Frequently Asked Questions
Welcome to the ManageEngine Mobile Device Management FAQ Section. This resource is designed to assist you in navigating and resolving common issues encountered during the management of your mobile devices. Our comprehensive solutions aim to address these challenges effectively.
If you encounter any issues that remain unresolved, please reach out to us via email, attaching the necessary log files. Our dedicated support team will promptly review your case and work with you to resolve the issues efficiently.
- General
- What is the difference between Cloud and On-Premises versions of Mobile Device Manager Plus?
MDM Cloud is the SaaS version of the MDM On-Premises. With MDM Cloud, you only have to sign in using your Zoho account and start managing your devices. The data and server configuration is managed by Zoho. Whereas in case of the On-Premises, you have to install the application and configure network settings to setup MDM and manage devices.
- What is the Technician URL for ManageEngine MDM?
The Technician URL for ManageEngine MDM is mdm.manageengine.com. This URL allows administrators and technicians to access the MDM console for managing enrolled devices, configuring policies, and performing remote actions.
- I want to manage fewer than 25 devices. What should I do?
For managing fewer than 25 devices, sign up directly for the free edition of ManageEngine MDM Cloud (supports up to 25 devices at no cost). Sign up here.
- Can I change the admin email address in ManageEngine MDM Cloud?
In the Cloud edition, the admin email address cannot be modified once the user account is created. If the admin email needs to be changed, the recommended approach is to transfer the admin privilegeto another user account with the desired email address.
- Where can I find which version of Mobile Device Manager Plus is running?
You can view the MDM build version at the top-right corner of the console, next to your profile icon. It is displayed as Build Version: <number>.
Example: Build Version: 11.2.2507.02
- Can we install MDM server in linux
No, you cannot install the ManageEngine MDM (Mobile Device Manager Plus) server on Linux.
- What is ManageEngine’s Enterprise Mobility Management (EMM) rating with Google?
ManageEngine is recognized by Google as an Enterprise Gold Partner for Android Enterprise Management.
Learn more: ManageEngine – Android Enterprise Management
- Is ManageEngine MDM a theft protection service?
No, ManageEngine MDM is not a theft protection service. It is an enterprise mobile device management (MDM) solution designed to manage and secure mobile devices like iPhones. However, it includes features such as lost device management and location tracking, which can assist in recovering lost or stolen devices.
- Can I back up personal data on a mobile device using ManageEngine MDM?
No, backing up personal phone data is not supported through ManageEngine MDM
- What is the difference between ManageEngine MDM and Apple Profile Manager?
- ManageEngine MDM is available both on-premises and on cloud.
- ManageEngine MDM can be used for managing multiple platforms unlike Apple Profile Manager, which is Apple-only.
- Profile Manager is more suitable for small Apple-only environments, while MDM is environment-agnostic.
- Dedicated MDM server for superior performance.
- Flexible groups/department management is available in MDM.
- What are the Operating Systems(OS) / platforms supported by Mobile Device Manager Plus?
Currently, the following software platforms are managed by MDM:
- iOS version 4.0 and above
- iPadOS version 13.0 and above
- Android 4.0 and above
- Windows Phone 8.0 and above
- Laptops and Surface pro running Windows 10
- Mac machines running 10.7 or later
- Apple TVs running 7.0 or later
- What are the databases supported by Mobile Device Manager Plus(MDMP)?
MDMP currently supports pgSQL and MS-SQL.
- Does MDM support migration from Cloud to On-Premises?
Yes, MDM supports migration from cloud to on-premises using our in-house migration tool.
- Do you have an option to migrate from ManageEngine MDM standalone version to the MSP version on cloud?
Yes, we support migrating from the standalone version to the MSP version in case of cloud. Contact the MDM cloud support team (mdmcloud-support@manageengine.com) for further details.
- What happens when my trial expires or when I move from Trial edition to Free edition ?
MDM provides you with a 30-day trial of the Professional Edition, where you can manage unlimited devices and add unlimited additional technicians. Once the 30-day trial expires, you can either extend you trial, purchase the product or move to Free edition. After trial expiry if you move to the Free edition, you are allowed to choose the devices(up to 25) that you want to manage. All the apps and profiles distributed to these devices as well as other configurations associated to the selected devices are retained. Free Edition is similar to Trial edition except that Free Edition allows a maximum 25 devices to be managed and no additional technicians can be added.
- Why am I unable to sign up with MDM Cloud service?
When trying to sign up, you encounter an error stating you are part of another organization such as "Access denied for this service. Please contact your Org (<org_name>) administrator [admin@org.com], it implies you are already a registered user as your organization has registered for Zoho Services. There is a super admin assigned for Zoho Services, who is the only who can sign up for any other Zoho service including MDM Cloud. If the super admin has signed up for Zoho services, you may request the super admin to add yourself as a technician to use MDM Cloud. In case you want to try MDM Cloud, you can use an alternate e-mail address to sign up and use the service. If you get redirected to https://mdm.manageengine.com/enroll.do, then you may request the super admin to add yourself as a technician to use MDM Cloud.
- How to avail additional storage for MDM cloud?
In MDM cloud, the default storage will be 5GB. You can avail for additional storage with addons. Contact support for more info.
- How to delete my MDM account?
To delete you MDM account, go to the MDM web console and click on Admin tab from the top menu. Now, select Company Details and click on Delete Account. Follow the on-screen instructions to removed your MDM account.
- Configure MDM
- What are the ports used by the MDM application?
Ensure that the following ports are open in the proxy/firewall. In addition to ports, ensure these domains are allowed in any proxy/firewall/third-party filters.
Port Number Type Purpose Connection Traffic 9020 HTTP ME MDM app and server communication. Inbound to Server 

9383 HTTPS ME MDM App and server communication. Inbound to Server 

443 HTTPS Should be open on Mobile Device Manager Plus server to reach APN, FCM, WNS server. For Android devices:
android.googleapis.com; www.google.com; android.clients.google.com; *.googleapis.com; play.google.com; google-analytics.com; googleusercontent.com; gstatic.com; *.gvt1.com; *ggpht.com; dl.google.com; accounts.google.com; gcm-http.googleapis.com; fcm.googleapis.com; fcm-xmpp.googleapis.com; pki.google.com; clients1.google.com; clients[2...6].google.com
The following domains must be open, based on the country that the server is located in:
Global: analytics.samsungknox.com; prod-knoxlog.secb2b.com; account.samsung.com; gslb.secb2b.com; gsl.samsunggsl.com
US : us-elm.secb2b.com; us-prod-klm-b2c.secb2b.com; us-prod-klm.secb2b.com; usprod-knoxlog.secb2b.com
China : china-gslb.secb2b.com.cn; china-elm.secb2b.com.cn; china-b2c-klm.secb2b.com.cn; china-prod-klm.secb2b.com.cn; china-klm.secb2b.com.cn; china-segd-api.secb2b.com.cn; myknoxapk.blob.core.chinacloudapi.cn
Asia, Africa, Europe, or other regions : eu-elm.secb2b.com; eu-prod-klm-b2c.secb2b.com; eu-prod-klm.secb2b.com; euprod-knoxlog.secb2b.comFor Apple devices:
albert.apple.com; captive.apple.com; gs.apple.com; humb.apple.com; static.ips.apple.com; tbsc.apple.com; *.push.apple.com; gdmf.apple.com; deviceenrollment.apple.com; deviceservices-external.apple.com; identity.apple.com; iprofiles.apple.com; mdmenrollment.apple.com; setup.icloud.com; vpp.itunes.apple.com; gg.apple.com; gnf-mdn.apple.com; gnf-mr.apple.com; gs.apple.com; ig.apple.com; mesu.apple.com; ns.itunes.apple.com; oscdn.apple.com; osrecovery.apple.com; skl.apple.com; swdist.apple.com; swdownload.apple.com; swscan.apple.com; updates.cdn-apple.com; xp.apple.com; *.itunes.apple.com; *.apps.apple.com; *.mzstatic.com; ppq.apple.com
For a detailed list, refer to this document from Apple.
For Windows devices:
https://login.live.com; https://*.notify.windows.com
These ports need to be opened to enable remote control/view with Zoho Assist.
Outbound to Server 
5223 HTTPS Should be open, if the mobile device connects to the internet through the corporate Wi-Fi, it is recommended to configure the IP in the range 17.0.0.0/8. Outbound from Corporate Network Firewall 

5228, 5229, 5230 HTTPS For FCM to reach the managed mobile device.
Host address: https://android.com; play.google.com; android.clients.google.com; www.google.com; googleapis.com; android.googleapis.com; gstatic.com; google-analytics.com; googleusercontent.com; *.gvt1.com; *ggpht.com; dl.google.com; fcm.googleapis.com; fcm-xmpp.googleapis.com; gcm-http.googleapis.com; gcm-xmpp.googleapis.comAs FCM doesn't provide specific IPs, you should allow your firewall to accept outgoing connections to all IP addresses contained in the IP blocks listed in Google's ASN of 15169.
Learn more.Outbound from Corporate Network Firewall 

5235,5236 HTTPS For Firebase Cloud Messaging (eg. EMM-DPC communication). Host address: https://gcm-xmpp.googleapis.com; gcm-http.googleapis.com; android.googleapis.com Outbound from Corporate Network Firewall 

Also, ensure Mobile Device Manager Plus server has adequate permission(s) to contact the domains listed here.
TLS and TCP protocols are used for enrolling devices in MDM.
- What are the domains accessed by MDM for enrolling and managing devices?
Both the MDM server and the device to be enrolled in MDM must have access to the following domains, which are to be excluded/allowed in firewall and/or any third-party filters.
Platform Domains Purpose Allow in Server Allow in Device All Platforms
(Android, iOS, windows)https://patchdb.manageengine.com Used for accessing the patch database for patch management and deployment. 

https://creator.zoho.com Access for creating custom business applications using Zoho Creator. 

https://mdm.manageengine.com:443 Enables ManageEngine Mobile Device Management (MDM) functionalities. 

https://upload.zoho.com Allows to enable secure file uploads between the server and devices. 

https://download-accl.zoho.com/ Allows servers and devices to securely download required parameters and resources from Zoho’s update server.
Allow it country specific:
https://download.zoho.eu/
https://download.zoho.in/
https://download.zoho.com.au/
https://download.zoho.com.cn/
https://download.zoho.jp
https://download.zohoone.ca
https://download.zoho.uk
https://files.zoho.sa
https://files.zoho.ae

iOS https://api.push.apple.com Facilitates Apple Push Notification Service (APNs) for device communication. 

https://itunes.apple.com:443 Provides access to Apple iTunes Store for app downloads and updates. 

https://vpp.itunes.apple.com Manages Volume Purchase Program (VPP) licenses. 

albert.apple.com
iprofiles.apple.comUsed for device activation and profile configurations. 

crl3.digicert.com
crl4.digicert.com
ocsp.digicert.comOnline Certificate Status Protocol (OCSP) for verifying Apple certificates. 

setup.icloud.com
gateway.icloud.comUsed for initial device setup and accessing iCloud services. 

https://ax.init.itunes.apple.com Communicates with Apple’s activation servers during device setup. 

https://ppq.apple.com Required for Apple ID and purchase verification processes. 

http://is2.mzstatic.com Used by Apple services to deliver static resources such as images, icons, and other multimedia assets required for Apple Store content or related application 

ocsp.apple.com Online Certificate Status Protocol (OCSP) for verifying Apple certificates. 

https://buy.itunes.apple.com/ Facilitates purchase and transaction-related services on the iTunes Store, including app purchases, subscriptions, and in-app purchases. 

https://uclient-api.itunes.apple.com Used by Apple to manage user interactions with the iTunes Store API, including app installations, updates, and other client-side operations related to the store. 

*.zohoassist.com:443 Enables access to Zoho services, including Zoho Assist for remote troubleshooting. Note: To configure the firewall for compatibility with Zoho Assist, refer to our Zoho Assist Guide.


https://mesu.apple.com Used by Apple devices to check for and download software updates, including iOS, iPadOS, macOS, and other Apple firmware updates. 

https://bag.itunes.apple.com This domain is used by Apple services to fetch configuration files, metadata, and other resources required for the iTunes Store, App Store, and related Apple services. 

https://mdmenrollment.apple.com Used for enrolling Apple devices into Mobile Device Management (MDM) Note: If a load balancer is used, ensure the same outgoing IP is used for consistency and to avoid any connection issues. This helps in maintaining a stable communication channel for device enrollment.


Windows https://login.live.com Authentication for Microsoft services. 

https://*.notify.windows.com
https://*.wns.windows.com
https://*notify.live.netWindows Push Notification Services (WNS) for managing notifications. 

login.microsoftonline.com Used for authentication and access management to Microsoft services, including Microsoft 365, Azure, and other Microsoft online platforms. 

Androids (Non-Samsung devices) *.googleapis.com Google API and account authentication access. 

https://assist.zoho.com:443
*.zohoassist.com:443Enables access to Zoho services, including Zoho Assist for remote troubleshooting. Note: To configure the firewall for compatibility with Zoho Assist, refer to our Zoho Assist Guide.


googleapis.com:443
accounts.google.com:443Google API and account authentication access. 

Allowed in the Corporate Network Firewall *.googleapis.com Google API and account authentication access. 

play.google.com
android.comEnables access to Google Play Store and Android services. 

google-analytics.com Used by Google Analytics to track and report website traffic, user interactions, and behavior analytics. 

googleusercontent.com Used by Google to host and deliver user-generated content, such as images, documents, and other assets stored in Google services (e.g., Google Drive, Google Photos). 

gstatic.com Used to serve static content such as scripts, stylesheets, fonts, and other assets for Google's services and applications. 

*.gvt1.com
*.gvt2.com
*.gvt3.comGoogle services for content delivery and updates. 

*.ggpht.com Used by Google to host and deliver high-resolution images, thumbnails, and other multimedia content for services like Google Photos and Maps. 

dl.google.com Used for downloading Google software, including browser updates (e.g., Chrome) and other Google applications. 

dl-ssl.google.com Provides secure HTTPS downloads of Google software and application updates, ensuring encrypted and safe transfers. 

androidclients.google.com Facilitates communication between Android devices and Google's services, including app and system updates. 

gcm-http.googleapis.com Used by Google Cloud Messaging (GCM) for HTTP-based push notifications to Android devices. 

gcm-xmpp.googleapis.com Supports Google Cloud Messaging (GCM) for real-time XMPP-based communication and notifications on Android devices. 

android.googleapis.com Handles Android-specific API services, including device updates, application installations, and authentication processes. 

fcm.googleapis.com Used by Firebase Cloud Messaging (FCM) to send notifications and data messages to Android and iOS devices. 

fcm-xmpp.googleapis.com Provides real-time communication for Firebase Cloud Messaging (FCM) using the XMPP protocol for message delivery to devices. 

pki.google.com Used for Public Key Infrastructure (PKI) services to validate and manage Google’s SSL certificates for secure communications. 

clients1.google.com
clients[2...6].google.comFacilitates client-specific operations and requests, including application updates and services from Google. 

https://assist.zoho.com:443
*.zohoassist.com:443Enables access to Zoho services, including Zoho Assist for remote troubleshooting. Note: To configure the firewall for compatibility with Zoho Assist, refer to our Zoho Assist Guide.


googleapis.com:443 Used to access Google's APIs over secure HTTPS connections. 

accounts.google.com:443 Google API and account authentication access. 

notifications.google.com:443 Used to manage and deliver notifications from Google services and applications. This includes system updates, app notifications, and alerts for Android devices and Google services. 

https://mdmdatabase.manageengine.com Centralized database for ManageEngine MDM, storing device details and configurations. 

Androids (Samsung devices) China-Only https://china-gslb.secb2b.com.cn:443 Used for Global Service Load Balancing (GSLB) in China to manage traffic and ensure optimal routing for Samsung Knox services and related infrastructure. 

https://china-elm.secb2b.com.cn:443 Facilitates access to the Samsung Enterprise License Management (ELM) system in China, managing the distribution and activation of enterprise licenses for Samsung Knox. 

https://china-knox.secb2b.com.cn:443 Supports Samsung Knox services in China, including device management and secure enterprise deployments via Samsung's Knox platform. 

https://china-b2c-klm.secb2b.com.cn:443 Handles B2C (business-to-consumer) services related to Samsung Knox in China, providing access to management tools and resources for consumer-facing applications. 

https://china-prod-klm.secb2b.com.cn:443 Supports production-level services for Samsung Knox in China, providing essential infrastructure for enterprise-level device management and application security. 

United States of America-only https://gslb.secb2b.com:443 Used for Global Service Load Balancing (GSLB) to manage and distribute network traffic efficiently across multiple data centers. 

https://gsl.samsunggsl.com:443 Global services for Samsung Knox integration. 

https://us-prod-klm-b2c.secb2b.com:443 Supports the B2C (business-to-consumer) services related to Samsung Knox in the U.S., offering access to tools and resources for consumer-facing applications and secure device management. 

https://us-prod-klm.secb2b.com:443 Facilitates production-level services for Samsung Knox in the U.S., providing enterprise-level device management and security solutions. 

https://usprod-knoxlog.secb2b.com Handles logging and tracking services for Samsung Knox devices in the U.S., ensuring detailed logs for security and management activities on enterprise devices. 

https://us-elm.secb2b.com:443 Supports access to Samsung's Enterprise License Management (ELM) system in the U.S., facilitating license distribution, activation, and management for Samsung Knox services. 

https://us-knox.secb2b.com:443 Provides services related to the Samsung Knox platform in the U.S., offering secure device management, configuration, and security features for enterprise deployments. 

https://us-b2c-klm.secb2b.com:443 Supports B2C-related services for Samsung Knox in the U.S., allowing access to consumer-level management and security solutions for devices. 

All other countries https://gslb.secb2b.com:443 Used for Global Service Load Balancing (GSLB) to efficiently manage traffic and ensure high availability for Samsung Knox services and infrastructure across regions. 

https://gsl.samsunggsl.com:443 Global services for Samsung Knox integration. 

https://eu-elm.secb2b.com:443 Supports Samsung's Enterprise License Management (ELM) system in Europe, providing tools for distributing, activating, and managing enterprise licenses for Samsung Knox services. 

https://eu-knox.secb2b.com:443 Facilitates access to Samsung Knox services in Europe, including secure device management and enterprise deployment features for organizations using Samsung devices. 

https://eu-prod-klm-b2c.secb2b.com:443 Handles B2C (business-to-consumer) services related to Samsung Knox in Europe, providing access to consumer-facing applications and device management tools. 

https://eu-prod-klm.secb2b.com:443 Supports production-level services for Samsung Knox in Europe, delivering enterprise-level solutions for managing devices, configurations, and security within organizations. 

For Samsung Knox Enrollment (Allowed on the firewall) *.samsungknox.com:443
*.samsungknox.com:80Supports Samsung Knox Mobile Enrollment (KME) and Knox services. 

*.secb2b.com:443
*.secb2b.com:80Samsung Knox Secure Business-to-Business services for device management. 

https://eula.secb2b.com:80
https://eula.secb2b.com:443Hosts the End-User License Agreements (EULA) for Samsung Knox services. 

https://umc-cdn.secb2b.com:80
https://umc-cdn.secb2b.com:443Used for content delivery via the UMC (Unified Mobile Control) system for Samsung Knox, providing updates, configurations, and media to devices under management. 

https://dir-apis.samsungdm.com:443 Used to communicate with Samsung's device management (DM) system via secure API calls, enabling the configuration, management, and security of Samsung devices. 

https://account.samsung.com:443 Supports Samsung account management services, allowing users to manage their Samsung accounts, sync data, and access other services related to Samsung devices. 

https://us-kme.samsungknox.com Facilitates access to Samsung Knox Mobile Enrollment (KME) services in the U.S., which allows businesses to streamline the enrollment and provisioning of Samsung devices in enterprise environments. 

https://us-kme.api.samsungknox.com Provides the API interface for Knox Mobile Enrollment (KME) services in the U.S., enabling third-party integrations and automating device enrollment and management processes. 

https://us-kme.api.mssl.samsungknox.com Used for secure API access to Samsung Knox Mobile Enrollment services, ensuring smooth enrollment and configuration of Samsung devices in the U.S. 

https://us-kme-reseller.samsungknox.com Supports the reseller interface for Knox Mobile Enrollment in the U.S., allowing authorized resellers to manage device enrollments and configurations for customers. 

https://mdmdatabase.manageengine.com Centralized database for ManageEngine MDM, storing device details and configurations. 

To identify the domains which are not reachable by the MDM server, click here
- How do I verify whether the required domains are reachable by the MDM server?
The domains which the MDM server is unable to reach are specified within the product. To view the these domains, follow the given instructions
- On the MDM server, click on the Admin tab. Under Setting up MDMP, open Proxy Settings.
- After configuring the proxy server, you can access List of required domains under the MDM server section. Click on it to view the same.
- Only the domains, along with the corresponding vendor details which MDM has failed to reach will be listed here.
NOTE : Entering the domain URLs in the browser address bar does not provide the reachability of the same.
Ports such as 5223, 5228, 5229, and 5230 should be open if the mobile device connects to the internet through the corporate Wi-Fi. If the managed devices connect through the cellular data network, this requirement is not necessary (HTTPS port). - How do I access the MDM Cloud instance if the admin who created the account has left the organization?
If account credentials of the admin are available, log into MDM Cloud and follow the steps given here to transfer the admin privilege to a new user. If the credentials are not available, contact MDM Support at mdmcloud-support@manageengine.com with either of the following:
- If the user who has left the organization still has access to the account used for logging in to MDM Cloud, a consent e-mail must be sent to MDM Cloud Support from the mentioned e-mail
- If the user doesn't have access to the e-mail account, a copy of the users termination or resignation letter must be mailed to MDM Cloud Support
- How do I assign MDM admin privilege to a different user?
Admins can transfer admin privileges directly from the MDM server in case they are changing their jobs or if the organization has purchased only one technician license. Refer this document for the steps to tranfer the MDM admin role to a different user.
- Why am I unable to assign administrator privileges on MDM Cloud to one of my organization users who is an administrator in another Zoho application?
The user's account might be configured as part of a different organization or the person is using other Zoho services. This can be resolved by deleting the account from the Zoho application and inviting the user to the right organization.
- Sign in to the application used.
- Delete the organization and remove any user-created MDM account in another application.
- After the account is deleted, sign out of Zoho Accounts and close the browser window.
- Follow the instructions to invite the user to MDM and proceed with assigning administrative privileges.
Note: Deleting the organization removes all the Zoho services which have been configured with this account. Zoho services being utilized for personal use, also get deleted. If the user is unsure about the services being used with the Zoho account or if the organizations need to be merged into one, contact MDM Cloud Support (mdmcloud-support@manageengine.com).
- How to solve if TFA message or OAuth not working when logging into MDM console?
Please contact MDM Cloud Support (mdmcloud-support@manageengine.com).
- "Unable to send mail;authentication failed" error message shown while setting up Office 365 in Mail Server Settings.
- Ensure Username provided in authentication details has the permission to send on behalf of the Sender email address.
- Desktop Central needs SMTP Client Authentication to be enabled in Office 365 to successfully send mails and the same should be enabled in Office 365 Admin portal. Additional details and steps are given here.
- If the issue still persists after the above steps, kindly follow the steps given by Microsoft.
- I want to change the e-mail address with which I signed up on MDM Cloud. How to do that?
- Open this link and sign in with the Zoho account if need be.
- Specify the new e-mail address.
- A verification mail is sent to the new e-mail address.
- Once verified, MDM automatically updates the new e-mail address.
In case you need to make a secondary e-mail address as primary, click on the mail icon present against the mail address. This makes the selected e-mail address as primary.
In case you want to change the e-mail address of any technician, you follow the same process mentioned. - Why does my email app prompt for password even after configuring certificate based authentication using SCEP?
Ensure that the SCEP template reflects the same authentication values as configured in the Exchange server. Additionally, for the authentication to work, the client certificate must contain the user principal name(UPN) of the user in the certificate's subject or subject alternative name fields. Refer to this link for more details.
- How can I use Active Directory Certificate Services(ADCS) or any other Certificate Authority(CA) for client-based authentication?
If client-based authentication is enabled in your organization's AD, you can configure the SCEP policy to ensure one-time login for the applications and services that depend on AD, like VPN, Wi-Fi, etc.
- While accessing the MDM server through a web browser, why do I encounter the warning Your connection is not private? (ERR_CERT_AUTHORITY_INVALID)
MDM secures the communication between the managed devices and the server using SSL certificates. Importing third party SSL certificates signed by a valid Certificate Authority secures the communication by encrypting it. Upon importing valid certificates, the user need not manually trust them while accessing the MDM server. The user can hence, securely access the server without the warning message.
- How does MDM secure the communication between the MDM server and mobile devices?
All communication between MDM and mobile devices is encrypted using TLS 1.2 protocol and certificates issued by SHA 256, thereby ensuring data security.
- How can I sync directory services with MDM Cloud ?
Zoho Directory's sync tool can be used to sync directory services like Active Directory/Azure Directory with MDM, for features like self-enrollment, auto-user assignment, and others which involves the directory services.
- Why am I facing errors while integrating my Google Workspace(G Suite AD) with MDM?
Reason: This issue occurs when you have already integrated Google Workspace(G Suite AD) with MDM and you try to integrate it once again. This integration can either be with MDM on-prem or MDM cloud.
Solution:
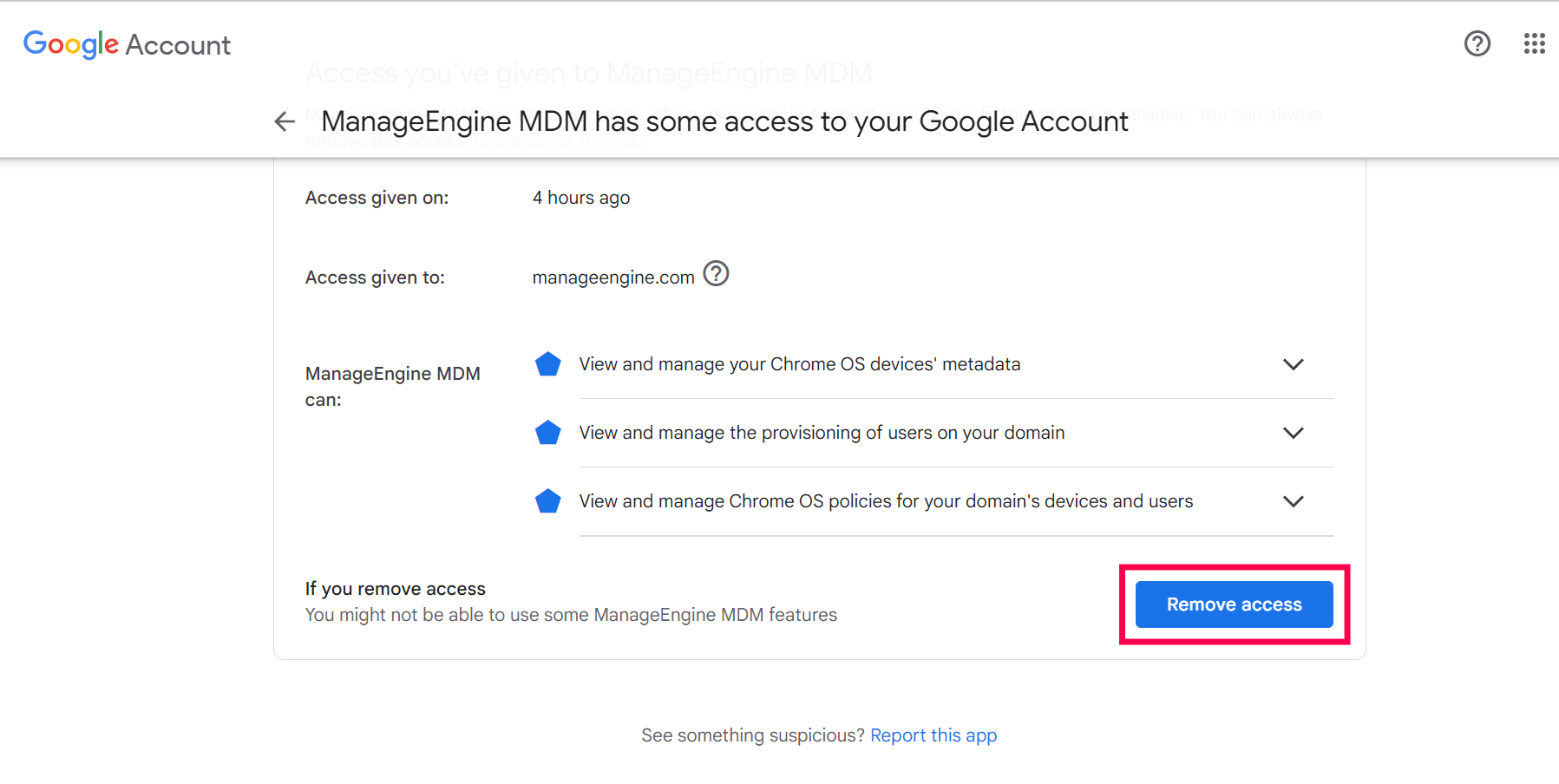
- You have to sign in into the account which is already integrated and remove the access. To do so,
- Go to this page and log in to the account.
- In case of MDM Cloud, Select Manageengine MDM and for On-Premise, select the app name which you have created on the Google Admin Console. Now click on Remove access.
- General
- What are the pre-requisites for Device Enrollment?
The prerequisites for enrolling a mobile device are:
- Creating APNs (applicable only for iOS)
- Configuring Proxy Settings (On-premises only)
- Configuring Mail Server settings (On-premises only)
- Setting up the user authentication type.
- The device that needs to be enrolled should be accessible through the internet in order to receive the email with enrollment settings.
- What are the pre-requisites for Self Enrollment?
End user should have the following for self enrolling a device.
- Connection to the Internet
- Self Enrollment URL
- Active Directory Authentication.
- What are the pre-requisites for enrolling a device in MDM Cloud?
- The URLs mdm.manageengine.com and transmail.net must be allowlisted for enrolling a device in MDM Cloud.
- If you're enrolling devices through invitation, ensure these two e-mail addresses: noreply@notifications.mobiledevicemanagerplus.com, noreply@zohoaccounts.com, and noreply-mdmcloud@manageengine.com must be allowlisted as well. If users don't have a Zoho account, they receive two mails. The former is used for sending join the organization mail(for creating Zoho account) and the latter is used for mailing the enrollment request. Modify the mail spam filter to ensure these mails don't fall into spam. If the user already has a Zoho account, only the enrollment request is sent.
- Create a Zoho account using e-mail and then follow the instructions provided in the enrollment request to enroll your device to MDM Cloud.
- Can I change the enrolment or management method from work profile to fully managed?
To transition a device from work profile mode to fully managed mode, the user must initiate the enrollment process from scratch. If the device was previously enrolled in work profile mode, a factory reset is necessary. Afterward, the user can enroll the device once again using the fully managed enrollment method.
- Where can I find the enrolled device in the console?
User can view or execute actions on the enrolled devices from the Devices section within the Enrollment Tab, as well as from the Inventory Tab and Management Tab.
- Can I apply kiosk mode or lock down the device to specific apps?
Yes, you can apply kiosk mode or lock down devices to selected apps for fully managed devices. You cannot apply Kiosk mode or block users from installing personal apps if the device is enrolled as a work profile.
To know more about kiosk mode, please refer to the Kiosk help page.
- Can I wipe the device?
Remote wiping of a device is feasible only on fully managed devices, while devices enrolled in work profiles can only have the work profile removed, meaning full data wipe is not possible on such devices.
- How can I assign managed devices from one user to another?
You can reassign managed devices by using the Re-assign User option in the MDM console. Navigate to: MDM > Enrollment > Devices tab.
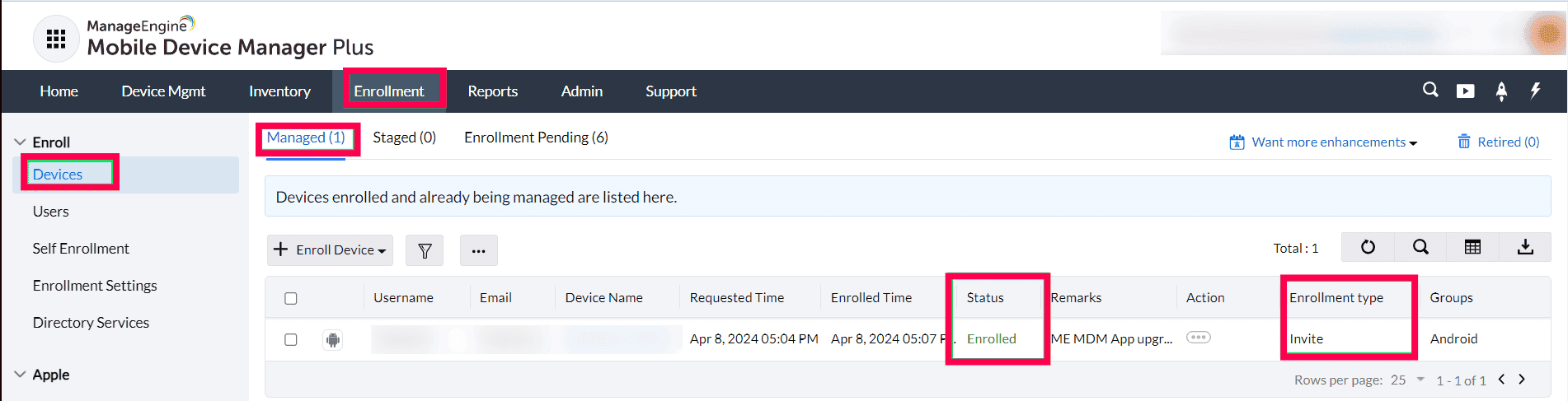
- How do I know if my device is a work profile or fully managed?
User can view the enrollment type of an enrolled device from the Devices section within the Enrollment Tab.
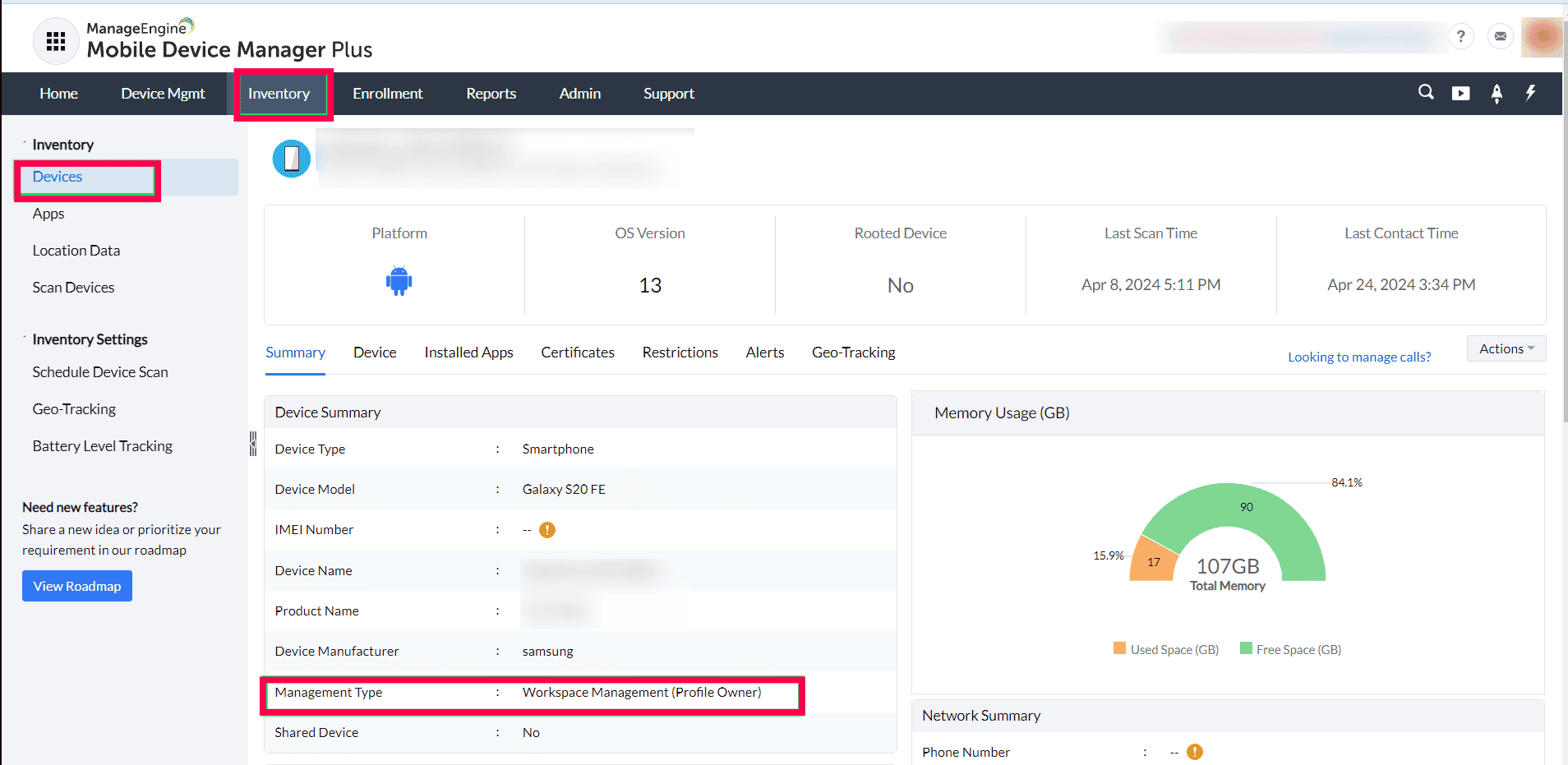
User can view the Management Method of an enrolled device by opening the Device details from the Devices section within the Inventory.
- Do I need to re-enroll my mobile devices after changing the Public IP address for NAT settings? (On-premises)
For Android devices, the process of registering a new FQDN/Public IP can be done by contacting support at mdm-support@manageengine.com.
For other platforms:
- These devices will continue using the old FQDN until re-enrolled. So, map both the old and new FQDN (or IP) in the DNS.
- Whenever SSL certificates are purchased or updated, ensure they include all FQDNs/IPs configured in the DNS.
Changing the private IP has no impact, as devices connect using the public IP or FQDN.
- Do the devices have to be factory reset to be enrolled and managed by MDM?
No, the devices need not be factory reset (unless specified otherwise) to be enrolled and managed by MDM.
- How much storage space does ME MDM app consume?
The app size will differ from device to device based on the platform type, but on average, the app size will be around 25-30 MB upon installation. However, the app size will increase based on the profiles/documents distributed to the device as these documents and profiles are stored in the app.
- How much network data and battery does ME MDM app consume?
ME MDM app consumes network data and battery only for downloading apps pushed to the device, with the data consumed depending on the size of the app. Other actions consume approximately 2 MB of network data monthly. Additionally, the consumption varies in case of geo-tracking based on the accuracy level specified.
- Why does my device IMEI contain 14 digits instead of 15 digits?
If the device is CDMA activated, then the IMEI contains only 14 digits and is referred as MEID. You can check the IMEI of your device by dialing *#06#.
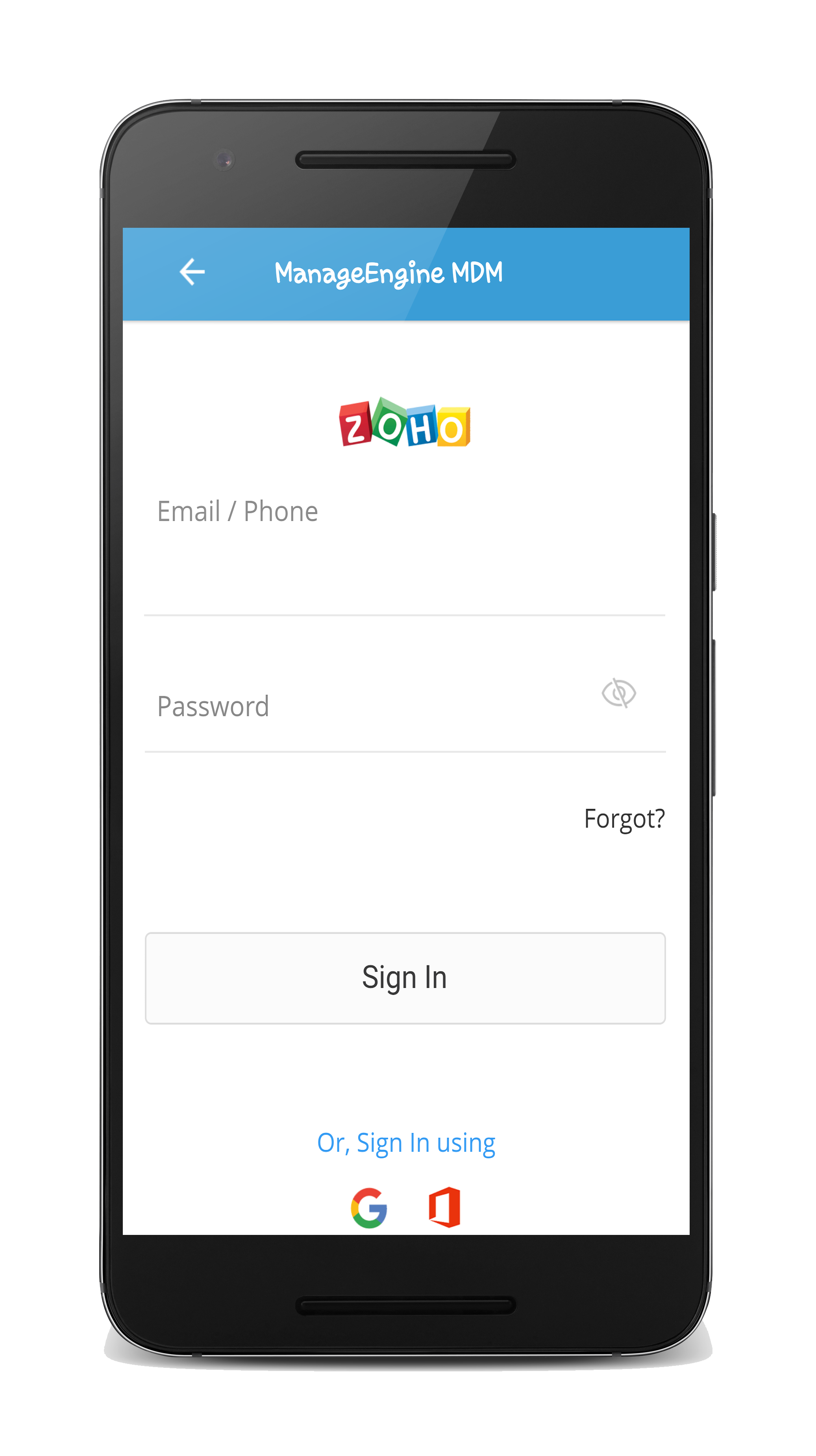
- Why am I unable to enroll devices through invite?
- Ensure OTP has not expired(It expires after 72 hours).
- Ensure you do not use OTP in place of Zoho account password or vice-versa. As seen below, in the first case, Zoho account is to specified and in the second, the OTP sent over mail, is to provided.
- I do not want to create a new account to be created for every device enrolled in MDM Cloud. Is there any other alternative type of enrollment?
To avoid using invites, you can prefer Self Enrollment, where the users enroll the devices themselves and Admin enrollment. Admin enrollment as the name suggests, is a type of enrollment where the enrollment process is carried out by the Admin. The other advantage with Admin enrollment, is that the process is automated, requiring minimum user intervention and/or admin action. MDM supports the following types of Admin enrollment for Android:
- Knox Enrollment(Only for Samsung devices)
- NFC enrollment
- Android for Work-based enrollment
The following types of Admin enrollment is supported in iOS:
- Why have the users not received the join organization mail yet, despite having sent an enrollment request?
- Ensure all the pre-requisites listed here have been configured.
- The mail could have fallen into the Spam/Junk folder. Verify the same and if yes, change the e-mail spam/junk filter criteria.
- Verify your anti-virus configuration to ensure it has not blocked the enrollment requests from being sent.
- Verify POP/IMAP configuration setup in the router web interface, if configured. Ensure it is not blocking the enrollment requests from being sent.
Verify if Restricted Sign-in is disabled on the OneAuth app present on users' devices, even if you have not enabled two-factor authentication. If the issue is not still persists, contact MDM Cloud Support (mdmcloud-support@manageengine.com).
- One of my organization users signed up with MDM Cloud, instead of enrolling the device. How to have the device enrolled?
- Open this link and sign in with the Zoho account, if need be.
- Click on Delete Organization present under Dashboard
- Click on Delete to remove the user-created MDM account. Note that, this also removes all the Zoho services which has been configured with this account. If the user is utilizing Zoho services for personal use, this also gets deleted. If the user is unsure about the services being used with the Zoho account, contact support(mdmcloud-support@manageengine.com)
- After the account is deleted, sign out of Zoho Accounts and close the browser window.
- Follow the instructions specified in the enrollment mail, to proceed with the enrollment.
- What are the pre-requisites for adding users or enrolling devices?
In case multiple teams(referred henceforth as org) in your enterprise use any Zoho service, follow the instructions specific to your scenario.
- If the user doesn't have an existing MDM account, the user can access the link in the invitation to join the org.
- If the user is already a part of another org, the user must ask the super admin of this org to remove the user. The user can then access the link in the invitation to join the org.
- If the user is the super admin in the other org, the user must assign another user as super admin. The new super admin must remove the user. Now, the user can access the link in the invitation to join the org.
- If the user is the only active user in the other org, the user must delete the org account as explained here. Now, the user can access the link in the invitation to join the org.
- Why do I get a page titled "Welcome to Device Enrollment", when I try to access MDM Cloud or try enrolling a device?
If this page is displayed when trying to enroll a device, ensure your accessing the appropriate enrollment URL from the device to be enrolled.
If this page is displayed when trying to access MDM Cloud, ensure your MDM Cloud admin has added you as a user. - How can we modify the username and email address of enrolled devices?
Mobile Device Manager Plus allows the admins to modify the username and email address associated with enrolled devices without having to re-enroll the devices. To modify the associated credentials follow the steps given below:
- Navigate to Enrollment and find the device whose user details has to be modified
- Under Actions select the Re-assign user option
- Enter the new user name and email address and Save.
Modifying the user details will reassign the account based profiles to the new email address.
- What are the best practices that need to be followed before handing out a device to a new user?
If you are re-issuing managed devices to new users, you may want to erase all content while keeping the associated apps and profiles intact. To re-issue a managed device, it is recommended to deprovision the device which will wipe the device data and thus remove all the apps and policies associated with the device. After deprovisioning, you have to re-enroll the device before issuing them to employees to ensure that the device is pre-configured with all the requisite apps and policies.
You can make use of admin enrollment methods like Apple Business Manager (ABM) for iOS devices, Zero Touch Enrollment for Android devices or Knox Mobile Enrollment for Knox supported Samsung devices to enroll devices remotely. These methods ensure that the device gets automatically enrolled and the profiles and apps are distributed as soon as the users are assigned to the devices.
- How can I simplify device onboarding if I'm an existing Zoho customer?
If you are an existing Zoho customer, you can sign up for MDM Cloud using your organization's Zoho account. To enroll the devices, follow the steps given below.
For Andorid devices, the users can download ME MDM app from Play store.
- Once the installation is complete, open the app and click on the Cloud tab.
- Specify the Zoho account log in credentials and Owned by details
- Accept the Terms and Conditions by clicking Continue.
- Enable Device Administrator and click Activate to complete enrollment.
For iOS devices, you need to enable Self enrollment and enroll using Zoho account credentials.
You can also enable Conditional Access for Zoho Mail using MDM as explained in this document.
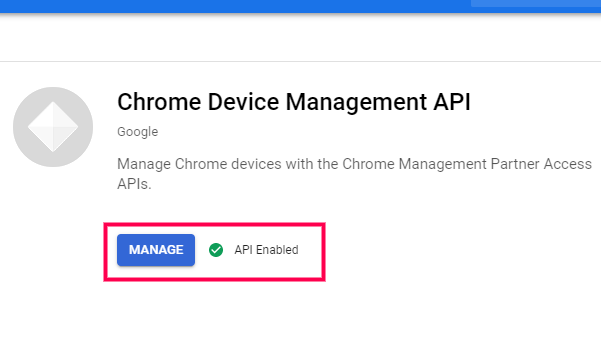
- How to enable Chrome Device Management API in the Google Admin console?
Follow the below mentioned steps to enable Chrome Device Management API
- To enable Chrome Device Management API, login to Google Cloud Console using your admin account.
- Go to API & Services > Library .
- In the search bar, type Chrome Device Management API to check if it is enabled.
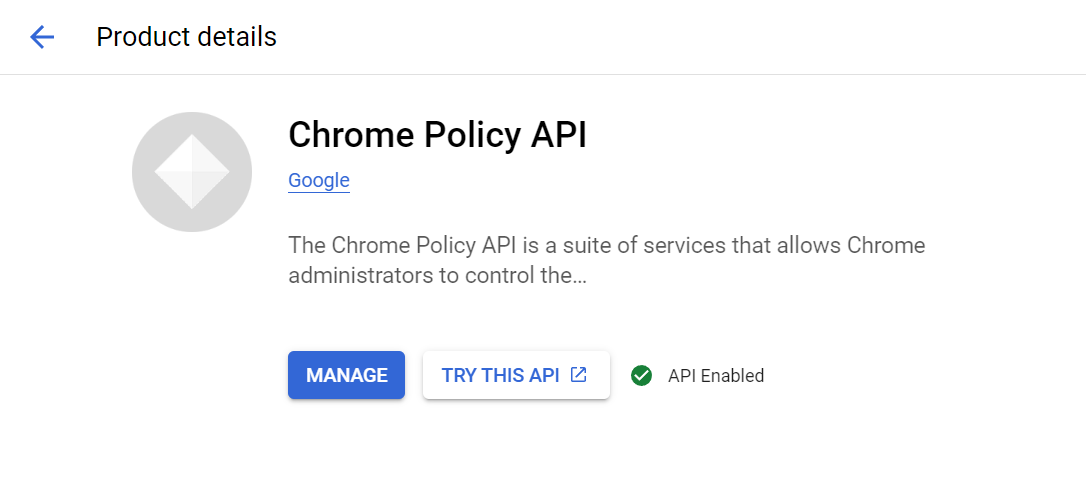
- How to enable Chrome Policy API in the Google Admin console?
To enable Chrome Policy API, login to Google Admin Console using your admin account.
- Go to API & Services > Library.
- In the search bar, type Chrome Policy API.
- Click on Enable.
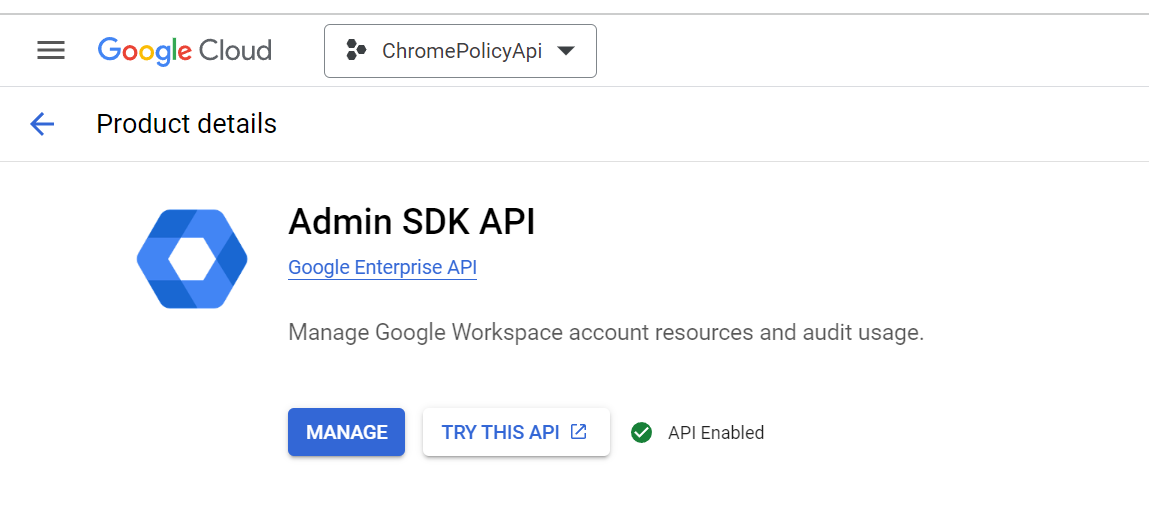
- How to enable Admin SDK API in the Google Admin console?
To enable Admin SDK API, login to Google Admin Console using your admin account.
- Go to API & Services > Library.
- In the search bar, type Admin SDK API.
- Click on Enable.
- Can I remove multiple devices in bulk from the Staged tab?
Yes, you can remove multiple devices in bulk from the Staged tab by applying filters to identify the relevant devices. However, bulk removal using a CSV file is not supported.
Steps to Remove Devices in Bulk:
- Navigate to the Staged tab.
- Apply the required filter criteria to list relevant devices.
- Select all filtered devices at once.
- Click on the three dots (⋮) menu in the top-right corner.
- Select "Remove" to delete the selected devices.
- During enrollment, why does the MDM Profile state Not Verified though it is signed by ManageEngine?
When the third party SSL (Secure Sockets Layer) certificates are not imported to the server, the communication between the MDM server and the ME MDM app is not secure. To establish a secure connection, the user has to manually trust the certificates during MDM profile installation. To automate this, SSL certificates signed by a valid Certificate Authority is to be imported to the MDM server. This will verify the MDM Profile installation during enrollment.
NOTE: The error Not Verified does not alter any of the functionalities offered by Mobile Device Manager Plus.
- Can I remove multiple devices in bulk from the Staged tab?
Yes, you can remove multiple devices in bulk from the Staged tab by applying filters to identify the relevant devices. However, bulk removal using a CSV file is not supported.
Steps to Remove Devices in Bulk:
- Navigate to the Staged tab.
- Apply the required filter criteria to list relevant devices.
- Select all filtered devices at once.
- Click on the three dots (⋮) menu in the top-right corner.
- Select "Remove" to delete the selected devices.
- Apple Enrollment
- Why should I renew APNs a month prior its expiry?
If the APNs certificate has expired, Apple Push Notification service will not be able to contact the managed mobile devices. Renewing an APNs after expiry is the same as creating new APNs, which means all the devices need to be enrolled again to be managed. Assume that the APNs expires on 30th of June, you need to ensure that you renew your APNs well before the expiry date and update it in the Mobile Device Manager Plus server. All the managed mobile devices should contact Mobile Device Manager Plus server at least once before 30th of June. If any of the managed mobile device fails to contact the Mobile Device Manager Plus server, then those devices should be enrolled again. Hence we recommend renewing APNs before a month of its expiry.
- Why is the renewed APNs certificate unavailable in the devices?
Devices receive the APNs certificate once they come in contact with the MDM server. There can be a slight delay in the process but that does not affect the communication between the server and the devices. Password-protected devices need to be unlocked in order to contact the server.
- Should the devices be re-enrolled if the APNs is renewed after expiry?
The devices need not be re-enrolled. Renewing the APNs certificate is sufficient. It is recommended that the certificate be renewed at the earliest.
- Do I need a D-U-N-S Number for ABM account creation?
No. A D-U-N-S Number is not required at account creation. You have 60 days to verify it, or your ABM account and data may be deleted. Government agencies do not need a D-U-N-S Number Apple verifies them directly. Once verified, the number appears under Settings > Organization Information; until then, you will see a “Verify your business” prompt.
- Do I need an Apple Enterprise/Developer account to manage iOS devices?
No, you do not require an Apple Developer Account to manage the iOS devices using Mobile Device Manager Plus.
- Can I enroll an Apple Watch using ME MDM?
No, as of now ME MDM does not support enrolling Apple Watch.
- I do not have a domain, how do I add ME MDM App to my tablets without using a Domain or Domain e-mail or without connecting to Play Store?
You can use local authentication and specify a user name and email address. If you want to enroll corporate devices, then you can use Admin Enrollment options such as NFC and QR code for Android devices, ABM and Apple Configurator for iOS and Windows ICD for Windows.
- What are the prerequisites that need to be met before using Apple Configurator to enroll iOS devices?
Ensure the following before enrolling devices using Apple Configurator:
- If the devices to be enrolled are bought from authorised reseller and ABM is available in your country, it is recommended to use ABM for enrolling these devices.
- If the devices to be enrolled were already in use, check if Activation Lock is disabled by going to Settings -> iCloud and turning off Find my iPhone.
- Can devices not purchased from authorised resellers be enrolled using Apple Enrollment Program?
iOS 11 and above devices can be enrolled into ABM using Apple configurator, even if they aren't purchased directly from Apple or authorised resellers. Follow the steps given in this document to enroll these devices.
- Why do I get an unexpected error when I try enrolling iPads using Apple Configurator?
This error is usually encountered when you have enrolled iPhones previously using Apple Configurator. In case of iPhones, Apple Configurator fetches the IMEI and thus, in case of iPads it tries to fetch the IMEI(which is not available for iPads) and shows an error. In such cases, you can factory reset the device using Apple Configurator and retry the process.
- What are the benefits of enrolling iOS/Apple devices using Apple Business Manager (ABM) instead of using Apple Configurator, Self Enrollment, or Invites?
By enrolling devices using ABM, you can leverage additional features such as,
- Out-of-the-box enrollment
- Mandatory device management - Enrollment cannot be revoked even on device reset
- One-time setup
- Automatic user assignment
- Supervision (Also available in Apple Configurator)
Click here to learn more about Apple Business Manager. To use ABM for device enrollment, it must be available in your country. Click here to find the list of countries where ABM is supported. To make effective use of MDM, it is recommended to enroll corporate owned devices using ABM or Apple Configurator and employee owned devices using Invites or Self Enrollment.
- What will happen if we move an ABM token from one server to another or if the same ABM token is used in two different MDM servers?
When an ABM token is removed from a server, the licenses used to distribute the apps will be reverted to your account. When you use this token on another server, the licenses can be used to distribute the apps to the devices.
It is not possible to use the same ABM token on multiple MDM server, as each MDM server manages the complete set of licenses purchased with the token. This results in the MDM server revoking the licenses of the apps distributed to devices and also removes the apps from the devices.
- Android enrollment
- Why do enterprises need an Android management software?
Enterprises need Android device management software for several reasons. And Android device management tool or solution can:
- Enhance device security by enforcing Android device management policies and protocols, thereby protecting against data breaches and unauthorized access.
- Streamline device configuration for the IT team, making it easier to set up and deploy Android devices across the organization.
- Simplify application management, allowing centralized control over app deployment and updates.
- Enable remote monitoring and support, reducing downtime and improving productivity.
Overall, Android device management software ensures efficient and secure management of Android devices in the enterprise environment.
- what are the benefits of using Android MDM Software?
Android MDM software offers a range of benefits to enterprises seeking efficient and secure management of their Android device fleet. By leveraging this software, organizations can enjoy the following advantages:
- Enhanced Android device security
- Centralized management of various device types from different OEMs (original equipment manufacturer)
- Streamlined enterprise-developed and store app deployment
- Adherence to organization and industry standards
- Remote troubleshooting and supporty
- Geolocation and tracking
- Customizable policies
- Efficient asset management
- Differentiate between Work Profile enrollment & Full Device Management.
Mobile Device Manager Plus (MDM) provides a range of features to manage your organization's Android devices. Visit our help page to learn more about the extensive list of features supported by MDM and their compatibility based on device and provisioning type.
- What is an MDM app, and what are its benefits?
The ManageEngine MDM app is the companion app installed on a device during enrollment to ManageEngine Mobile Device Manager Plus. It serves as the agent app, facilitating the agent-server communication necessary for ongoing device management. Visit our help page to learn more about Mobile Device Management app.
- How i can automate the enrollment of the android device?
- Zero Touch or Knox Enrollment:You have the option to configure either Zero-touch Enrollment or KNOX Enrollment (available only for Samsung Knox Supported devices) for corporate-owned Android devices. These methods ensure that Android devices automatically enroll when they connect to Wi-Fi after a factory reset.
- For BYOD Device: You can send bulk email invite enrollment and end users can enroll using the email invite.
- Why doesn't my Android device support Android for Work despite running on Android 5.0 or later versions?
For a device to utilize Android for Work(AfW)-based features and configurations, the OEMs(Original Equipment Manufacturers) must provide support for the same on the devices. If AfW support is not provided for a specific device model by the OEMs, they cannot support Android for Work and hence, features requiring the device to be provisioned as Profile Owner/Device Owner cannot be pushed to the device. Some of the devices supporting Android for Work are listed in these links - link #1, link #2 and link #3.
- Google Play Services is not supported in my country/device. How can I manage my Android devices?
In this case, on the MDM console, navigate to Enrollment->ME MDM app (under Android) and set Communication Type to Periodic. Click on Save Changes. You can then enroll devices using EMM Token Enrollment, ADB enrollment, or NFC enrollment methods.
- Why does my Android device show the error "Device already provisioned", when trying to enroll a device using NFC enrollment?Android devices running 5.0 or above, enable an implicit Activation Lock by default on associating a Google account with the device. When the device is corporate/complete wiped, the device retains the Google account details and the Activation Lock is still enabled. So on trying to enroll this device after wiping using NFC enrollment, the error "Device already provisioned" is displayed, as the device is already associated with a Google account. The implicit Activation Lock can be disabled only by providing the Google Account details, associated with the device previously.
- How to verify the whether a work profile has been installed in the managed Android device?
Work profiles are installed when Android devices are provisioned as Profile Owner using Android for Work. To verify whether Work profile has been installed in the device, go to Settings, and select Accounts. Work profile is listed under the Work section.
- How to uninstall a work profile from the managed Android device?
In Android devices running 5.0 or later versions, go to Settings, click on Accounts and select Remove work profile. Click on Delete to confirm the removal of all apps and data within the work profile.
- General
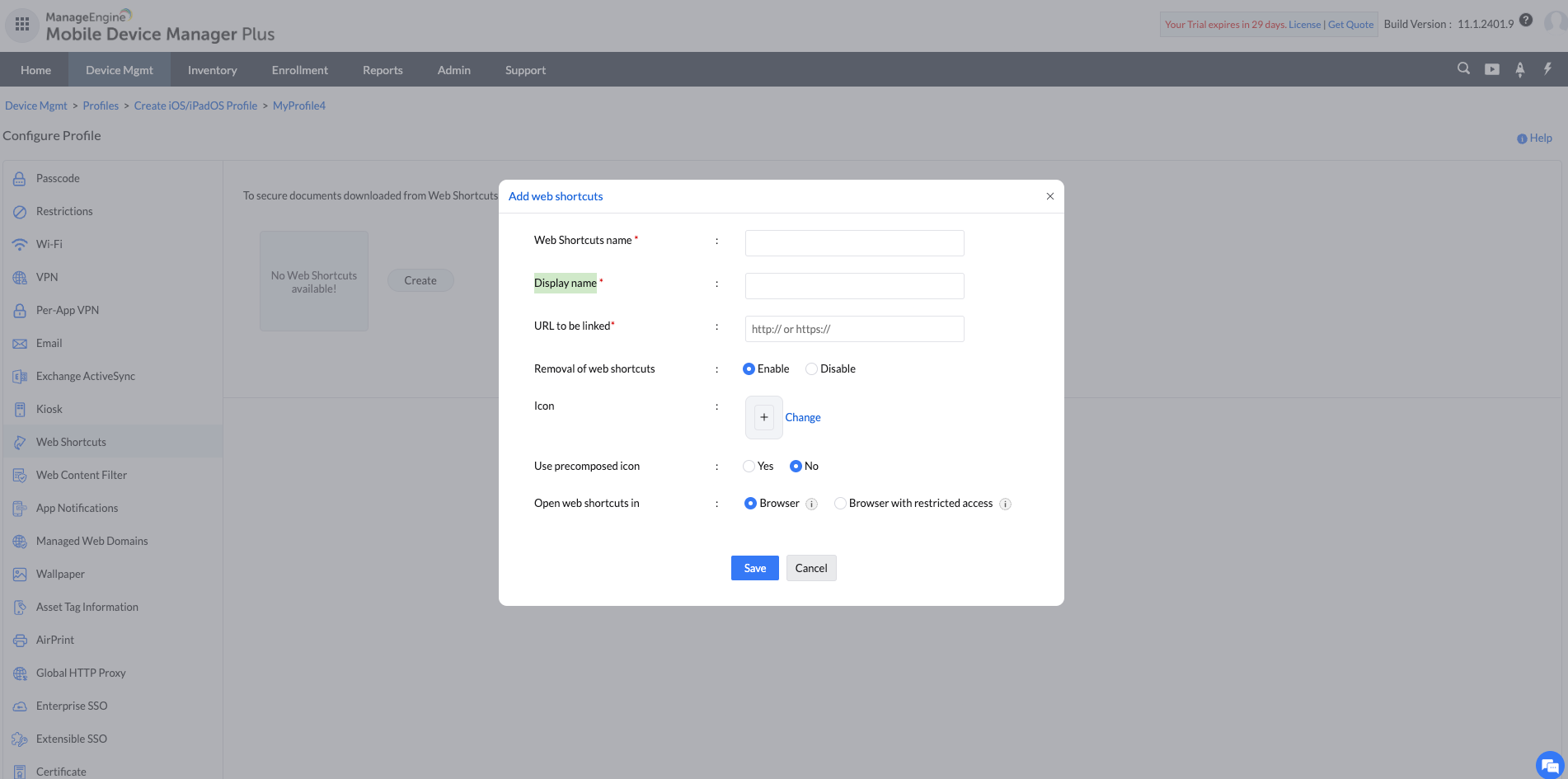
- How to delete a Web Shortcut in profiles?
We can delete an existing Web Shortcut by clicking on the delete icon beside the name. Deleting a Web Shortcut will re-publish the profiles to the device without the Web Shortcut.
- Can a passcode policy forced on the mobile device be revoked by the user?
No, passcode policy that is forced on the mobile device cannot be revoked by the user. Though users can disable passcode settings on their device, users will be forced to set passcode when the device is unlocked. However if MDM profile is removed from the device the device can no longer be managed by Mobile Device Manager Plus.
- What do you mean by imposed policies?
Policies and Restrictions which are applied successfully to the managed mobile device are called imposed policies.
- What is meant by violated policies?
Administrator instructs the users to accept the Policies and Restrictions which are pushed to the device. When the user over rules the policies and restrictions, then those policies and restrictions are called as violated policies.
- What will happen if my device has violated policies?
When a user overrides the policies and restrictions pushed by the administrator, these policies will be marked as violated policies and will be listed under Violated Policies tab in ME MDM app. The consequence of violated policies differ based on the policy that is violated
- Passcode: If passcode policy is violated in Device Owner devices, the device will be disabled until the user sets a compliant passcode. In Profile Owner devices, the apps inside the work profile will be disabled until the user sets a compliant passcode. The apps present outside the container or personal apps will remain functional.
- Add managed account: Managed Account has to be added on the devices for deploying apps using MDM. Managed Account addition might fail when the Play Store or Play Service is not updated. Once the Play Store or Play Service is updated, follow the on-screen instruction to add Managed Account to the device.
- Location or NFC always on: In Profile Owner devices if Location/NFC is enabled as Always On under Restrictions policy and the user turns it off, the policy will be marked as violated. The user will be prompted to turn on Location/NFC and the policy will remain violated until the user turns on Location/NFC.
- What is the difference between Idle Timeout before lock and Grace Period for device lock?
Idle timeout before device lock specifies the time allowed for the device before the screen turns off. This is similar to the settings that can be configured in the device (Settings > General > Auto Lock). Grace period for device lock refers to the time allowed for the user before prompting for a passcode. The screen of the device turns off and when the user slides the arrow to unlock the screen he would be prompted to enter his passcode. This is similar to the settings that can be configured in the device (Settings > General > Passcode Lock).
- How to prevent users from accessing the Settings on the devices?
In case of iOS devices, the settings can be restricted by disabling the individual settings under Restriction in Profiles. For Android devices, the Settings app can be disabled by disabling the option "Modify default device settings" under Restrictions in Profiles.
In addition to these methods, user can be prevented from changing any settings by running the device in Single App Kiosk Mode.
- Can MDM be used to pre-configure essential settings such as Wi-Fi and E-mail over-the-air without any user intervention?
Yes, you can configure E-mail, Wi-Fi and other essential settings (such as VPN, Exchange etc.,) across platforms on MDM server and then associate it to groups. Devices added to this group on enrollment, are automatically distributed the configured policies and thus, getting pre-configured on device. Know more about all the policies supported by iOS, Android and Windows in MDM.
- How to automatically Blocklist websites with inappropriate content?
Admins can automatically Blocklist inappropriate or malicious content by enabling the checkbox Automatic restriction of malicious content or Automatically restrict inappropriate content under Web Content Filtering for Android and iOS device profiles respectively.
- Is it possible to apply profiles created for one platform to devices running on another platform?
No, the profiles deal with specific device functionalities and are platform dependent. Therefore they cannot be applied to different platforms.
- I want to apply different policies as different profiles. Is it possible to apply multiple profiles to devices?
Yes, multiple profiles can be applied to devices. We recommend applying all account based policies as one profile and the restrictions as separate profile, as every time a modified version of the profile containing all these policies is re-distributed, the passcode for the account-based services such as Exchange and configurations such as Wi-Fi preferences, previously synced mails etc., specified in the account-related policies is reset and has to be manually entered by the user again.
- What will happen if I apply profiles with contradictory restrictions to devices?
For iOS devices, the most secure profile will be associated. Whereas in the case of Android devices, the most recently applied profile will be applied. For instance, if you distribute profile A with camera disabled and profile B with camera enabled, profile B will be applied on Android devices since that is the most recent. While in Apple, profile A will be associated since that is the most secure.
- Is it possible to restrict users from adding VPN configuration from third party VPN apps?
Restrict users from installing third party VPN apps as users can bypass the VPN restriction. You can blocklist VPN apps by navigating to Inventory -> Apps (Choose the VPN apps to be blocklisted) -> Blocklist.
- Troubleshooting tip for successful migration of the device from one server to another.
One should always choose the device to be activated by the "Admin" to ensure a successful migration procedure of the device from one server to another.
- What happens if the default messaging or calling app is blocklisted or uninstalled?.
If the default messaging or calling app is blocklisted, calling and messaging stop working; if uninstalled, it reverts to the original default app.
- What to do when iCloud sign out is greyed out?
The iCloud sign out will be greyed out on the device if Screen Time is enabled on the device. In that case, turn off the screen time from device settings to enable iCloud sign out.
- How can we ensure that the user does not install/uninstall apps from managed devices?
We can prevent the installation and uninstallation of apps from devices by applying a few restrictions to devices.
- Under Device Mgmt, select Profiles.
- Choose the OS of the device to which the profile is to be applied.
- Under Restrictions, click on Applications.
- Restrict the options, Install Apps and Uninstall Apps.
- Publish and distribute the profile to devices.
- Do I distribute Email/Exchange/VPN configurations through profiles or apps?
Email, Exchange, and VPN can be configured through MDM by applying profiles, or by distributing the required apps. Profiles with the required configurations can be pushed to the devices, and using dynamic variables, user details will be mapped to the respective devices. However, the required apps for Email, Exchange, and VPN can be provided with app configurations, and distributed to the devices. This ensures that if an app gets a new feature, the user will be able to avail it. Refer this link for more details on app configurations.
- How can I deprovision a managed device when it has lost contact with the MDM server?
Press the back button or tap on top of the home screen four times and enter the Revoke Administration Password in the space provided to remove ME MDM app when prompted, thus temporarily revoking management. If the device is in Kiosk, the password needs to be entered twice, i.e., once to exit Kiosk and again to revoke management from the device.
- Apple
- What is the behavior of Restriction policy in iOS devices?
Mobile Device Manager Plus assures high security through restriction policies. Whenever more than one policy is applied for a same cause, whichever policy provides more security will get applied automatically. For example, assume two restriction policies are assigned to a device, where one is applied to authenticate the usage of camera and the other is to restrict the usage of camera, the policy which assures high security will get applied automatically. So the usage of camera will be restricted in the device.
- Can OS updates be restricted on managed iOS devices?
No, Apple doesn't permit MDM solutions to restrict OS updates. However, MDM provides a workaround to prevent OS updates as explained here.
- Can the user be restricted from changing the date and time settings on iOS devices?
Restricting users from changing the date and time settings on devices is not permitted by Apple. Mobile Device Manager Plus can restrict the user from accessing any settings by running the device in Kiosk Mode where the device has access only to one app. Another method that can be used is, by ensuring the required apps are dependent only on the network date and time and not the device date and time.
- Can we use Mobile Device Manager Plus to distribute contacts to iOS devices?
You can make use of the CardDAV profile to distribute contacts to the managed devices. Here you can make use of Google contacts or any other third party service that supports CardDAV.
- Can we prevent users from adding iCloud accounts to managed devices?
You can restrict users from modifying accounts on the devices by navigating Device Management -> Profiles -> Restrictions -> Advanced Security and restricting the Modify Account Settings option.
The user will not be able to modify accounts like mail accounts, iCloud and iMessage settings. If you want to completely restrict iCloud, then navigate to Profiles -> iCloud and restrict it. This will completed restrict the apps from syncing with iCloud and also the device backup on iCloud.
- Can MDM prevent Wi-fi sharing on Apple devices?
With iOS 11, Apple released a feature that allowed users to share the wi-fi credentials to new devices by bringing two devices running iOS 11 close to each other. Though this feature is useful and allows easy access to personal wi-fi, it can cause problems in corporate scenarios. That is why Apple ensured that any wi-fi distributed through a mobile device management solution cannot be shared to others using wi-fi sharing. Therefore, any wi-fi preconfigured using Mobile Device Manager Plus cannot be shared to other users using wi-fi sharing feature.
- On restricting Add/modify iCloud, Mail and other accounts for iOS devices, I am facing password related issues with Email and Exchange ActiveSync policies, configured via MDM. How do I solve this?
Case 1:
- The admin configures an Email based profile, and another profile which restricts Add/modify iCloud, Mail, and other accounts, using MDM. On associating these profiles, the user is prompted to provide the email password during the initial setup. If the user closes this prompt before providing the password, it cannot be configured, unless the Email profile is associated again with the device.
- If the restriction is enabled without OAuth, and Multi Factor Authentication is used, an app specific password needs to be set by the user.
- Before iOS 16: If OAuth is enabled on the devices, the prompt to enter the Exchange password will not be displayed on the device, and it cannot be configured unless the Add/modify iCloud, Mail, and other accounts restriction is disabled.
- After iOS 16: You can perform OAuth even if the restriction of Add/modify iCloud, Mail, and other accounts is enabled.
Case 2:
- Similarly, if both the Email and Exchange profiles are associated with an iOS device, the mail account is successfully configured during the initial setup. When the password expires, the device does not prompt/allow the user to change it. The workaround is to re-associate the Email profile to the device, since Apple has not provided any solution for this.
- What to do if the admin or user forgets the passcode for iOS devices?
If the admin forgets or does not know the passcode, the only solution is to clear the passcode in the MDM server. If wrong passcodes are entered multiple times, the device will be disabled. After the device is disabled or locked by Apple if the device is switched off or restarted, the device will lose connection with the MDM server and the remote commands such as remove passcode issued from MDM server will not be executed on the device.
- How can you override Guided Access on iPhone/iPad?
Guided Access can be overruled using the following methods:
- Single App Mode profile:
By associating a Single App Mode - Kiosk profile with the device, Guided Access can be overruled. Once this is done, disassociating the profile will return the device to it's original state. - Lost Mode:
Activating lost mode on the device also removes Guided Access. Once Lost Mode is de-activated, the device will be back to normal.
Note : The above mentioned steps are only possible for supervised devices. To manually remove Guided Access, force restarting the iPhone/iPadwill bring the device back to normal. - Single App Mode profile:
- Android
- Why can't I backup and restore data on my Android devices?
Android has restricted backup and restore data functionality in devices provisioned as Device Owner by default. In case of Samsung devices provisioned as Device Owner, backup through Samsung Cloud and Smart Switch backup features is restricted by default and can not be enabled.
- How to enable Notification Badges in the MDM launcher for Android devices in Kiosk mode?
To display notification badges on Android devices running in Kiosk mode, follow these steps:
- Navigate to Device Mgmt > Profiles > Create a new Android profile.
Note: For existing kiosk profile , select the profile and click on modify. - Under Kiosk > General settings > Multi-app mode.
- Select 'Yes' for Show Notification Badge.
- Click save and publish the profile.
- Now distribute this profile to the required groups/devices.
- Navigate to Device Mgmt > Profiles > Create a new Android profile.
- How can the phone call app be added to Android devices in kiosk mode?
Users can be allowed to make phone calls and access contacts from Android devices in kiosk mode by adding the respective apps to the kiosk profile. Samsung and other Android devices make use of different package names for this app and hence it is recommended to search for the apps using the following bundle identifiers.
- Samsung : com.samsung.android.contacts
- Core Android : com.android.contacts and com.google.android.dialer
- General
- I need to manage devices in an internal network. How do I configure the MDM server to manage these devices?
For policies and restrictions to be applied to the devices immediately, the devices have to be connected to the Internet. For Android and Windows devices, by default the MDM server communicates to the devices through FCM and WNS. This can be changed under Enrollment > ME MDM app> Configure mode of communication > Periodic. However, to manage iOS devices, the devices must have Internet connectivity.
- What is the difference between App Store Apps and Enterprise/In-house Apps?
App Store apps are those which are available in the App Store. They can be either paid App or free app. Enterprise apps, also called as In-House apps are specially developed and designed for every Enterprise. This is unique and completely owned and distributed by the Enterprise itself.
- What is Volume Purchase Program (VPP)?
Volume Purchase Program(VPP) is used for purchasing app licenses in bulk and distributing the same to user either through managed distribution or redemption codes. Know more about Volume Purchase Program here.
- What will happen if I distribute an iOS app to Android and Windows devices?
Mobile Device Manager Plus app distribution is designed in such a way that you can only distribute iOS apps to iOS devices, Android apps to Android devices and Windows apps to Windows devices.
- What are the prerequisites for Windows Phone Enterprise App Distribution?
For mobile devices running Windows 8 and 8.1, the steps to perform App distribution:
- You have to register a company account on Windows Phone Dev Center and obtain an enterprise certificate from Symantec
- You should generate an application enrollment token (AET)
- Upload the generated AET file into the server (MDM -> App repository -> Windows app settings -> App distirbution certificate -> Configure)
- Before adding enterprise apps in app repository, you have to sign the app using AET. For more details visit help.
- What is AET? What is its purpose?
AET refers to Application Enrollment Token. The Windows Phone 8 operating system requires users to enroll each device with the enterprise before users can install company applications on their devices. Only way to achieve this is using Application Enrollment Token, which enables you to distribute enterprise applications on a Windows Phone 8 device. For more information visit help.
- What is the behaviour of app permissions when a device is put into Kiosk Mode?
Once a device is put into Single App Mode, no permission prompt will be generated. This means that the app cannot access any other features that use camera, contacts, or location services. The admin should allow these settings before putting the device into Single App kiosk.
- What are the prerequisites to distribute enterprise apps using Mobile Device Manager Plus?
Follow one of the given methods to distribute enterprise apps using Mobile Device Manager Plus:
- Enterprise Distribution: If you have a development team which is familiar with developing apps, you can choose this method. Ensure the setting "Save for Enterprise Distribution" is enabled, while the app is being developed.
- B2B App Distribution: If you do not have the resources to develop the app in-house, you can make use of B2B app distribution. Follow the steps given here for B2B apps.
- Can I remove user installed apps using MDM?
Yes, you can remove apps present on the devices, by blocklisting them as explained here.
- Can the same app be installed both within and outside the container?
Yes. An app that is dis tributed by the admin using Mobile Device Manager Plus will be available in the container. An app that is installed by the user will be available outside the container. For example, you can have a Gmail app inside the container for corporate Email account and outside the container for personal Email account.
- Unable to upload Enterprise app while uploading AAB files.
Currently we support only APK files. Kindly follow the right syntax while uploading XML files to avoid errors while uploading Enterprise apps.
- Can I manage app bundles using MDM?
App Bundle is a publishing format that lets developers deliver customizable features with smaller app size. Since MDM does not support distributing App Bundles, host the App Bundle privately to distribute using MDM.
- Can I Download an APK from the App Repository?
No, you cannot download an APK from the App Repository in ManageEngine Mobile Device Manager Plus (MDMP). The App Repository is designed for storing, managing, and distributing apps to devices, but it does not provide an option to download the APK file directly.
Alternative Ways to Get the APK
- From the Original Source: If it's a store app, download it from the Google Play Store or the app developer’s website.
- From Your Uploads: If you uploaded a custom enterprise app (APK) to the repository, you should retrieve it from your local storage where it was originally uploaded.
- Apple
- How to disable App Store on the managed devices, without affecting the installation of apps distributed via MDM?
You can restrict App Store on managed devices, by creating a profile and navigating to Restrictions -> Applications and restricting Users can install apps from App Store. This ensures only apps distributed through MDM can be installed on the device(must be running iOS 9.0 or later versions). If this is restricted for devices running other OS versions, even MDM-distributed apps cannot be installed on the device.
- Can we install App Store apps without entering Apple ID?
App Store apps can be installed without entering Apple ID, as explained here.
- Can you revoke the license code after installing the App?
Yes, with the help of iOS app license management feature in ABM, Mobile Device Manager Plus will let you to revoke and reassign app licenses to the required user device.
- Should the user have to use the Apple ID password while installing the Apps from App Catalog?
Yes, the user has to enter the Apple ID to install the apps. To install apps silently or without requiring Apple ID, refer to this.
- Can I use Mobile Device Manager Plus to force install Apps on the managed Devices?
- Does MDM allow enterprise iOS apps to be installed silently, without user intervention?
Yes, you can install enterprise apps silently on iOS devices, if they are Supervised. Firstly, add the enterprise app source .ipa file to App Repository. Distribute it to devices and/or groups, after ensuring the Force Install option is enabled in Distribution Settings
- Can MDM be stop and/or control app updates on managed iOS devices?
Yes, you can stop and/or control app updates on managed iOS devices, if the apps are distributed and installed on the devices through ABM. Also, ensure Without Apple ID is selected during the initial ABM settings. This allows the app to be installed without requiring Apple ID and the app gets associated to the device instead of Apple ID, which is how it is usually associated. As the app is not associated with the Apple ID present on the device, the App Store doesn't notify the users of possible app updates, when distributed through MDM. You can choose to force app updates on the device as explained here
- Can MDM be used for completely locking down iOS devices?
Yes, you can choose to completely lock down the device by preventing users for installing/uninstalling apps and ensure only apps distributed via MDM is installed on the device. To lock the device to specific app(s)/settings, you can use Kiosk mode.
- How to Blocklist system apps on iOS devices?
System apps also known as pre-installed apps can be blocklisted using MDM by following the steps given below:
- On the MDM console, navigate to Inventory -> Apps.
- By default, the checkbox Show only installed apps will be checked. Uncheck this to display all apps on the devices, including the pre-installed apps.
- Search and select the app to be blocklisted. Click on Blocklist app and specify whether the app should be blocklisted for All devices or Specific groups/devices.
- Why are app updates delayed on kiosk devices?
Customers managing unattended kiosk devices, such as digital signages or Apple TVs, often encounter app update delays. This happens because:
- When an app update is pushed via MDM, the update begins only when the device is locked.
- Kiosk devices usually run continuously and are rarely locked, causing the update to remain pending indefinitely.
- Use the Remote Restart feature to restart the device remotely. This automatically initiates the OS update process after the device restarts.
- You can also remotely lock the device to help trigger the update process. On Apple devices, updates are pushed only when the device is locked this is by design and is part of Apple’s expected behavior.
- Why are app updates skipped on non-kiosk devices?
Customers using non‑kiosk devices face a different challenge when deploying app updates during business hours:
- When an app update is pushed via MDM, users receive a prompt asking them to install the update.
- Many users tend to cancel or postpone the update, leaving the device unpatched.
- This results in critical security updates or app fixes being delayed, increasing the risk of vulnerabilities and compliance issues.
- To avoid this, it is recommended to use App Update Scheduling, which allows updates to be installed automatically during non-business hours without requiring user interaction.
- Why am I unable to update enterprise apps on my iOS device over mobile data?
Apple restricts users from updating apps that are more than 200MB in size over mobile data, so by default they get updated over Wifi. This can be changed under App Store-> App downloads -> Always allow.
- How to enable Developer Mode on iOS/iPad OS devices?
To enable Developer Mode
- Go to Settings->Privacy & Security tab.
- Scroll down to the Developer Mode list item and toggle Developer mode.
- Tap the switch to enable Developer Mode
- You will receive an alert .Tap the alert’s Restart button.
- After the device restarts and you unlock it, the device shows an alert confirming that you want to enable Developer Mode. Click on Enable and Developer mode will be enabled.
- How to enable Developer Mode on iOS/iPad OS devices?
To enable Developer Mode
- Go to Settings->Privacy & Security tab.
- Scroll down to the Developer Mode list item and toggle Developer mode.
- Tap the switch to enable Developer Mode
- You will receive an alert .Tap the alert’s Restart button.
- After the device restarts and you unlock it, the device shows an alert confirming that you want to enable Developer Mode. Click on Enable and Developer mode will be enabled.
- Why don’t I see the App Store on my school iPad?
The App Store may be hidden because your school has applied the “Users can install only approved apps” restriction. With this restriction enabled, the App Store is blocked and only apps pre-approved and distributed by the school are available for installation.
- Why does my Apple VPP app show different versions?
The different app versions displayed are the versions compatible with each platform. Each app version is the supported version to that platform.
Note: The app developer decides whether the app version has to be same or different for each device(iOS, TVOS, macOS).
For example, Here in this case, The version 9.34.8 is compatible with iPhone, iPod and iPad. The version 2.3 is supported for Apple TV.
- How can I distribute my unlisted iOS app to devices?
Unlisted apps are apps published in App store that can be accessed with their direct link. These apps are hidden and cannot be found by search.
You can distribute an unlisted app to devices through MDM via ABM.
- On the ABM portal, click on Apps and Books.
- Search for the unlisted app with its App store URL.

- Purchase the app and assign token in MDM.
- Perform sync in Device Mgmt -> App repository -> Apps. Click on Sync apps and choose Sync Apple apps from the dropdown.
- Once the sync is completed, the app will be available in the app repository.
- You can then distribute the app to the devices.
- Android
- How to upgrade ME MDM app installed in Android devices?
To upgrade the ME MDM app installed on Android devices, visit our guide on automatically updating the ME MDM app on Android devices.
- How do I update the Google Play Store?
To Update Google Play Store:
- Open the Playstore App.
- Tap the profile icon (top right), then go to Settings > About.
- Tap on "Play Store version". If an update is available, it will download automatically. If not, it will display a message saying "Google Play Store is up to date."
- How can I stop users from adding unwanted accounts on managed devices?
This can be done by using the Restrict Specific Accounts option in the Android restrictions settings. Add the account identifiers you want to block, and the device will prevent users from adding those accounts. For example, blocking the Google account identifier stops users from adding any personal Gmail account.
- How do I update Google Play Services?
To Update Play services:
- Open the Chrome app and search for "Google Play Services".
- In the search results, click on the Google Play Services link to open it in the Google Play Store.
- If an update is available, tap "Update".
- Is it possible to remotely start an app on Android?
Yes, this can be done using the Custom Launch App Configuration in the ME MDM app. For more details, refer to the ME MDM App Configuration page.
- Why am I unable to distribute enterprise apps to Xiaomi devices?
This is an issue on particular models of Xiaomi devices. If you're unable to distribute enterprise apps to Xiaomi devices, follow the steps given below:
- On the Xiaomi device, navigate to Settings and click on About phone. Now click on MIUI version7 times.
- You will see a popup message which says you are a developer now.
- Navigate back to Settings and then click on Additional settings. Now click on Developer options and scroll down to the option Turn on MIUI optimization and disable it.
- The device is rebooted. Once rebooted, you will be able to distribute enterprise apps to this device.
- Why can’t users install certain apps in Google Play and see the error “The developer has restricted access to this app for accounts of anyone under 18 years of age”?
This behaviour occurs when an app is age-restricted by the developer.
The Developer has restricted access to this app for accounts of anyone under 18 years of age.
Cause: Google Play has introduced an enforcement that blocks apps marked as 18+ when the developer enables the Restrict Minor Access setting. Managed accounts are not recognized as adult accounts, which prevents the app from being installed or displayed.
Resolution:
- For organizations: If a required business app is affected, contact the app developer to confirm whether the 18+ restriction is necessary.
- For app developers: In the Google Play Developer Console, go to Target Audience and Content. If the app must remain rated 18+ but still be available for enterprise users, clear the option Restrict users under 18 from seeing this app.
- How to distribute Apps when all Google services are blocked on the device?
If the customer's network is a closed network, they can upload the .apk file of the app to App repository and distribute it to devices as explained in our Distributing apps to devices guide.
- The version of an app distributed via MDM and the version installed in the device are different. How is this possible?
This is due to staged rollouts of app updates on the Google Play store. An app developer can release updates only to a percentage of devices, which are chosen randomly. Click here for more information on staged rollouts.
Only the app versions which have completely rolled out (100%) are added to MDM. For example, say a staged rollout for an app is released for 20% of the devices. If the device falls into this category at the time of distributing the app via MDM, this issue of different app versions occurs. The app installed on the device will be of the latest version (The latest rollout), and the MDM server will have the previous version which has completely rolled out.
For apps developed using Google Play's multiple APK support (Listed as "Varies with device"), different APKs are targeted for different device configurations. Each APK of the app is an independent version, but they share the same app listing on Google Play. This might again display different app versions on the server and the device, based on the device type.
- How to purchase paid apps or make in-app purchases using Android for Work ?
Android for Work (AfW) has stopped supporting paid apps. You can still distribute paid apps using MDM by adding them as Play Store apps (Non-AfW) to the App Repository. Once these apps are distributed to the devices, the user needs to access Play Store using a personal Google account where the apps can be purchased and downloaded. A personal Google account is also necessary to make in-app purchases. If a managed account is used in this place, only the free version of the app can be downloaded and in-app purchases cannot be made. To ensure that the user is able to add a personal account, navigate to Device Mgmt->Profiles->Android->Restrictions->Device Functionality on the MDM server and ensure that Add Accounts is set to Allow. For more information, visit our Managing Play Store Apps guide.
NOTE: If there are multiple accounts on the device, the user needs to switch to the personal account to make the purchases.
- How can I restrict users from installing unapproved apps on Android devices?
This can be done in 3 different ways.
- Android restrictions: If you want to completely prevent users from installing any apps on the devices, you can disable the restriction Users can install unapproved apps by navigating to Device Mgmt->Profiles->Android->Restrictions->Applications, on the MDM console. This will ensure that only apps distributed by MDM are present on the devices.
- Blocklist apps: If you want to prevent users from installing a specific set of apps on the devices, you can navigate to Inventory->Apps on the MDM console and select the apps to be blocklisted. In some cases, these apps will be removed from the devices immediately and cannot be installed on the devices again.
- Kiosk: If you want the users to access only a single app or a specific set of apps and restrict the others, you can provision the devices in Kiosk by navigating to Device Mgmt->Profiles->Android->Kiosk, on the MDM console. Kiosk provisioning prevents users from navigating to other apps on the devices, other than the Kiosk app(s). Additionally, specific device settings and functionality can also be restricted.
- Why am I not able to clear the ME MDM app history from my recently used apps?
In Samsung devices, MDM restricts users from being able to close the ME MDM app. Once the device is switched on, the app will automatically start running. This is to ensure that the device maintains connectivity with the MDM server and that any policies or restrictions are immediately applied to the device.
- How can I hide notifications from the ME MDM app?
We recommend that the notifications from the ME MDM app are always on, as these would keep the user informed about imposed policies or violated policies. Notifications can be turned off on the device's settings, but for devices running on Android 8.0 and higher, the notifications will by default be shown to the user. This is a privacy feature enabled by Android.
- Why are certain apps removed after enrolling an Android device as Device Owner?
MDM enables apps on devices provisioned as Device Owner based on the following conditions:
- All non-launchable system apps.
- Launchable system apps provisioned with system signature.
If an app satisfies the above conditions, but still is not enabled on the device, this can be resolved by distributing the app via MDM. Navigate to App Repository> Add App> Play Store App>enter the Bundle Identifier of the app and save it. This app can then be distributed to the devices.
- Unable to upload any of the Android Enterprise App in Windows Server 2012 R2 system.
This issue is caused because MDM uses a tool called appt as recommended by google to analyze apk details. Recently aapt has been upgraded to the latest version - aapt2, which requires certain dll requirements that are missing in older versions of Windows Server 2012 R2 system. Thus, an error is thrown when executing the aapt2.exe. This can be solved in the following two ways:
- Upgrade the hosting server machine to make use of the latest tool- aapt2.
- If the above option is not working, a backward-compatible feature can be used to manually enter the app details, upload and distribute them to devices. Contact support to know more.
- General
- Does MDM require an agent to be installed in all the devices that are being managed?
In case of iOS and Windows devices, Mobile Device Manager Plus leverages the native MDM client already available in all the devices. The agent is required only to perform the following-
- Track the location of the devices
- Securely view and save documents on the ME MDM app
- Remotely view or control the devices
- Update logs from the devices
- Detect jailbroken or rooted devices
Whereas, in case of Android devices, an ME MDM app is required to manage mobile devices. The installation of the app is taken care of during the enrollment process.
- How to remove a device from the Mobile Device Manager Plus server?
If the device is enrolled with MDM, it has to be deprovisioned before being removed from the server. On the MDM console, open the Enrollment tab and click on the ellipsis button under the Action column, corresponding to the device to be removed from management. Now, click on Deprovision. The device will be moved to Staged tab from where it can be deleted using Remove Device option. If the device is offline or if it has already been unmanaged, it can be directly removed from the MDM server.
- Is call recording supported in Mobile Device Manager Plus?
No. Mobile Device Manager Plus does not provide an option to enable or manage call recording on devices. This functionality is not available due to platform restrictions and privacy regulations.
- What happens on the device when it is removed from MDM?
The admin can choose to deprovision the device to revoke MDM Management using the following options:
- Repair Device
- Employee left organization
- Retire Device
- Others
Repair Device, Employee left organization and Retire Device factory resets the device whereas under Others, the admin can choose between a Complete Wipe and a Corporate Wipe.
When the Complete Wipe option is chosen during deprovision, the device is factory reset resulting in the removal of all content and settings. When the Corporate Wipe option is chosen during deprovision, the consequences are as follows:PLATFORM PROVISIONING TYPE DESCRIPTION Android Device Owner, Core Android and Samsung devices On device deprovision, all the associated profiles are automatically removed without uninstalling the formerly distributed apps. Profile Owner The complete work profile is removed resulting in the removal of every policy, app, and content distributed via MDM. Apple On deprovision, all the associated profiles, apps and distributed content are removed from the device. The ME MDM app is also removed if Remove app on MDM Profile Removal option was checked at the time of adding it to the App Repository Windows On deprovision, all the associated profiles, apps and distributed content are removed from the device. All configurations in Company/Workspace are cleared for devices running Windows 8.1 and above. NOTE: If a passcode policy is associated with the device, only the policy is removed and the passcode remains on the device on deprovision.
- How do I change the user or device details on the console?
To change the device name, navigate to Inventory and click on the Edit button next to the device name. To change user details, select the device in the Inventory tab, under Actions choose Edit User Details.
- How long does it take to receive the location details and history report in ManageEngine MDM?
The time taken to receive the location details and history report in ManageEngine MDM depends on the number of devices and the volume of location data. For example, retrieving a report with approximately 10,000 location entries may take around 30 to 45 minutes.
- Can mobile devices be automatically shut down?
Yes, It can be done using Remote Shutdown Command and it is currently supported for iOS devices that are Supervised, and running on versions 10.3 and above, and for macOS devices.
- Why isn't my iPad's IMEI shown when viewing device information on the Inventory?
If the device has SIM slot, then MDM can display the IMEI. In case you've enrolled iPads that do not have SIM slots, the IMEI cannot be obtained and thus, not displayed by MDM.
- When are devices marked as Inactive Devices on the MDM server?
The device status will be marked as inactive when the device loses contact with the server for a period longer than the duration specified by the admin. Below are the scenarios when a device may lose contact with the server. If the device,
- is switched off.
- is not connected to the Internet.
- factory reset and is unmanaged.
- is removed from management by the user when it did not have internet connectivity. To prevent users from revoking management refer to this document.
- is connected to any network internal or otherwise, that blocks certain URLs thereby preventing the device from contacting the MDM server. To verify this try accessing mdm.manageengine.com from the device browser.
- How to undo Supervision in iOS devices and Device Owner provisioning in Android?
Both Supervision as well as Device Owner provisioning lets the Administrator leverage additional control over the managed devices. It can be undone by factory resetting the device.
- How can we manage BYOD?
"Bring Your Own Device" (BYOD) being the integral part of Mobile Device Manager Plus, you can ensure the security of corporate data. Whenever any user's personal device is lost, or the employee quits an organization, administrators can execute security commands like corporate wipe or complete wipe to ensure data security. Hence Mobile Device Manager Plus MDM is a smart choice for every enterprise to manage BYOD.
- What is difference between Complete Wipe and Corporate Wipe?
Corporate wipe is a security command used to wipe data on the device. This security command is mostly used to secure the corporate data from devices, when they are lost. Corporate Wipe is used to remove only the configurations and Apps that have been pushed using Mobile Device Manager Plus and this command will not wipe any personal data of the user.
Corporate Wipe will remove Exchange Server or Email only, if they are configured via Mobile Device Manager Plus. This includes, the files and documents shared using the corporate e-mail.
Complete wipe command is used to wipe all in the data in the device, which makes the device as good as a new.
- Can you wipe the data from the device's external memory?
Yes, you can wipe data on the device's external memory.
- How to protect Corporate Data on the mobile devices?
You can secure corporate data on mobile devices by applying the following restrictions:
- Disabling Screen capture
- Disabling Backup (iCloud)
- Disabling Document Sync
- Disabling Photo Stream
- Disabling Shared Stream
- Disabling User to accept untrusted TLS Certificates
- Forcing Encrypted Backups.
- Configuring Email settings to restrict data forwarding.
These restrictions will help you to secure Corporate data on mobile devices.
- Which are the devices that support the remote control feature?
Mobile Device Manager Plus offers remote management features with the following requirements
Remote Control (Android):
Full remote control is available for select OEM devices (refer to our supported OEM list ) from Android 5.0 and above, and for all other devices from Android 7.0 and above, provided the devices are provisioned as Device Owner .
Remote Viewing (Android & iOS):
Available for iOS devices and Android devices (5.0 or later) that are provisioned as a Profile Owner. - How can I completely disable location tracking in MDM?
Most organizations prefer to disable geotracking due to user privacy concerns. While admins have an option to track devices only when lost by configuring Geo-tracking Settings, some admins prefer to completely disable location tracking on devices. This can be achieved by navigate to Admin -> Device Privacy. Click on Modify and under Geo-location select Do not collect. Under Applicable Devices, select whether this setting must be applied only to personal, corporate or all devices. Click on Save and MDM would not collect any location details from the managed devices
- How do I add users(technicians) to manage devices?
You can associate users to either pre-defined roles or create roles and associate them. Additionally, you can modify the users, their roles and even delete them. Know more about user management here
- How to add a user and grant the user read-only privileges?
- On the MDM server, navigate toAdmin tab and select User Administration, present under Global Settings .
- Click on Add User. Provide the required details and specify the role as Guest. This ensures the created user has read-only access.
- How to change Super Admin privilege from one user to another?
- Login here with Zoho account. All the services being used by the Zoho account are listed.
- Click on the pencil icon present against the Super Admin Name, to change the Super Admin, as shown in the image below.
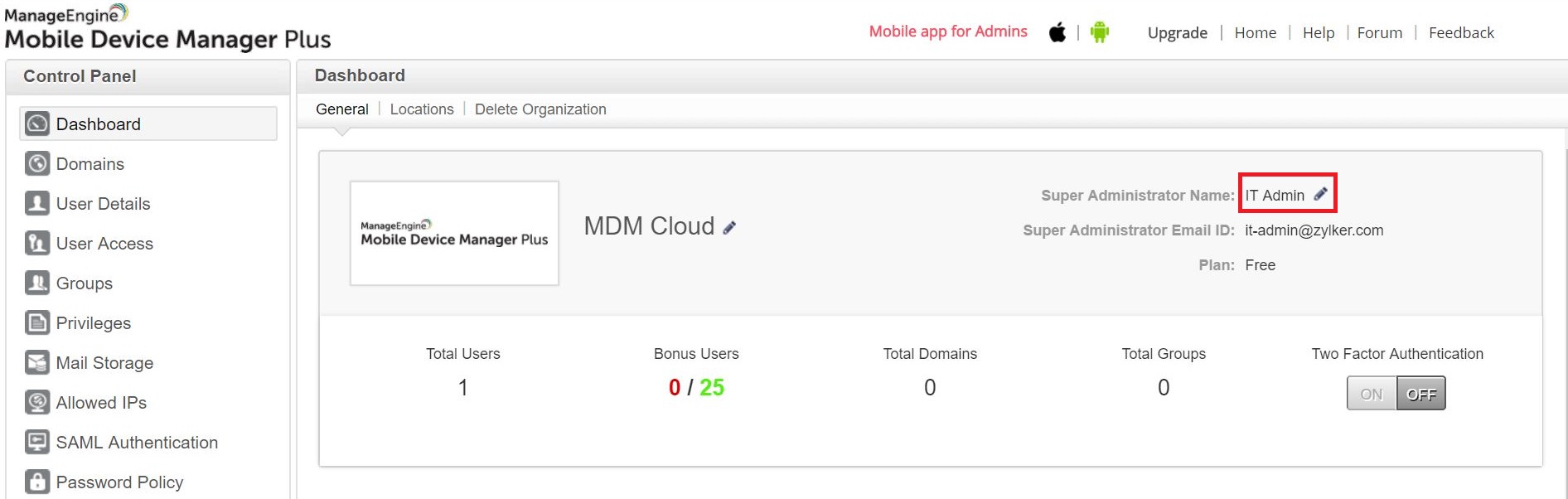
- All the user added administrators on MDM Cloud are listed. Select the new Super Admin. The Super Admin E-mail Address gets modified automatically.
It is to be noted the Super Admin of all the Zoho services are changed, when this is done.
- Apple
- What purpose do Apple IDs serve in iOS device management?
For iOS device management, the Apple IDs are used by both the organization and the users. The organizations Apple ID should preferably be mapped to the organization and not any individual in the organization. While the user's Apple ID is mapped to the individual device user.
Following are the services that make use of the organization's Apple ID-
- For creating a Device Enrollment Program (DEP)/ Apple School Manager (ASM) account to enroll mobile devices
- For creating a Volume Purchase Program (VPP) account to distribute and manage apps on the devices
- For creating an Apple Push Notification Services (APNs) certificate, for communication between the server and the APNs.
NOTE: It is recommended to only make use of the organization's corporate Apple ID for the above mentioned services, as they all require the same Apple ID to be used during renewal.
The user's Apple ID can be used for the following-
- Purchasing personal apps on the devices. The apps that are distributed from the MDM server using ABM do not need the user's Apple ID
- Accessing iCloud and the other related services like iMessage, Facetime and iCloud Drive.
- Turning off Activation Lock on devices on unmanaged devices. Activation Lock is automatically turned off by the MDM service if it is managed.
- Why Erase All Content and Settings option is missing for managed iPadOS devices?
If the iPadOS devices are enrolled as shared iPad devices then this option will be missing. Admin can factory reset the device in the Inventory on MDM console by using Complete Wipe option.
- Cannot disable lost mode.
Disable lost mode command may fail occasionally when Apple returns the command with error code 12069. To recover, factory reset the device using Apple Configurator or iTunes.
Note: But in the case of devices with no sim cards such as iPads when the device is in lost mode and is restarted then the Wi-Fi connectivity is lost and the device is locked. To avoid this, it is suggested to clear the passcode on the devices after successfully enabling lost mode on the device but before restarting the device. - Failure of clear passcode command.
The clear passcode action may occasionally fail due to mismatch in the unlock token(Unlock Token is used to unlock a device where a user has forgotten the device passcode. These tokens should be saved for devices when the devices are initially configured). The mismatch of this unlock token may happen if the OS update is pending or due to several other reasons. Hence, this issue can be resolved by updating the OS or restoring the device.
- What benefits does Declarative Device Management bring?
Declarative Device Management streamlines app tracking and reporting by enabling devices to automatically update statuses and report changes instantly. This ensures the inventory remains accurate in real-time without requiring frequent server check-ins, making device management faster and more efficient. To learn more click here
- Android
- Does MDM always require bluetooth and location permission to manage Android devices?
MDM requires these permissions to perform certain functions. Location permission is required to identify the already connected WiFi(from Android 8). So, we will use this while applying WiFi in restrictions payload or WiFi payload. We use bluetooth connect permission(from Android 12) to fetch the bluetooth mac address and also while applying the bluetooth always on/off restriction.
- Why couldn't I fetch details like serial number, IMEI from my Android devices that are enrolled as a Profile Owner?
Android restricts collecting device identifier details like serial number, IMEI number, MEID etc in Profile owner devices as a part of privacy policy from Android 12 devices. To know more about this, refer here.
- Why is Secure Folder restricted by default in Samsung Device Owner devices?
The Secure Folder option is prevented in the Samsung framework itself and when the device is enrolled as Device Owner, apps like a Secure Folder, Dual Workspace will be restricted by default because they will be using a separate user which cannot be managed by MDM.
- What happens to the Device Owner devices with EFRP profile when a complete wipe is initiated on them from the server?
For Non-Samsung devices: While factory resetting the device, the accounts will get removed and the FRP will be skipped.
For Samsung devices: Google Accounts present in the device need to be manually removed before wiping the device. The Account removal will be successful, only if the Google Play services are supported above a specified version. - How can we unmanage a device enrolled using ABM/ASM?
A device enrolled using ABM/ASM cannot be unmanaged simply by factory resetting the device. To unmanage this device, we first need to remove the device from the ABM server and then reset the device in Recovery Mode.
- Why do I need to encrypt my device for provisioning devices as Device Owner/Profile Owner?
Data encryption is mandated by Google for provisioning Android devices running 5.0 or later versions and 6.0 or later versions. Only for devices running 7.0 or later versions is encryption not required for provisioning the device as Profile Owner/Device Owner.
- Why are users able to remove the Managed Account on devices?
When Managed Google Play is integrated without G Suite on the MDM server, a Managed Account is created on the device. By default, this Managed Account cannot be removed by the user. However,
- If the Managed Google Play integration is removed from the MDM server, the managed account on the device will be considered invalid and can be removed by the user.
- If the Managed Account has expired, it can be removed by the user.
- If an expired account is removed, a new Managed Account will be automatically added on the device.
- Does Corporate Wipe command from MDM affect the G Suite account on the device ?
If the G Suite account is configured on the device by enabling Enforce EMM policies under G Suite admin console->Settings->Security->Mange EMM provider for Android, the account gets added to the Work Profile on the device. A Corporate Wipe command, erases the Work Profile along with the G Suite account.
- Why Conditional Exchange Access is not supported for Outlook?
Conditional Exchange Access can not be offered for Outlook for the following reasons:
- Outlook offers access to Exchange email via internet. Since the Exchange mail's credentials and the server URL are stored in the Exchange servers, Outlook relies on the internet to relay requests from a remote client to the Exchange server. This involves the risk of exposing the server directly to the internet.
- When a device tries to access Exchange mailbox, an EAS identifier will be issued to the device for device identification. The EAS identifiers of devices that are enrolled with MDM are stored in the server and any new connection with unknown EAS identifiers will be blocked from reaching the server. In Outlook app, every time a user uses the same Exchange credentials to login from a different device, the same EAS Identifiers will be issued to the device. This would allow any unmanaged devices to gain access to the Exchange mailbox, thereby introducing security risks.
- How do I send iOS device logs to MDM Cloud support?
You can compile the iOS logs from the device, using MDM app and mail it MDM Cloud support team(mdmcloud-support@manageengine.com)
- Open the ME MDM App in the managed device.
- Navigate to Support tab.
- Select Collect logs. A notification is shown when the logs are successfully compiled. These logs get automatically mailed to the Cloud support team.
- How do I submit logs from the Mobile Device Manager Plus app in Android?
When you tap Support in the ME MDM app, the Log Upload Details screen opens. After selecting the issue type and entering the admin email, the logs are sent to the ManageEngine MDM support team using the email address you provide in the Admin Email field. The support team uses this email to identify your ticket and contact you if needed.
- How to purchase MDM Cloud?
- On the MDM server, navigate toAdmin tab and select Subscription, present under Global Settings.
- Fill in the number of devices you want to manage and other required details. Click on Buy Now.
- On clicking, Zoho Store page is opened. Review and confirm your order.
- Proceed and provide your payment method. On successful completion, your MDM Cloud license will be activated immediately.
This is a pay-as-you-go Service and can be mended as and when you need. Additionally, you can also purchase offline(Non-Store) by mailing to sales@manageengine.com.
- How to reactivate my license, if it has expired?
- On the MDM server, navigate toAdmin tab and select Subscription, present under Global Settings.
- Click on Manage Plan.
- On clicking, Zoho Store page is opened. Renew your license here.
- On successful completion, your MDM Cloud license will be activated immediately.
In case you're denied access to MDM server, click on the Buy Now to proceed with the reactivation. - What are the types of payments supported by MDM Cloud?
Payments are securely done using Zoho Store. MDM Cloud supports payment via Visa, MasterCard, American Express and PayPal. You can also purchase offline(Non-Store), by mailing to sales@manageengine.com.
- How do I modify my MDM Cloud license?
- Modify your license by navigating to this link(sign up with the Zoho account, if need be). Click on Manage Plan, which re-directs you to Zoho Store.
- Hovering on the plan, lets you add/remove the number of devices to be managed. Similarly, hovering on technicians and multi-language support, lets you add/remove technicians and unsubscribe multi-language support respectively, as shown in the image below:
- Assume you want to add more devices for management. Click on the plan and specify the number of devices you want to manage.
- On specifying the additional devices, the required cost to be paid is displayed. You can then continue with the payment and finish the purchase.

- How to change payment method from offline(Non-Store) to online?
For changing payment method from offline(purchasing licenses by mailing to sales@manageengine.com) to online,
- On the MDM server, navigate toAdmin tab and select Subscription, present under Global Settings. Click on Manage Plan, which redirects you to Zoho Store. Now click on the Payment Method link as seen in the image below
- Provide credit card details and click on Update, to modify your payment method.
- How to modify the specified credit card details?
- Login with the same Zoho account used for signing in with MDM Cloud.
- All the information about your billing cycle, card details and billing address can be viewed here. Click on Change Card to edit or update your card details
You can also change the billing address here as well. All your confidential data is secured using VeriSign.
- Why does the remote control session show a black screen?
This occurs when sensitive information, such as passwords or security details, is displayed on the device.
- Is there a time limit for Remote View or Remote Control sessions?
No, there is no fixed session time limit. The remote session will continue as long as the device remains connected to a stable network.
- Is file transfer possible for Android devices?
Yes, file transfer is supported for Android devices.To enable this, ensure the “Enable File Transfer” option is turned on in the ME MDM app configuration.
For BYOD (Bring Your Own Device) setups, only files stored within the workspace container can be transferred during remote troubleshooting sessions.
- Is file transfer possible for Android devices?
Yes, file transfer is supported for Android devices.To enable this, ensure the “Enable File Transfer” option is turned on in the ME MDM app configuration.
For BYOD (Bring Your Own Device) setups, only files stored within the workspace container can be transferred during remote troubleshooting sessions.
- Can I remotely view or control Apple TV devices using MDM?
No, Apple TV devices cannot be remotely viewed or controlled through MDM.
- Is it possible to update iPadOS / iOS using mobile data?
Yes, iPads and iPhones running iPadOS / iOS 15 or later can update over 5G, but only if the following conditions are met:
- Device: iPhone 12 or later / iPad with 5G cellular capability
- Network: Connected to a 5G cellular network
- Settings:Allow More Data on 5G is enabled under
Settings > Cellular > Cellular Data Options > Data Mode
Note:
- Only cellular models of supported iPads are eligible.
- iPhones older than iPhone 12 require Wi-Fi.
- Some carriers may restrict or block updates over cellular.
- iPadOS / iOS updates may consume large amounts of data — check your data plan to avoid extra charges.