- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Network security devices play a crucial role when it comes to protecting your organization's network from external cyberthreats. By auditing the log data generated by these network devices, you can gain valuable information regarding various security events taking place in your network. However, the volume of log data generated by these network devices is incredibly high, making it difficult to monitor and analyze in real time. The good news is that EventLog Analyzer can simplify the entire process for you.
Monitoring and analyzing WatchGuard traffic using EventLog Analyzer
EventLog Analyzer is a centralized, web-based tool that provides IT compliance and log management for all WatchGuard security devices and virtual private networks (VPNs). The intuitive, easy-to-use interface offers administrators end-to-end log monitoring and management, agent-based and agentless log collection methods, custom log parsing, complete log analysis with reports and alerts, a powerful log search engine, and flexible log archiving options.
EventLog Analyzer monitors and stores every new log, along with its timestamp, size, and WatchGuard device information. This makes it easy to load, analyze, and generate reports from archived logs.
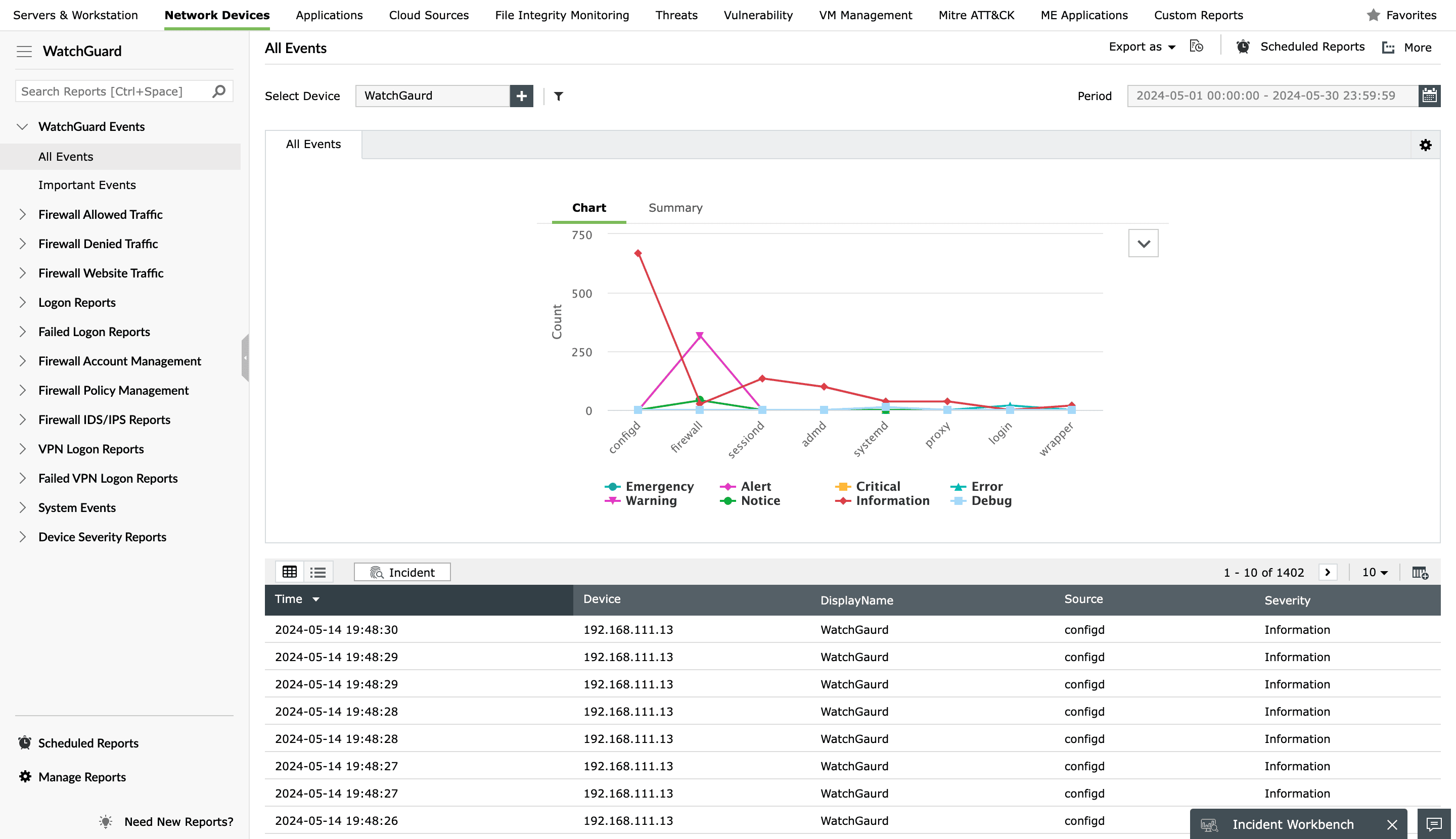
Since EventLog analyzer is capable of handling heterogeneous logs, it is possible to standardize WatchGuard logs along with other network device logs so they share a common format. This makes it easier to monitor and correlate logs from different devices to get a better understanding of the overall data flow through the network. All logs collected by WatchGuard devices, such as WatchGuard Firebox, can be archived regardless of their predefined interval. This way, you can create and load archived files into your database at any time.
Analyzing network threats using WatchGuard network log monitoring reports
EventLog Analyzer has an extensive set of out-of-the-box reports exclusively for WatchGuard networks that are broadly classified into 12 categories:
Firewall allowed traffic reports:
View information regarding traffic that has been allowed entry into the network. The traffic is categorized on the basis of source, destination, protocol, and port. You can also monitor traffic patterns and trends using this report.
Available Reports
Allowed Traffic | Top Traffic based on Source | Top Traffic based on Destination | Top Traffic based on Protocol | Top Traffic based on Port | Allowed Traffic Trend
Firewall denied traffic reports:
View all the connections that have been denied access to your network, and monitor traffic patterns and trends as well.
Available Reports
Denied Connections | Top Denied Connections based on Source | Top Denied Connections based on Destination | Top Denied Connections based on Protocol | Top Denied Connections based on Port | Denied Connection Trend
Firewall website traffic reports:
Track allowed traffic as well as traffic trends, and monitor website traffic based on source, destination, protocol, and port.
Available Reports
Website Traffic | Top Website Traffic based on Source | Top Website Traffic based on Destination | Top Website Traffic based on Website | Website Traffic Trend
Logon reports:
Monitor logon trends, all successful logons to your firewall, and the hosts and users with the most logons.
Available Reports
Logons | Top Successful Logons from Source | Top logons based on users | Logons trend
Failed logon reports:
Track failed logon trends, all unsuccessful logons to your firewall, and the hosts and users with the most failed logons.
Available Reports
Failed Logons | TTop Failed Logons from Source | Top failure logons based on users | Failed Logons Trend
Firewall account management reports:
Manage and monitor your firewall accounts by tracking account change information and identifying all new or deleted administrators.
Available Reports
Admin Added | Admin Deleted | Admin Modified
Firewall policy management reports:
Analyze changes made to firewall rules and network monitoring policies to get a head start on periodically cleaning up your firewall policies.
Available Reports
Policy Added | Policy Modified | Policy Deleted
Firewall IDS/IPS reports:
Monitor vulnerabilities and identify the source or destination devices most frequently involved in attack attempts. View an attack trend report as well.
Available Reports
All Attacks | Top Attacks based on Source | Top Attacks based on Destination | Attacks Trend
System event reports:
Monitor system events such as WatchGuard firewall configuration changes, clock updates, system status changes, and services that failed to start.
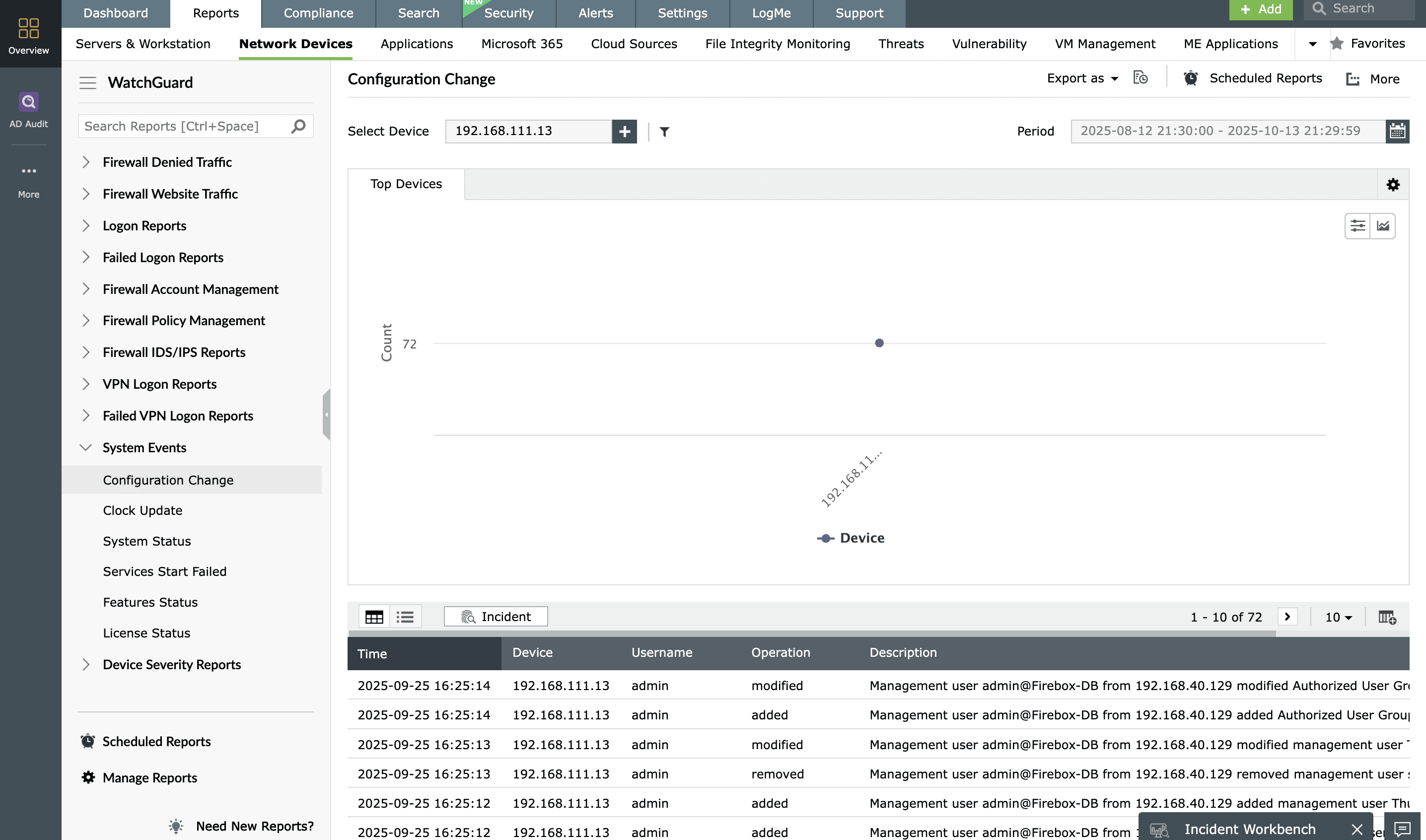
Available Reports
Configuration Change | Clock Update | System Status | Services Start Failed | Features Status | License Status
Device severity reports:
Analyze WatchGuard device logs to get a clear picture of the events happening in your network based on their severity. Monitor all access points, security events based on severity (such as emergency, alert, or error), and warning events.
Available Reports
Emergency Events | Alert Events | Critical Events | Error Events | Warning Events | Notice Events | Information Events | Debug Events
VPN logon reports:
Keep track of all successful VPN logons, logouts, and logon trends.
Available Reports
VPN Logons | VPN Logout | Successful VPN Logons Trend
Failed VPN logon reports:
Track unsuccessful VPN logons and failed logon trends.
Available Reports
Failed VPN Logons | VPN Failed logon trend reports
You can add your own customizable reports in addition to the existing set of exhaustive reports. Schedule both existing reports and user-created reports to export them to PDF or CSV and automatically email them to stakeholders.
Benefits of monitoring WatchGuard devices and VPNs using EventLog Analyzer:
- Secure, tamper-free log archiving
- Intuitive interface
- Powerful log forensics that enable robust searches
- Custom compliance reports to fulfill compliance standards
- Easily customizable report templates to meet internal policy needs
- Real-time email and SMS alerts on configuration changes and events of interest
Get instant notifications when suspicious events occur with real-time alerts
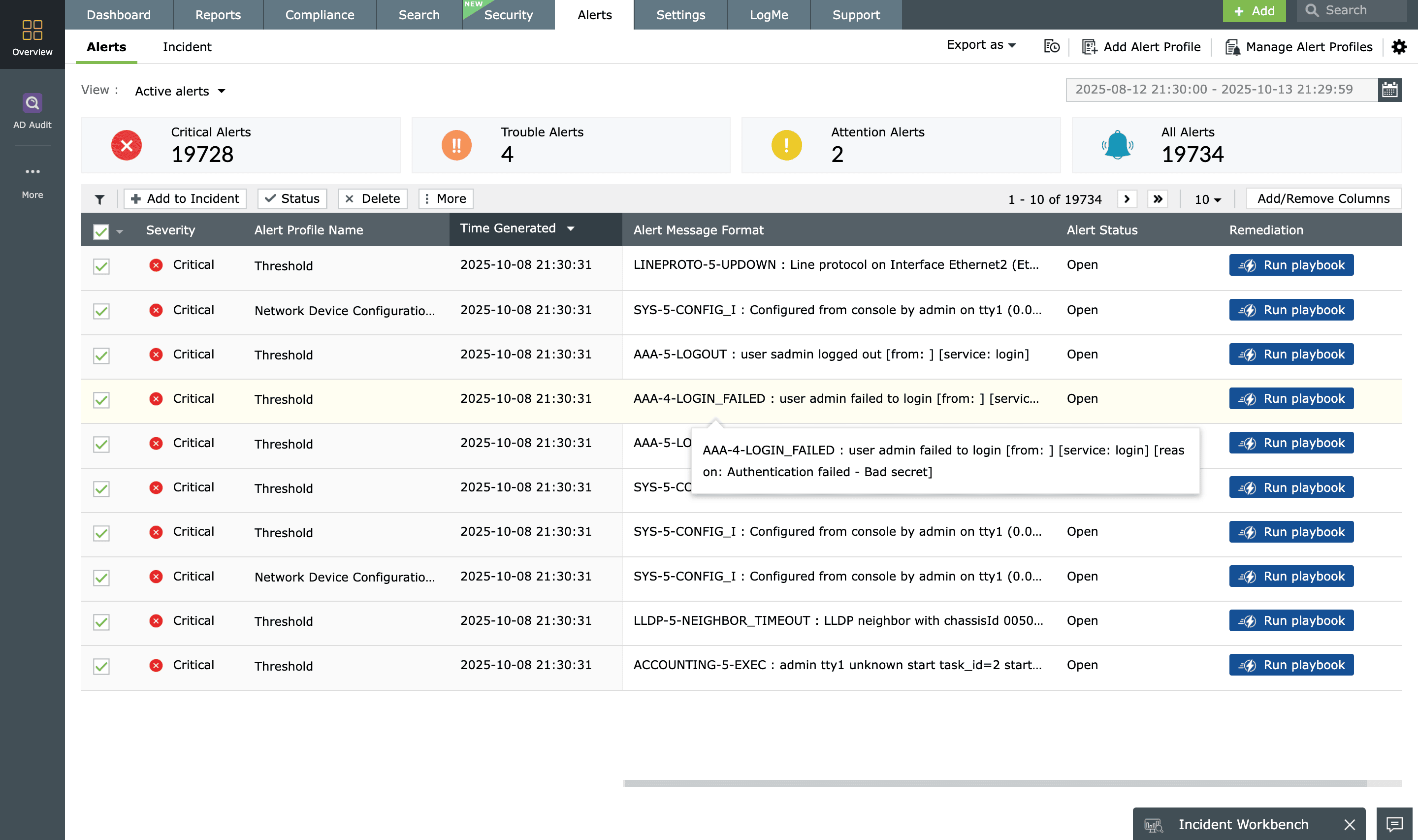
Minimize the mean time to detect and respond to any attack with the help of EventLog Analyzer's real-time alerting feature. Whenever there is any sign of a threat, alerts will be triggered, and EventLog Analyzer will notify you immediately via email or SMS.
The alerts have three severity levels: Attention, Trouble, and Critical. You can prioritize the alerts based on their severity level and focus on remediating the most critical ones first.
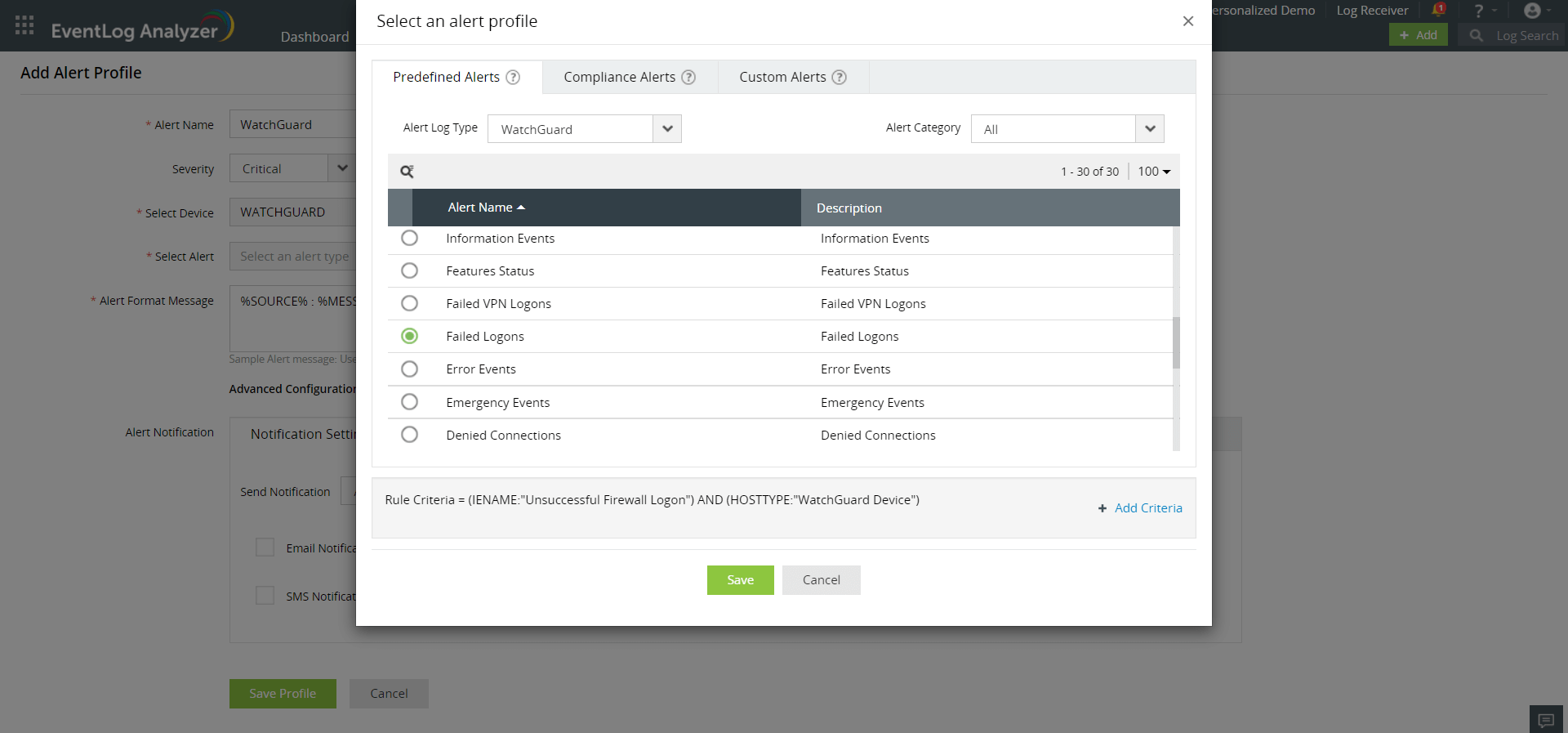
Using EventLog Analyzer, you can set up alerts to monitor specific events on WatchGuard security devices, such as configuration changes, warning events, failed logons, critical events, and policy modifications.












