Direct Inward Dialing: +1 408 916 9892
Written by Mahidhar Adarsh, IT security team, ManageEngine Updated on September 2025
Start your free trialA disabled user account could be enabled and misused by malicious agents. This is why it's essential for IT administrators to audit their AD environment in real time using Active Directory native auditing or third-party tools. This can help them identify the user that enabled the user account. Below are the steps to find who enabled a user account in Active Directory:
Perform the following actions on the domain controller (DC):
Note: If you're using a workstation, the following script should be run on PowerShell:
Get-EventLog -LogName Security -ComputerName <DC name>| Where-Object {$_.EventID -eq 4722} | Select-Object -Property *
where <DC name> is the name of the domain controller where you want to check the details of the user account that was enabled.
Through native auditing, you can search for events and keep an eye on changes made to user objects. However, this becomes impractical when you have to deal with hundreds of user accounts and need to keep track of each event as it occurs.
ADAudit Plus is real-time Active Directory auditing software that helps gain visibility into the changes made to AD objects and their attributes. Monitor each phase in the life cycle of a user account along with details on who initiated it, from where, and when.
Find who enabled a user account in Active Directory, when, and from where.
Other reports on recently created, deleted, moved, and locked out user accounts help you gain more insight into your AD user accounts.
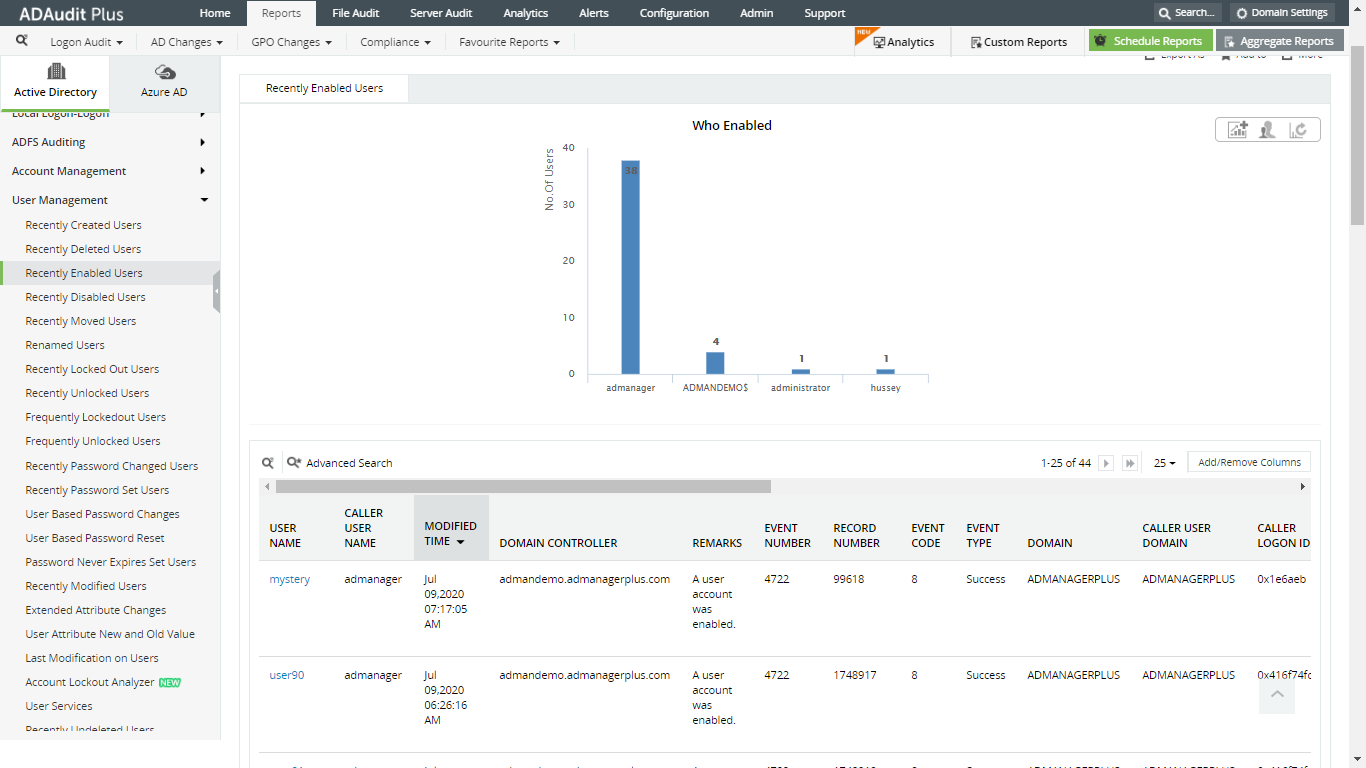
Find who enabled a user account in Active Directory, when, and from where.
Other reports on recently created, deleted, moved, and locked out user accounts help you gain more insight into your AD user accounts.