What is Windows Event Viewer?
Last updated on:In this page
- What is Windows Event Viewer?
- Key features of Windows Event Viewer
- Accessing Windows Event Viewer
- -Using the Start Menu
- -Using the Run Dialog
- -Using the Control Panel
- -Using the Command Prompt
- Using Windows Event Viewer
- Benefits of using Windows Event Viewer
- Limitations of Windows Event Viewer
- How ManageEngine EventLog Analyzer helps analyzing Windows logs?
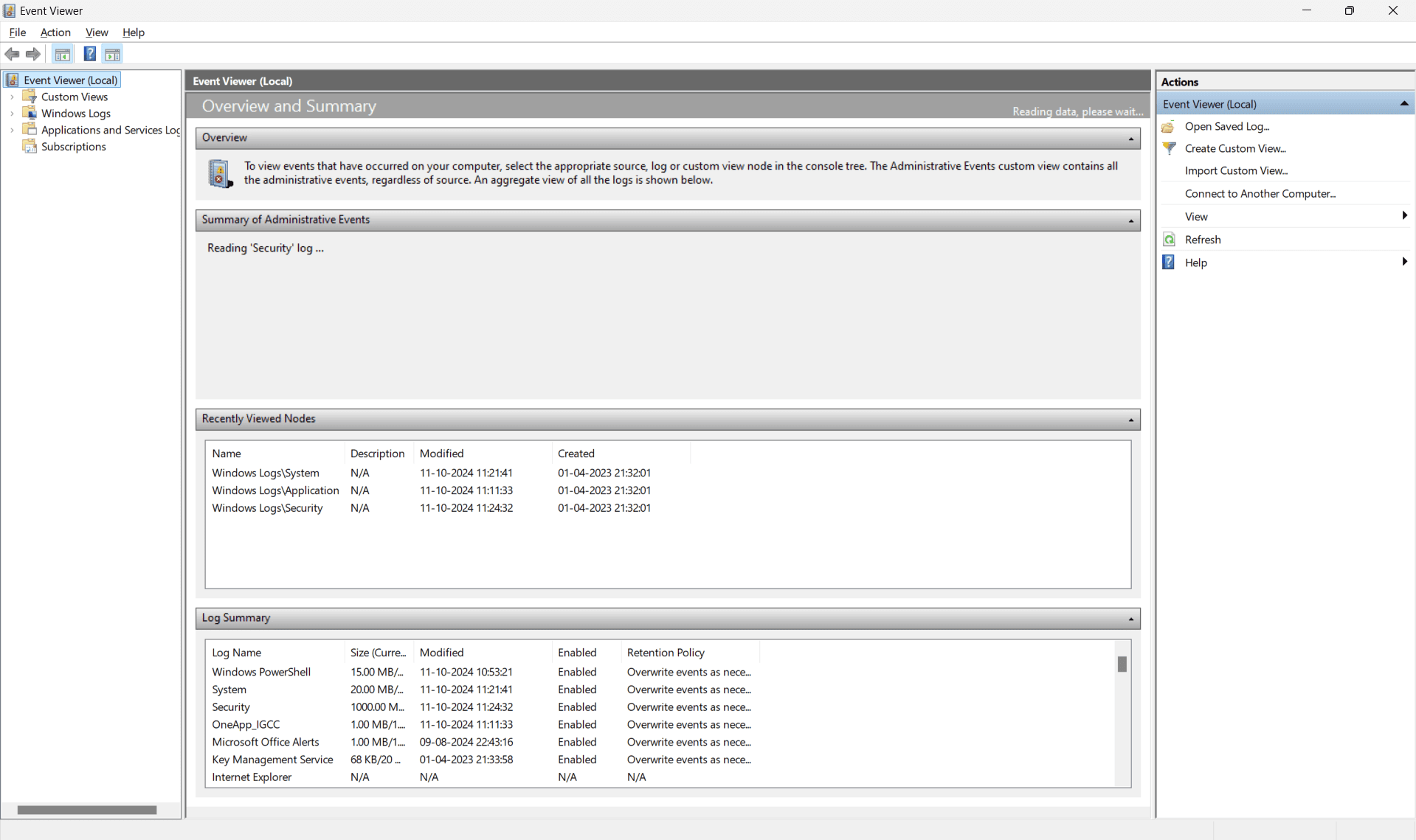
Windows Event Viewer is a built-in application for the Windows operating system that allows users to view and manage event logs. These logs contain information about various system, security, and application events, which can be critical for diagnosing issues, understanding system performance, and ensuring security compliance.
Windows Event Viewer's interface presents event logs in an organized manner, allowing users to navigate through different types of events easily, filter specific logs, and drill down into the details of each event. This tool is essential for monitoring and maintaining the health, performance, and security of Windows-based systems like Windows 10.
Get to know more about Windows event logs from here.
What are the key features of Windows Event Viewer?
- Viewing event logs: Windows Event Viewer organizes event logs into several categories for easy visualization and interpretation, typically:
- Application logs: Contains events logged by applications or programs. For example, when an application crashes, it might log the details in this log. These logs contain events logged by applications or programs. For example, a database application might log a file error in this section.
- Security logs: Records security-related events, such as login attempts, resource access, and other security auditing events.
- System logs: Stores events logged by Windows system components, such as driver failures, system errors, or hardware issues.
- Setup logs: Includes events related to the setup and installation of applications and system updates.
- Forwarded events: Logs events collected from other systems.
- Organizing event logs into levels: Event Viewer organizes event logs into many levels—including information, warning, error, and critical—depending on the nature of the event. While the information event indicates a successful operation, such as a system start, a critical event signifies a security issue, such as a permission change, which might require immediate attention. Event Viewer helps you analyze event logs in an orderly manner by categorizing the logs under different levels.
- Analyzing event logs in-depth: Event Viewer presents the details of an event log in readable manner, letting you analyze the event in-depth. It presents detailed information such as the event ID, source, log type , level, user involved, and a detailed description of the event in readable format with an intuitive interface. This helps you analyze event logs easily and quickly troubleshoot issues.
- Allowing custom views and filters to be built: Event Viewer lets you apply filters to view specific logs based on criteria, like date, event level, or source, making it easier to find relevant information. Custom views can also be created to focus on specific events or logs.
- Storing event logs: Event Viewer also allows you to forward and export event logs to other log management tools or SIEM solutions for further analysis or to be archived for long-term storage. These storage features are useful for maintaining records or sharing logs with support teams for troubleshooting.
How to access the Windows Event Viewer?
There are several methods to access the Windows Event Viewer in Windows 10 and other systems, depending on your preference or the situation.
Here’s how you can quickly get started:
Using the Start Menu
- Step 1: Click on the Start Menu button in the bottom-left corner of your screen.
- Step 2: In the search bar, type Event Viewer.
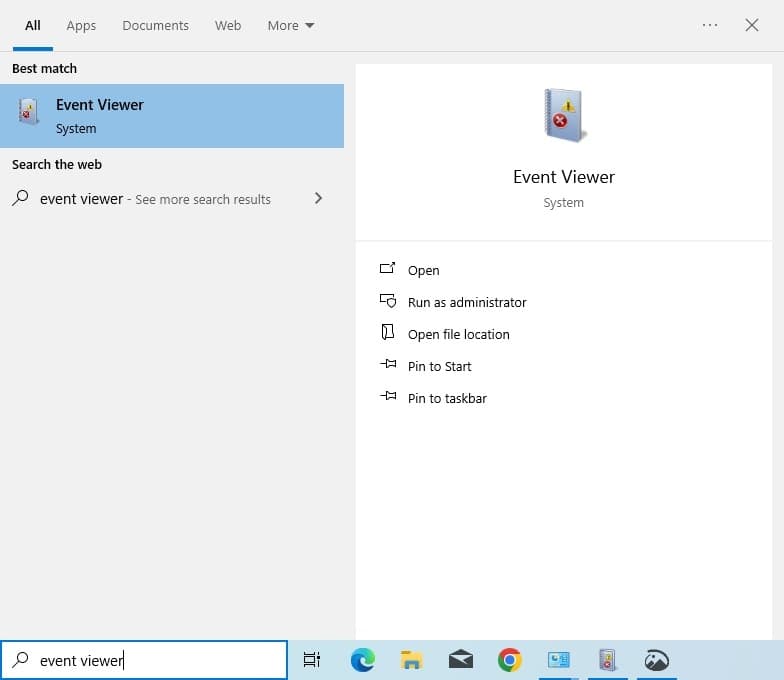
- Step 3: Select Event Viewer from the list of results.
- Step 4: The Event Viewer window will open, displaying the console tree and other interface components.
Using the Run Dialog
- Step 1: Press Win + R on your keyboard to open the Run dialog.
- Step 2: Type eventvwr and press Enter.
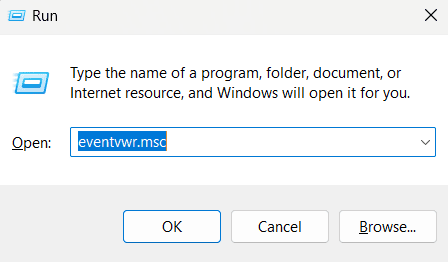
- Step 3: The Event Viewer window will open immediately.
Using the Control Panel
- Step 1: Open the Control Panel from the Start Menu.
- Step 2: Go to System and Security.
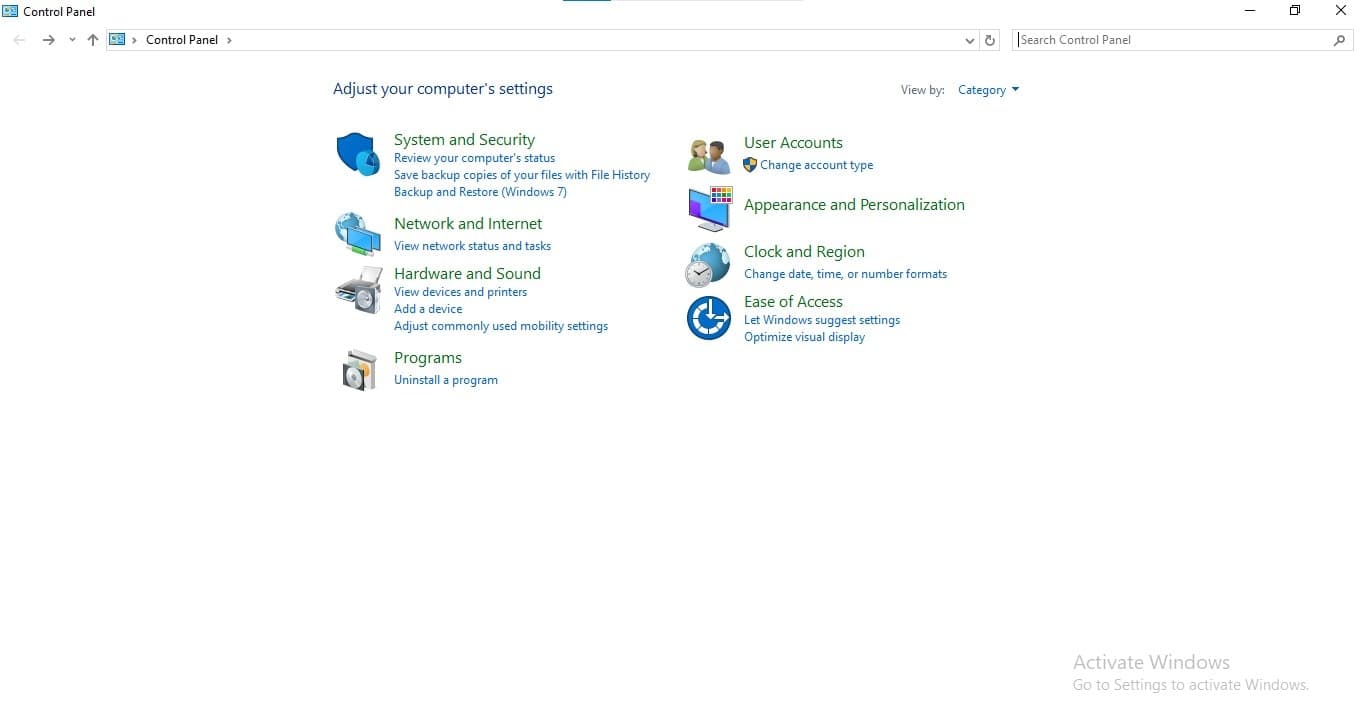
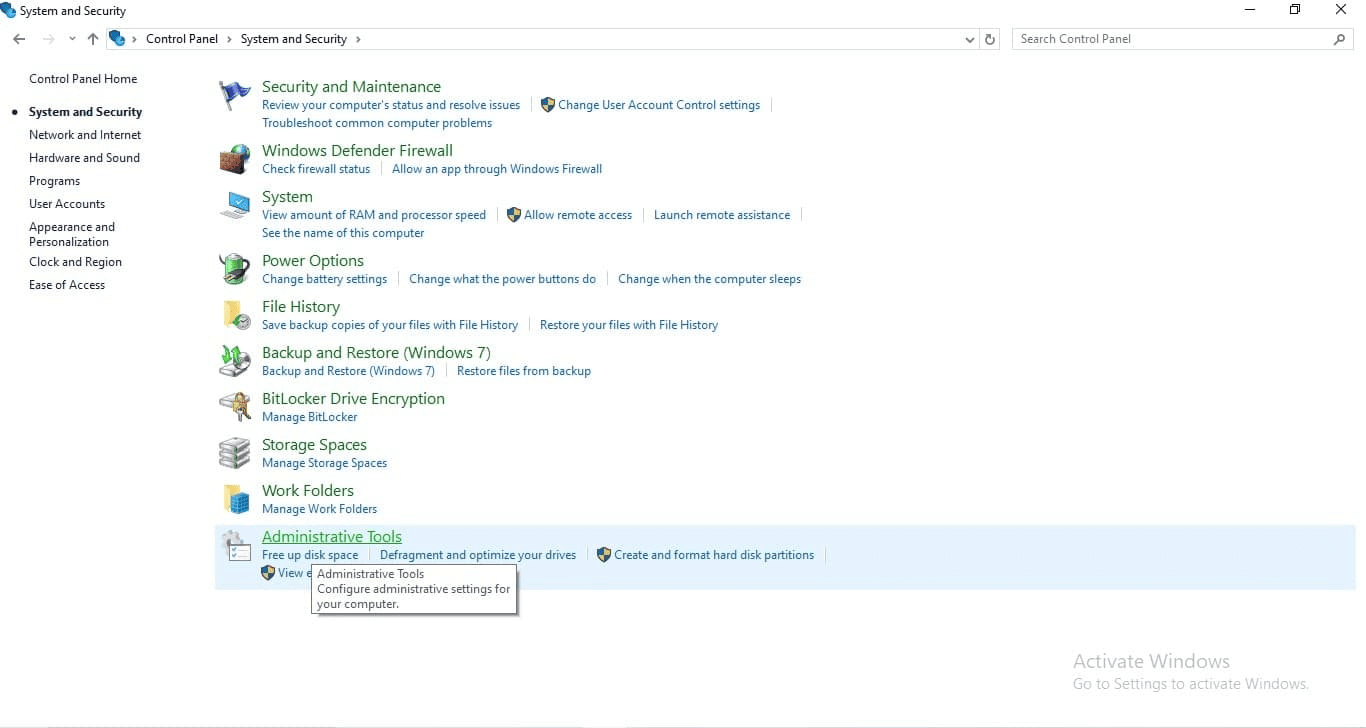
- Step 3: Click on Administrative Tools, then double-click on Event Viewer.
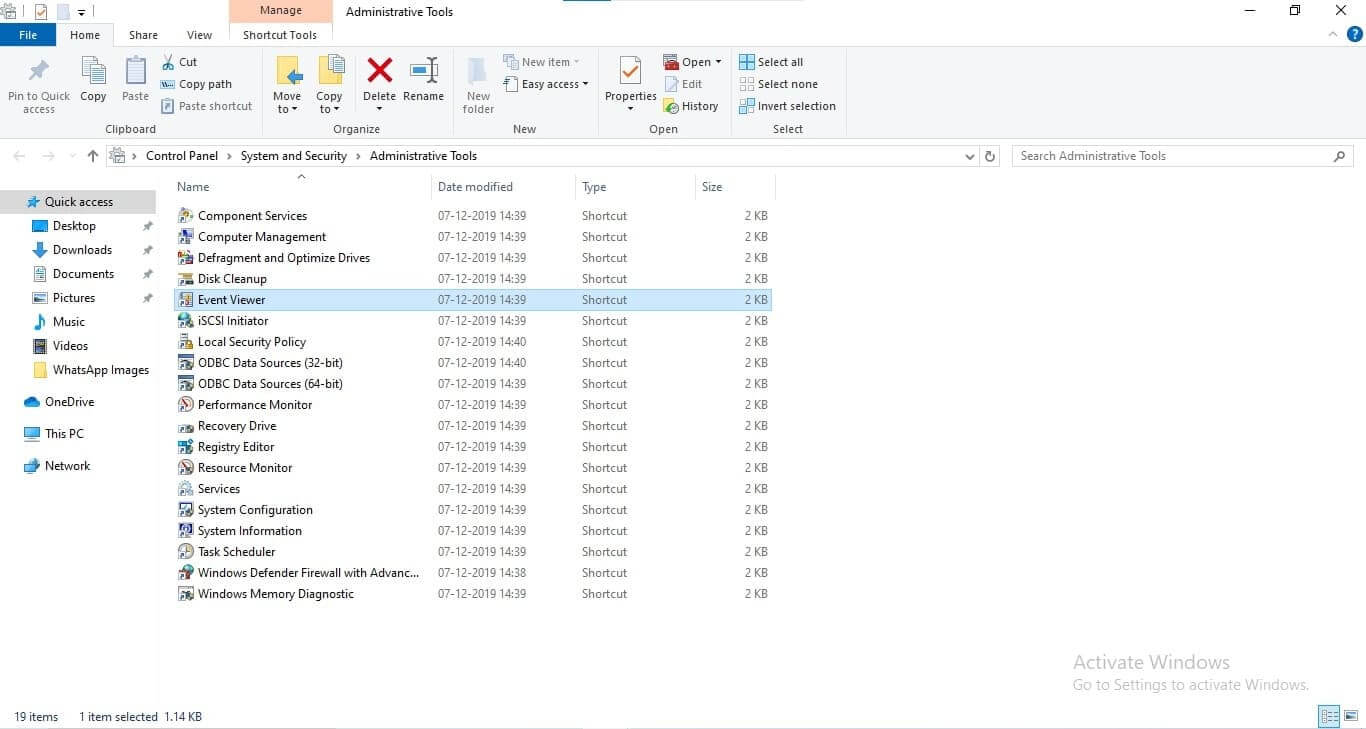
Using the Command Prompt
- Step 1: Open the Command Prompt by typing cmd in the Start Menu search bar and press Enter.
- Step 2: Type eventvwr in the Command Prompt window and press Enter.
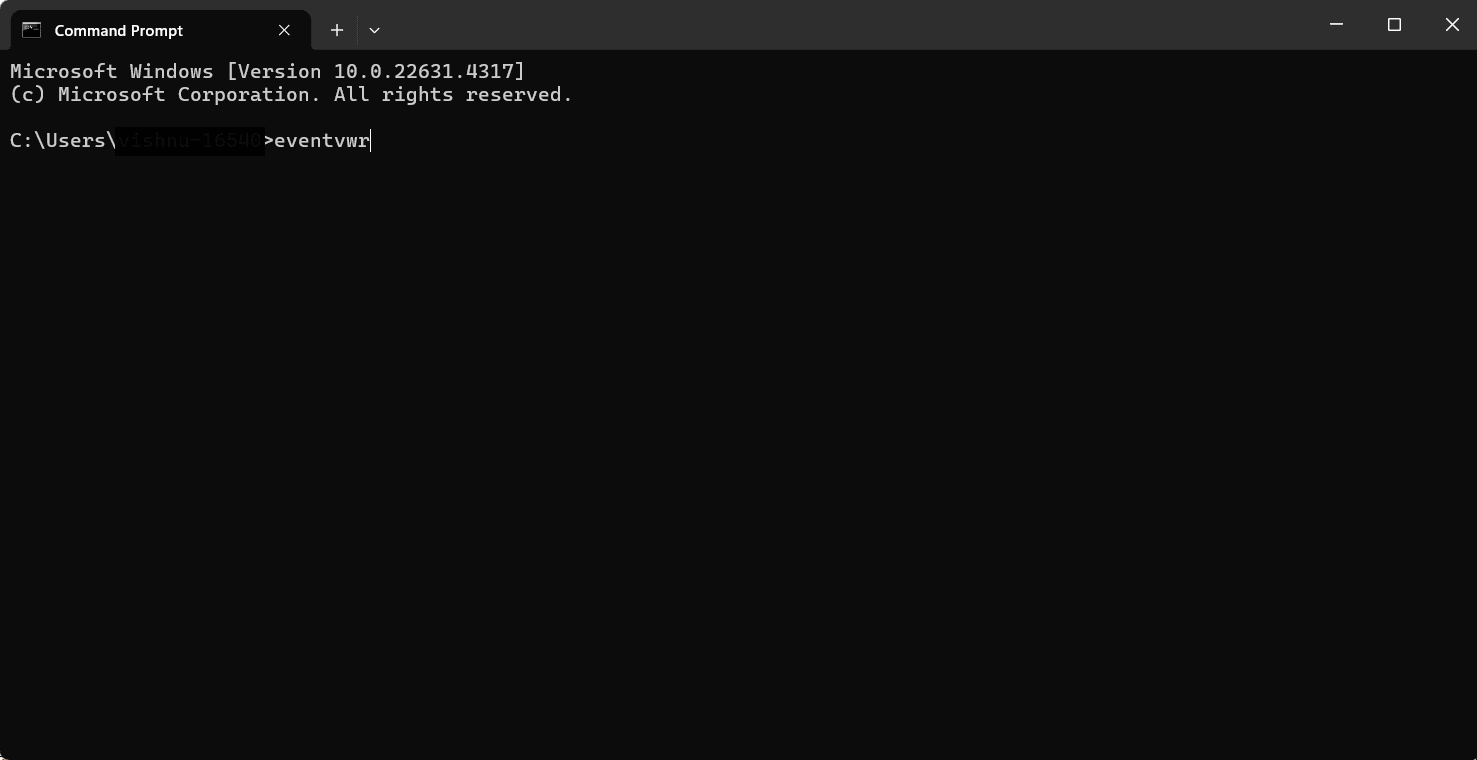
- Step 3: The Event Viewer will be launched.
How to filter logs using Windows Event Viewer
Filtering logs helps narrow down the logged events to those most relevant to your investigation or monitoring task.
Here's how you can filter logs in Windows Event Viewer.
Step 1: Open Windows Event Viewer
- Press Win + R to open the Run dialog box.
- Type eventvwr.msc and press Enter.
- The Event Viewer window will open.
Step 2: Select the log you want to filter
- In the Event Viewer, expand the Windows Logs or Applications and Services Logs node in the left pane.

- Select the log type (such as Application, System, or Security) where you want to apply the filter.

Step 3: Access the filter
- Click Filter Current Log in the Action Pane on the right side of the window. Alternatively, you can right-click the log name and select Filter Current Log from the context menu.

- The Filter Current Log dialog box will appear.
Step 4: Specify the filter criteria
Windows Event Viewer offers different filter criteria, including filters based on date and type, event level, source, and event id. Specify the applicable filter criteria outlined below.
To use date and time filters:
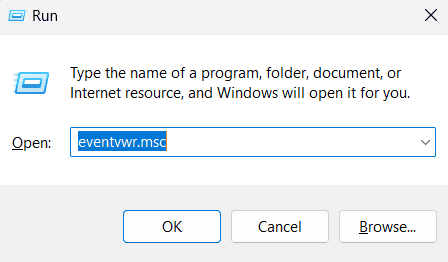
- In the Logged section, use the dropdown menu to select a predefined time range (e.g., Last Hour, Last 24 hours) or choose Custom range to specify the start and end dates for the events you want to view.

- If you select Custom range, click on the First Event and Last Event drop-downs next to the From and To fields and select Events On.

- Now, click on the calendar icons next to the Events On drop-down to pick the desired date and time.
Filtering based on event level:
- In the Event level section, select the checkboxes next to the event levels you want to include in the filter (e.g., Critical, Error, Warning, Information, Verbose).

- Unchecking all levels will clear the filter, but it’s recommended to select the levels relevant to your task.
Filtering based on event source:
- In the Event sources dropdown, you can filter events by their source. For example, if you are troubleshooting issues with a specific application, select the application’s name from the list.
- You can select multiple sources by holding down the Ctrl key while clicking the sources you want to include.

Filtering event logs using event ID:
- Enter specific event IDs in the <All Event IDs> field to filter events by their ID. For example, if you're looking for logon events, you might enter 4624 (the event ID for successful logons).

- You can enter multiple event IDs separated by commas, or use a range (e.g., 1000-1500) to filter a broader set of events.
Step 5: Apply the filter
- After specifying your criteria, click OK to apply the filter.
- The Event Viewer will now display only the events that match your filter criteria.
Step 6: Review the filtered events
- Examine the filtered events in the middle pane of the Event Viewer. You can click on any event to see its details in the lower pane.
- If you need to refine your filter further, you can return to the Filter Current Log dialog by following the steps above.
Step 7: Save the filtered view (Optional)
- If you regularly need to view events using the same filter, you can save the filtered view. After applying the filter, click on Save Filter to Custom View in the Action Pane.
- Name the custom view and choose where to save it in the Event Viewer.

- Your custom view will now be accessible under the Custom Views node in the left pane for future use.
Filtering logs in this way can greatly reduce the time it takes to find relevant events and can be crucial for effective monitoring and troubleshooting.
How to search for specific events using the Find feature of Windows Event Viewer?
Searching for specific events in Windows Event Viewer using the Find feature is a simple process that allows you to locate particular events within large log files quickly.
Here are the steps to help you search specific events efficiently:
- Step 1: Click Find in the Action Pane or press Ctrl + F to open the Find dialog box.
- Step 2: Enter a keyword, event ID, or any other search term related to the event you are looking for.
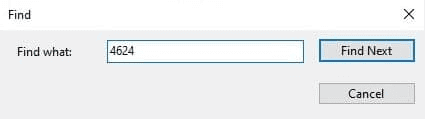
- Step 3: Click Find Next to locate the event. The search will highlight the first matching event in the log.
Here are some tips to help you search better for specific events in Windows Event Viewer:
- Using wildcards: Incorporate wildcards (e.g., * or ?) to broaden your search when you’re unsure of the exact terms or numbers.
- Filtering before searching: Apply filters before using the Find feature to narrow down the log entries, which can make your search faster and more accurate.
- Combining criteria: Use multiple criteria (e.g., event ID, source, date) in conjunction to refine your search and pinpoint specific events more effectively.
How to create custom views in Windows Event Viewer?
In Windows Event Viewer, custom views allow you to create tailored log views that display only the events relevant to your specific needs. This is especially useful for cybersecurity analysts who need to monitor particular types of events across large volumes of logs.
Creating a custom view
- Start the process: Right-click on Custom Views in the Event Viewer console tree and select Create Custom View.
- Set filtering criteria: In the Create Custom View dialog box, specify the filtering criteria, including:
- Time range: Select the time period for which you want to view events.
- Event levels: Choose which event levels (e.g., Error, Warning) to include.
- Event logs: Select the specific logs (e.g., Application, Security) from which events should be drawn.

- Event IDs and keywords: Input any specific event IDs or keywords to narrow down the view further.
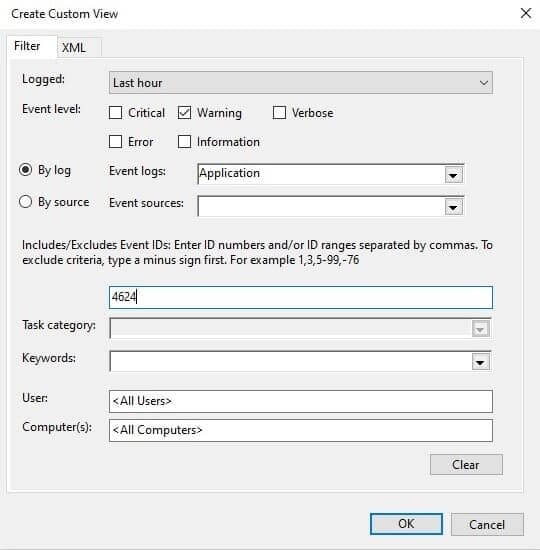
- Name and save the view: After setting the criteria, click OK, give the custom view a name and description, and then click OK again to save it.
- View the results: The new custom view will appear under Custom Views in the Console Tree, ready for use.
Why is Windows Event Viewer essential?
Event Viewer plays a crucial role in capturing granular details about a system and application events. In an age where system uptime and data security are critical, Event Viewer offers users a reliable way to monitor and manage their Windows infrastructure, offering insights into both normal operations and potential issues.
Here are some key scenarios where Windows Event Viewer can be helpful:
- Diagnosing system issues
- Scenario: An application crashes unexpectedly, causing disruption in business operations.
- How Event Viewer helps: By reviewing the application logs, users can identify the error code, event ID, and potential causes of the crash, facilitating a quick resolution.
- Security audits
- Scenario: You want to monitor users' activities or review the activities of admins.
- How Event Viewer helps: The security logs in Event Viewer provide detailed views into user logons, logoffs, permission changes, object accesses, and other security events.
- Monitoring system performance
- Scenario: Users notice a slowdown in system performance and try to identify the underlying cause.
- How Event Viewer helps: System logs in Event Viewer can reveal resource bottlenecks, failed services, or other performance-related issues, guiding corrective actions.
- Incident response
- Scenario: A potential security breach is detected, and the incident response team needs to gather evidence and understand the scope of the breach.
- How Event Viewer helps: By analyzing security event logs, the team can trace the actions of the threat actor, understand the attack vector, and take appropriate containment and remediation measures.
- Compliance reporting
- Scenario: An organization must generate reports on system and security events to comply with regulatory requirements like GDPR, HIPAA, or PCI DSS.
- How Event Viewer helps: The detailed logs in Event Viewer can be exported and analyzed to generate reports that meet these regulatory standards.
To record user and object access activities, you need to enable basic and/or advanced audit policies.
What are the limitations of Windows Event Viewer?
Though useful to filter, search, and analyze event logs, Windows Event Viewer has several limitations that can hinder its effectiveness for users, especially those who are not technically inclined.
- Complexity and user interface: The interface is not very user-friendly, especially for those who are not familiar with event logs. Also, it can display a vast amount of data, making it challenging to sift through and find relevant events without prior knowledge of what to look for.
- Limited filtering: The filtering options in the Event Viewer are limited. While you can filter events based on keywords, event IDs, and categories, it’s often insufficient for more complex queries.
- Slow search functionality: Searching through logs can be slow, particularly on systems with several events. This can be a significant hindrance when trying to troubleshoot time-sensitive issues.
- Security concerns: The logs stored and accessed using the Event Viewer are stored locally, therefore prone to tampering. If a machine is compromised, an attacker can easily clear the logs to erase traces of their activity. This security risk highlights the need for centralized logging solutions in corporate environments, where logs are sent to a secure location for analysis and retention.
- Inconsistent data retention: While users can set a maximum log size, there is no straightforward option to limit logs based on time. This means that once the log reaches its maximum size, older entries are overwritten without consideration of their age, which can result in the loss of potentially important information.
These limitations often lead organizations to seek third-party log management solutions or security information and event management (SIEM) tools, which offer enhanced log management, advanced analytics, centralized monitoring, and more robust alerting and reporting features.
How does ManageEngine EventLog Analyzer help with analyzing Windows event logs?
ManageEngine EventLog Analyzer is a comprehensive log management and IT compliance solution designed to streamline the collection, analysis, and management of log data across various IT environments.
Here’s an in-depth look at how it helps analyze Windows event logs:
- Automated log collection: EventLog Analyzer automates the collection of logs from multiple sources, including Windows servers and workstations. The solution automatically discovers and configures devices, helping setup log collection within minutes. It supports agent-based and agentless log collection methods for Windows infrastructure.
- In-depth log analysis: This log management tool uses advanced analytics and a real-time correlation engine to analyze event logs. EventLog Analyzer addresses both operational and security log analysis use cases, including system error event analysis, performance issue remediation, tracking unauthorized accesses, and user activity monitoring.
- Windows file server monitoring: EventLog Analyzer comes with a built-in file integrity monitoring feature for Windows and Linux servers to track changes made to files and folders. It provides insights into who did what actions, when, and from where. A detailed object access audit is carried out to detect unauthorized modifications, ensuring data integrity.
- User activity monitoring: EventLog Analyzer tracks user activities—such as logon attempts and access to sensitive data—which is crucial for identifying potential insider threats and ensuring compliance with security policies.
- Threat hunting capabilities: EventLog Analyzer allows security teams to conduct root cause analyses for security events, enabling them to pinpoint the exact log entries that triggered incidents. This feature helps in understanding the context of security events and facilitates quicker resolution.











