IT infrastructures are typically made up of numerous applications, processes, and scripts that are in constant communication with other applications, systems, databases, and network devices to ensure business operations are conducted smoothly. This communication requires access to credentials such as passwords or SSH keys with which the various components authenticate one another.
A commonly followed practice is to hard code the authentication credentials in the application source code or store them in clear text within configuration files and scripts on local systems. Embedded credentials are believed to expedite application-to-application communication, especially in high-scale deployments, so IT teams are reluctant to rotate them in fear of breaking or disrupting operations. This is why these credentials, once created, often remain unchanged with continued exposure to a wide audience, creating a huge risk of unauthorized access to mission-critical systems.
PAM360 helps enterprises eliminate the use of hard-coded credentials and passwords stored on local machines across their networks by providing secure APIs for application-to-application and application-to-database credential management.
Achieve operational continuity without hard-coding privileged credentials
PAM360 provides secure APIs that enable third-party applications and processes to retrieve privileged credentials for business operations, eliminating the need for hard-coding sensitive passwords in application source codes or configuration files. Leveraging the wide range of APIs available, processes and applications can readily communicate with one another, checking out privileged credentials from PAM360's database whenever required to ensure speed and agility.
PAM360 currently offers two flavors of APIs:
- A command-line interface for scripts over secure shell (SSH).
- Representational State Transfer (REST) API.
End-to-end management of application credentials with enhanced security
Incorporating a gateway-based access path for application-to-application communications ensures that sensitive credentials are consolidated in a secure, central location and always remain on IT administrators' radar. On top of this, these application credentials are subjected to security best practices such as frequent rotation, strong policies, and so on, eradicating the prevalence of stale passwords without the need for daunting manual updates.
Enforce access controls and fine-grained privileges on application credentials
To access application credentials through APIs, PAM360 requires users to set up native user accounts from within the product and map them to the endpoints from where the APIs are being called. These user accounts are access controlled and are allowed access to credentials depending on the privileges given to them by the administrator. Available privileges include various operation levels like retrieve, modify, or create.
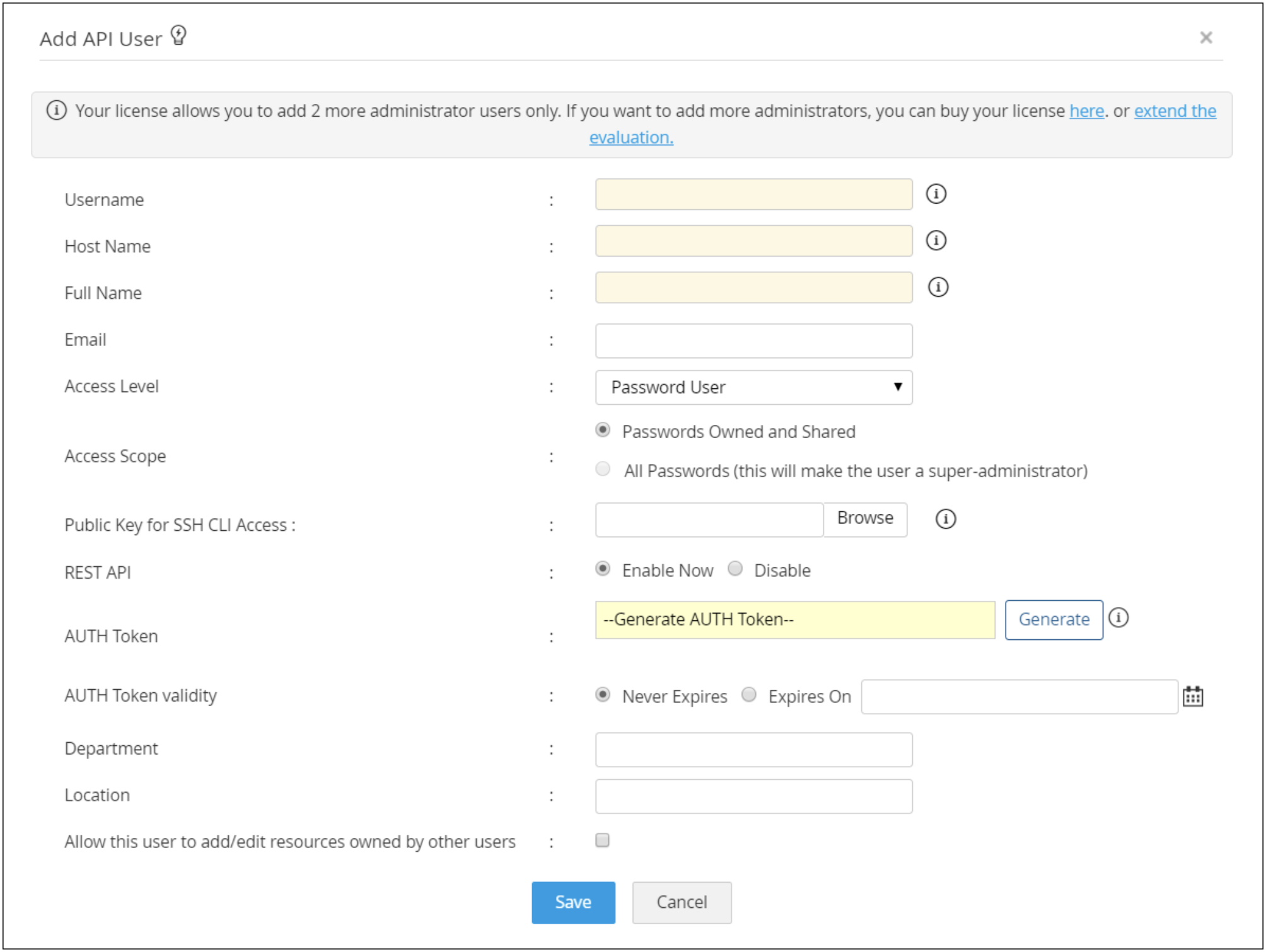
Meet compliance mandates and internal requirements.
Various government and industry regulations mandate that sensitive information should not be hard-coded. Eliminating hard-coded passwords and subjecting application credentials to periodic rotation can help organizations satisfy both internal audits and external compliance requirements.