Role of cybersecurity teams in threat hunting
Cybersecurity is a field characterized by a constant game of cat and mouse, where defenders and attackers continuously evolve their tactics to outsmart each other. This dynamic is especially evident in the roles played by various specialized teams within cybersecurity, namely the red, blue, and purple teams. Each team plays a vital role in not only identifying vulnerabilities but also in strengthening an organization's ability to defend against cyberthreats effectively. Let's delve into how these teams contribute to the process of threat hunting.
What is the red team in cybersecurity?
The red team functions as a simulated attacker, using offensive tactics to identify vulnerabilities within an organization's security framework. This involves red team testing, which simulates real-world cyberattacks to probe for weaknesses in the organization's defense systems. This team's role is akin to that of a skilled adversary, aiming to breach defenses through various attack vectors. This proactive approach enables organizations to identify and address potential vulnerabilities before they are exploited by actual attackers. The key roles of the red team include:
- Simulation of real-world attacks:
They replicate sophisticated cyberattacks to test the organization's defenses, using tactics, techniques, and procedures similar to those of real-world attackers, thereby uncovering exploitable vulnerabilities. - Identifying weaknesses:
Through simulated attacks, the red team reveals weak points in security systems, policies, and employee practices, highlighting areas susceptible to threats. - Providing insight for improvement:
Insights from red team operations offer valuable information for enhancing security measures and preparing for potential real-world attack scenarios.
What is the blue team in cybersecurity?
In contrast to the red team, the blue team is dedicated to defense. Their role is to detect, respond to, and mitigate cyberthreats. The blue team's responsibilities encompass maintaining the security infrastructure, monitoring for suspicious activities, and implementing defensive protocols. They are the organization's first line of defense, constantly vigilant and ready to counteract any attempted breaches by the red team or real attackers. Their effectiveness is often enhanced through continuous training and staying updated on the latest cybersecurity trends and technologies.The blue team's roles include:
- Monitoring and detection: The blue team is responsible for the continuous monitoring of the organization's networks and systems. They use various tools and techniques to detect unusual activities that could indicate a security breach.
- Response and mitigation: Upon detecting potential threats, the blue team works to contain and mitigate them. This includes implementing security protocols to prevent the spread of an attack and minimize damage.
- Continuous improvement: The feedback and data gathered from handling real-time incidents are used to strengthen the organization’s defenses and refine their threat hunting strategies.
Purple team: A combination of both red and blue teams
The purple team bridges the gap between the red and blue teams. They ensure that the findings from red team assessments are effectively communicated and understood by the blue team. This helps the red and blue teams learn from each other’s experiences and techniques. This collaboration enhances the effectiveness of threat hunting activities.
This dynamic exchange of insights between the red and blue teams under the purple team's framework leads to significant improvements in both attack simulations and defensive tactics, ultimately enhancing the overall cybersecurity of the organization. The purple team's structure in cybersecurity varies based on an organization's needs and size. It can be an independent team or a joint group comprising members from both the red and blue teams.
The red team contributes by simulating advanced cyberattacks testing the organization's defenses against realistic threats. Their efforts help in identifying potential vulnerabilities and areas where security could be breached. On the other side, the blue team focuses on defending against these simulated attacks, using their knowledge to strengthen and refine the organization's defensive mechanisms.
Threat hunting is a proactive, human-driven approach of identifying cyberthreats and vulnerabilities lurking undetected in your network. In the process of threat hunting, these teams play vital roles. The red team's offensive tactics uncover potential threats and vulnerabilities, the blue team's defensive measures work to mitigate these threats, and the purple team's collaborative approach enhances the overall security posture. This continuous cycle of attack, defend, and improve is crucial in staying ahead in the fast-paced world of cybersecurity
Benefits of red, blue, and purple teaming
| Aspect | Red team | Blue team | Purple team |
|---|---|---|---|
| Objective | Proactively uncovers security vulnerabilities through simulated attacks | Ensures adherence to legal and regulatory standards through audits | Synchronizes offensive and defensive strategies for resilience |
| Benefits | Early identification and rectification of security weaknesses | Management of overall cybersecurity risk through compliance | Improved overall security readiness and understanding |
| Threat hunting approach | Proactively searches for vulnerabilities through attack simulations and penetration testing | Monitoring, analysis, and defense strategies | Balances risk by combining offensive and defensive perspectives |
| Role in cybersecurity | Offensive, proactive approach | Defensive, compliance-oriented approach | Integrative, collaborative approach |
| Cultural Impact | Encourages a proactive and vigilant security mindset | Embeds a culture of compliance and legal awareness | Fosters a culture of collaboration and continuous improvement |
Here's how Log360 can help in threat hunting
Log360, a comprehensive SIEM solution with integrated DLP and CASB capabilities, serves as a crucial asset for cybersecurity teams by actively identifying and countering threats. It excels in threat hunting user behavior analysis, and real-time alerts, ensuring immediate attention to suspicious activities. The solution also streamlines incident response with automated remediation and tracks incident resolution for accountability.
In addition, it conducts regular security audits, implements file integrity monitoring, and extends security measures to cloud platforms. Log360 goes above and beyond by integrating a compliance management system with audit-ready report templates for various regulatory mandates such as the PCI DSS, HIPAA, FISMA, SOX, the GDPR, and the GLBA. This robust tool offers a holistic approach to security, safeguarding organizations from a wide range of cyberthreats.
Experience effortless hunting for threats in your network with Log360
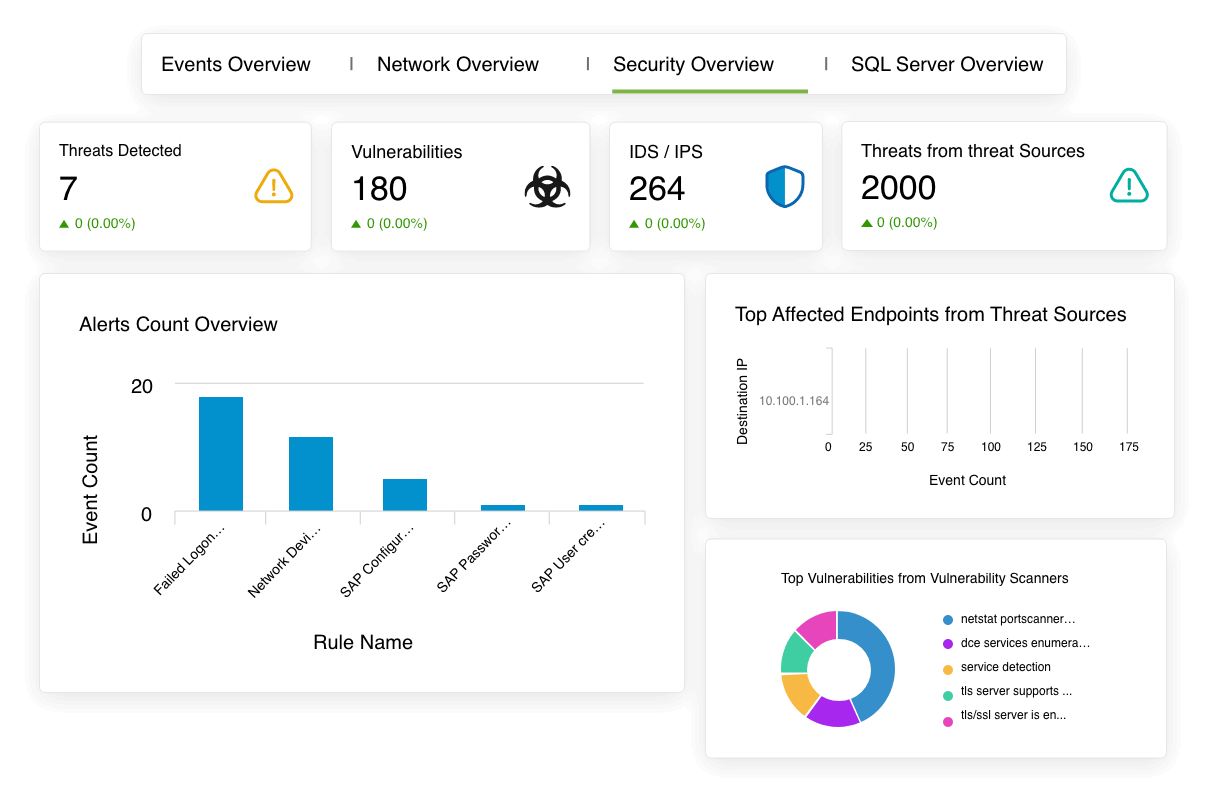
- Get complete visibility into your threat landscape.
- Use real-time monitoring to help analyze and correlate logs.
- Eliminate false negatives and proactively hunt for threats.
- Efficiently counterattack and maintain compliance with industry standards.
- Perform advanced forensic analysis to enhance your cybersecurity efforts.
What's next?
Explore how red, blue, and purple teams work together to uncover and neutralize threats faster.
- Role of cybersecurity teams in threat hunting
- What is the red team in cybersecurity?
- What is the blue team in cybersecurity?
- Purple team: A combination of both red and blue teams
- Benefits of red, blue, and purple teaming
- Here's how Log360 can help in threat hunting