation, implementation, customization, and training based on the business needs.
About Log360
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. Vigil IQ, the solution's TDIR module, combines threat intelligence, ML-based anomaly detection and rule-based attack detection techniques to detect sophisticated attacks, and offers an incident management console for effectively remediating detected threats. Log360 provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities.
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It combines threat intelligence, machine learning-based anomaly detection, and rule-based attack detection techniques to detect sophisticated attacks, and offers an incident management console for effectively remediating detected threats. Log360 provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities.
Product Documents
Others
2022 Zoho Corporation Pvt. Ltd. All rights reserved.

