- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
EventLog Analyzer is a comprehensive log management tool that automatically collects, analyzes, and securely stores IIS logs to enhance network and web security. Get insights into configuration changes, web server attacks, security errors, and much more using this IIS log viewer tool.
How EventLog Analyzer helps you make the most of Microsoft IIS logs
Intuitive reports from raw IIS log data
EventLog Analyzer automatically collects IIS logs from web server files and stores them in its central server. You can view the raw IIS logs to conduct analysis at any point. Alternatively, the solution also presents critical information on HTTP bad requests, locked errors, client and server errors, and more in the form of intuitive reports.
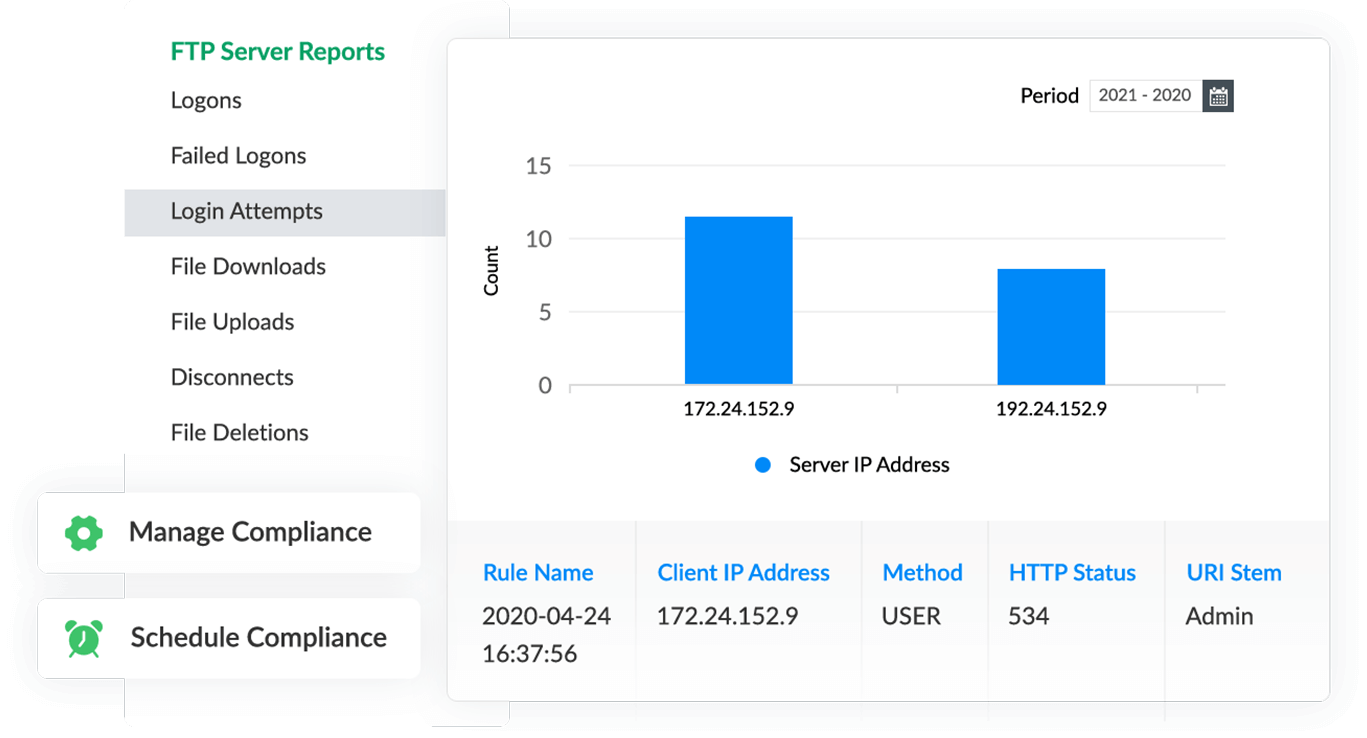
Analyze IIS FTP server logs
Gain key insights into IIS FTP server events such as logons, failed login attempts, top users, file downloads, or security data exchanges. Monitor critical admin configuration changes to logging, IP domains, SSLs, and more using intuitive reports, and be alerted in real time via SMS or email whenever these critical changes occur. Viewing IIS logs and manually analyzing the response time and unique visitors can be hectic; with our IIS log analyzer tool, you can get instant reports on the IIS FTP server's average response time and insights into unique visitors.
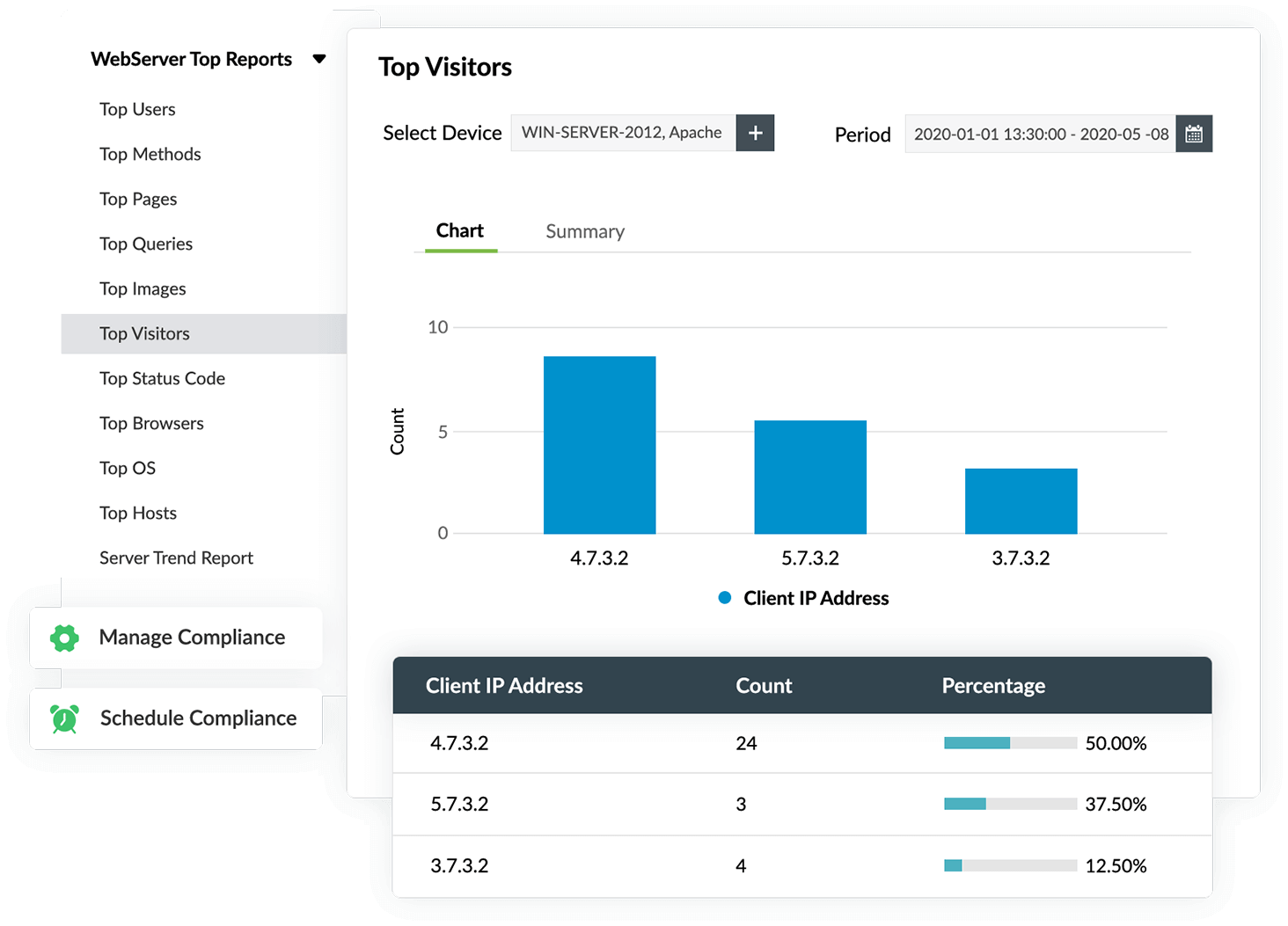
Audit IIS web server events
Monitor errors like HTTP bad requests, gateway timeouts, and user authentication failures, and security attacks such as SQL injection and DDoS attacks. EventLog Analyzer's incident management module sends you real-time alerts if any web server attacks are detected. It can also help you get a comprehensive view of your IIS web server activity through trends, patterns, and overview reports, and identify performance bottlenecks and detect suspicious user requests made to the IIS web server accurately.
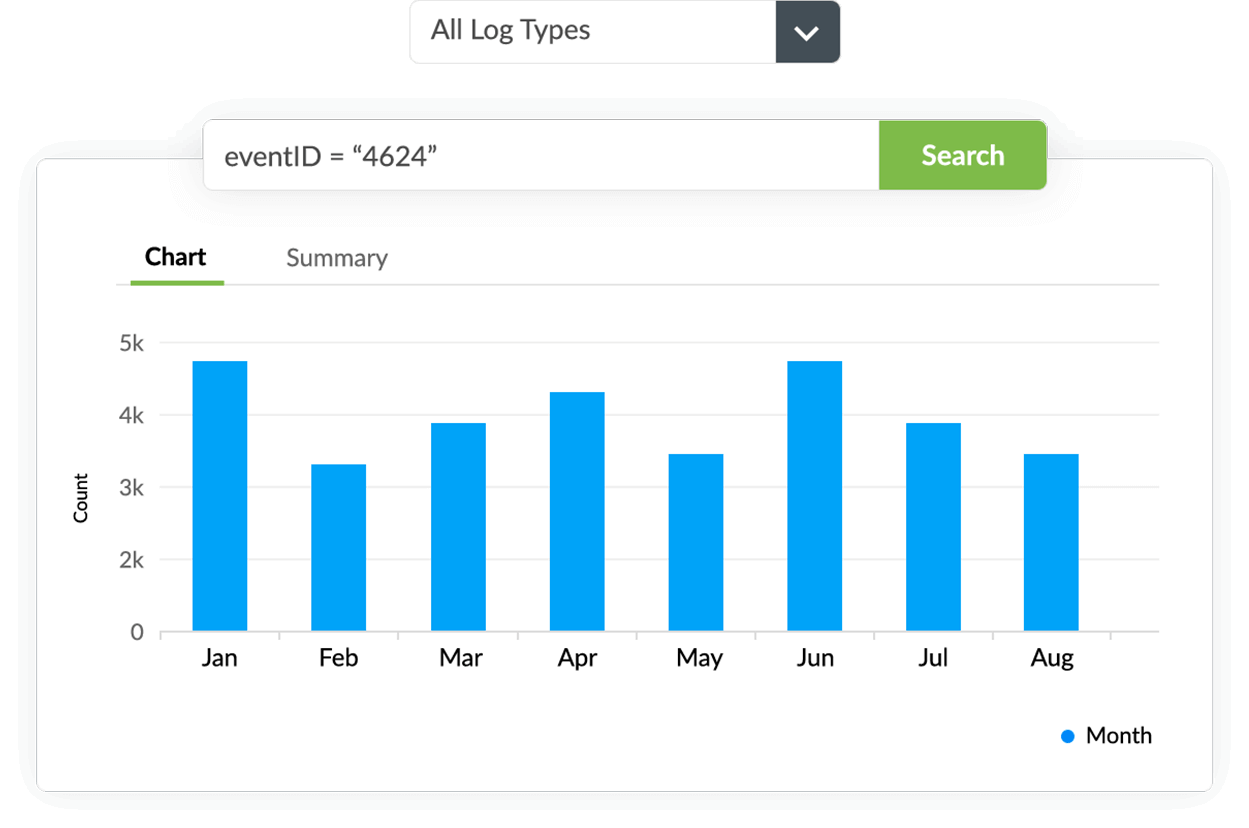
Detect threats to IIS servers
EventLog Analyzer periodically imports log data and tracks complex IIS server logs to identify the root cause of any security event present in an IIS server. Using IIS error log analysis, you can detect the problems encountered by users while accessing your website. EventLog Analyzer's IIS log viewer ensures your server's critical and confidential data is safe from the hands of intruders. If a security threat is detected in an IIS server, real-time alerts are sent to your network admin to proactively prevent your site from going down. Additionally, it detects malicious IP addresses and URLs with its augmented threat intelligence capability.
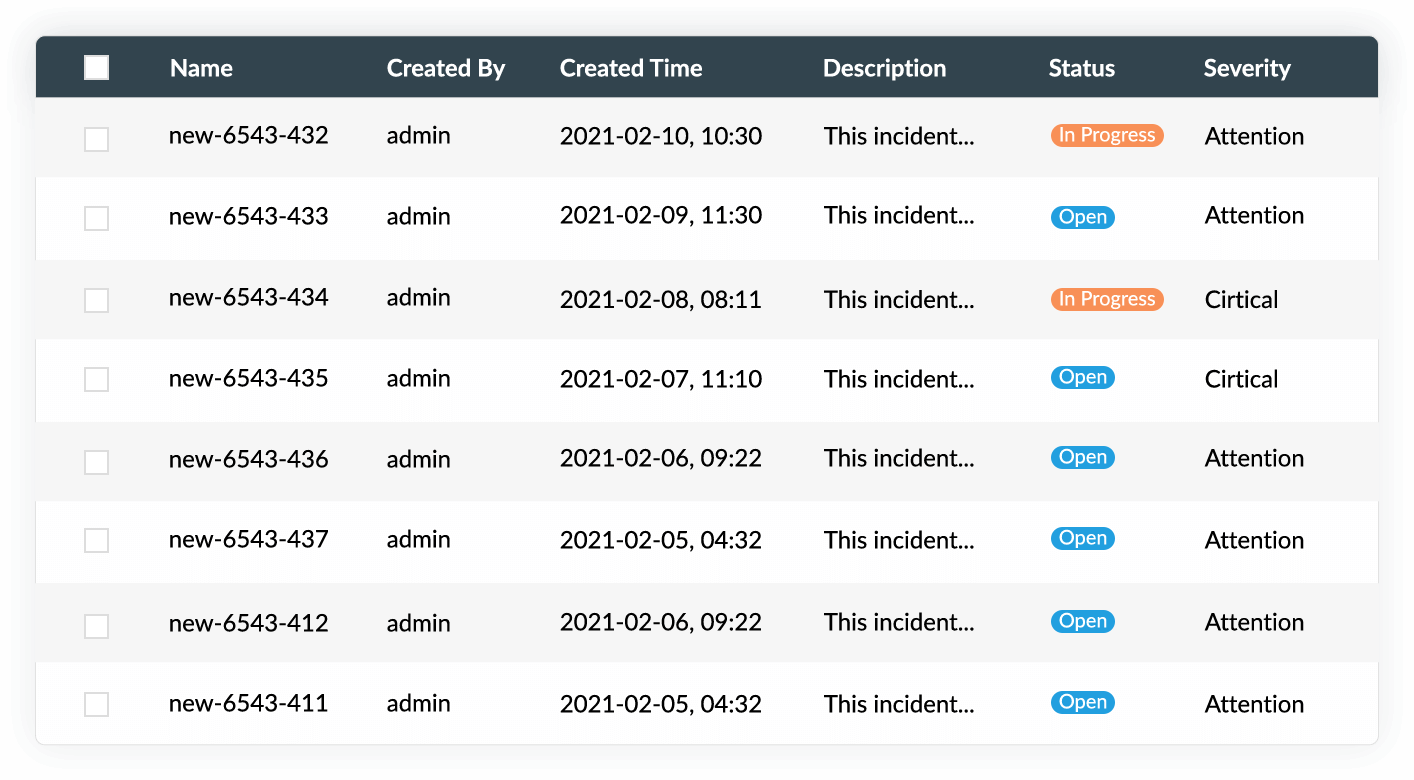
Generate extensive reports at ease
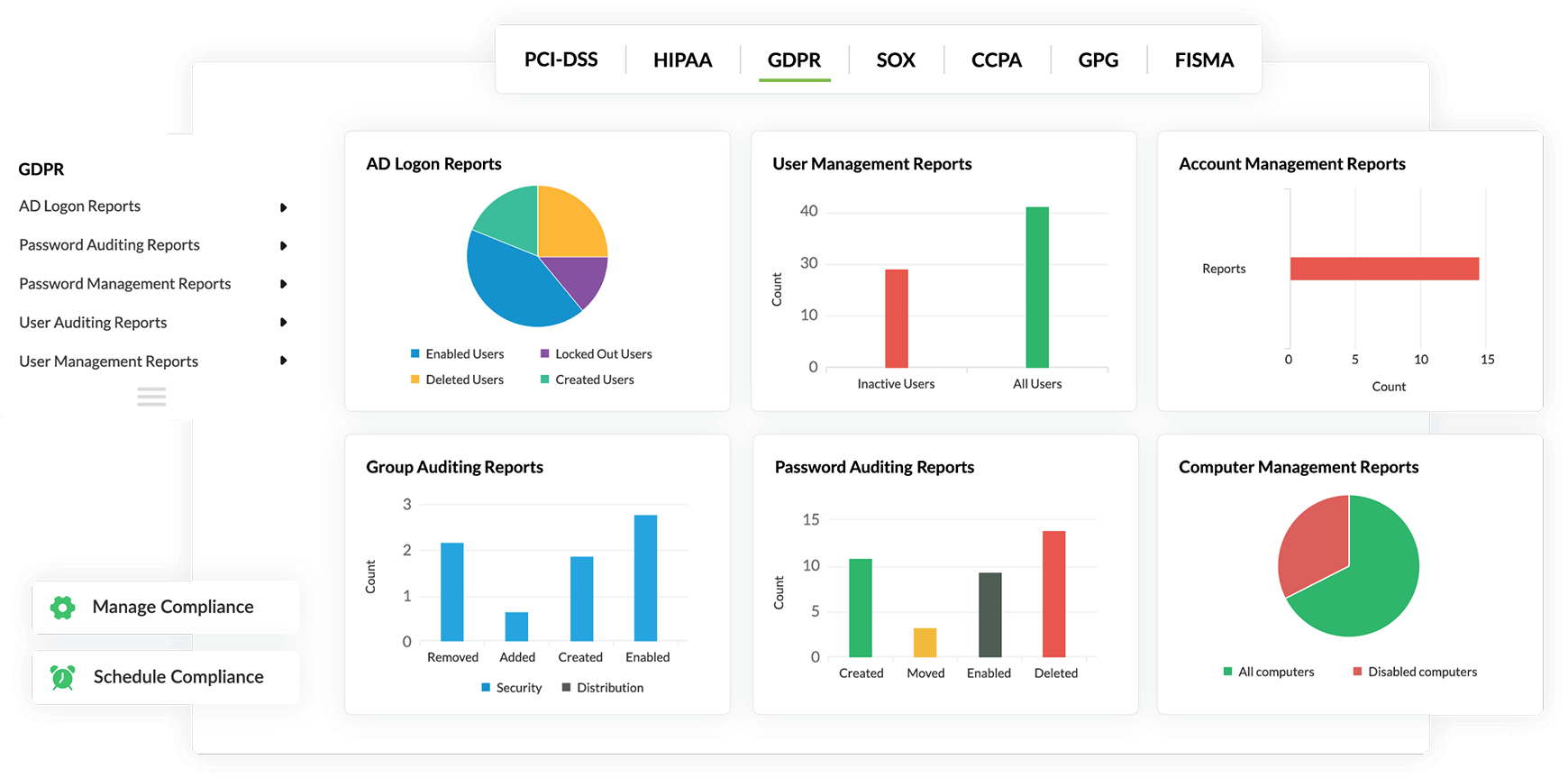
Generate audit-ready reports to comply with regulatory IT mandates such as HIPPA, FISMA, the GDPR, SOX, and PCI DSS. EventLog Analyzer also gives you full flexibility in creating custom reports to help you meet internal security policies and to comply with new compliance mandates. Based on your organization's requirements, you can customize and schedule predefined reports, too.
Related solutions offered by EventLog Analyzer
Windows log management
Centrally manage event log data from Windows devices including workstations, servers, and terminal servers to meet auditing needs. Combat security attacks with real-time alerts and event correlation.
Syslog management
Collect and analyze Syslog data from routers, switches, firewalls, IDS/IPS, Linux/Unix servers, and more. Get in-depth reports for every security event. Receive real-time alerts for anomalies and breaches.
Privileged user monitoring
Monitor and track privileged user activities to meet PUMA requirements. Get out-of-the-box reports on critical activities such as logon failures, reason for logon failure, and more.
Threat intelligence
Get instant alerts when malicious IP sources interact with your network. EventLog Analyzer's contains threat intelligence from international threat feeds such as STIX, TAXII, and AlienVault OTX.
IT compliance management
Comply with the stringent requirements of regulatory mandates viz., PCI DSS, FISMA, HIPAA, and more with predefined reports & alerts. Customize existing reports or build new reports to meet internal security needs.
Log forensic analysis
Perform in-depth forensic analysis to backtrack attacks and identify the root cause of incidents. Save search queries as alert profile to mitigate future threats
5 reasons to choose EventLog Analyzer as your IIS log viewer tool
1. In-depth auditing and reporting
EventLog Analyzer analyzes IIS server logs to detect security vulnerabilities and suspicious activities. It provides in-depth auditing reports to comply with various regulatory IT mandates such as PCI DSS, HIPAA, and the GDPR. You can easily customize the audit report templates to meet specific auditing requirements.
2. A powerful correlation engine
EventLog Analyzer's correlation engine associates events from diverse log sources including IIS servers to determine whether a known attack pattern is unfolding in the network. It provides more than 30 correlation rules that can help your security team detect malicious activities taking place in the network.
3. Automated incident management
EventLog Analyzer detects and mitigates security incidents, and automated incident response workflows are triggered to ensure a quick response to security threats. Automated actions include disabling users or computers, killing processes, and shutting down systems.
4. Augmented threat intelligence
EventLog Analyzer's advanced threat intelligence module instantly recognizes over 600 million malicious IPs, so you can ensure that no malicious source enters your network. With the built-in global IP threat intelligence database, you can detect critical events such as malware attacks and source and target IPs, and prevent network intrusions.
5. Comprehensive log management
EventLog Analyzer's comprehensive log management feature aggregates logs from various sources in the network and presents all the security events on a centralized dashboard to help your SOC team easily make sense out of this vast amount of logs. Moreover, it supports logs from over 750 diverse log sources.
Frequently asked questions
An IIS log viewer simplifies the process of analyzing and viewing log files by collecting, parsing, and normalizing the log data from various IIS servers. EventLog Analyzer, a comprehensive log management tool, allows you to view IIS logs by presenting the collected data on a centralized dashboard in the form of graphs and reports. Additionally, you can compare log events to identify and analyze suspicious activity in IIS servers, expedite incident response, and conduct root cause analysis.
IIS logs are stored in ASCII format, which makes them difficult to interpret. Analyzing and searching through enormous amounts of log data manually is a tedious and time-consuming task. A log management tool like EventLog Analyzer can help you overcome the hurdles that come along with manual log analysis.
An IIS log analyzer monitors your web servers for indicators of attack and can notify you if malicious activity is detected. Here are a few ways in which an IIS log viewer helps you improve your organization's network security:
- Log normalization: For easier comparison, normalization converts different log elements into the same format.
- Correlation analysis: Log data is correlated from multiple network devices, servers, systems, and firewalls to identify attack patterns.
- Dynamic threat intelligence: Threat intelligence is used to detect anomalous network behavior and defend against security threats instantly.
IIS web servers are highly prone to DDoS or SQL injection attacks. An IIS log viewer's advanced features can reduce the risk of cyberattacks and help you detect unusual network traffic. Additionally, it helps you monitor all user activity from the time they log in to the time they log out.
With the help of an IIS log analyzer tool like EventLog Analyzer, you can streamline the whole process of viewing and analyzing log files in IIS servers. The solution automates and centralizes the entire log management process. Your IIS server logs will be thoroughly analyzed to uncover any operational or security vulnerabilities.











