Direct Inward Dialing: +1 408 916 9892
The first step in safeguarding your organization's network and resources is monitoring your employees' logon activity. Tracking users' logon patterns can help detect logons occurring at unusual times, logons to unauthorized hosts, and other suspicious activities. It also helps sysadmins detect and respond to sudden spikes in failed logon attempts, as such attempts indicate the possibility of a brute force attack. Read on to see how to enable auditing of account logon events.
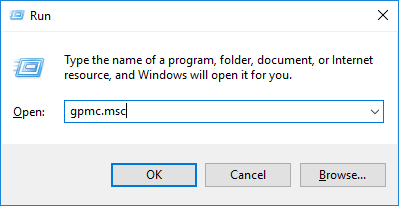
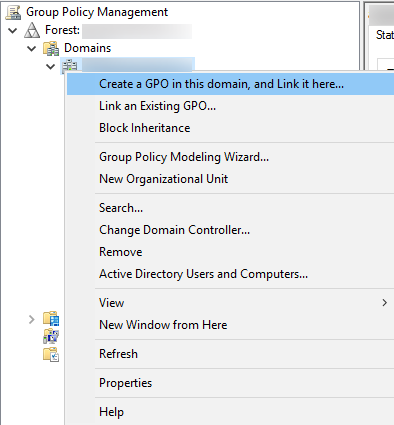
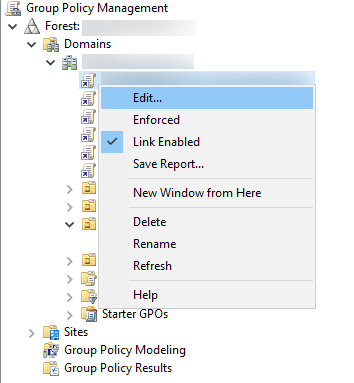
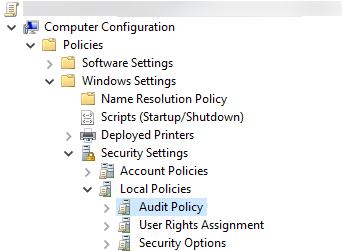
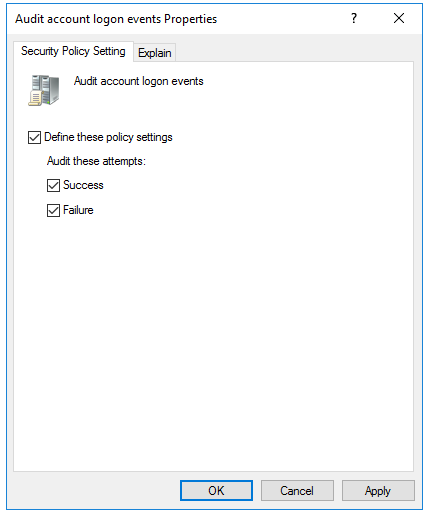
Once this policy is enabled, events are logged on Domain Controllers' (DC) security log whenever a logon is validated by the DC.
Once the above steps are complete, account logon events get recorded as event logs under various Event IDs. These events can be viewed in the Event Viewer by following the steps below:
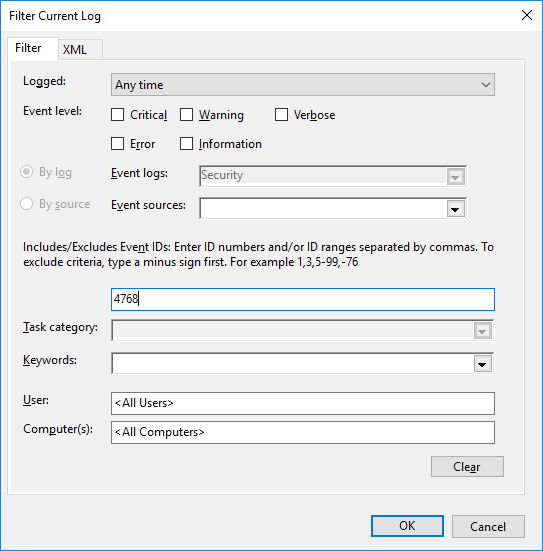
*The following Event IDs are generated for the given events:
| Event ID | Subcategory | Event Type | Description |
|---|---|---|---|
| 4768 | Kerberos Authentication Service | Success and Failure | A Kerberos authentication ticket (TGT) was requested |
| 4769 | Kerberos Service Ticket Operations | Success and Failure | A Kerberos service ticket was requested |
| 4776 | Credential Validation | Success and Failure | The computer attempted to validate the credentials for an account. |
Note: By default, only successful logon attempts are audited. Failed attempts can be audited by enabling it in Advanced Audit Policy Configuration.
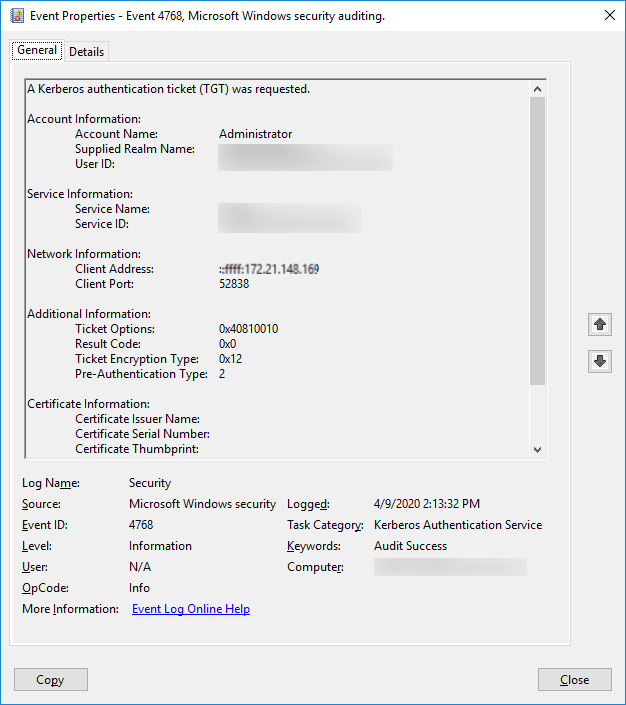
As you can see, getting a comprehensive overview of all the logons occurring in your network is impossible using native auditing to keep track of each event as it occurs. An administrator would have to search for the Event ID and view each event's properties. This is highly impractical.
ADAudit Plus monitors user logon activity in real time and provides in-depth reports. You can also get alerts for unusual logon activity and automate a response for them. ADAudit Plus provides all these features and much more to safeguard your Active Directory.
After we enable auditing, as an alternative to using Event Viewer, we can use ADAudit Plus, an AD auditing tool, to monitor logon events in real-time and view informative reports on them.
Click on details to open Logon Failure Analyzer for that user. This shows the possible reasons the attempt failed.
View top logon failures for a custom time period and view events that occur during business or non-business hours.
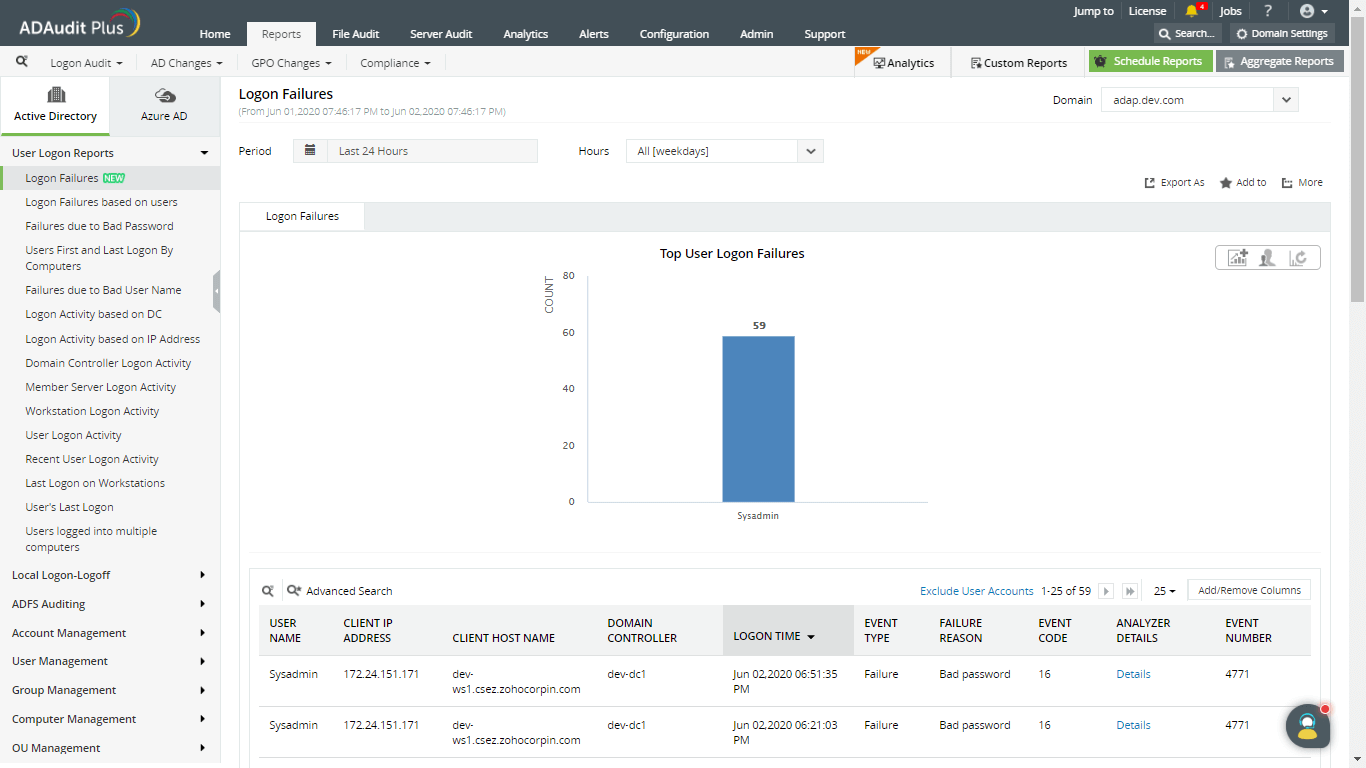
View logon activity on business or non-business hours.
Add trusted users to the "exclude user accounts" list to remove their data from the reports.
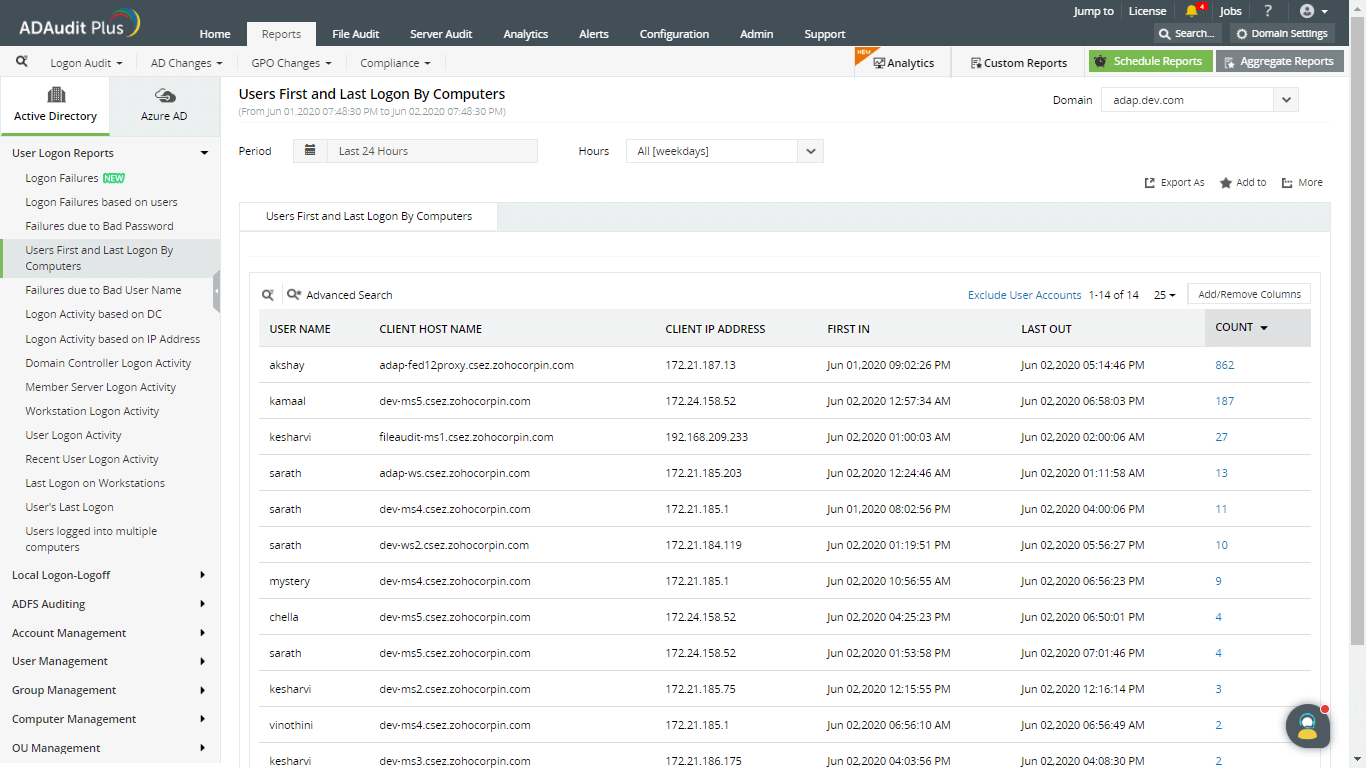
See the unusual time period and associated volume of logons.
To view more information on each anomalous activity, click on Details.
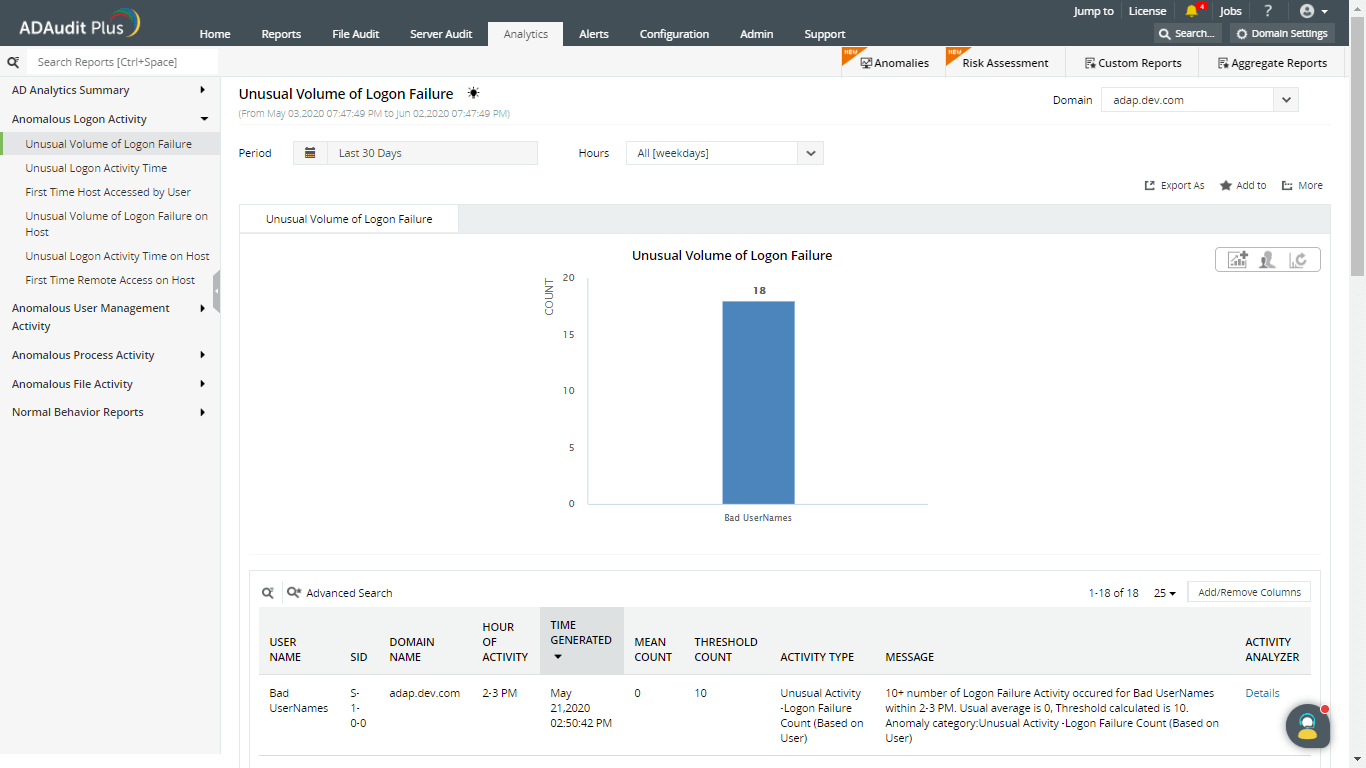
ADAudit Plus helps monitor and report on users' logon activity with ease.