Exceptions
All the vulnerabilities, misconfigurations, high-risk software that are discovered in your network appears under the Threats tab in the web console. However, if you wish to exclude the displayed item from being interpreted as a threat (vulnerability/misconfiguration/high-risk software) by Vulnerability Manager Plus, you can do so with the Threat Exception feature.
Applies to:
Exceptions can be either of the following type:
When components/applications/configurations in your systems are incorrectly identified as threats, you can mark them as false positive while defining exceptions.
Identified threats (vulnerabilities/misconfigurations/high-risk software) can be excluded as acceptable risk if they pose little to no risk and also include, but not limited to, some of the following conditions:
- When they're found to be affecting mission critical servers that have very thin patching window and can't afford to have extended downtime.
- When the patches that are released for those low risk vulnerabilities are found to be problematic during patch testing and may cause downtime or disrupt application functionality.
- Your organizations may have legitimate uses for certain business-critical practices that may also pose risk under certain conditions. For instance, shared folders facilitate centralize administration and provide a central location for users to store and access common files but folders shared with write permissions are displayed as misconfiguration under Threats tab, since ransomware and other malware can easily identify and spread to the computers that have shared folders with write permission to a compromised computer.
- When compensation controls such as host or network based intrusion prevention systems are already in place to mitigate the security risk of those detected threats.
A threat may found to be affecting multiple systems. You can control the scope of the exception by choosing the custom group to which the exception should be applied.
- A default group named, "All Computers Group" is created by Vulnerability Manager Plus. If you wish to exclude a threat for all the machines in your network, then you can choose "All computers group" in the custom group field. The excluded threat will no longer appear anywhere in the console except the Manage Exceptions view under the Threats tab.
- If you want to exclude a threat for a specific group of machines, then you can create separate custom groups based on OS, servers or remote office, etc., and specify that custom group while defining exceptions. Learn how to create custom groups. This is especially useful when you wish to exclude remediation to a particular group of machines. For instance, say a vulnerability or misconfiguration is excluded for a specific custom group, like custom group "Windows servers", and if it's found to be affecting any other machines outside this custom group, the vulnerability or misconfiguration will still be displayed in the appropriate view under Threats and the remediation can be applied only to the affected machines outside the custom group to which the particular threat is excluded.
Note
- When a new machine is added to the custom group for which exceptions are defined, all the threats that are excluded for that custom group will also be excluded to the newly added machine
- When a vulnerability is added to exception, the corresponding patch will not be declined. You'll still find those patches in the missing patches view. Patch deployment will not be affected in anyway by adding vulnerability exceptions. However, if you wish to decline the patch, you can do it from the Patches tab.
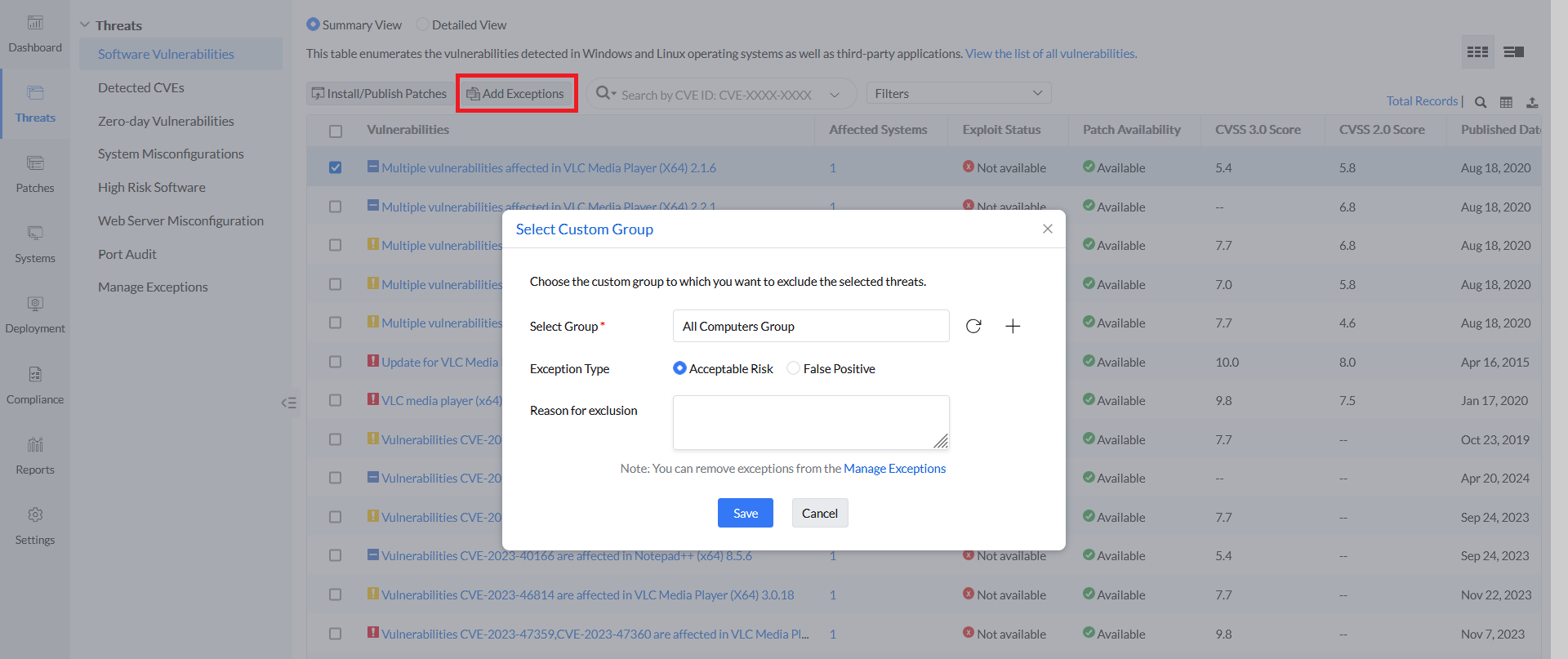
If you wish to add vulnerabilities, misconfigurations or high-risk software to the exception list, navigate to the appropriate view under Threats tab and follow the below steps:
- Locate and select the items that you want to exclude from being displayed as threats and select add exceptions.
- Select a custom group to which you wish to exclude those threats.
- Choose the exception type. You'll have the option to choose either false positive or acceptable risk.
- Specify the reason for exclusion.
- Click ok to add selected items to the exception list successfully.
You can also add/view exceptions individually for each system by clicking on the particular system under systems tab and accessing the drilled down view of vulnerabilities, misconfigurations and high-risk software present in those systems.
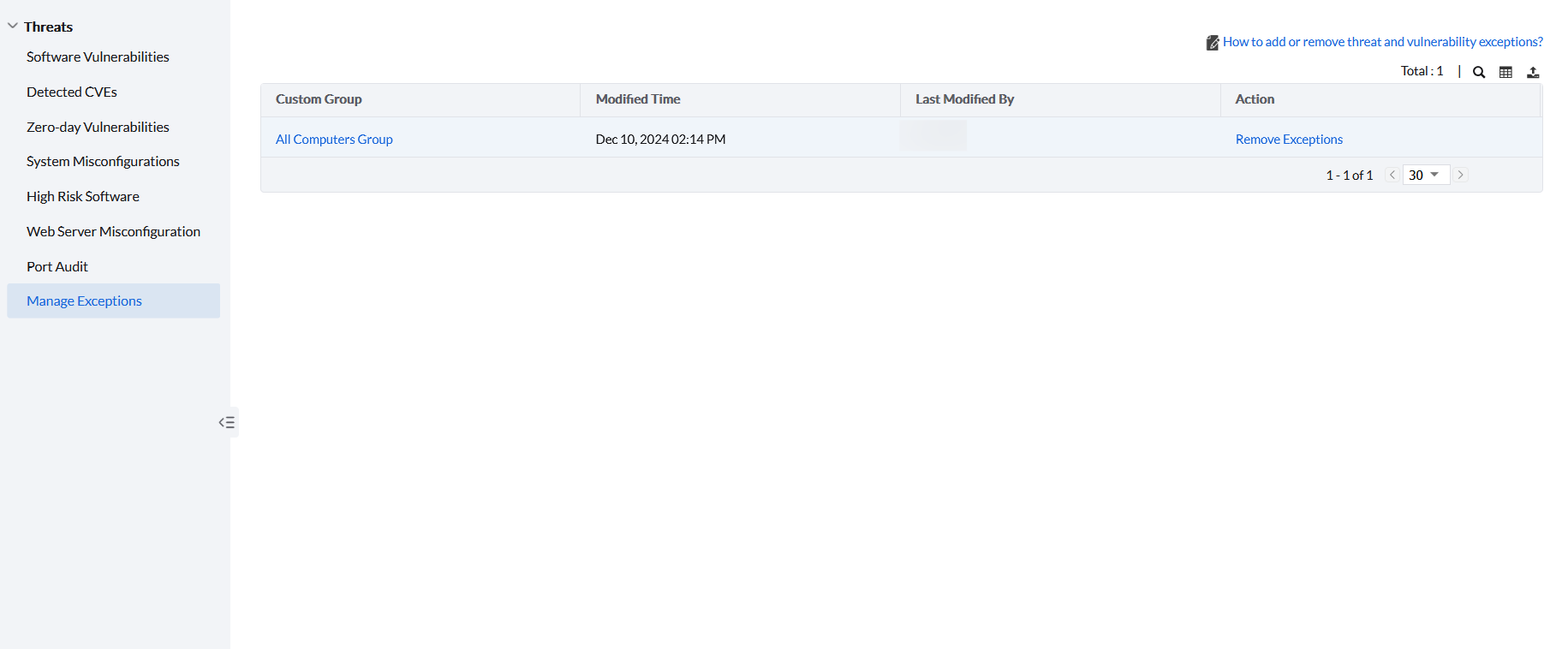
- You can remove exceptions only from the Manage exceptions view. To remove exceptions,
- Navigate to Threats → Manage Exceptions.
- Here, you will find a list of custom groups for which exceptions are defined.
- Click on Remove Exception under action to remove all the exceptions for a custom group.
- If you wish to remove exceptions individually for a particular custom group, select a group to view vulnerabilities, misconfigurations and high-risk software that are excluded for the group.
- Locate and select the items that you want to remove from exception and click on remove exception.



