- Home
- Logging Guide
- Log correlation
What is log correlation?
In this page
- What is log correlation?
- How is event correlation performed?
- Why do you need log correlation?
- Event correlation methods
- Challenges of conducting efficient event correlation
Log correlation is a technique of analyzing log data from different sources to identify a pattern of events. It is used to gain better visibility into the network's activity and thereby effectively secure the network against vulnerabilities and threats.
Log correlation is a crucial part of the log management process. After the logs are collected and stored, the centralized log server performs analysis to detect specific events. Log correlation is a key log analysis technique that helps admins detect known attack patterns.
How is event correlation performed?
During log analysis, event correlation is used to connect the seemingly discrete events that occurred on different devices or applications across the network and check if they form a pattern.
Let us consider a scenario. A user remotely logs in to a machine. The information about this login, such as the IP address and the time, is available in the VPN logs. This user then escalates their privileges, which is recorded in the domain controller logs. With the escalated privileges, the user tries to access sensitive files from a critical file server, which gets recorded in the file server logs.
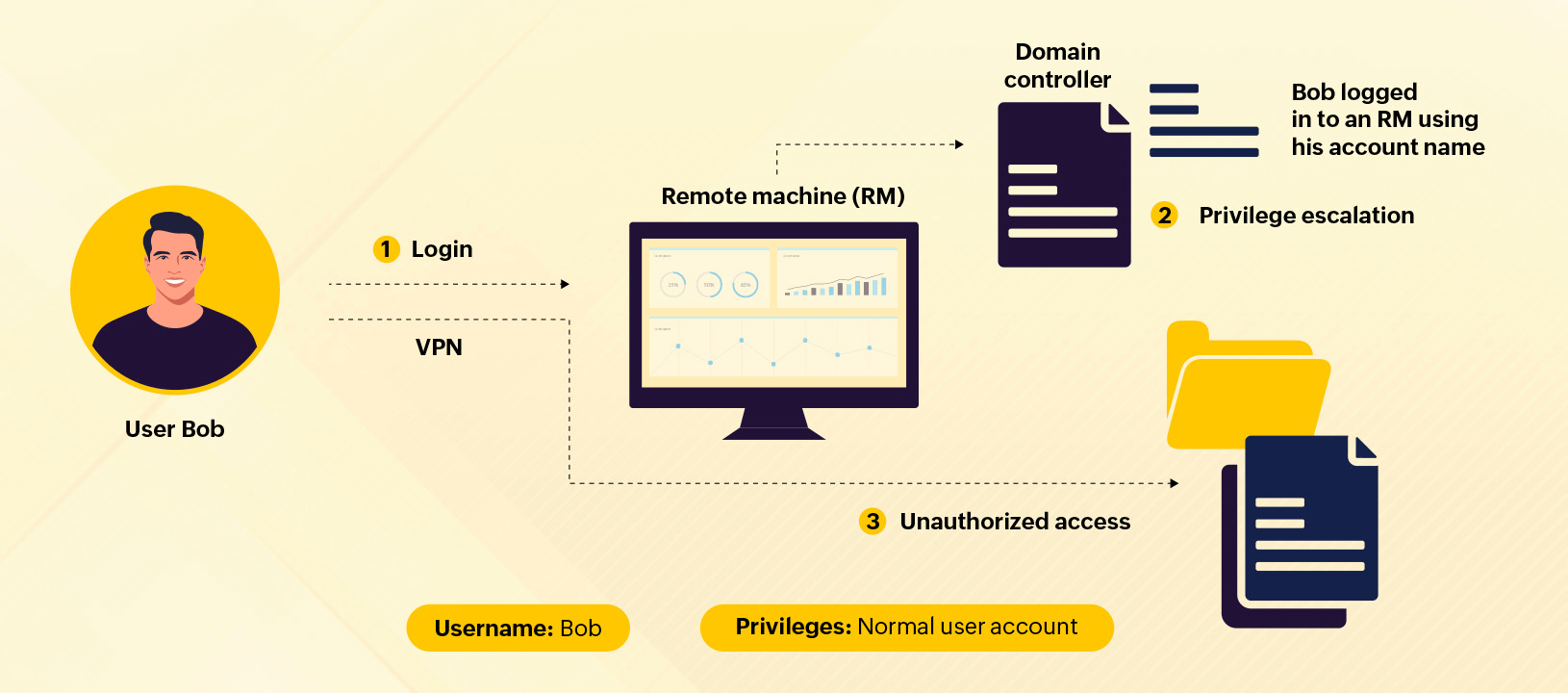
A security administrator can detect the potential threat of unauthorized file access only if they correlate all of the above discrete events. A log management tool can effectively correlate these events and alert security admins about the potential threat.
Why do you need log correlation?
Here are a few important reasons why enterprises need log correlation.
1. Automate attack detection in real time
In agentless log collection, the logs generated on every device are collected without an agent. The device or application where the log is generated will directly send the log data to a central server. The transmission will be secured using protocols such as TCP and HTTPS.
2. Detect security flaws
A tool that performs log correlation can help detect operational and security flaws in their initial stages, allowing analysts to fix them before they cause a lot of damage.
3. Perform effective root cause analysis
A log correlation tool provides visibility into the sequence of events or incident timeline of a breach, helping with effective root cause analysis.
4. Optimize security operations
An effective log correlation tool can optimize the SOC's KPIs, such as the mean time to detect (MTTD), mean time to acknowledge (MTTA), and mean time to respond (MTTR).
5. Meet compliance requirements
Using tools that perform log correlation can help you comply with the compliance requirements of HIPAA, the GDPR, the PCI DSS, and others.
Event correlation methods
Correlation is usually done through one or more of the following methods: time-based correlation, rule-based correlation, pattern-based correlation, topology-based correlation, and more.
Time-based correlation
In this method, we examine what happened before or during an incident to identify the sequence of events of the breach and how the events are related.
Rule-based correlation
Rule-based correlation uses specific variables, like the timestamp, type of transaction, and location, to compare events. You have to write new rules for every variable, making it unfeasible for a lot of organizations.
Pattern-based correlation
Pattern-based correlation combines the strengths of both time-based and rule-based correlation techniques to check if the relationships between events match a predefined pattern.
Topology-based correlation
This method maps the events to the topologies of the networks or devices that are affected. This enables you to visualize the incident easily within your IT environment.
Challenges of conducting efficient event correlation
The biggest challenge of conducting event correlation stems from how big organizations have become and the sheer amount of information generated by them every minute. It has become an impossible task to keep up with the volume of events generated and to parse them for actionable information. Correlation tools help us perform these tasks efficiently and save time, allowing IT teams to solve problems without having to spend hours detecting them.
The log correlation tool checklist
Log management and SIEM solutions come with log correlation capabilities. Depending on your security needs, you can choose either a SIEM solution or a tool that just manages the logs and provides analytical reports.
If you are looking for a tool to step up your security game, then you must choose a SIEM solution that has log correlation along with other solid security features, such as threat intelligence, behavior-based anomaly detection, incident management, data loss prevention, and cloud security.
Here are a few important things that you need to consider when choosing your security tool for performing log correlation:
1. Ease of use
Security solutions are often complex to deploy and use because they ingest and process a huge amount of data. This complexity is also the reason security admins cannot use the solutions' features to the fullest. Make sure to choose a security tool that is easy to deploy and use. In particular, it should come with an easy-to-use, intuitive interface for viewing the incidents that are correlated with each other, building a custom correlation tool, and doing even more with little to no training.
2. Built-in features
It is essential to be aware of the features of the SIEM tool you are considering onboarding. For example, what log types and formats does it support? How does it process event data? Will it be able to correlate events and trigger an appropriate response quickly during critical events? Make sure you get answers to these questions when looking for a security solution.
3. Ease of integration
A holistic security overview will only be possible if you orchestrate all your security solutions. Ensure that the SIEM tool you choose integrates and orchestrates with other security solutions, such as your antivirus, anti-phishing, and anti-malware platforms. It must perform correlation across the data from these security tools to provide you with complete visibility into your network's security.
Good log correlation software can help you effectively spot threats and stop them in their early stages before they cause disasters. EventLog Analyzer, ManageEngine's comprehensive log management tool, can perform log correlation, send out real-time notifications, and manage incidents to mitigate cyberattacks. Check out our solution's event correlation capability here.











