To make informed business decisions, organizations keep extensive records of their past activities. Similarly, IT teams need intuitive reports on privileged access to make decisions about enterprise password and key management, and comply with various industrial and federal regulations. PAM360 offers a collection of reports that help organizations gain a wider, in-depth view of password security and privileged user activity with timed reports on password inventory snapshots, password shares, user access stats, password reset history, and more. Further, IT administrators can rely on PAM360's out-of-the-box compliance reports for security audits, generate custom reports using data available from audit trails, or query the database directly to extract specific types of data formatted as reports.
Get complete visibility over password usage, access control, and rotation history
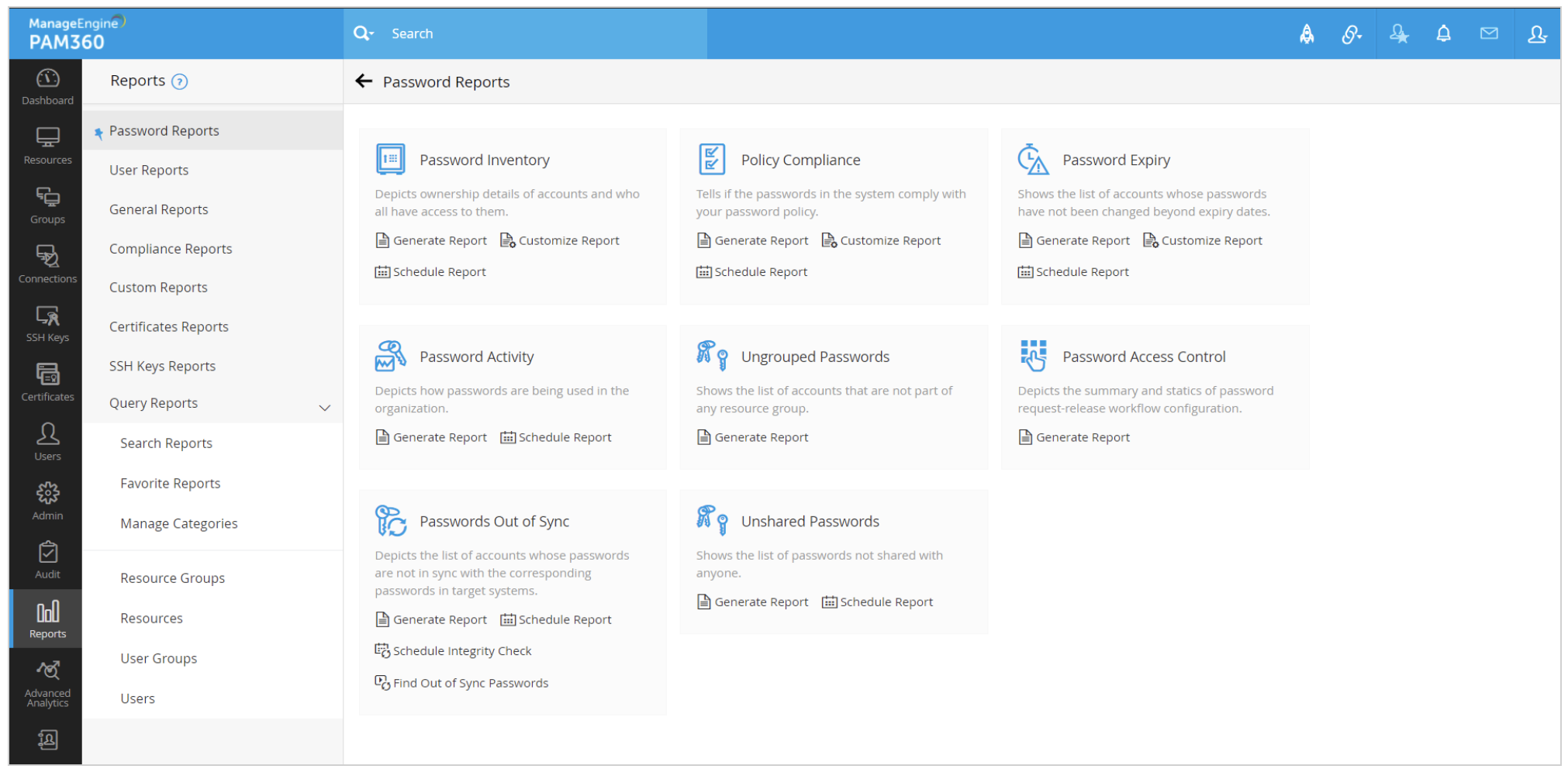
PAM360 helps businesses get a holistic view of privileged password usage across the enterprise by facilitating generation of reports with details such as a list of users and their groups, roles, login attempts, credential approval and sharing, and all other password-related activities performed. On top of that, administrators can identify and monitor the most active users and permission levels they possess for different resources. The activity logs of specific users can be converted into reports as needed for internal audit purposes. All this information is also mapped out in graphical format for easier consumption.
PAM360 also provides specific reports on passwords that violate your current policy—along with details on which policy requirement is not adhered to—and reports on passwords that are no longer valid. Administrators can automate report generation through a simple scheduled task creation and once generated, the reports can be configured to be mailed to select recipients in PDF or XLS formats. Click here to learn more about user and activity reports.
Exercise complete flexibility, and generate custom-fit reports
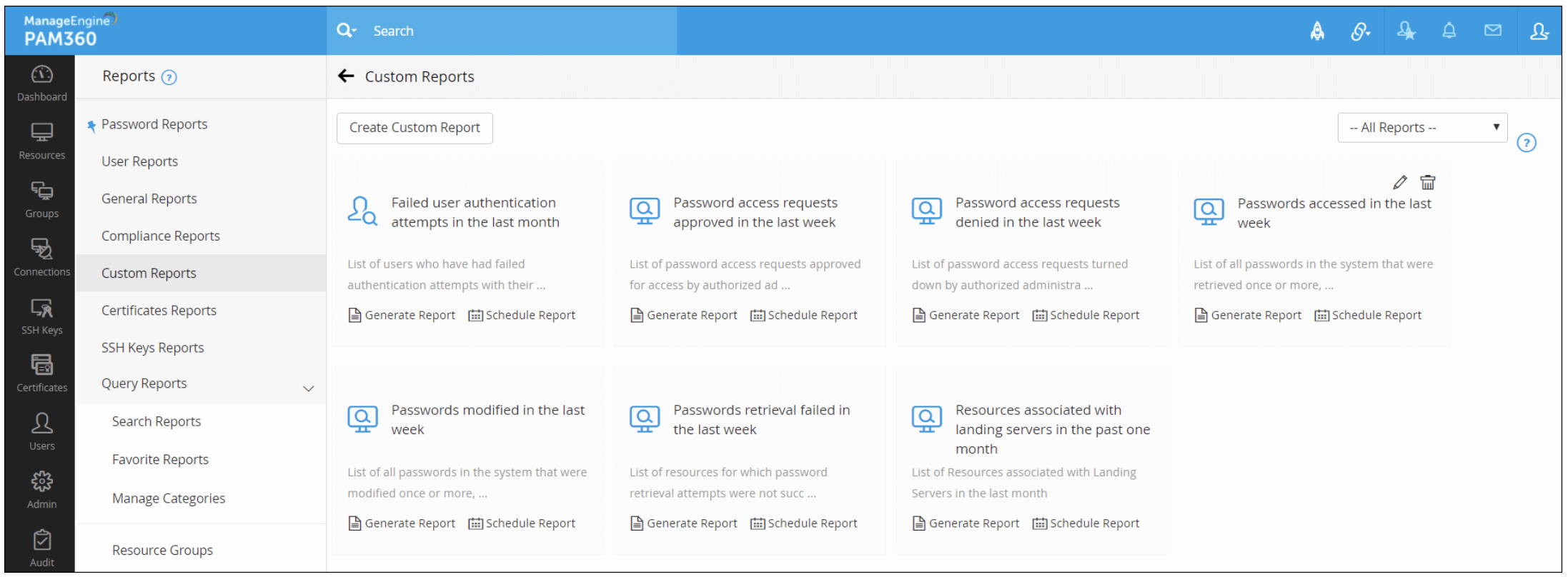
PAM360 allows you to generate custom-fit reports in which you can combine standalone detail sets from audit records and general status reports to derive useful information. You can leverage the available data to meet auditing requirements, security mandates, and various compliance needs. Administrators can effortlessly extract desired information from PAM360's database by specifying granular filter criteria. For instance, if your security audit requires a snapshot of department-wise use of passwords, you can specify the appropriate criteria and generate department-specific reports.
This report also comes in handy when an employee leaves the organization or when you terminate a third-party contract, especially with regards to determining their privilege levels in the organization and assessing the associated vulnerabilities. For instance, if an administrator who has elevated access to privileged assets leaves, it's important to initiate resets. Using custom reports, you can pull out the complete list of passwords the specific user had access to, and take necessary follow-up action. Click here to learn more about custom reports.
Effectively meet IT audit requirements with PAM360's out-of-the-box compliance reports
Security has always been a major concern in IT; now, with various industry and government regulations in place, organizations must adopt strategies that prove compliance with them. With the proliferation of privileged accounts across the corporate network, it can be daunting for IT admins to track, monitor, and provide auditors with appropriate evidence to meet compliance requirements. PAM360 overcomes this by facilitating the generation of audit-ready, out-of-the-box compliance reports that relay enterprise security.
PCI-DSS compliance report
PAM360 helps address security requirements in the payment card industry, spanning several sections of PCI-DSS. In a nutshell, these sections necessitate protection of sensitive data with strong cryptography, changing system default passwords, restricting access to information on a need to know basis, using strong passwords along with periodic rotation, continuously monitoring privileged access, and enforcing an enterprise-wide policy to standardize information security practices.
ISO/IEC 27001 compliance report
On a broader level, ISO/IEC 27001 requires establishing, maintaining, and continually improving an information security management system in an organization. PAM360 helps achieve compliance with mandates specified under clause A.9 of the standard, which deals with access control. The clause outlines the requirement of a robust information security policy to ensure only authorized users have access to critical systems, all users are uniquely identified and have established accountability for all privileged activities, access is only allowed to systems through secure mechanisms, and sensitive information is protected with cryptographic controls. PAM360's ISO/IEC 27001 compliance report communicates an organization's compliance level in relation to control requirements as outlined in the clause A.9.
NERC-CIP compliance report
Organizations in the energy sector are required to comply with NERC-CIP, which lists standards focused on ensuring the security and reliability of power systems. PAM360 ensures compliance with select requirements that mandate a regular review of authorized personnel with access to critical systems, granular access controls based on functional roles, robust authentication methods, comprehensive auditing of security events, monitoring of user activity during privileged sessions, and use of strong passwords with reliable complexities.
GDPR compliance report
The General Data Protection Regulation (GDPR) is a comprehensive set of standards framed and adopted by the European parliament to protect all EU citizens' personal data and safeguard their privacy. The GDPR clearly defines the scope of personal data in Article 4 as "any information relating to an identified or identifiable natural person (data subject).” Any organization that works with the personal data of EU residents has to comply with the GDPR, irrespective of where the organization itself is located. In order to exhibit compliance with the GDPR, PAM360 offers features to uphold data subjects’ rights and ensure that privacy is safeguarded at all times. The exclusive report based on GDPR guidelines elaborates the configurations enabled in the product that helps IT teams steer clear of any non-compliance during security audits.
Apart from the above out-of-the-box reports, PAM360 also provides compliance for industry regulations like NIST, SOX, and POPIA. Click here to learn more about compliance reports.
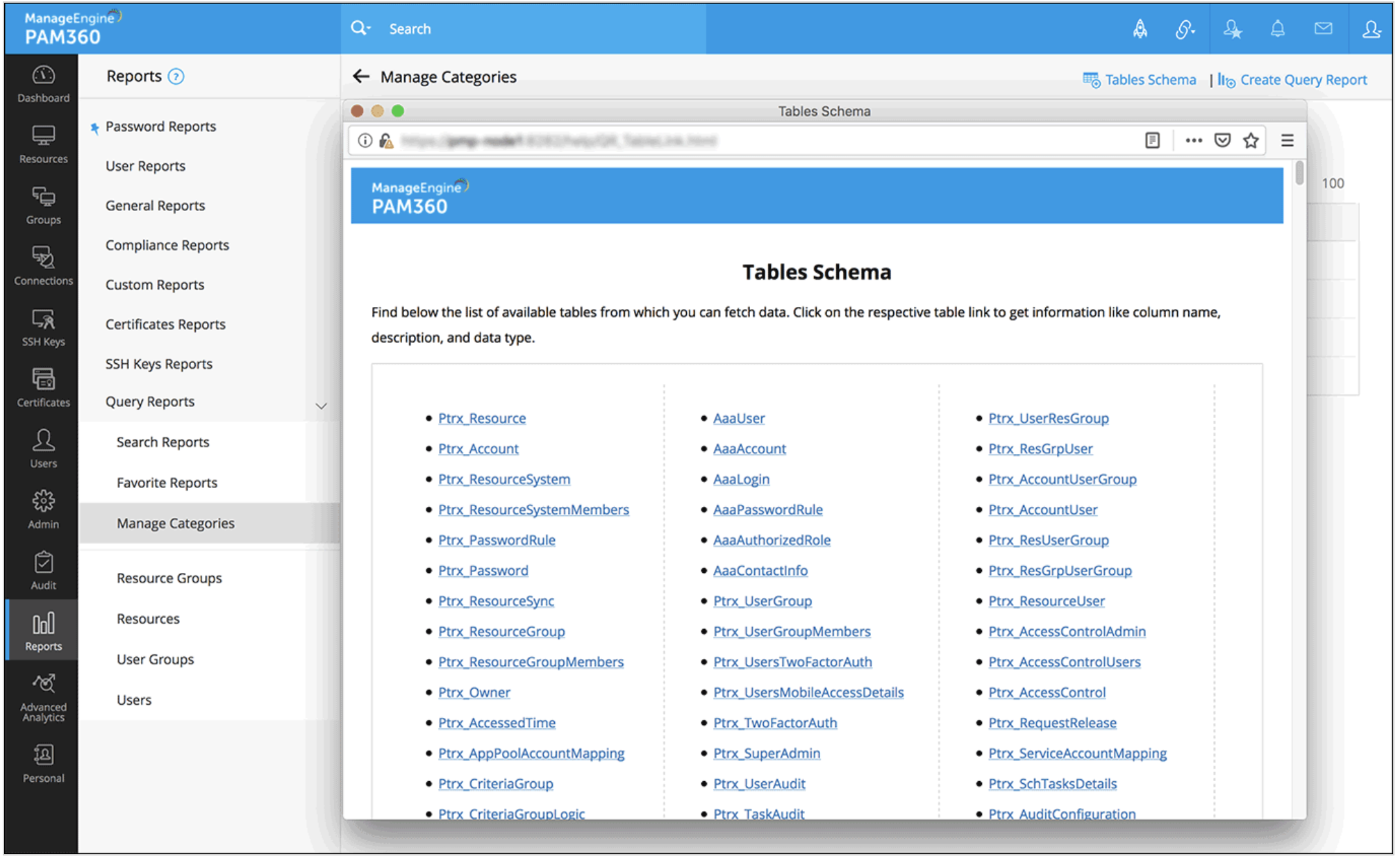
Directly query the PAM360 database to fetch specific information about privileged access
With PAM360, administrators can query the database—either by writing their own SQL query or customizing an already existing query—to extract specific information directly from it. These queries help fetch information from select tables and present them as structured reports for easy perusal. Once a query report is created and saved, administrators can configure them to be automatically generated on a recurring basis via scheduled tasks. Click here to learn more about query reports.