

Data encryption is crucial for enterprise network security. Managing BitLocker encryption across multiple devices is challenging, but Endpoint Central's BitLocker module offers a streamlined solution for securing drives.
The BitLocker management module allows you to create tailored encryption policies for safeguarding network devices. You can choose from full drive, OS drive, or used space encryption to optimize data protection based on individual device requirements. The module supports devices with and without TPM for authentication and offers granular control over encryption algorithms. Specific options are available for Windows 10 and later, as well as Windows 8.1 and earlier systems. This document guides you through creating and configuring these encryption settings.
You can implement encryption or decryption processes for endpoints using BitLocker policies.
NOTE - Adhere to BitLocker encryption pre-requisites before deploying an encryption policy.
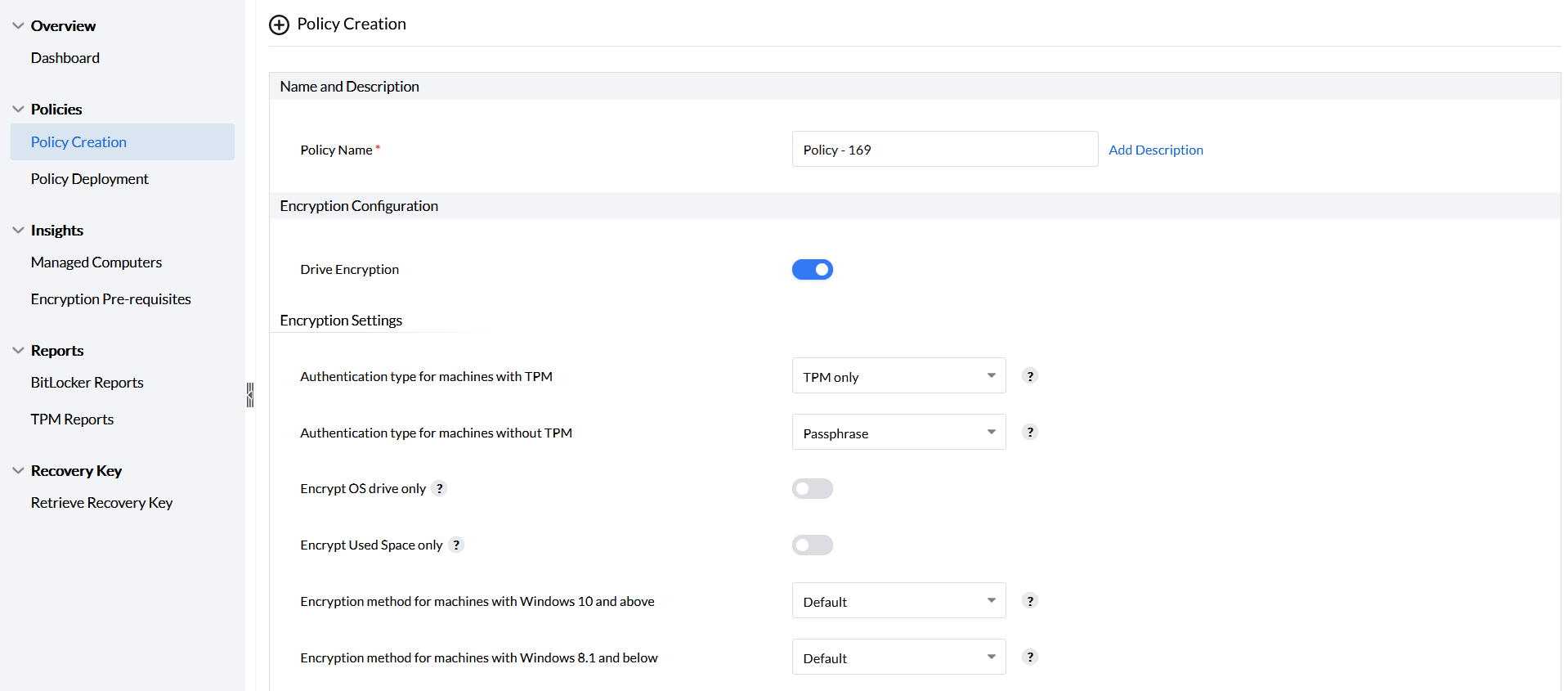
BitLocker policies safeguard devices through robust authentication, varying based on whether the machine has a Trusted Platform Module (TPM). You can optimize drive encryption by combining different algorithms: full drive encryption, OS drive encryption, or used space encryption. For added flexibility, Encryption options are tailored for Windows 10 and later as well as Windows 8.1 and earlier systems.
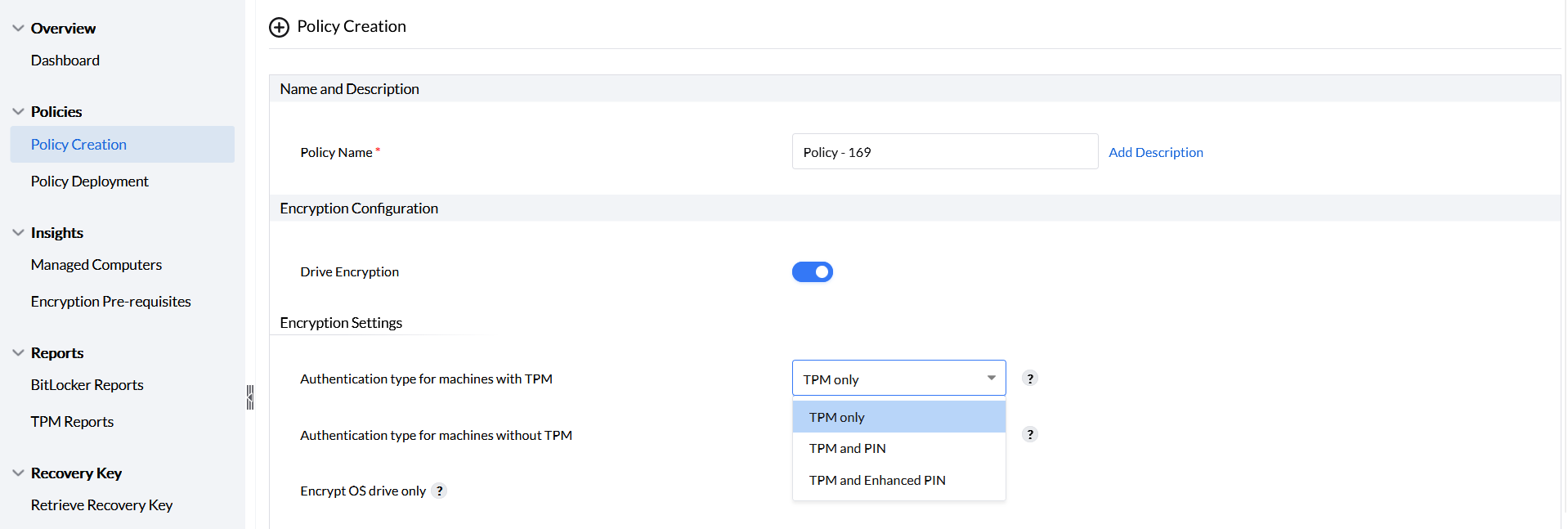
Authentication for machines with TPM can be enabled by choosing any of the three options provided as shown in the image.
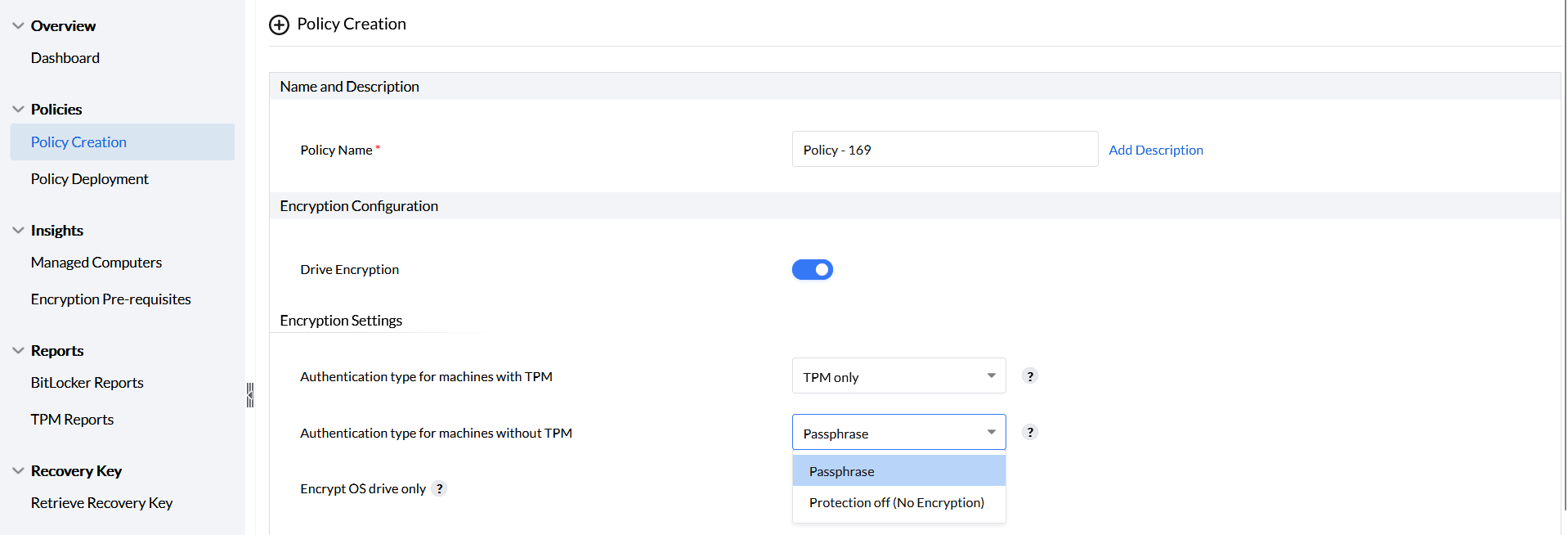
For machines without TPM, authentication is enabled only with a passphrase, prompting the user to enter it upon boot.
You can optimize drive encryption with the settings provided by BitLocker policies. You can apply policies by combining the following three encryption algorithms:
To encrypt all drives and spaces, enable only the Drive Encryption setting. Ensure that Encrypt OS drive only and Encrypt used space only options are disabled.
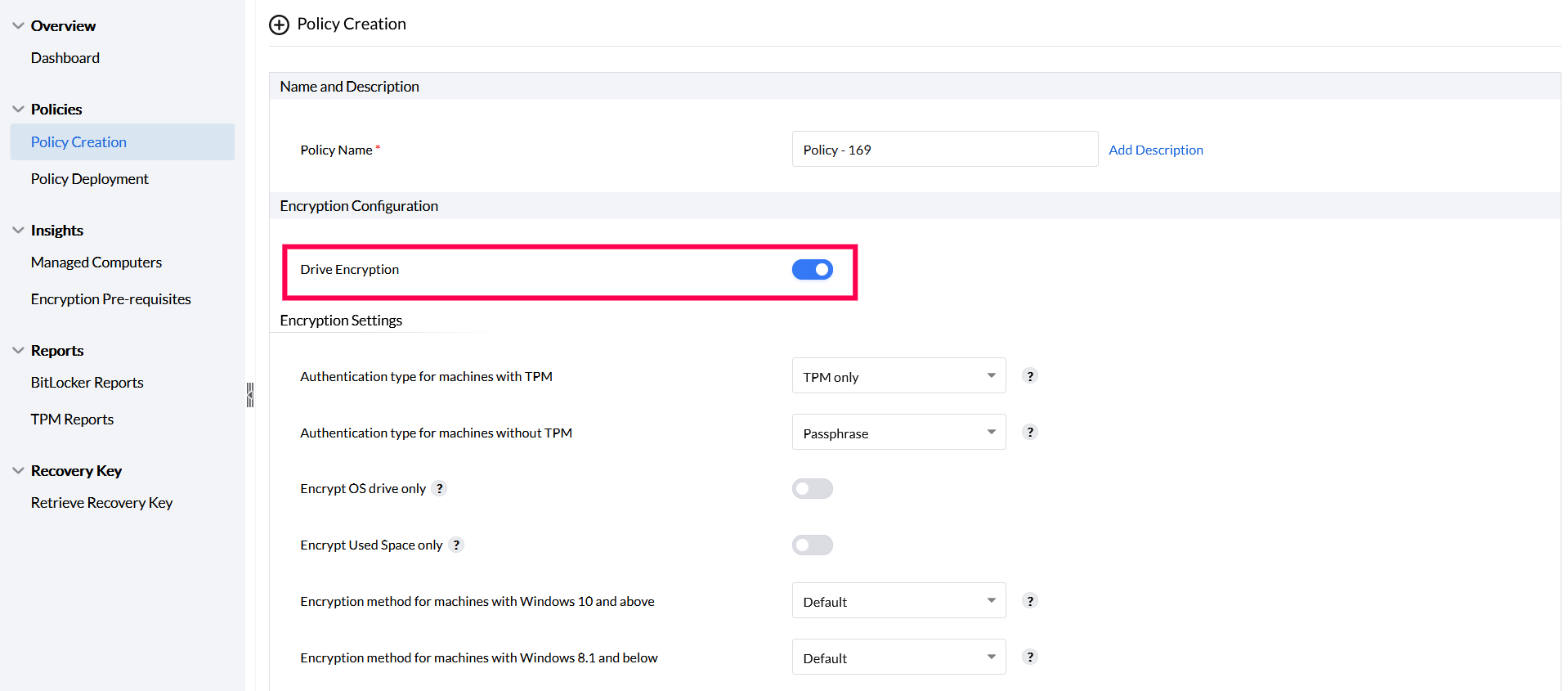
To encrypt only the OS drive, enable the Encrypt OS drive only option in the Encryption Settings. This ensures only the OS drive is encrypted while all other data drives remain decrypted.
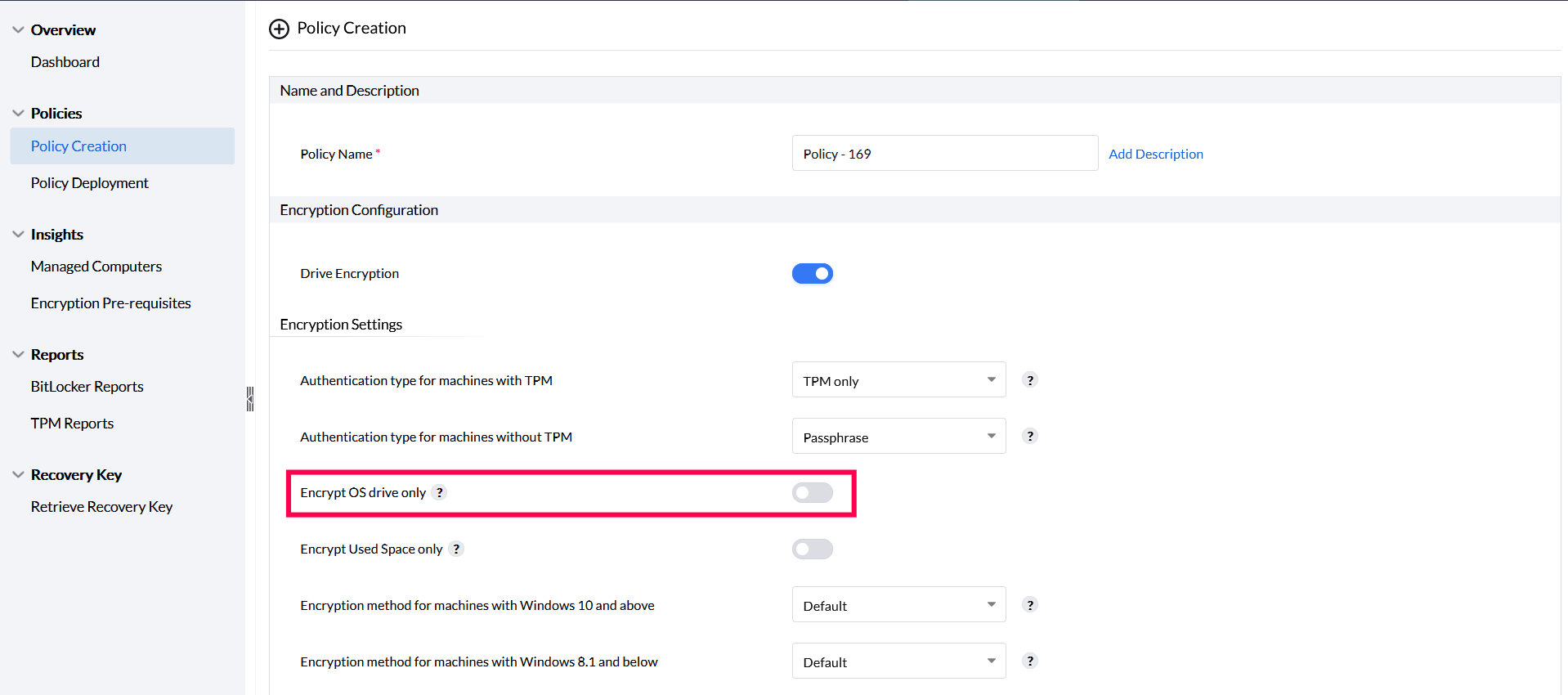
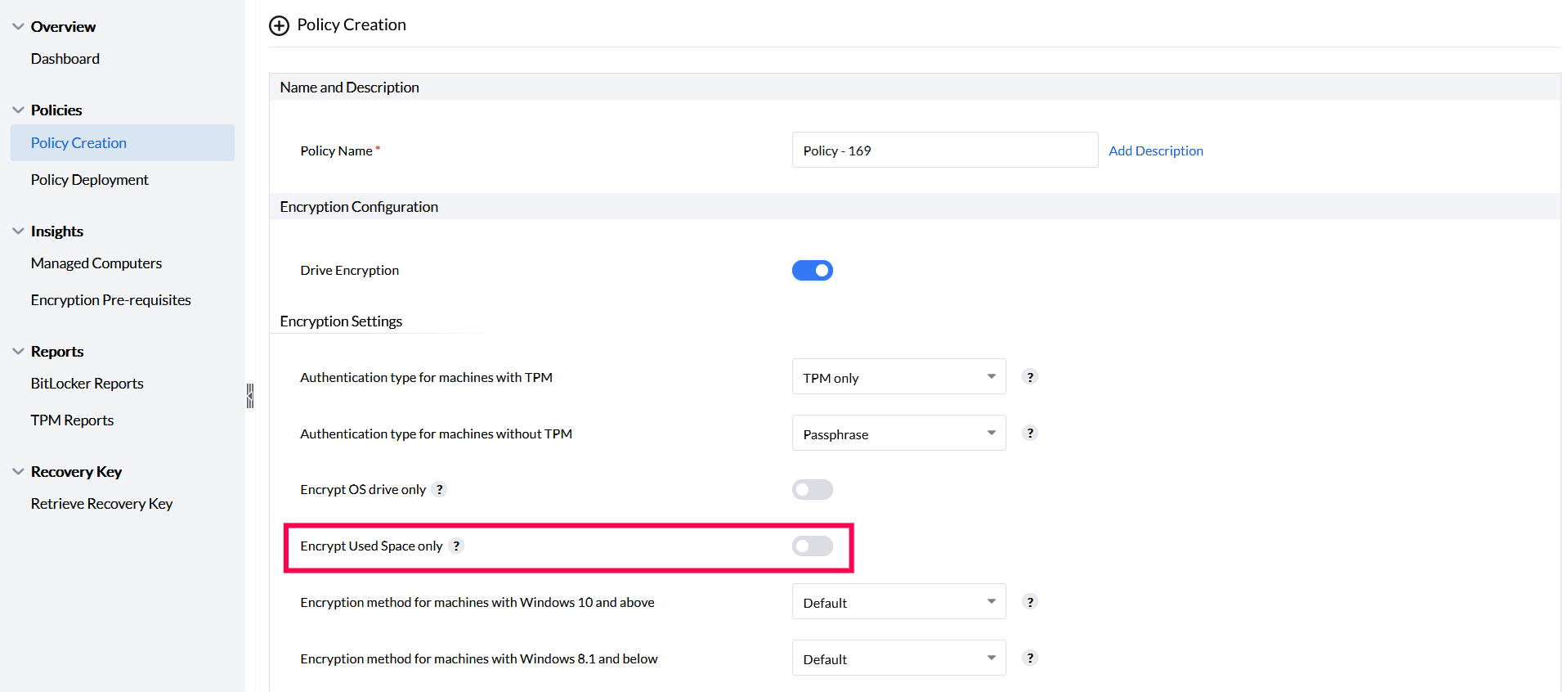
To encrypt only the used space, enable the Encrypt used space only option in the encryption settings. This will encrypt only the used space on your drives, leaving free space decrypted.
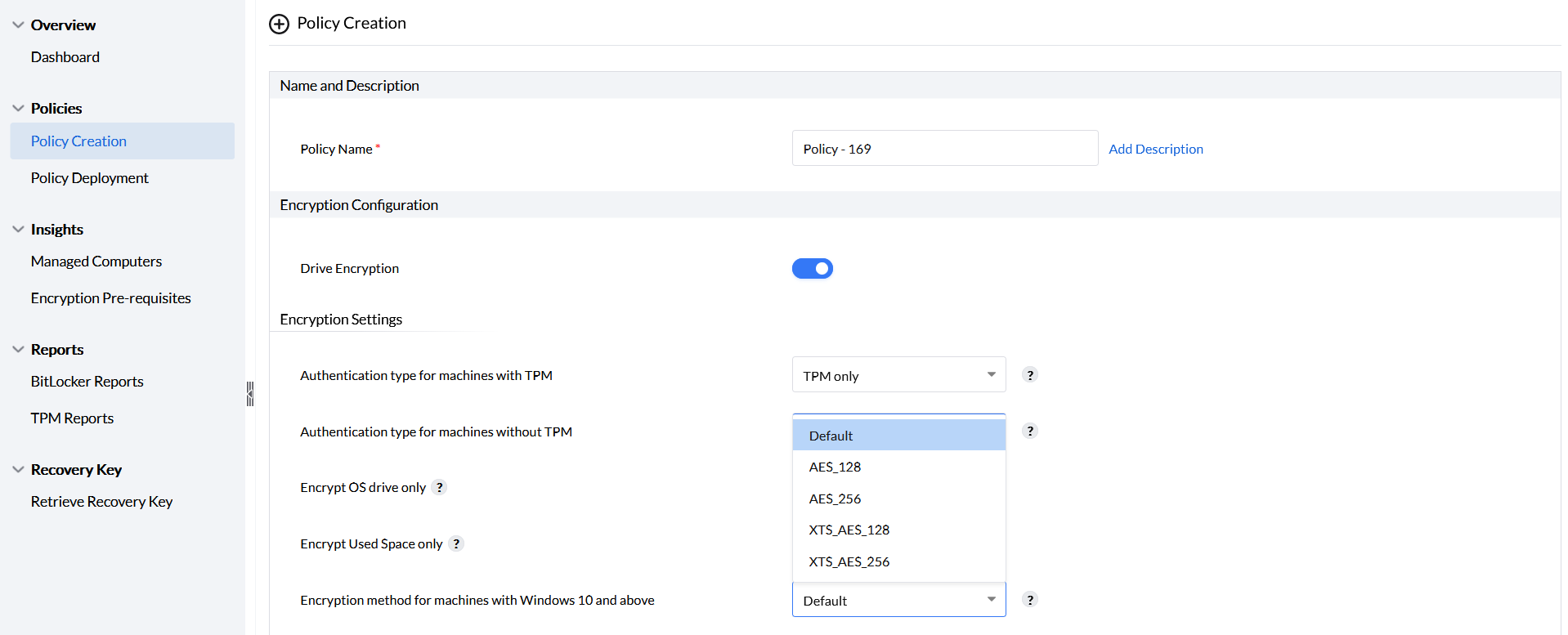
BitLocker offers settings for encrypting machines with different algorithms. Specific set of algorithms are available for Windows 10 and above and for Windows 8.1 and below. The default method is based on the previously configured Group Policy Object (GPO) or the encryption method associated with your system OS.
Available algorithms include AES_128, AES_256, XTS_AES_128, and XTS_AES_256. For optimal performance, use Microsoft’s default encryption. Stronger options exist for compliance needs, but be aware that they can slow down your computer.
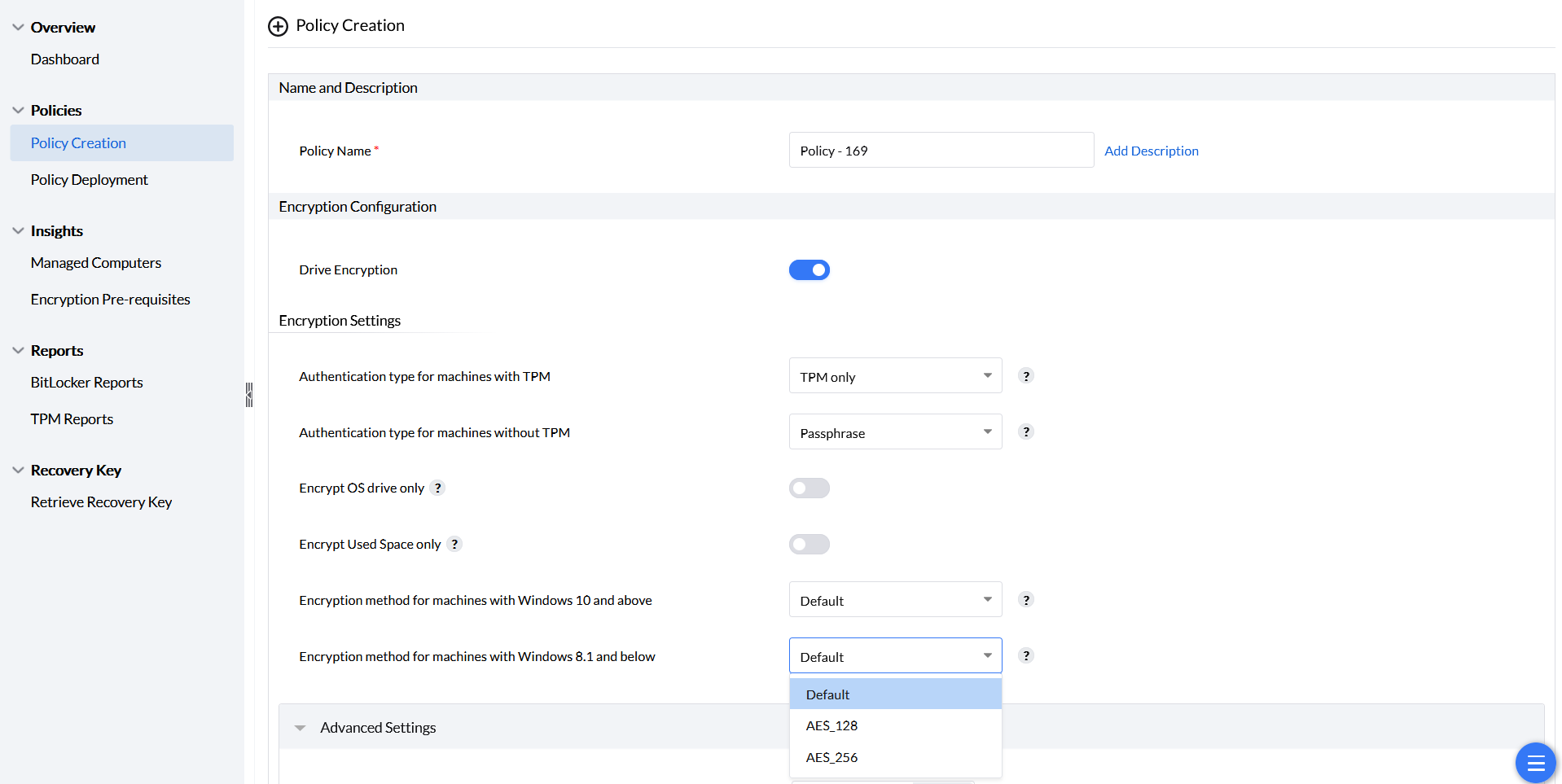
Available algorithms include AES_128 and AES_256. For optimal performance, use Microsoft’s default encryption. Stronger options exist for compliance needs, but be aware that they can slow down your computer.
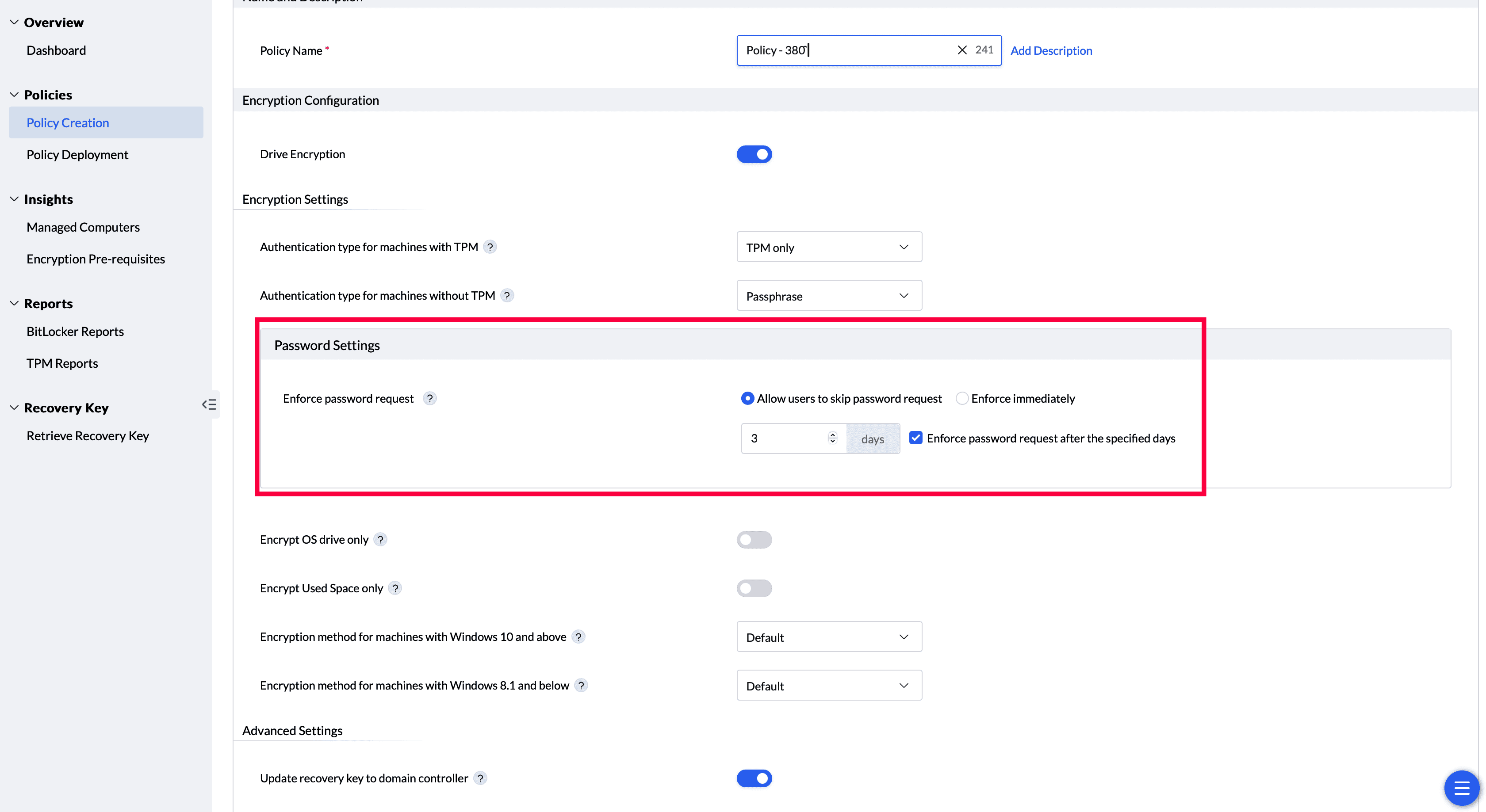
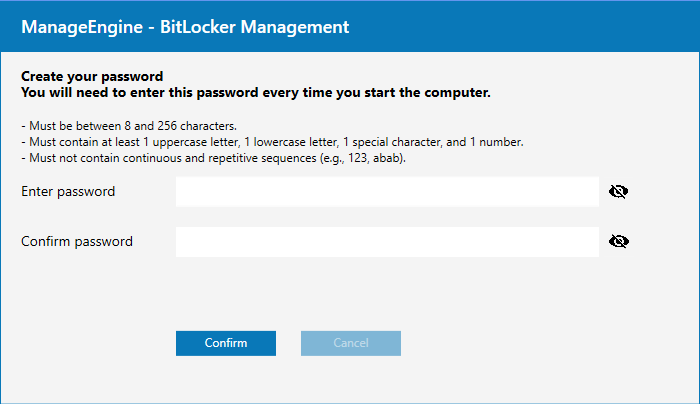
After this period, the "Cancel" button is disabled, requiring the creation of a BitLocker password to ensure all systems remain encrypted and compliant.
Note: If the authentication type for devices with TPM is set to "TPM only" and the authentication type for devices without TPM is set to "Protection off," the password setting option will not be visible, as there is no authentication configured.
BitLocker policies also include advanced settings for postponing encryption, configuring recovery key updates, and setting a rotation period.
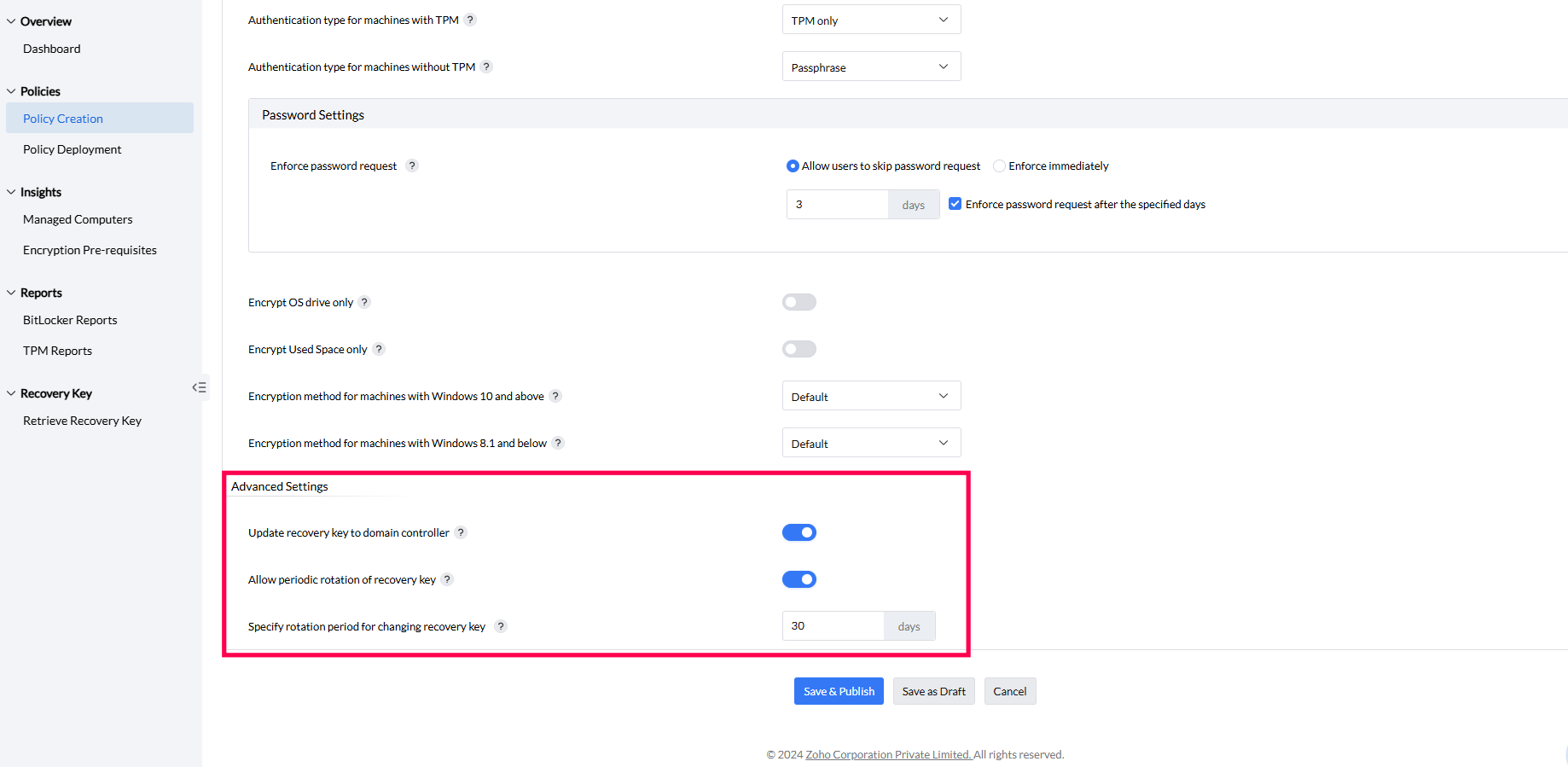
Once you have configured the settings, you can save as a draft or publish directly. The created policy can be viewed in the policy list under the Policy Creation tab.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.