Privilege elevation and delegation management (PEDM) is a category of privileged access management (PAM) that includes essential controls to provide non-admin users with administrative access to sensitive applications, resources, scripts, and systems on a granular, time-limited basis. In effect, PEDM enables IT teams to implement the principle of least privilege, in which they provision just enough privileges for users to perform their jobs, which eliminates the risks of standing privileges associated with unmanaged, outdated, and orphaned privileged accounts.
PEDM is an essential cog of PAM software
Occasionally, non-admin users, such as developers, may need higher privileges to gain administrative access to critical resources. In such cases, IT teams need a way to elevate privileges temporarily and have them revoked when the user completes their task.
While privileged account and session management solutions can grant temporary access to critical accounts, such accesses can be provided only on an all-or-nothing basis. In these instances, users are mapped to temporary admin accounts, also known as ephemeral accounts, which can provide them with full administrative access to the target resources, including applications and assets that they should not access or don't need to access to carry out their task. Further, if these temporary admin accounts are shared with more users, or much worse, if one of these accounts get compromised, any attacker could use it to navigate the privileged networks and systems while remaining undetected.
PEDM solves this problem by allowing users to access sensitive resources and applications through a time- and request-based approach. Access to critical resources is provided with elevated privileges for a specific period based on the validation of their requirements. Such temporary privileges are revoked and credentials of these privileged accounts are rotated after the stipulated time to prevent any unauthorized access attempts in the future. This also helps purge any standing privileges that can be exploited by attackers or even malicious insiders.
Manage user privileges with ManageEngine PAM360's PEDM capabilities
ManageEngine PAM360's PEDM capabilities empower IT teams to establish granular control and visibility over user privileges by including just-in-time and self-service privilege elevation options for local and domain Windows accounts. This essentially includes granting higher privileges associated with certain applications, systems, scripts, and processes for a designated period. These tight controls allow IT teams to adopt the principle of least privilege in order to provide non-admin users with just enough privileges to carry out their activities.
Types of PEDM capabilities offered by PAM360
PAM360 offers both agent-based and agentless modes of privilege elevation. In the agentless mode, known as just-in-time privilege elevation, users with valid access requirements will be automatically elevated into local security groups for temporary access to target systems and are reverted to their default privileges upon the expiration of their access request period. Similarly, a domain user account can be elevated into a domain security group via an integration with ManageEngine's Active Directory Management solution, ADManager Plus. Learn more about how PAM360's just-in-time PEDM features works.
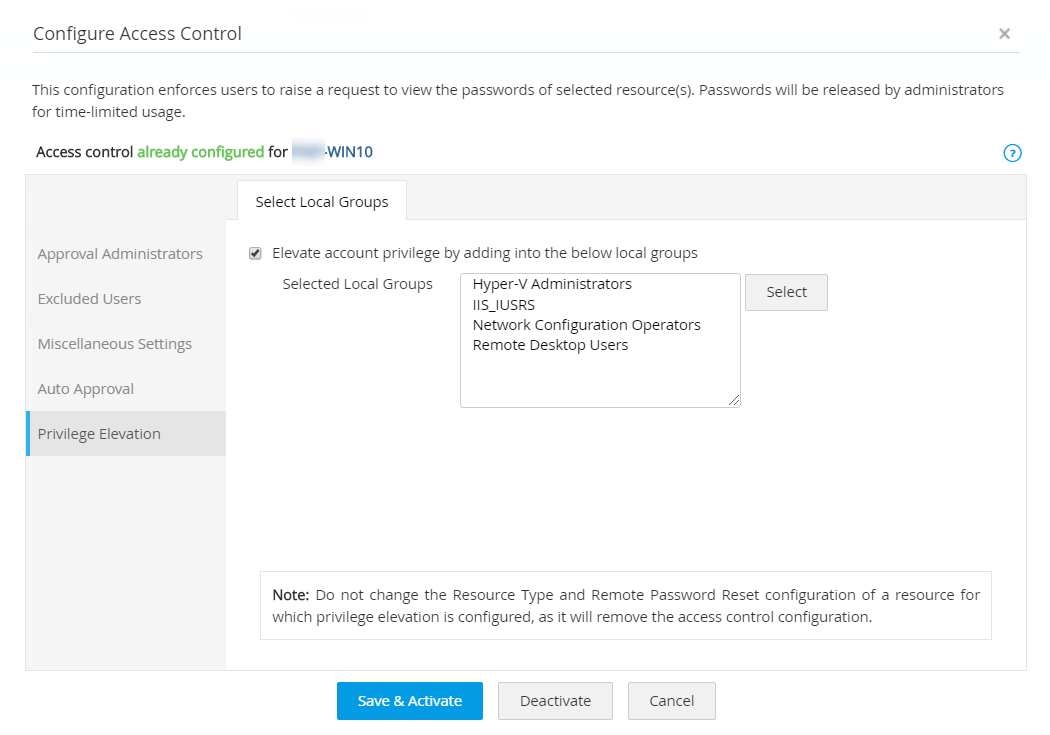
The agent-based privilege elevation approach, also known as self-service privilege elevation, is enabled by installing and configuring self-service privilege elevation agents in the target endpoints. Learn more about how this approach works.