Anomalous activities can often go unnoticed when they happen in silos. These activities can range from multiple failed login attempts to access from unauthorized IP locations. While such isolated events might not raise any red flags on their own, they create a cause for concern when looked at in unison. Without the right approach, differentiating potential threats from valid actions performed by privileged users is difficult. PAM360's Trust Scores address this by helping businesses take an adaptive Zero Trust approach to privileged access management.
PAM360 generates dynamic trust scores for users and devices based on their compliance with security policies. If the baseline score isn't met, admins can enforce automated actions that can terminate or deny access to users, request valid reasons to access resources, and much more. These scores help enterprises profile anomalous activities and act on them immediately.
Get started with Zero Trust privilege
PAM360's approach to Zero Trust involves customizable trust scores for devices and users. You can set customizable trust scores for a variety of factors based on your organization's security policy or key parameters. PAM360 will weigh each risk factor based on its individual scores and formulate a cumulative trust score out of 100. You can use this score to trigger custom actions in real time.
Identify trusted users
Monitor a wide range of risk factors based on user actions. User trust scores can be scrutinized based on factors such as access location, time of access, and other privileged factors.
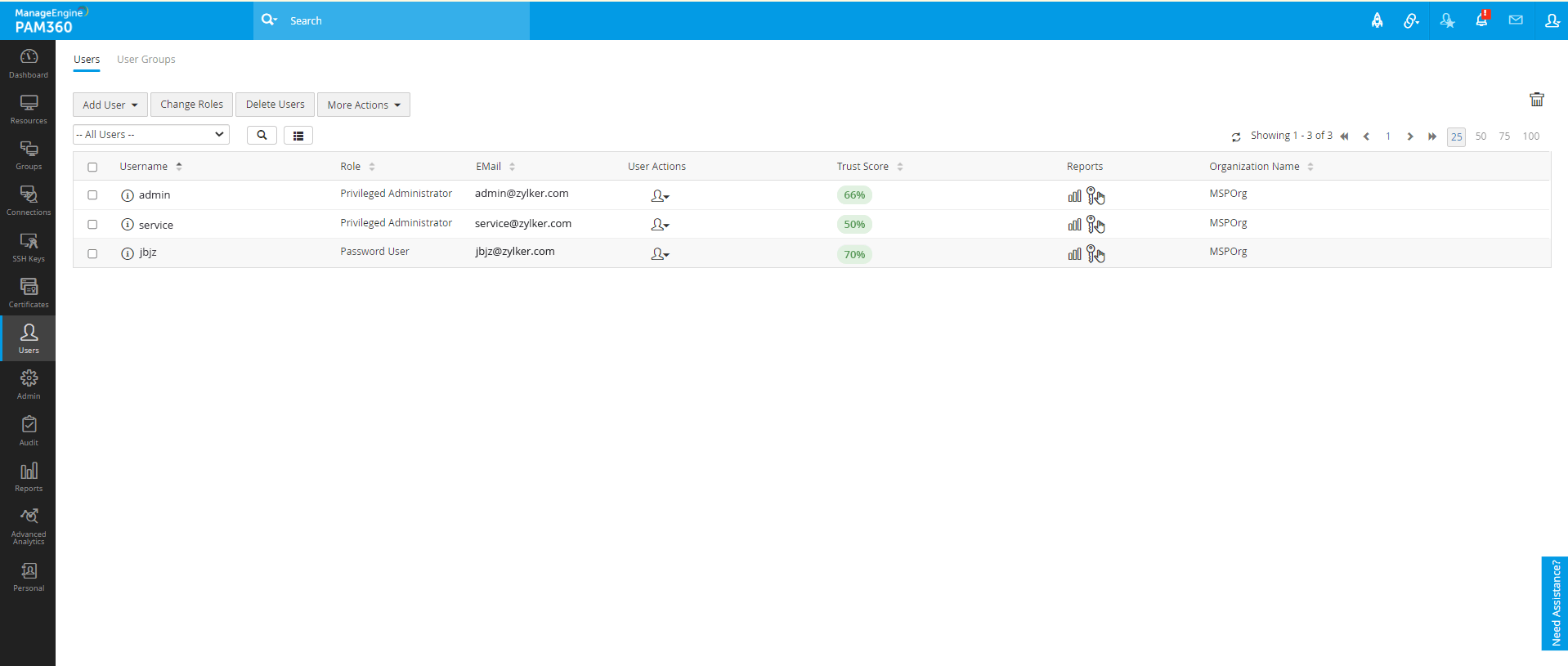
Isolate non-compliant devices
Devices can be audited to grant user access only when they're compliant with security policies. Set custom trust scores for a range of factors that assess if the device is up to date, has a secure login mechanism in place, and various other factors.
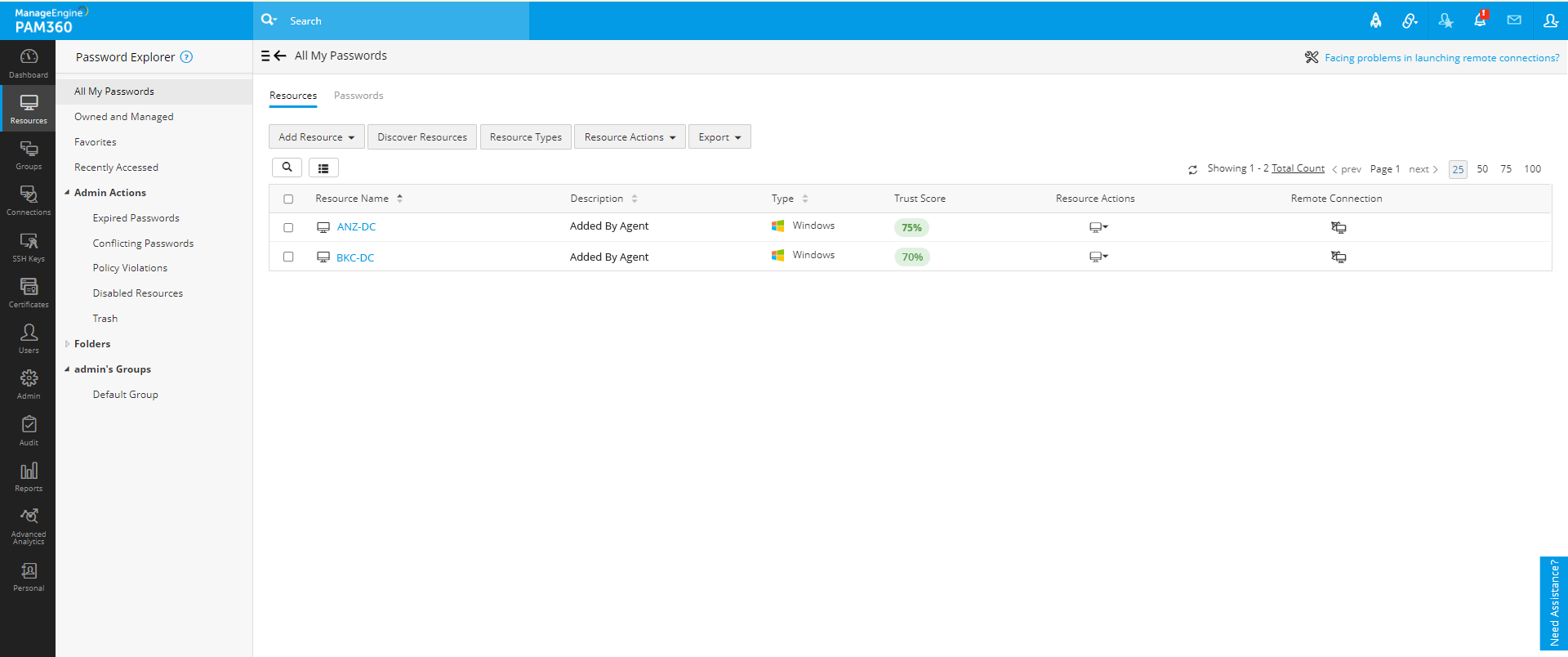
Dynamic, real-time scores
Trust scores formulated by PAM360 are adaptive and get updated in real time based on current user actions. This gives you an accurate depiction of the trust posed by any user or device in your organization and helps you make informed decisions.
Trigger automated actions
Set custom workflows that can be initiated when scores cross a threshold in real time. For example, you can terminate sessions of users with a trust score less than 90, restrict RDP access for users with low scores, restrict user authentication on non-compliant devices, and much more.
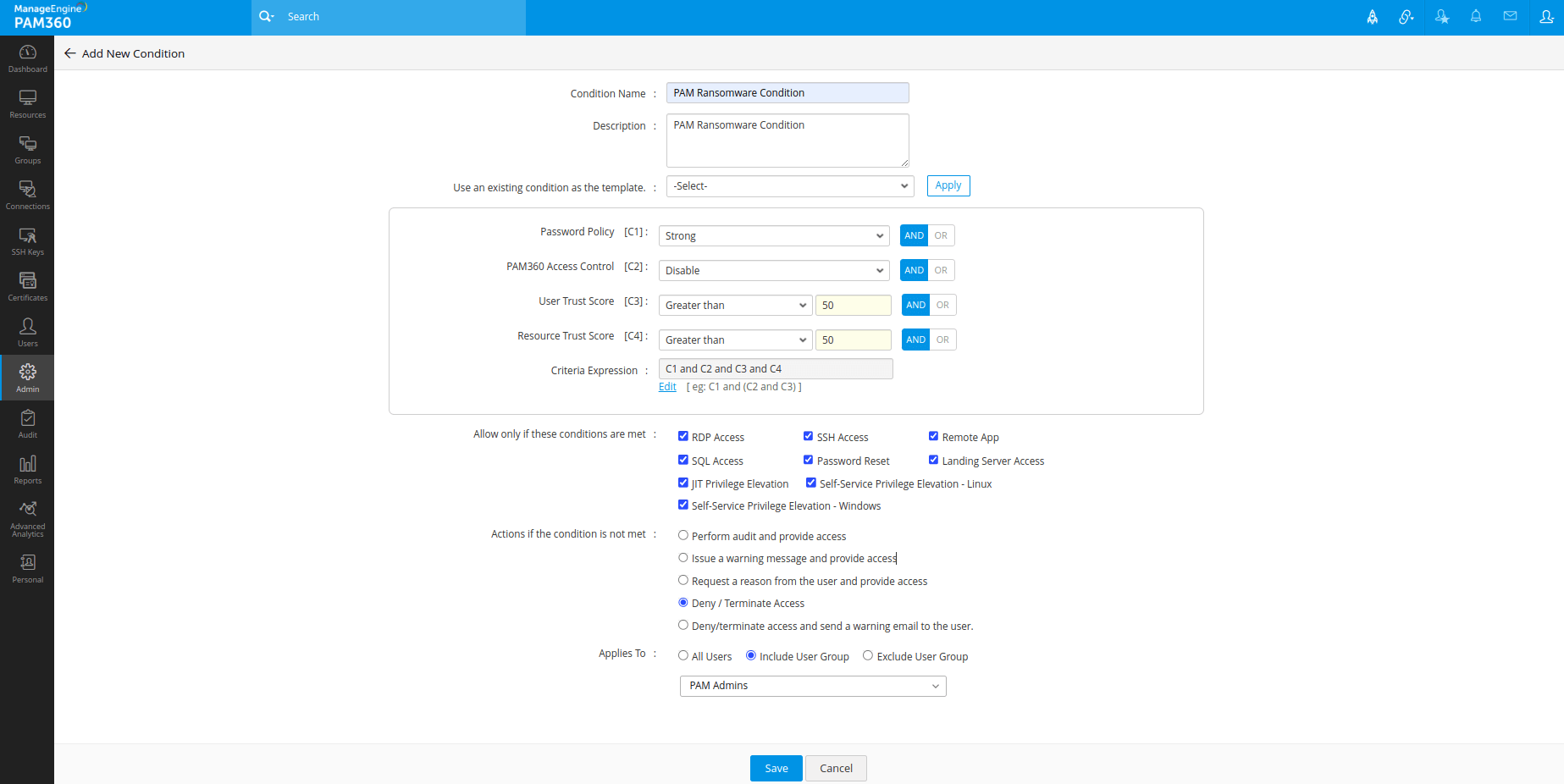
Take a Zero Trust approach to privileged access management with PAM360
PAM360 employs Zero Trust principles across all functions of privileged access management. From limiting user access with role-based access control to limiting privileged access with just-in-time privilege elevation, we take a Zero Trust approach across every aspect of PAM.