An audit trail of a privileged session is a chronological record of events that provides basic information to trace all the activities performed during that session. Audit records of a privileged session may include what the event was, which user or application initiated the event (including IP address and device type), what operations were performed during the entire session, and the date and time of the event.
The need for comprehensive audit trails in IT security
Unmonitored access and its misuse is a serious problem for most systems. Capturing all the activities of privileged users is critical to identify and prevent anomalous actions that may harm business. Organizations must document the privileges granted to users, the actions performed with such privileges, and how these actions impact their IT environment. Traditional approaches to logging user activities cannot fully meet these requirements.
Audit trails help in identifying suspicious behavior. Through real-time monitoring and automated audit logs, administrators can identify system implementation issues, operational issues, unusual or suspicious activities, and other system errors.
Various compliance standards, like HIPAA, SOX, and PCI DSS, expect organizations to monitor and capture all actions performed by privileged accounts.
Facilitate regular internal audits and configure instant alert notifications
PAM360’s audit trails instantly record all events around privileged account and key activities, login attempts, and scheduled or completed tasks. This data helps in complying with regular internal audits and forensic investigations, demonstrating who accessed what resource or files, where, when, and why.
Only an administrator can view all the actions performed by other users. You can notify users of their activities through in-product notifications. PAM360 also lets you send instant email notifications to specific recipients when certain events take place.
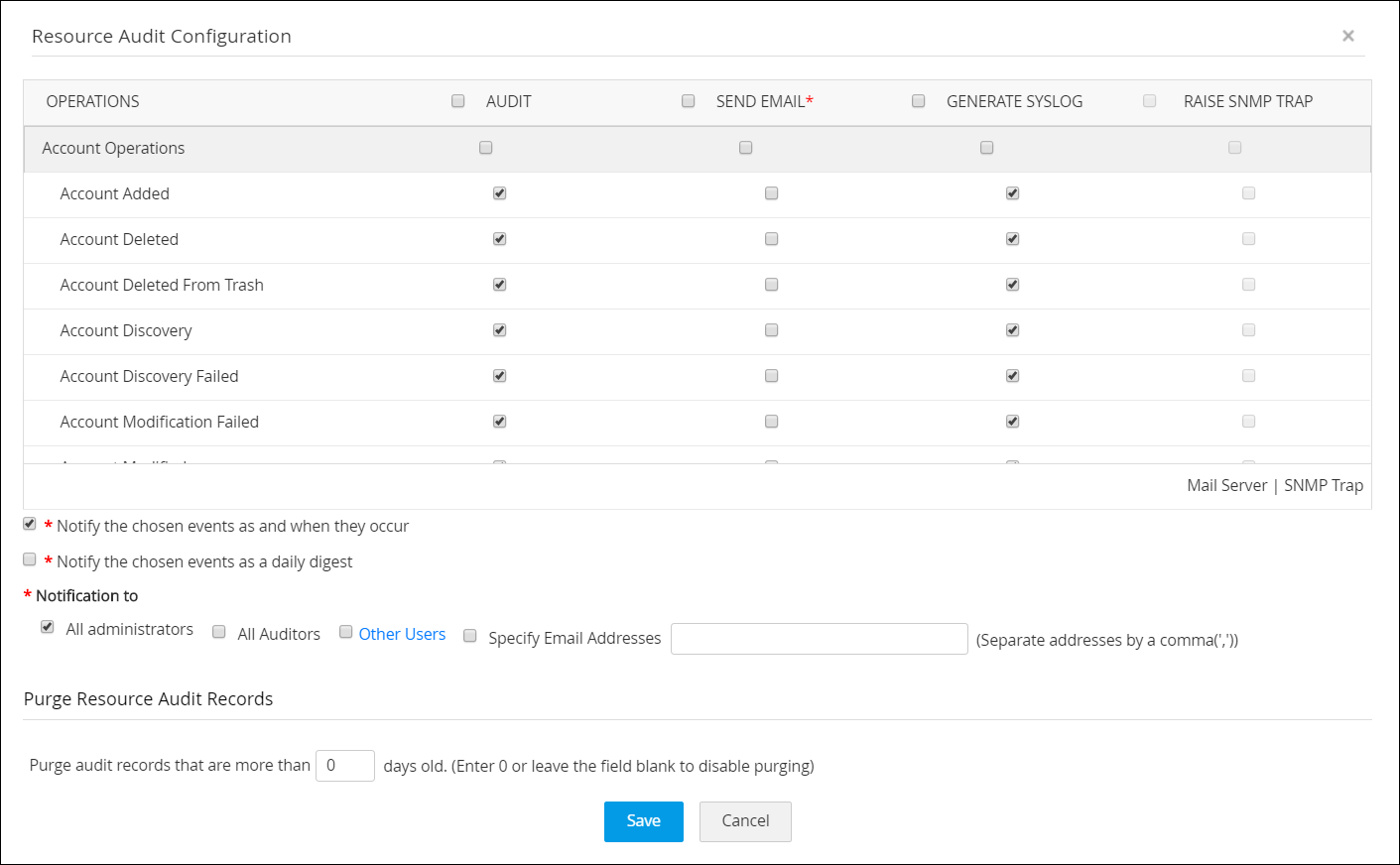
Demonstrate compliance easily with tamper-proof audit trails
Regulatory statutes such as HIPAA and SOX mandate proper maintenance of electronic records and require implementation of mechanisms for proper compliance and auditing. PAM360 provides immutable audit logs that can be shared with auditors to demonstrate compliance.
Send syslog messages and SNMP traps to your SIEM and network management systems
If you use a third-party security information and event management (SIEM) tool in your organization, you can integrate PAM360 with the tool to send syslog messages for the various events that occur within PAM360. You can also integrate your network management tool with PAM360 to receive SNMP traps.
These tools analyze and correlate privileged access data with other event data sourced from across the enterprise, helping security teams acquire a holistic view of privileged access and gain insights into suspicious activities.
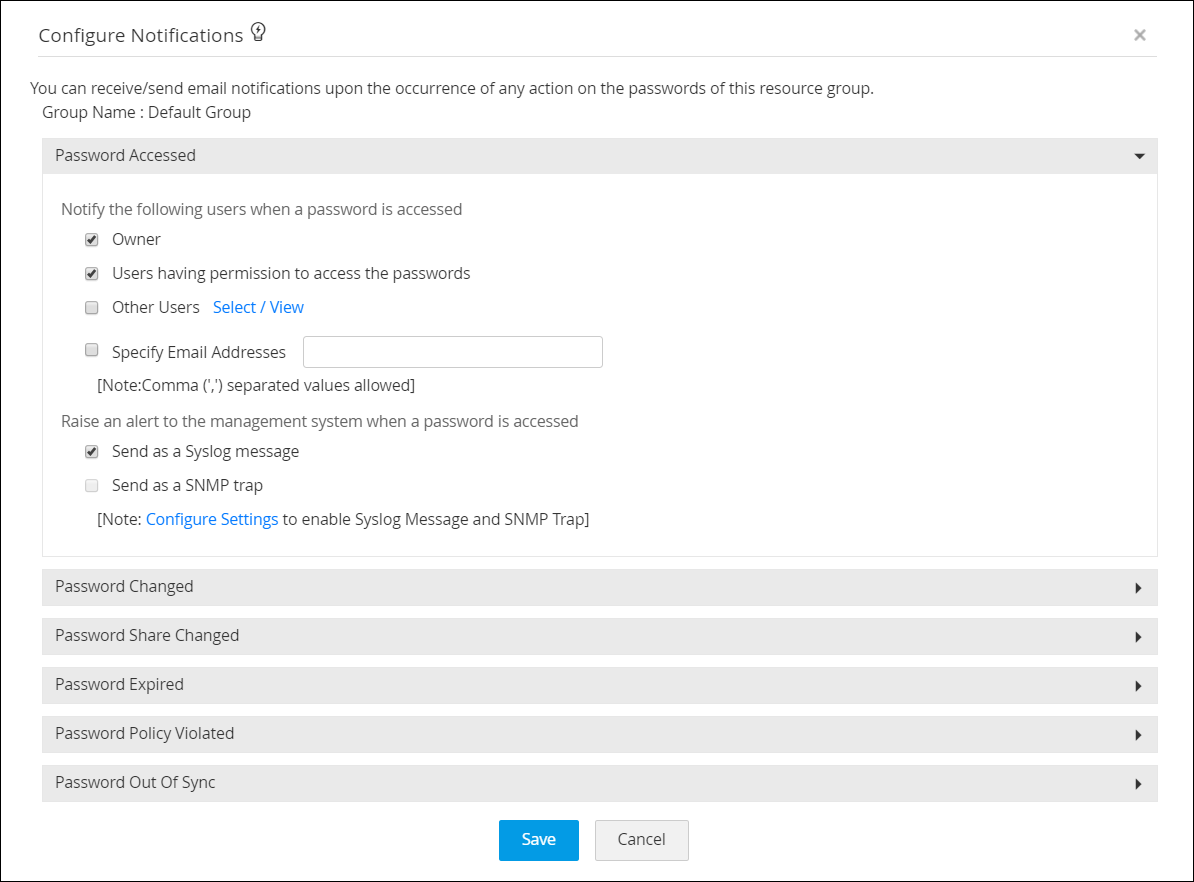
Purge audit trails regularly to avoid storage clutter
If your organization is large, the captured audit logs will naturally grow at a faster rate. You can purge audit logs that are older than a specified number of days to keep the disk space free. You can also store these logs in the local drive, and move or delete them as required.