

Endpoint Central provides users with the ability to exclude specific files or folders from detection to prevent false positive detections and improve the overall efficiency of the platform.
By excluding files or folders from detection, users can prevent legitimate file activity from triggering alerts and avoid unnecessary interruptions to their workflow. However, it is important to exercise caution when using this option and ensure that only authorized files and folders are excluded from detection to maintain the security of the system.
Here are the steps on how to exclude files or folders from detection.
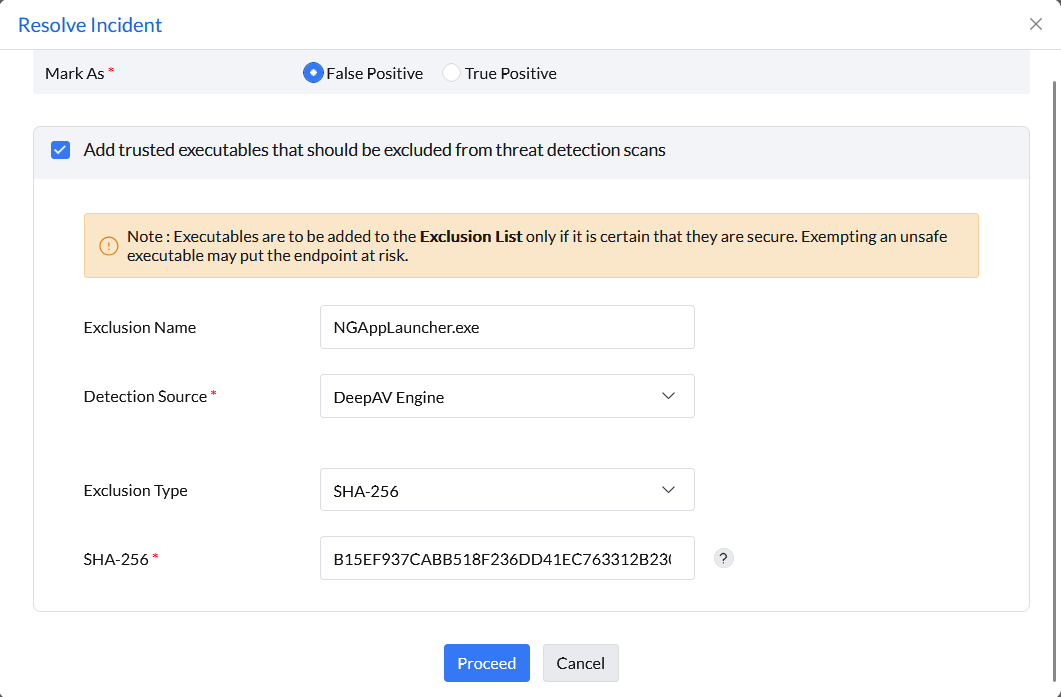
In the event that an incident is labeled as a false positive during its initial detection, Endpoint Central automatically recognizes it as such during subsequent detections. However, to prevent future false positive detections and to exclude similar processes, the incident can be added to the Exclusion List.
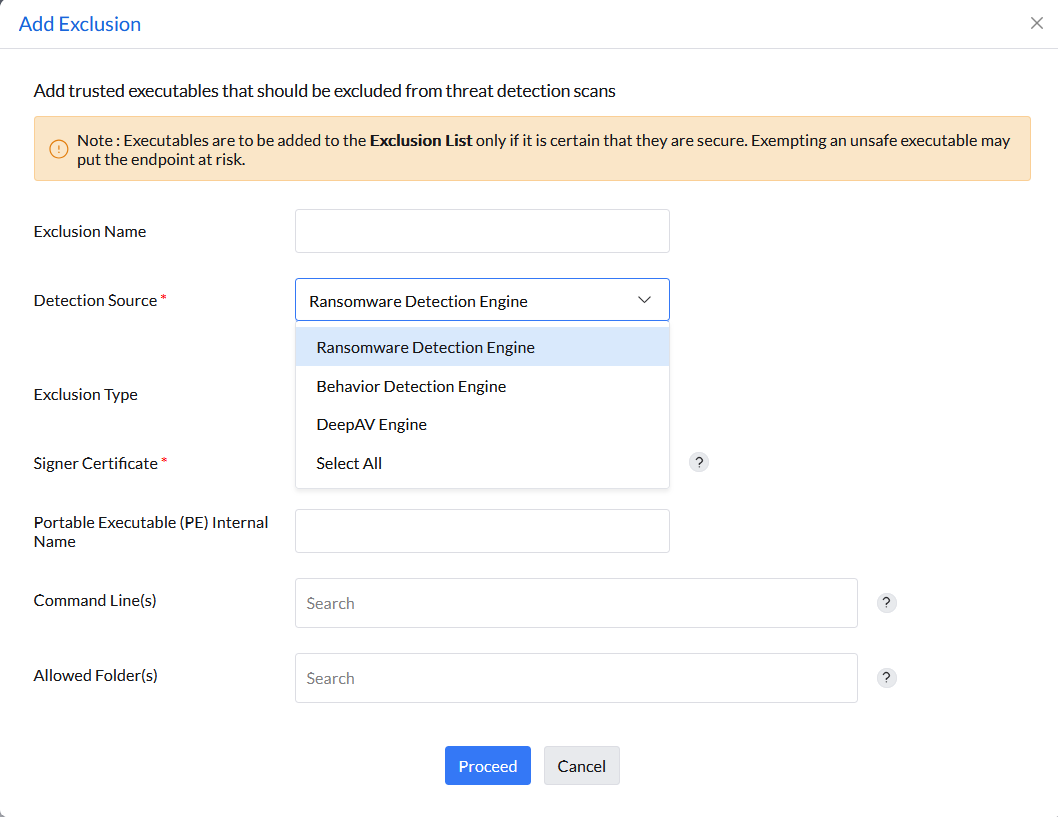
Adding a false positive process to the Exclusion List should only be done if there is a high level of certainty that it is indeed a false positive. Otherwise, it could potentially compromise the security of the device.
To add false positives to the Exclusion List, please follow the steps below:
You can exclude processes using any of the following techniques:
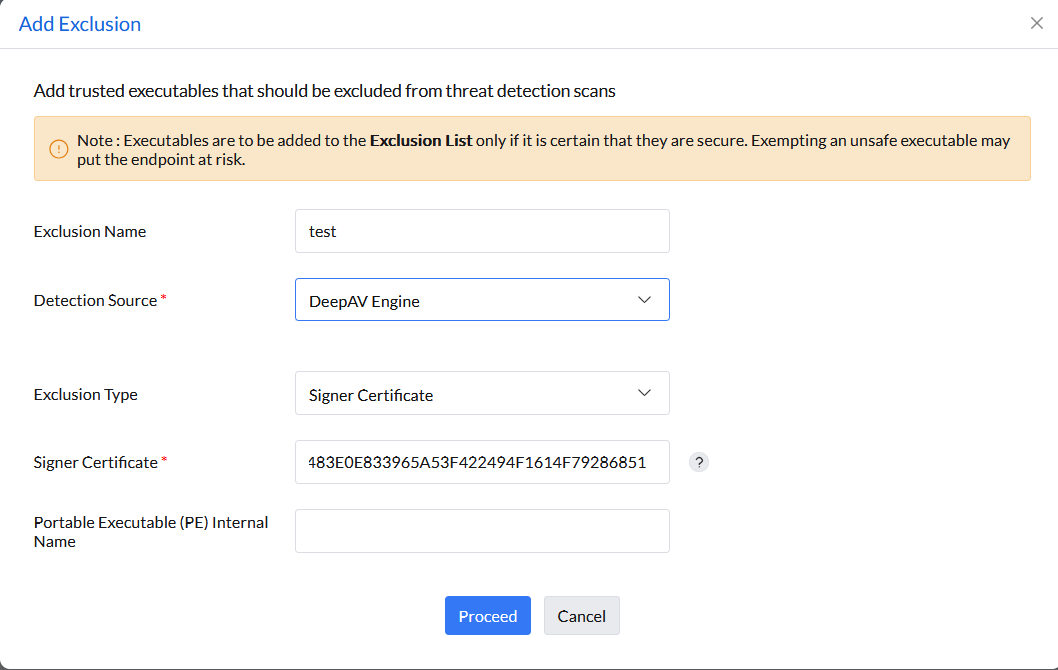
Note: This method is case-insensitive, and the executable must have a valid signature.
Example: 8870483E0E833965A53F422494F1614F79286851
Note: This is case-insensitive.
Example: b07f4b15a93ee95a7679be7dd3bd4f1399f12a02e826911515de7cef54f7fd1d
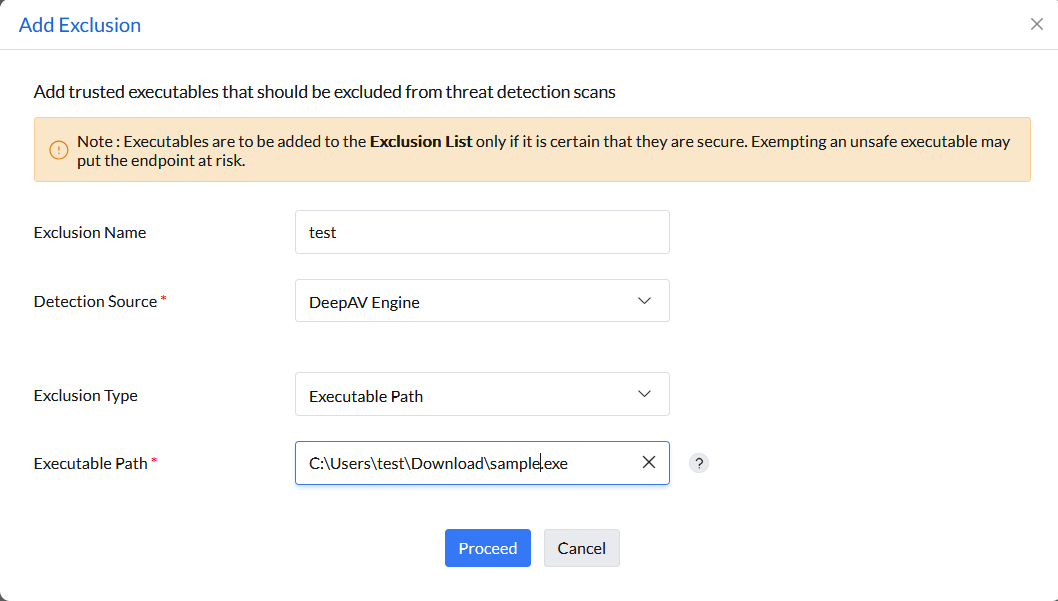
Note: This method is not recommended since ransomware may copy itself to this location and evade detection.
Example: C:\Windows\system32\notepad.exe
Example: C:\*\*\notepad.exe
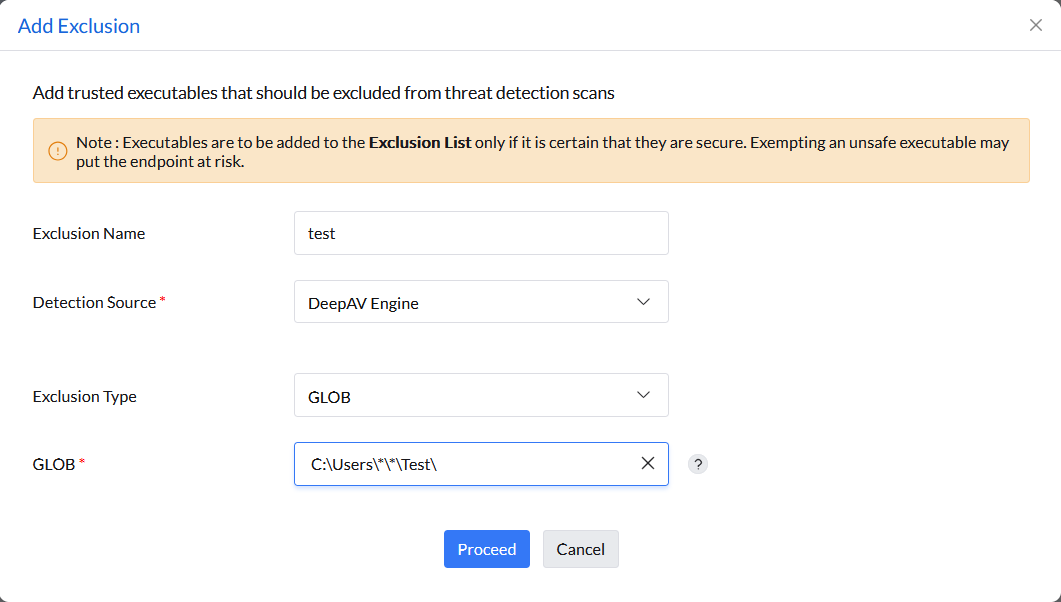
Example: cmd.exe /c vssadmin delete shadows /all,
cmd.exe /c DeleteBackups.bat
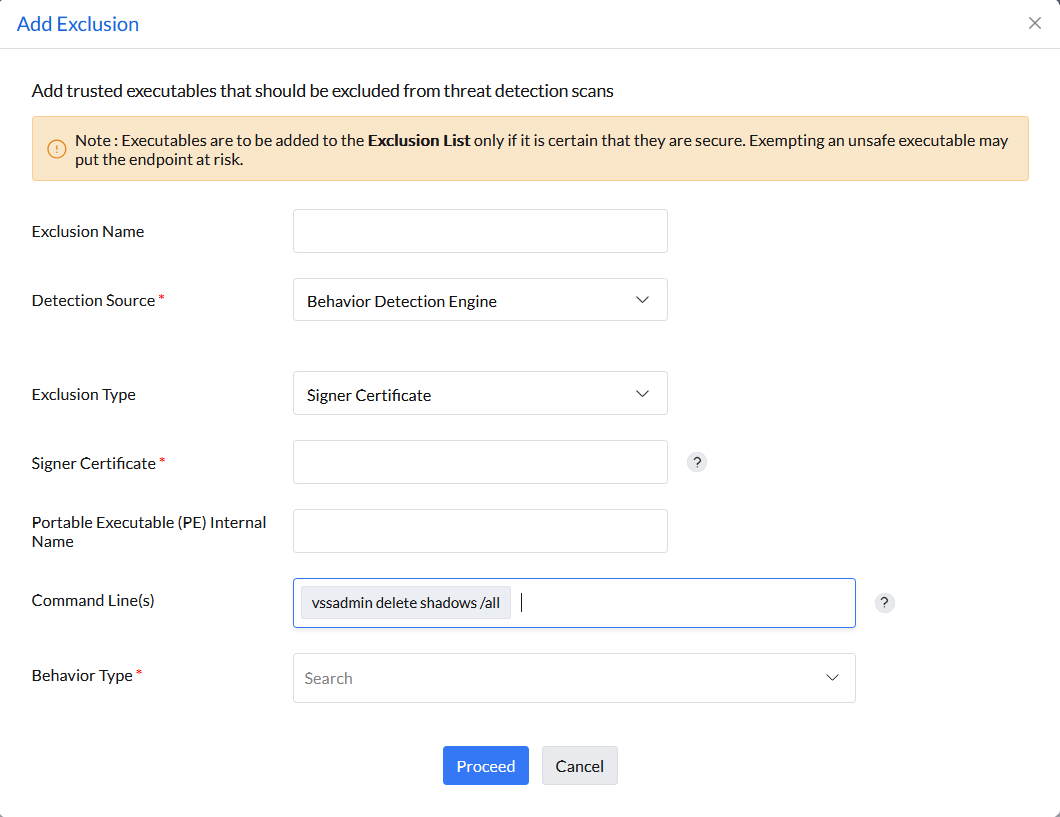
While adding an exclusion from the detection source Behavior Detection Engine, the Behavior Type, an alert rule for precise behavior detection, is to be selected. Follow the steps below to identify the behavior type:


Additionally, it is possible to exclude specific folders from detection by the Ransomware Detection Engine in Endpoint Central. To exclude a folder from detection, follow these steps: