- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Breached password protection
Thousands of passwords are exposed during data breaches every day. Once compromised, these passwords are available to multiple threat actors over the dark web. If a user in your organization were to use one of these passwords, it could create a weak link in your IT security architecture.
ADSelfService Plus, a holistic identity security solution, can prevent the usage of breached passwords in your organization.
Credential stuffing attacks
In a credential stuffing attack a hacker uses a database of already compromised credentials to illegally break into a user account. Unchecked use of breached passwords can leave your organization susceptible to these attacks. The potential damage is greater when users reuse the same credentials for multiple applications.
Screen for breached passwords with ADSelfService Plus' integration with Have I Been Pwned
ADSelfService Plus is an identity security solution that can bring your organization closer to a Zero Trust environment.
Have I Been Pwned is a website that checks if a given password has ever been compromised. The site was launched to allow members of the public to check if their credentials have been exposed in a data breach. Data from new breaches is automatically added to the repository of the website. Founded by security expert Troy Hunt, the site has records of over 13 billion accounts as of May 2024.
Through our integration with Have I Been Pwned, ADSelfService Plus can check if the password a user chooses has been previously involved in a security breach. If it has, ADSelfService Plus forbids the password and asks the user to choose a different one.
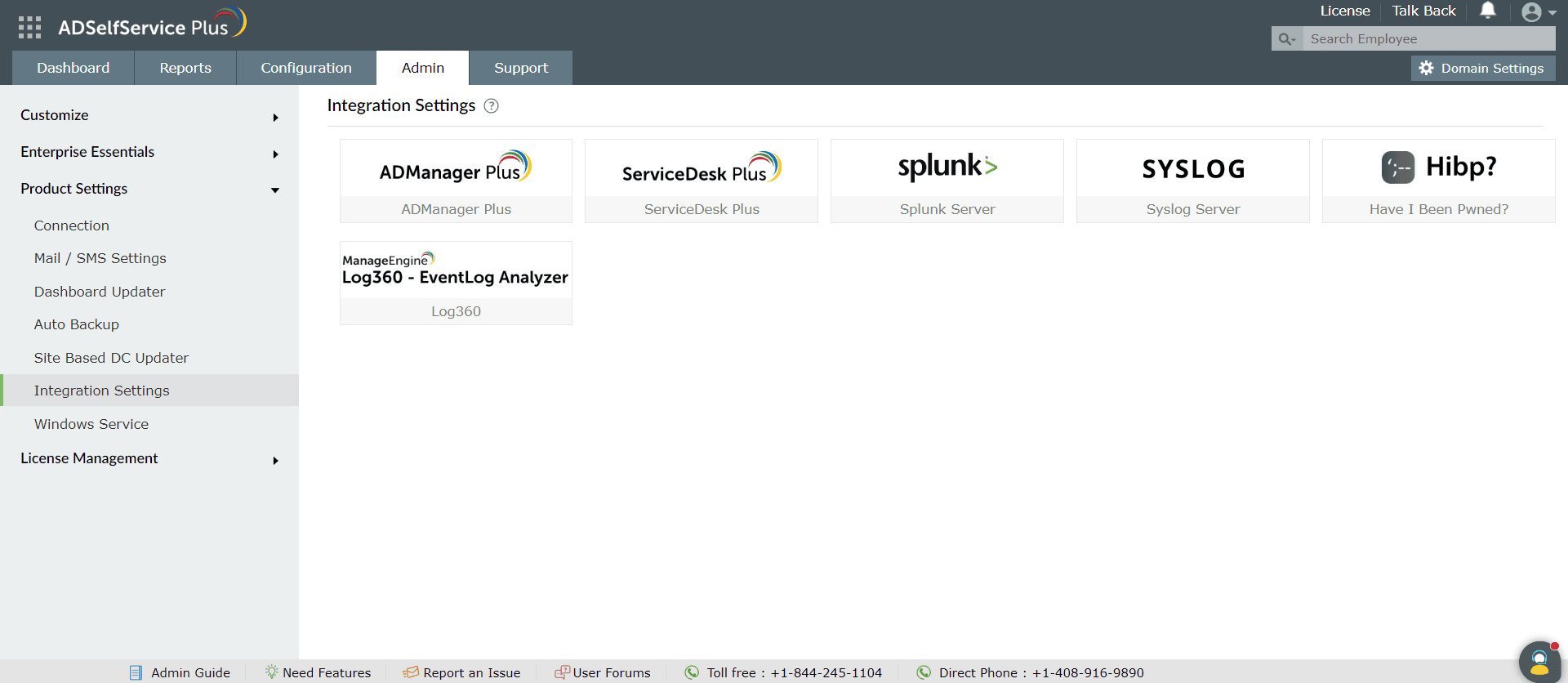
Easily integrate ADSelfService Plus with Have I Been Pwned and restrict the use of breached passwords.
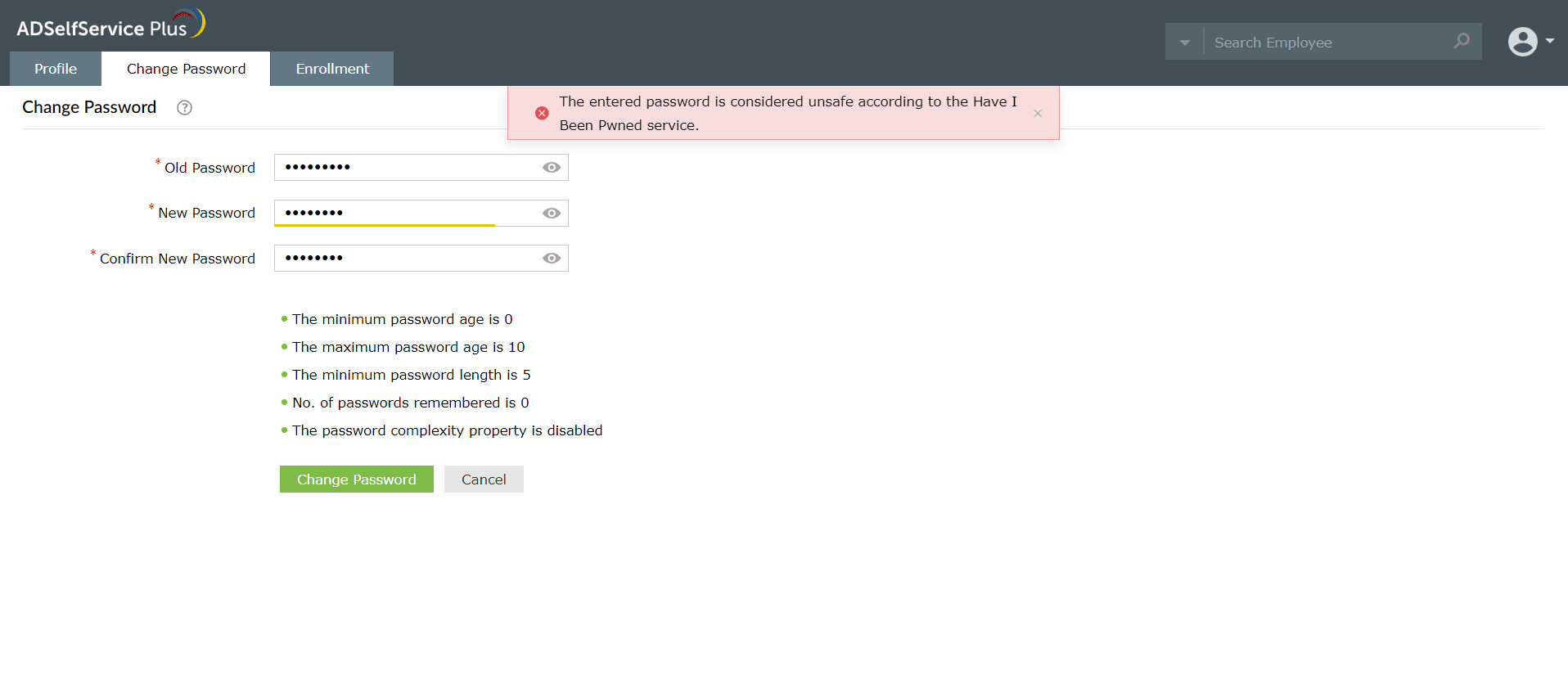
Alert users when they choose a breached password during a password change.
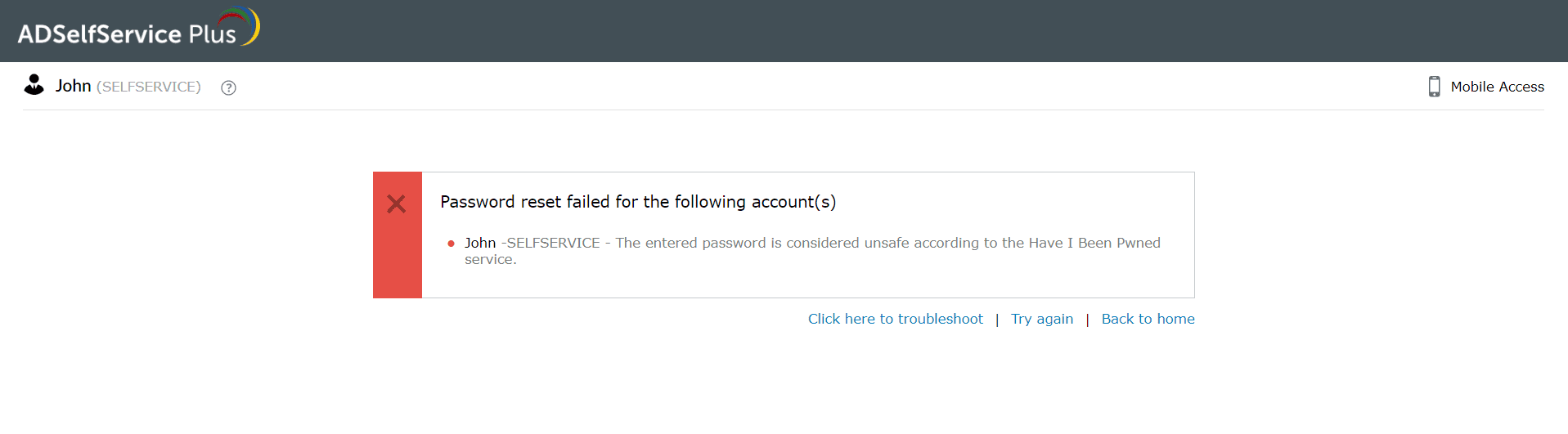
Alert users when they choose a breached password during a password reset.
Go beyond passwords
Traditional password authentication is vulnerable to many security risks because with enough time, threat actors can hack any password. While stronger passwords require more time and effort, they can still be cracked and, like all passwords, are still susceptible to phishing attacks. So, having passwords as the only security barrier between your network and bad actors is not advisable.
- Enforce MFA : Secure enterprise applications and machine access with adaptive MFA supporting 20 authentication factors, including FIDO passkeys, biometrics, and YubiKey.
- Enable passwordless authentication : Empower users to access enterprise applications without a password, instead using stronger authentication factors such as biometrics, FIDO passkeys, and custom TOTPs.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.










