IT security is a steady and continuous process. Hackers employ new methods of attack to breach privileged data, which requires security teams to stay on top of emerging threat and attack trends to preempt any suspicious user activity. Thankfully, SIEM tools aid in analysing event logs sourced from multiple endpoints and assets, which provides deeper understanding of threats and their sources. This allows security teams to identify and eliminate blind spots and security loopholes, and take necessary steps to fortify them before they can be breached.
ManageEngine PAM360 includes SIEM integration capabilities to periodically feed privileged access data to log management tools. SIEM tools will then analyze and correlate this information with other event data sourced from across the enterprise to detect and gain valuable intelligence about suspicious activities. This helps IT teams make informed security decisions to prevent breaches and privilege abuse.
How does the integration work?
PAM360 integrates with SIEM tools, such as ManageEngine EventLog Analyzer, Splunk, Sumo Logic and other Syslog collectors, to consolidate and process events logs sourced from privileged sessions and resources.
This integration includes options to generate SNMP traps and/or syslog messages in the event of an anomalous activity within your IT infrastructure. These syslog messages and SNMP traps can then be sent to any third-party SIEM solution, which offers thorough analysis and correlation of the event data provided by PAM360. The correlated data is then fed back into the PAM360 console, and users can derive the event information from the interactive dashboards under the 'Advanced Analytics' tab.
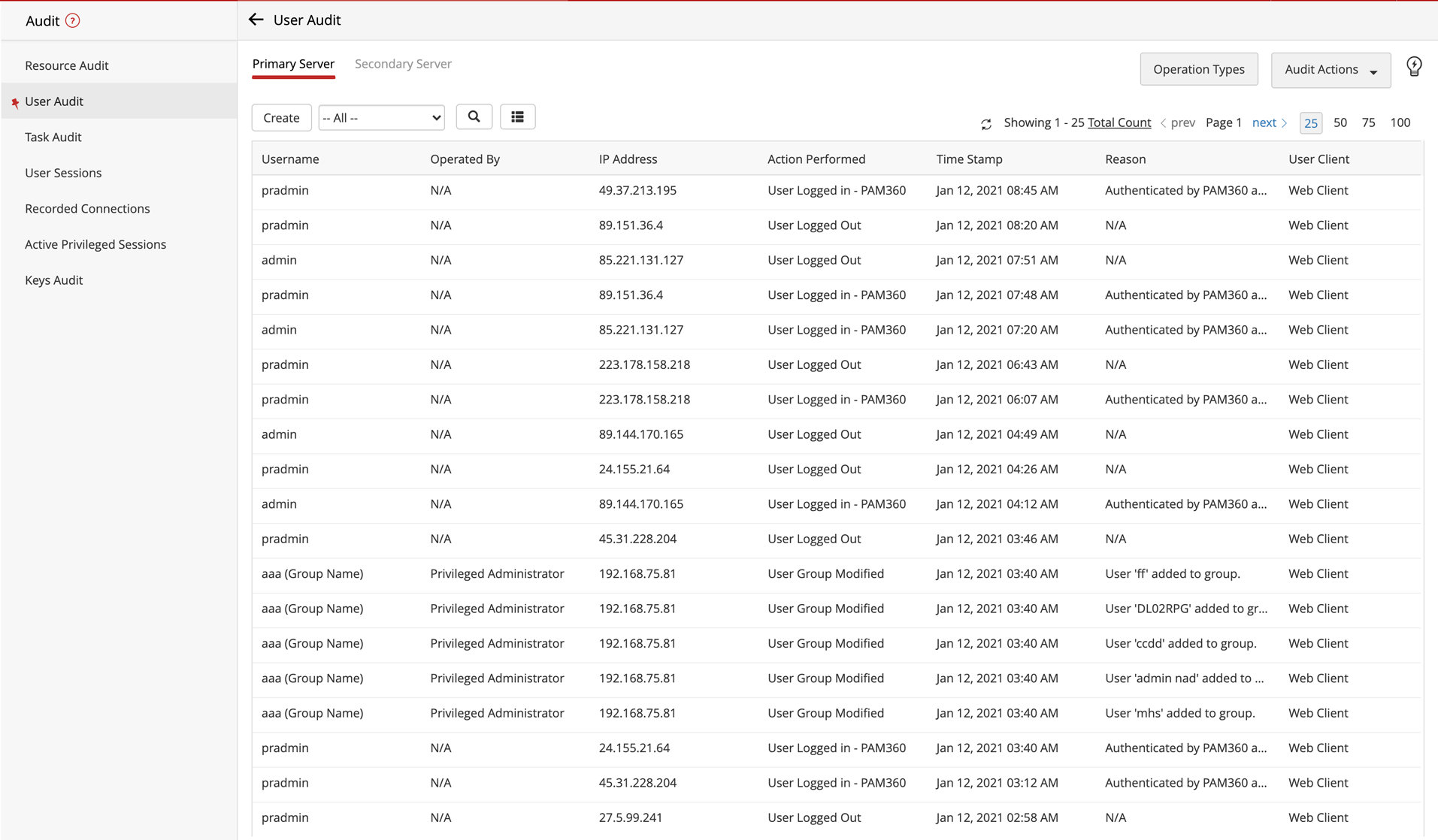
PAM360's integration with third-party SIEM tools offers real-time consolidation and correlation of user activities, assets and threats to continuously identify and isolate bad actors. Additionally, this integration provides security teams with deeper context and insight on how privileged accounts are distributed, interlinked and accessed throughout your organization, which adds an additional layer of security to your defence strategy. This way, IT teams can channelize their time and efforts into analyzing the root cause of security incidents, and mitigating threats by planning the essential precautionary and remedial actions.
Key benefits of this integration include, but are not limited to:
- Consolidating the holistic view of user activities from a central console.
- Correlating events reported by PAM360 with events generated from other applications and devices to derive actionable intelligence contributing to the root cause of security events.
- Detecting anomalies by reviewing and comparing real-time event data with the historical data.
- Building a credible knowledge base containing niche information about existing anomalies derived from past events to plan appropriate incident response measures, which helps in mitigating insider threats and abuse of privileged assets.
For more details about the integration, please click here.