What is cybersecurity?
Cybersecurity is the practice of protecting computers, networks, applications, and data from unauthorized access, attacks, or damage. It encompasses a variety of strategies including network security, application security, information security, operational security, disaster recovery, end-user education, and physical security. The goal is to safeguard the confidentiality, integrity, and availability of information against threats like viruses, malware, and social engineering attacks, like phishing.
With the growing reliance on digital technologies and the increasing volume of sensitive data online, cybersecurity has become indispensable for individuals, businesses, and governments. It aims to safeguard assets and maintain operational continuity, adapting continually to counteract emerging threats and vulnerabilities in the ever-evolving digital landscape.
Why is cybersecurity increasingly important?
In 2024, the global average cost of a data breach was USD 4.88 million, a 10% increase over a year. Surprisingly, 11% of leaders were "unsure if their company had a data breach during 2023," showing the need for better awareness. The vast majority (78%) of businesses did not experience breaches, but the risk triples for organizations with over 25 employees, highlighting the importance of scalable security measures for growing companies.
Global cybercrime costs are projected to increase by 15% annually, totaling $10.5 trillion by 2025. This is due to rising security expenses, as shown by a 2022 Accenture survey where 81% of participants deemed the costs of fighting cybercrime as unsustainable. IoT malware surged by 87% in 2022 due to more devices connecting online, expanding the potential for attacks. Significant breaches, like Yahoo's in 2013 and Cam4's data breach in March 2020, affecting a billion accounts, underline the urgency for robust personal data protection.
Given these statistics, cybersecurity is a critical concern for businesses of all sizes and industries. Effective cybersecurity measures, including AI and automation, can significantly reduce the cost and impact of data breaches, underscoring the importance of ongoing investment in cybersecurity infrastructure and training.
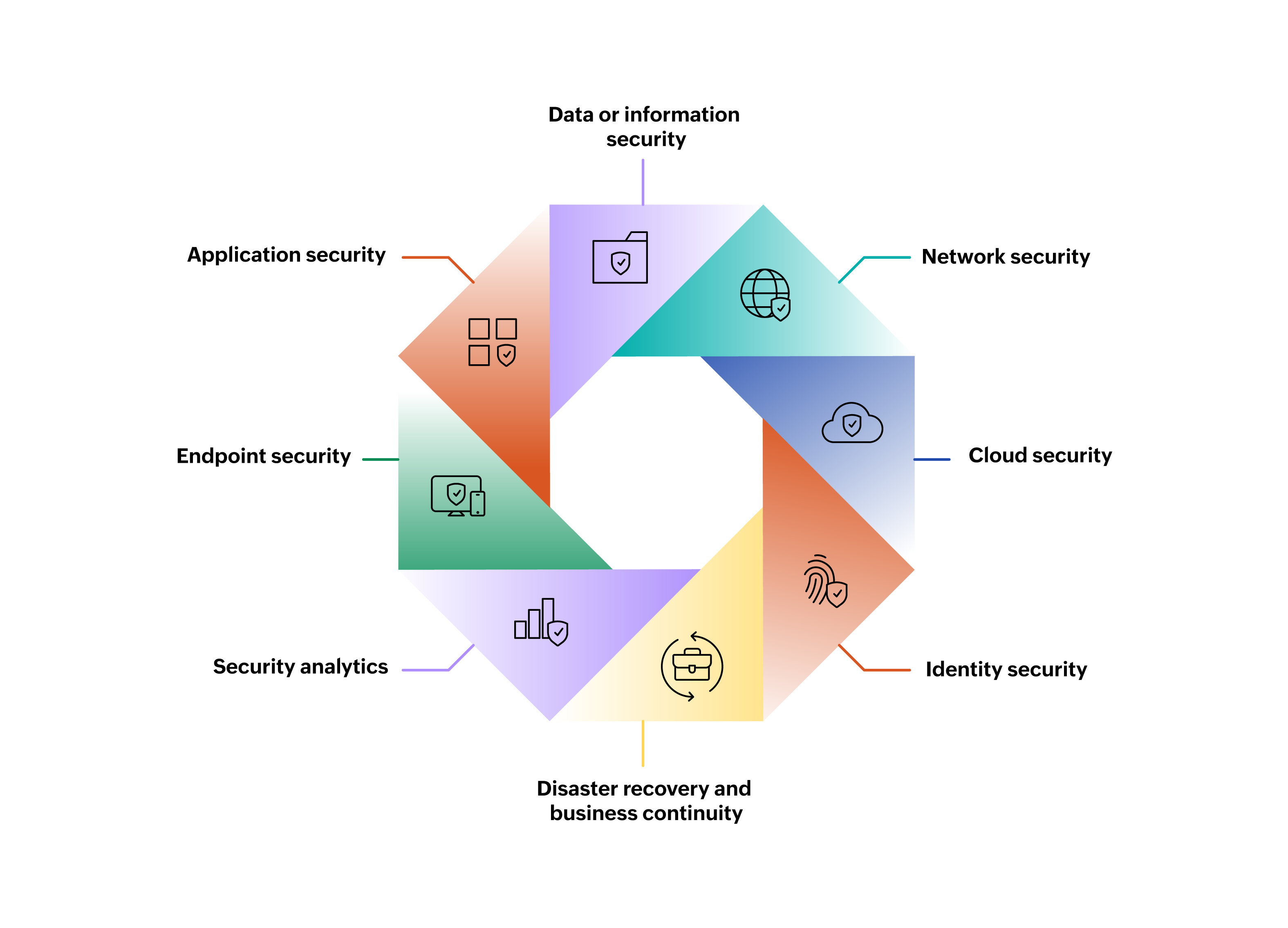
Key pillars of cybersecurity
Cybersecurity encompasses a wide range of fields and can be broken down into these key pillars:
Network security refers to the actions taken to protect the integrity and usefulness of data and networks. It involves implementing tools, technologies, and policies to safeguard against unauthorized access, misuse, and attacks. These measures include firewalls, intrusion detection and prevention systems, antivirus software, VPNs, and data encryption tools, ensuring that data traveling over the network is secure and protected from hackers and other threats.
Cloud security
As cloud computing grows, safeguarding cloud environments has become essential. This entails a robust security framework encompassing a combination of internal measures and external solutions. Cloud security posture management (CSPM) tools identify vulnerabilities and misconfigurations, while cloud workload protection platforms (CWPPs) provide continuous monitoring and threat detection for cloud-based applications. Additionally, cloud access security brokers (CASBs) act as gatekeepers, enforcing security policies and protecting sensitive data from unauthorized access.
Identity security
Identity security aims to protect all types of identities within an organization, including employees, devices, applications, bots, customers, and third-party vendors, from identity-based threats and attacks. Identity and access management (IAM) provides the foundational framework for managing these identities and controlling access to resources. Privileged access management (PAM) specifically secures high-value assets by controlling and monitoring privileged accounts. Meanwhile, identity governance and administration (IGA) ensures that identity life cycle management and access rights align with organizational policies and compliance requirements. By implementing robust IAM, PAM, and IGA solutions, organizations can significantly reduce the risk of data breaches and other security incidents.
Data or information security
Data or information security focuses on protecting sensitive information, using methods like encryption, access controls, data classification, and data loss prevention (DLP) measures, from unauthorized access, disclosure, alteration, or destruction.
Application security
Web applications face numerous threats. Application security counters these by addressing critical vulnerabilities, preventing malicious interactions, and adapting continuously to protect against new threats.
Endpoint security
Endpoint security is the process of protecting devices such as PCs, laptops, and mobile phones from cyberthreats. It includes important elements like next-generation antivirus (NGAV) and endpoint detection and response (EDR) to enforce security policies, identify threats, and react promptly to incidents by remotely wiping or containing affected endpoints. This security measure also defends these devices on a network or in the cloud against cybersecurity threats, like advanced malware and zero-day attacks. By investing in robust endpoint security, organizations can secure sensitive data and ensure business operations continue smoothly.
Security analytics
Security analytics is a sophisticated cybersecurity practice that leverages data collection and analysis to proactively identify and mitigate threats. This enables organizations to safeguard their critical infrastructure and financial well-being. By incorporating big data and threat intelligence, security analytics empowers organizations to detect a comprehensive range of threats, encompassing insider activity, persistent cyberattacks, and targeted assaults from external actors.
Disaster recovery and business continuity
Disaster recovery policies outline the organization's response to a cybersecurity incident or any event leading to operational or data loss. These policies detail how the organization restores operations and information to pre-incident levels. Business continuity plans are utilized to maintain operations without specific resources.
Advantages of implementing cybersecurity practices
Implementing cybersecurity strategies can help businesses:
Better protect themselves against cyberthreats: Cybersecurity reduces the risk of being hit by diverse cyberthreats, ranging from phishing to ransomware, enhancing resilience.
Ensure data privacy and protection: Maintaining data security is essential for protecting privacy, as it guards sensitive information, such as personal details, trade secrets, and healthcare data, from unauthorized access. This also safeguards important business assets, like trade secrets, from cybercrime, thus preserving a company's competitive edge.
Minimize operational disruptions: By preventing cyber disruptions, cybersecurity ensures that businesses can maintain smooth operations, avoiding financial and reputational damage.
Ensure regulatory compliance: Cybersecurity measures are a key part of many data privacy mandates and industry regulations. Implementing cybersecurity best practices can help in the process of complying with these regulatory requirements and help avoid financial penalties.
Maintain customer trust: Implementing strong cybersecurity builds customer confidence in an organization's commitment to data protection.
Prevent financial losses: Preventative cybersecurity measures can help businesses avoid the significant expenses associated with recovering from cyberattacks.
What are the different types of cybersecurity threats?
Staying updated on new technologies, security trends, and threat intelligence can be difficult, but it's essential for safeguarding information and assets from various cyberthreats. Types of cyberthreats include:
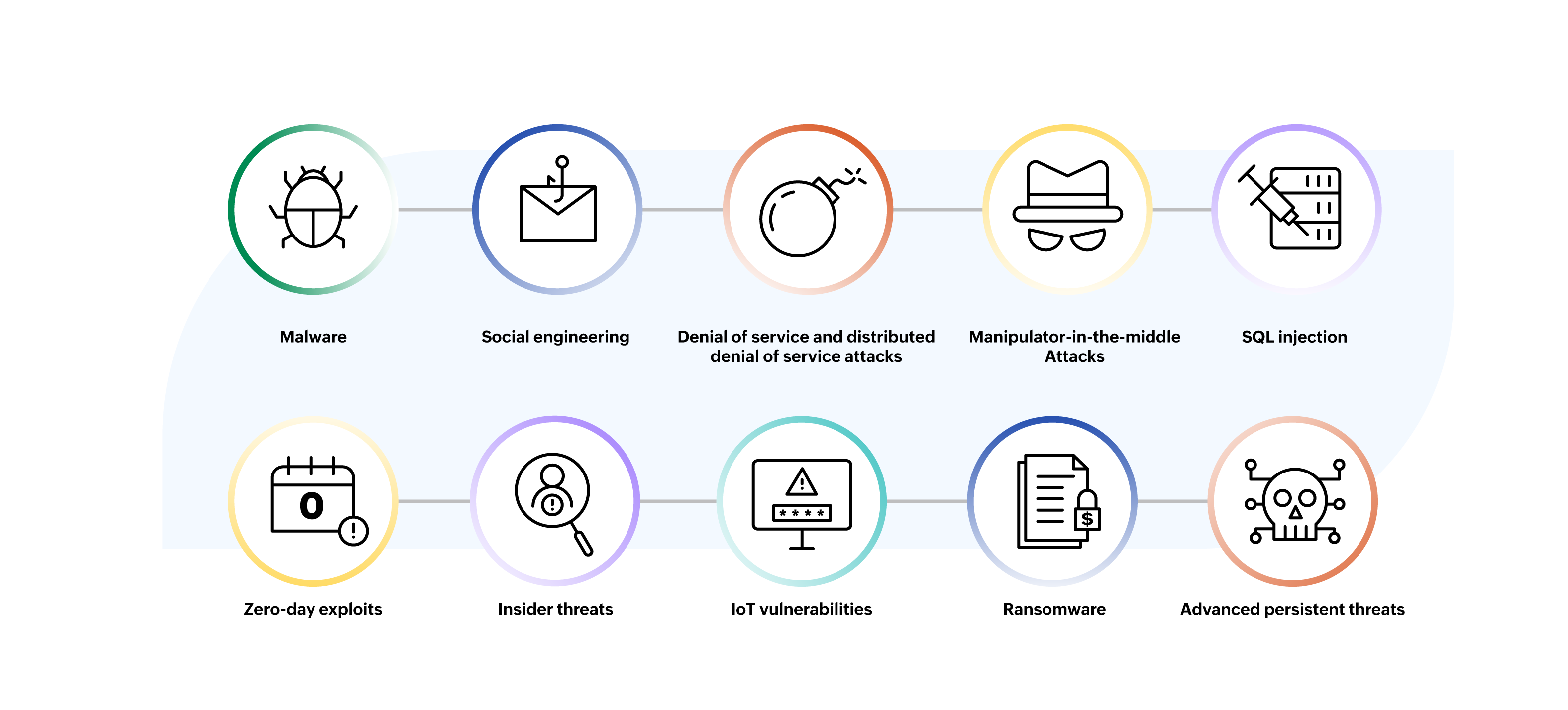
Malware
Malicious software, including viruses, worms, Trojans, ransomware, spyware, and adware, poses a significant risk to your digital security. These programs can infiltrate your devices, steal sensitive information, or render your systems unusable.
Social engineering
Social engineering techniques involve manipulating individuals to disclose sensitive information or engage in actions that jeopardize security. Attackers often use psychological manipulation or deception through emails, phone calls, or impersonation to trick victims. Examples of social engineering attacks include phishing, whaling, baiting, tailgating, etc.
Denial of service and distributed denial of service attacks
Denial of service (DoS) and distributed denial of service (DDoS) attacks aim to disrupt online services by flooding target systems or networks with an overwhelming volume of traffic. These attacks can render websites inaccessible, causing significant downtime and financial losses.
Manipulator-in-the-middle attacks
Manipulator-in-the-middle (MITM) attacks occur when hackers intercept and manipulate communication between two parties, potentially gaining access to sensitive data or injecting malicious content into the communication stream.
SQL injection
Web apps using SQL databases are vulnerable to SQL injection attacks. Attackers inject malicious SQL code to gain unauthorized access to databases, steal data, or manipulate website functionality.
Zero-day exploits
Zero-day exploits focus on vulnerabilities in software or hardware that have not been patched by vendors yet. Cybercriminals exploit these vulnerabilities to launch attacks before security patches are released, posing a significant threat to organizations and individuals.
Insider threats
Individuals within organizations can pose security risks by intentionally or unintentionally compromising sensitive data or systems. Insider threats may include employees, contractors, or partners with access to confidential information.
IoT vulnerabilities
Internet-connected devices, such as smart home appliances and industrial systems, often lack adequate security measures, making them vulnerable to exploitation. Attackers can compromise IoT devices to gain unauthorized access or disrupt operations.
Ransomware
Ransomware attacks encrypt files or systems and demand payment for decryption keys. These attacks can have devastating consequences, causing data loss, financial damage, and reputational harm to individuals and organizations.
Advanced persistent threats
Advanced persistent threats (APTs) are sophisticated, targeted attacks carried out by well-funded adversaries with specific objectives, such as espionage or sabotage. APTs involve stealthy infiltration and persistent monitoring of target networks over an extended period.
Top cybersecurity challenges today
The top enterprise cybersecurity challenges paint a picture of an environment where threats are not only persistent but are also evolving in complexity, driven by advancements in technology and changes to the cyber landscape. The significance of adaptive and proactive security measures is highlighted by these challenges:
The rise of AI and GenAI
AI and GenAI platforms, such as ChatGPT, have made cybersecurity attacks more sophisticated. Cybercriminals are now using generative AI to improve their phishing attacks. This means that traditional phishing attacks can now appear more realistic and professional, as errors are eliminated and writing styles are improved. Additionally, some criminals are taking advantage of deepfake technology to make their scams and attacks even more convincing.
Beyond phishing, AI presents broader issues such as the risks of data exposure, where sensitive information might be accidentally revealed when using GenAI models. Data poisoning, compliance issues, ethical AI use, and robust governance are other concerns. GenAI models also generate large amounts of data (leading to data sprawl) and unauthorized, non-compliant AI use (shadow AI) poses additional risks to organizations.
Ransomware as a service
Ransomware as a service (RaaS) is a cybercrime model where developers create and distribute ransomware to affiliates. Developers provide affiliates with tools and resources to conduct attacks. This model makes ransomware attacks more accessible and profitable. It lowers the entry barrier for less-skilled individuals and has led to an increase in ransomware variants and attacks. RaaS makes it difficult for law enforcement to track and prosecute cybercriminals and poses a challenge for cybersecurity professionals due to its constantly evolving nature.
Data deluge
The data deluge poses a major cybersecurity challenge by complicating data management and increasing the risk of data leakage. With vast amounts of data, ensuring privacy, integrity, and regulatory compliance becomes daunting, making it harder to spot breaches. The risk is higher for personal data, which is attractive to cybercriminals. For example, unauthorized data access or accidental data exposure can lead to ransomware attacks. To mitigate these risks, organizations must adopt advanced, scalable security measures and maintain vigilant data governance.
Mobile malware
The rise of mobile malware, exacerbated by bring your own device (BYOD) policies, poses a critical cybersecurity challenge. BYOD policies, while increasing flexibility, expose corporate networks to heightened risk, as employees' devices, often less secure, can easily be compromised.
Cybercriminals exploit this by disguising malware within seemingly benign apps like QR code readers or games available on both official and unofficial app stores. These malicious apps, including altered versions of popular ones, leverage their apparent legitimacy to infiltrate devices. Once infected, these devices become gateways for unauthorized access to sensitive corporate data.
Supply chain attacks
Ensuring the security of the IT supply chain is essential because any weaknesses can affect many systems. The key to a secure supply chain is making sure that all software and hardware assets sourced from outside suppliers are safe and reliable. Even if an organization has strong security practices in place, it can still be vulnerable to cyberthreats if its partners and vendors do not follow similar security practices. The challenge is growing with more complex attacks targeting both software and hardware. To guard against these risks, it is crucial to check the security of all third-party components thoroughly.
Cybersecurity talent gap
The field of cybersecurity is facing a critical shortage of skilled talent, as the demand for experienced professionals outpaces the supply available in the workforce. This shortfall presents a significant challenge for organizations trying to uphold robust security practices. Compounding the issue is the lack of adequate cybersecurity training within the existing workforce.
With the increased importance of IT in modern organizations, there is an increasing need for well-staffed cybersecurity teams capable of analyzing, overseeing, and reacting to security incidents. "Eighty-three percent of IT security professionals say burnout causes data breaches" according to Devo Technology's cybersecurity burnout survey. Forrester states that "57% of directors state stress and burnout as the top reason for leaving their position." Additionally, 64% of security team members report that stress has negatively impacted their productivity. As the demand for skilled workers grows and the challenges in IT become more complex, current employees are working twice as hard, burning out, and leaving their jobs, further widening the skills gap.
Common cybersecurity myths
There are many misconceptions and myths in the cybersecurity field that can result in poor choices and higher risks. Here are some cybersecurity myths we've debunked:
I only need strong passwords, firewalls, and an antivirus solution to be secure
While these are crucial, it is important to understand that all these solutions are vulnerable to compromise. These three elements are fundamental to cybersecurity, but techniques like brute-force attacks or social engineering can be used to bypass supposedly secure passwords. Therefore, it is vital to implement additional security measures such as MFA for enhanced protection. Keeping your firewall secure requires regular antivirus software updates and proactive monitoring for breaches.
It is not my responsibility to handle cybersecurity
When discussing the importance of maintaining a company's security, it is not solely the responsibility of the IT security team. All employees play a crucial role in ensuring the security of their business. Approximately 58% of insider attacks occur as a result of careless insiders. Educating employees on cybersecurity and their responsibilities is vital. Training will equip them with the skills needed to recognize threats and enhance their actions.
It is okay to use the same password and username across all domains
Using the same login information across multiple websites may seem convenient, but it poses a significant security risk. Cybercriminals are aware of this practice and can exploit it using automated tools like bots and AI. Hackers can easily access your data through a credential-stuffing attack. If your credentials are compromised and used across various accounts, it can lead to a domino effect of security breaches. Prioritizing convenience should not come at the expense of security. Use a password manager tool to keep track of unique passwords for all your accounts.
I am an SMB; cybercriminals will not attack me
Small- and medium-sized businesses (SMBs) are not as safe as they may think, which makes them easy targets for cyberattacks. All businesses that handle sensitive information are at risk, with over 10,000 attacks per day reported by the Federation of Small Businesses in the U.K. These businesses often have poor security measures, such as no formal password policies, outdated software, and a lack of security software.
While hackers may prefer larger enterprises for financial gain, small businesses can suffer devastating consequences from a cyberattack, potentially leading to closure. A small business is hacked every 19 seconds in the U.K. To protect themselves, small businesses with limited cybersecurity budgets should seek guidance from IT support services to implement effective defenses.
We regularly test our security posture to ensure our security
Regular penetration tests may not be sufficient. These are simulated attacks that assess your defenses and find vulnerabilities, but they are just a snapshot of your security at a specific moment. To effectively protect against evolving threats and cybercriminal tactics, it is essential to combine penetration tests with other security assessments and monitoring tools that offer ongoing visibility and updates on your security status.
Cybersafety tips for individuals to protect themselves against cyberattacks
- Keep your software and operating systems up to date to stay secure with the most recent security updates.
- Utilize antivirus software to detect and remove threats, and ensure your software is regularly updated for optimal protection.
- Ensure that your passwords are strong and not easily guessable.
- Avoid opening email attachments from unfamiliar senders, as they may contain malware.
- Be cautious of clicking links in emails from unfamiliar senders or unknown websites, as it could be a phishing attempt.
- Unsecured Wi-Fi networks in public places should be avoided, as they can make you susceptible to manipulator-in-the-middle attacks.
Top best practices for cybersecurity
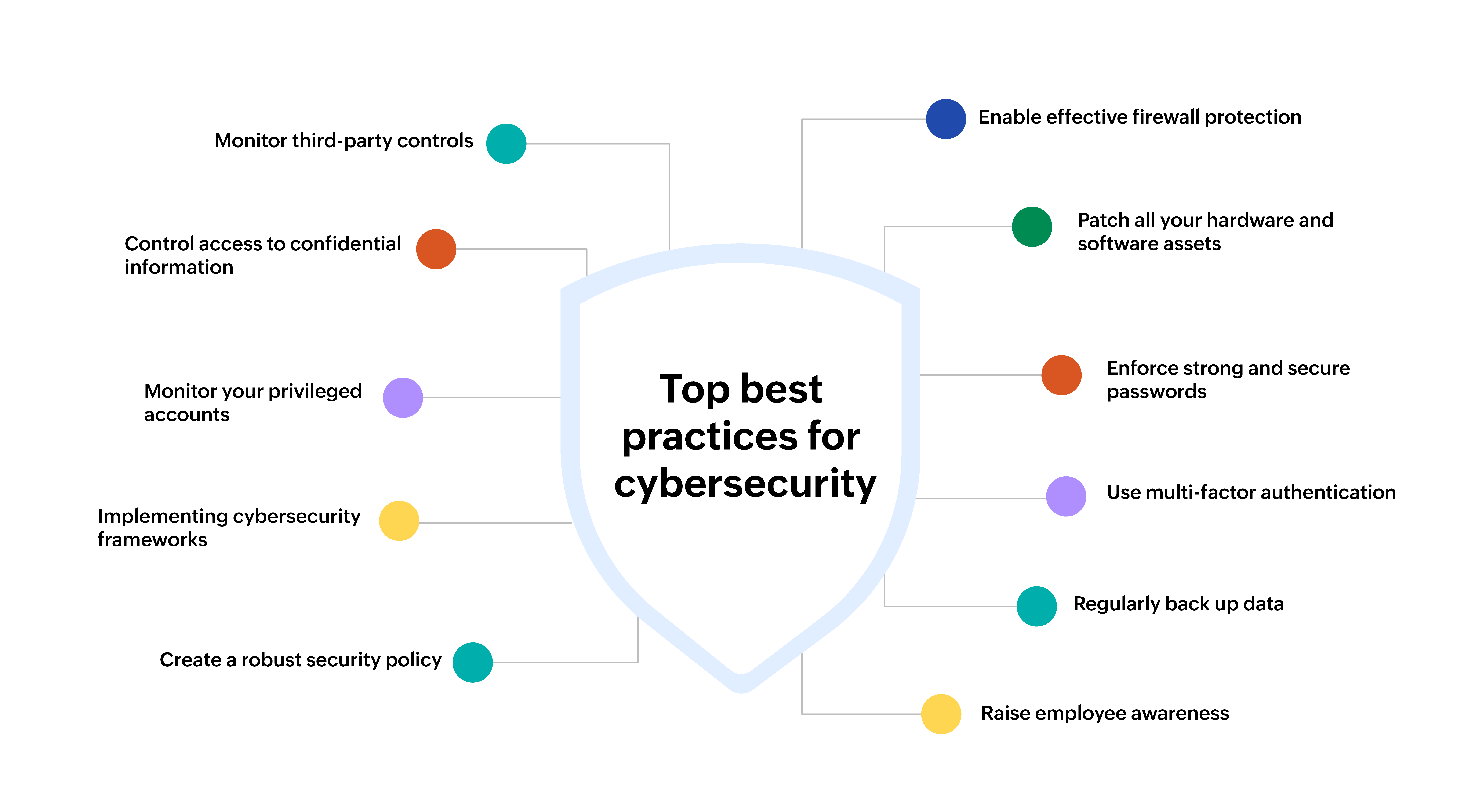
Enable effective firewall protection
Using a firewall to protect the company network is important to avoid cyberattacks. The firewall blocks unauthorized users from accessing websites, emails, and other online sources of information. It is crucial to have firewall software installed for any employee working on a company device.
Patch all your hardware and software assets
Update your security software, servers, and operating systems regularly to stay current with the latest versions. Keep your antivirus and anti-malware solutions up to date to combat security breaches effectively. Installing updated security software on all devices and networks is crucial for protection against the newest cyberthreats.
Enforce strong and secure passwords
It is crucial to use a strong and intricate password to prevent cybercriminals from gaining access to company data. A secure password typically comprises 10–14 characters with a mix of numbers, symbols, lowercase letters, and uppercase letters, but it is also important to update the password regularly to deter hackers from infiltrating the system.
Use multi-factor authentication
Multi-factor authentication enhances data protection by adding a security layer that prevents hackers from gaining unauthorized access. Even if a hacker obtains your password, they would still need to pass through additional authentication factors such as security code, OTP, fingerprint, voice recognition, and more. This advanced security measure helps secure your data and enables better access control by differentiating between users with shared accounts.
Regularly back up data
Backing up data has become more important in recent times. Data is a top targeted for cybercriminals, so it is crucial to back up files and store them securely according to company security protocols. It is vital to ensure that data is well protected, encrypted, and regularly backed up.
Following a data backup strategy like the 3-2-1-1-0 rule can ensure the effectiveness of your backup strategy. The rule includes the following steps: Keep at least three copies of your data, store the copies on two different types of media, keep one copy off site, store at least one of the copies offline, and test your backups regularly for zero errors.
Raise employee awareness
Companies prioritize employee training on cybersecurity policies and updates. Employees must comply with the company's policy and be aware of threats. Learning from breaches and understanding the impact is crucial. Companies value feedback and new ideas for stronger security measures.
Monitor third-party controls
Controlling access from external parties is a key component of a security plan. Allowing third-party individuals to have unrestricted access to your data increases the risk of insider attacks. Monitoring the actions of third-party entities is crucial in safeguarding your data from breaches. It is vital to limit the access of third parties to specific areas and remember to deactivate their access once their work is complete.
Control access to confidential information
IT teams are in charge of overseeing access to information, which involves regulating access to security passwords, confidential data, and other sensitive information. Only a select few individuals may be authorized to handle the company's financial data and proprietary information. Typically, employees are granted minimal access privileges and may only be given additional access upon request or under certain conditions.
Monitor your privileged accounts
Privileged users have the potential to be an asset or a significant risk to a company's data security. It is crucial to limit the number of privileged users and promptly deactivate their accounts when they leave the company. Implement user activity monitoring solutions to detect any suspicious behavior within the network.
Implementing cybersecurity frameworks
Implementing cybersecurity frameworks, like the NIST Cybersecurity Framework (CSF), ISO 27001, or CIS Controls, is important for organizations to protect their digital assets and information. These frameworks help with managing and reducing cybersecurity risks, improving incident response, and increasing security awareness. This proactive approach helps organizations detect and respond to threats better, lowering the chances of data breaches and security incidents.
Create a robust security policy
A formal policy serves as a comprehensive guide for all cybersecurity practices within an organization, ensuring alignment between security experts and employees in enforcing data protection rules. Regular updates to policies are necessary to enhance security capabilities and prevent malicious attacks. Implementing cybersecurity frameworks and best practices as recommended by industry or domain bodies like NIST and CIS is crucial.
A written cybersecurity policy acts as a formal guide for all security measures in a company, ensuring that security specialists and employees are on the same page and can enforce rules protecting data. However, different departments' workflows may differ, requiring updates to policies to strengthen security measures against malicious attacks. It is essential to consult with all stakeholders when drafting the policy to find a balance between productivity and security, ensuring that cybersecurity policies don't impact employees' work.
How to plan and build a cybersecurity strategy for your business
Developing a cybersecurity strategy for your business requires dedication, but it can determine whether you outperform your competitors or face closure. Follow these fundamental steps to create a successful security strategy.
Step 1: Understand your cyberthreat landscape
To develop a strong cybersecurity strategy, it's crucial to understand the types and severity of attacks your organization faces and stay informed about recent incidents among competitors. This helps you grasp your cyberthreat landscape. Additionally, keeping up with predicted trends, such as the growth of ransomware and supply chain vulnerabilities, is essential. Equally important is having a comprehensive understanding of your internal IT infrastructure, including the types and variety of assets, the third-party tools your employees use, and the presence of shadow IT.
Step 2: Assess your cybersecurity maturity
Assess your organization's cybersecurity level using a framework like the NIST CSF. Take into account the technology, governance, and policies related to cyber-physical systems, IoT, operational technology, and traditional IT. Set maturity targets for the next three to five years using the same framework. Focus on improving network security to prevent distributed denial-of-service attacks and establish strong backup and recovery measures to defend against ransomware. For remote work policies, secure temporary tools used during the pandemic and aim for specific maturity levels as new strategic goals.
Step 3: Determine how to improve your cybersecurity program
Establish a baseline and determine your desired cybersecurity goals. Identify the necessary tools and capabilities to reach these objectives. Consider resource consumption and weigh options for improvement. Involve the upper management in the decision-making process. Ensure understanding of the need for changes to protect the organization from cyberthreats. Utilize any existing plans for future success.
Step 4: Document your cybersecurity strategy
After getting approval from management, document your cybersecurity strategy thoroughly by updating risk assessments, plans, policies, guidelines, and procedures. Clearly define responsibilities and involve those who will be implementing the strategy. Explain the changes and emphasize their importance to gain support. Also, remember to update cybersecurity awareness and training efforts, as everyone plays a role in improving security. As risks change, so should cybersecurity culture.
Step 5: Monitor and reassess security threats and strategies
Creating a cybersecurity strategy is an ongoing process with challenges. It is crucial to regularly monitor and reassess your organization's cybersecurity maturity. This includes internal and external audits, tests, and simulations. Be prepared to adapt your strategy to new threats and changes in technology or assets.
Achieving comprehensive cybersecurity with ManageEngine
Safeguard your employees, network, devices, and information from both internal and external risks using ManageEngine's IT security solutions.
The increased use of cloud solutions and hybrid work has expanded organizations' potential points of attack. Cyberattacks, such as ransomware and social engineering, are more frequent and damaging, with the average cost of a data breach reaching USD 4.45 million in 2023 according to IBM's report.
ManageEngine offers cybersecurity solutions to help protect your organization from these growing threats. Our solutions can help your organization implement security best practices like the CIS Critical Security Controls, frameworks like the NIST CSF, and Zero Trust security to strengthen your security defenses and safeguard your people, data, and devices.