How does PASM work?
The primary purpose of any PASM solution is to monitor and protect privileged user accounts and sessions, which helps IT teams track, control, record, and audit access to critical information and endpoints.
The two key focus areas of a PASM tool include:
Privileged account management

More often than not, some users are provided with elevated privileges, i.e., they have more privileges than required to perform their activities. As a result, there is always a gap between the required permissions and granted privileges.
Further, when these over-privileged users leave the organization, it takes IT teams a while to deprovision their accounts and revoke the privileges associated with them. In the meantime, a malicious insider could gain access to these orphaned accounts and exploit these privileges to gain unfair advantage over sensitive data. In such instances, a PASM solution proves effective in eliminating any unmanaged standing privileges.
PASM tools come with am encrypted vault that allows IT teams and other administrative users to store and manage privileged identities, such as user accounts, passwords, SSH keys, PKI certificates, and other authentication data.
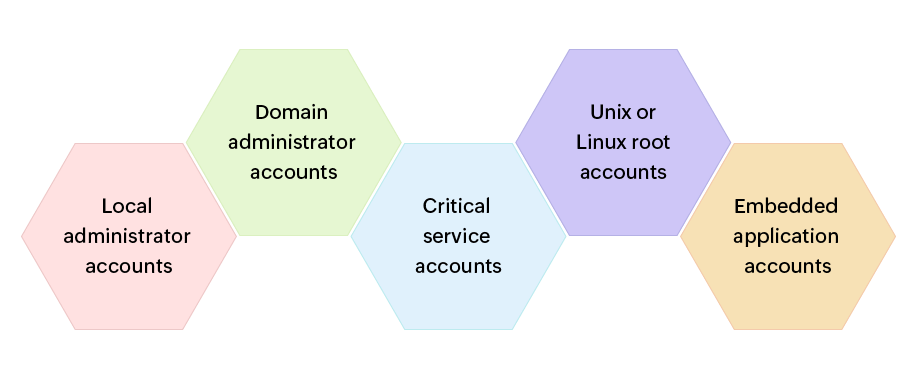
Here's a quick snapshot of the types of privileged accounts:
Further, PASM tools offer robust controls, such as:
- A secure and dynamic vault to store and manage credentials, certificates, files, and keys.
- Request-release workflows for validating and approving password access requests.
- Role-based access provisioning for administrative privileges.
- Real-time monitoring and auditing of password-related user activities, such as login attempts, password resets, and password policy changes.
- Scheduled password rotation for privileged endpoints.
These tools work on the principle of least privilege (POLP), where users are granted minimal and sufficient access privileges to perform their usual tasks. For tasks that require higher, administrative privileges, users will have to present appropriate approvals to gain administrative access to classified data. Furthermore, PASM solutions include built-in privilege elevation controls with which IT teams can ensure that access to privileged accounts and assets can be provisioned on a case-to-case basis.
In other words, instead of granting permanent higher privileges, IT teams can provide users with access to privileged resources for a specific period. Upon expiry of the requested time frame, access to these resources will be revoked, and original (and minimal) user privileges will be reinstated.
Privileged session management
PASM solutions include exclusive session management controls to facilitate secure access to remote endpoints, such as applications, data centers, databases, operating systems, network devices, and cloud storage.
While VPNs serve the purpose of offering a secure gateway between two remote machines, PASM tools go a step further by providing more versatile and contextual capabilities such as session recording, monitoring, shadowing, termination, auditing, and file transfers. This enables IT teams to monitor and control user sessions in real time, and also to terminate any suspicious user sessions.
PASM's session management feature enables IT teams to spot unauthorized sessions and effectively terminate any anomalous user activities. In addition, privileged session management offers a detailed, unalterable audit trail that typically contains the essential insights of the what, who, and when of every session, which can further be used for forensic investigations and security audits.

Furthermore, PASM tools apply the POLP at the device level, where non-administrative users without appropriate privilege elevation approvals will not be granted access to critical endpoints. In other words, only users with valid requirements will be provided with temporary administrative privileges to perform their tasks, and once their job is completed, their ephemeral privileges will be revoked and the credentials of the resources will be automatically rotated to prevent any unauthorized access attempts in future.
The following are some standard session management capabilities to look out for while considering a PASM solution:
- Live session collaboration, shadowing, and termination
- Session recording, archival, and playback
- Secure remote access provisioning
- Comprehensive audit trails, logging support, and reports
Why should organizations implement a PASM solution right away?
A privileged account in the wrong hands is the perfect recipe for disaster. While cyberattack methods are constantly evolving, it is more often a simple misuse of administrative accounts or weak credentials that is enough to put an organization at the center of a massive breach. All the recent cyberattack trends prove the fact that attackers typically choose to keep it simple, and passwords happen to be the lowest hanging fruit when it comes to data breaches.
Lax password management, such as reusing and sharing privileged credentials, could expose an organization to bad actors. Manual management of passwords is not only tedious but also a dicey affair owing to the fact that any negligent insiders could expose the credentials to attackers. Privileged credentials, when handled by criminals, could open the floodgates to business-sensitive data worth thousands to millions of dollars.
Having said that, a strong PASM solution can help IT teams in securing and streamlining their privileged access routines. PASM solutions enable admins to have centralized control over their privileged users, accounts, and assets, and can ensure that the credentials for these accounts are reset periodically and masked from non-administrative users unless a valid request for access is presented.
Further, these tools provide extensive, real-time audits of privileged user activities, which help IT teams identify and eliminate security blindspots and vulnerabilities to preempt any imminent attacks while also staying compliant with industry standards. Another good reason to switch to a PASM solution is its relevance across business functions, which makes it a versatile and industry-agnostic addition to any organization.
To put things in perspective, PASM not only helps you lock the door but also helps you hide the key to your sensitive information.
Here are the top business benefits of deploying a PASM solution:

Granular visibility over privileged accounts: Get a holistic view of user activities across your enterprise networks with comprehensive audit trails, and alerts about privileged account usage.
Strengthen overall access governance: Besides providing fine-grained access, PASM solutions also include controls to monitor and control geographically-distributed enterprise resources. Real-time monitoring of remote sessions improves overall transparency, and empowers IT admins to prevent insider attacks through live session recording and shadowing.

Proactively secure against insider threats: Identify anomalous behavior, block suspicious users, and prevent security incidents with effective, real-time insights on user sessions. Enforce role-based access controls to ensure only privileged users have administrative access to sensitive information.
Ensure effective compliance with industry regulations: Seamlessly prove compliance with various regulatory standards and government laws, such as the GDPR, HIPAA, PCI DSS, NERC-CIP, and SOX.

Enable granular access to external stakeholders and third parties: A compromised vendor or an outsourced employee who has access to privileged credentials could become a weak link, and can increase the chances of a cyber incident. However, with a robust PASM tool in place, admins can leverage smart access workflows that enable seamless provisioning of temporary, passwordless privileged access for third parties to access specific business systems and applications.
Essential PASM features to look for in a PAM solution
It is important for IT teams to make a prudent choice when it comes to choosing a PAM solution. Here is a list of core PASM capabilities that every PAM solution should include:
- An enterprise credential vault that is fortified with multiple levels of data encryption, both at rest and during transit
- Strong multi-factor authentication with options like AD or LDAP, RADIUS, SAML, and smart card
- Automatic discovery of privileged accounts, users, and resources on a periodic basis
- Granular password sharing options, role-based access provisions, and request-release workflows for password release
- Secure APIs to facilitate application-to-application communications for automatic password checkouts
- Support for periodic password resets and integrity checks; password reset support for a wide range of resources including Windows and Linux machines, network devices, virtualization devices, and DevOps and RPA tools
- Privileged session monitoring and secure remote access provisioning
- Real-time session monitoring, recording, and playback
- Extensive session audit trails, and comprehensive logging and reporting options
- Support for managing the life cycle of SSL and TLS certificates and SSH keys
How to include PASM in your overall PAM strategy
Here are some recommendations for you to get a head start on implementing a PASM strategy in your organization:
Conduct a thorough audit of all administrative accounts and their corresponding privileges
Assign default, least privileges for user accounts, which should ideally be set as minimal as possible

Implement just-in-time (JIT) privilege elevation controls to enable time-bound access to critical resources

Identify inactive and orphaned user accounts, and revoke all their associated privileges

Record and audit privileged activities and sessions across the enterprise

Enforce multi-factor authentication as an additional layer of security to your privileged accounts

Educate your workforce about the perils of lax privileged access hygiene by conducting periodic cybersecurity training, since the human element is one of the biggest risk factors when it comes to insider threats
Implementing an effective PASM routine with ManageEngine PAM360
ManageEngine PAM360 is an enterprise privileged access management solution that enables IT teams and administrative users to establish strict governance and gain granular control over critical user accounts and corporate resources.
PAM360's PASM module is loaded with niche features to help you effectively control and monitor access to critical data. Some of the robust PASM capabilities of PAM360 include:
- A secure enterprise credential vault for passwords, digital signatures and certificates, license keys, documents, images, service accounts, and more, which is fortified with AES-256 encryption.
- Granular role-based access provisioning for regular users and third-party contractors.
- Smart request-release workflows to validate and approve password access requests.
- Advanced JIT privilege elevation controls to provision time-limited, temporary access to privileged resources to non-administrative users.
- Real-time notifications and alerts about password-related activities to spot and preempt abnormal actions, thereby ensuring enhanced incident response.
- Seamless session monitoring, recording, and sharing to help admins keep tabs on live user sessions, and also to terminate suspicious activities instantly.
- A comprehensive auditing and reporting module that provides detailed audit trails and extensive reports on password access activities and privileged sessions, which aids in identifying the root cause of credential abuse and insider threats during security audits.
- Effective and continuous compliance with regulations, such as ISO 27001, HIPAA, the GDPR, SOX, and PCI DSS, which can help your organization adhere to industry standards.

