MFA Trusted Machines Report
Users can opt to trust their machines for MFA (i.e., save their MFA verification for machine logins) for a specified number of days. The MFA Trusted Machines report displays details of active user-machine login agent MFA trusts, including the username, the machine name or IP address, the time the trust was initiated and the trust validity period.
This report also enables admins to search for specific user-machine MFA trusts and remove them.
Report generation
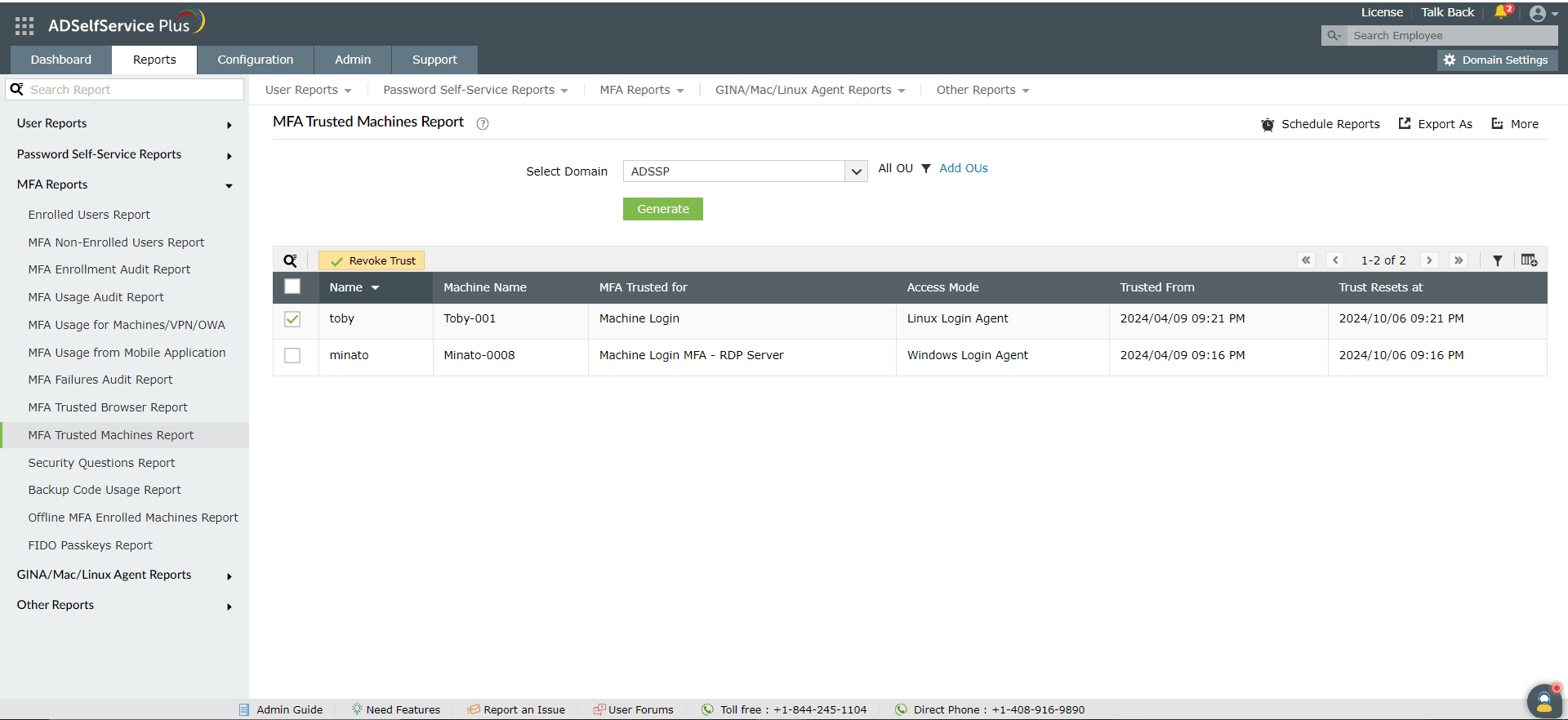
You can generate the MFA Trusted Machines Report by following these steps:
- Log into the ADSelfService Plus admin portal with administrator or operator privileges and navigate to Reports > MFA Reports > MFA Trusted Machines Report.
- Specify the domain in which to search using the Select Domain option.
- Specify OUs (if necessary) using the Select OUs option.
- Click Generate.
Revoking Trust
You can select any of the entries in the report to display the Revoke Trust button, which can be used to revoke any of the active user-device MFA trusts.
Report customization
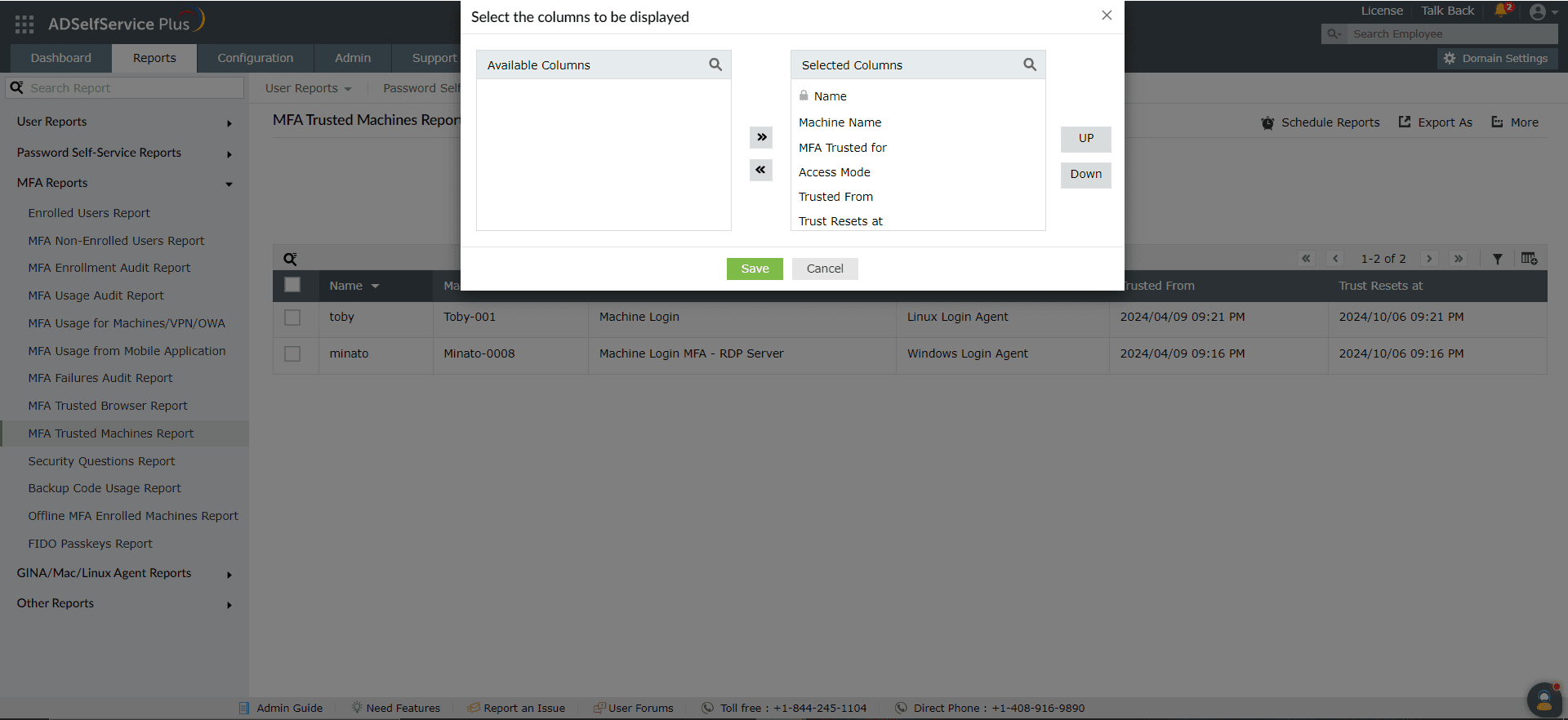
- Adding or removing columns: To add or remove columns, click the Add/Remove Columns [
 ] option at the far right of the report. In the Select the columns to be displayed pop-up that appears, select the required fields under Available Columns and click the right arrow (>>) to move them to the Selected Columns. To remove columns, select the unused fields under Selected Columns and click the left arrow (<<) to move them to Available Columns.
] option at the far right of the report. In the Select the columns to be displayed pop-up that appears, select the required fields under Available Columns and click the right arrow (>>) to move them to the Selected Columns. To remove columns, select the unused fields under Selected Columns and click the left arrow (<<) to move them to Available Columns.
- Ordering the columns: The columns' positions can also be altered by selecting a value under Selected Columns and using the Up and Down options to change its position.
Advanced Filtering
- Once the report is generated, the entries can be narrowed-down based on the following parameters by clicking the Advanced Filter [
 ] icon at the far right of the report.
] icon at the far right of the report.
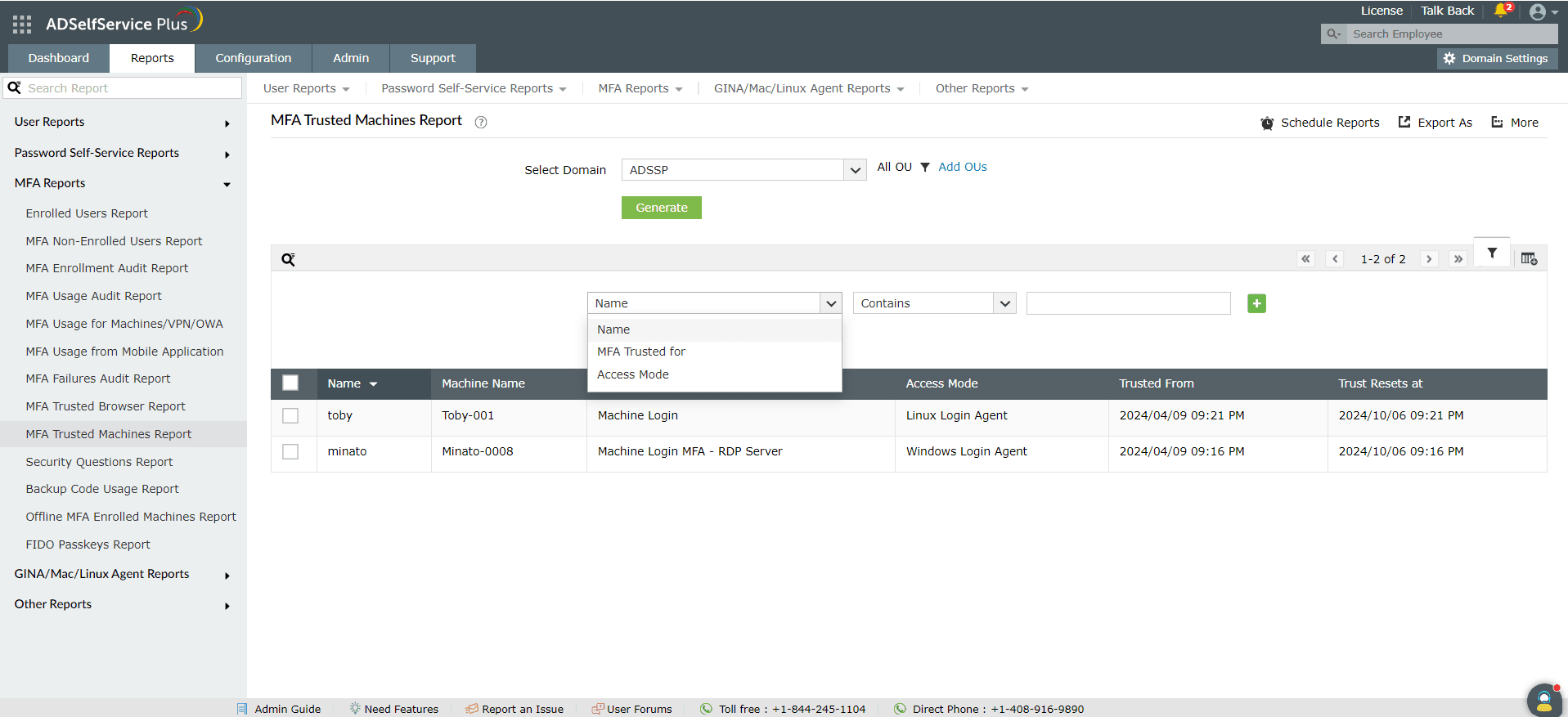
- Name: This option lets you narrow-down users with active user-device trusts by username. The conditions available to refine this include Contains, Does Not Contain, Equals, Is Not Equal To, Starts With, and Ends With.
- Access Mode: This option can be used to display active MFA device trusts for the Linux Login Agent, Windows Login Agent, or the macOS Login Agent.
Searching
- Click the search icon [
 ] to look for specific data in the report.
] to look for specific data in the report.
- Specific users can be searched for using their username or Machine Name.
- Searching happens using the criteria " contains ". For example, if the username column is searched for the word " jack ", then all usernames containing the sequence " jack " will be displayed as a result.
Sorting
Click any of the column headers to view the report's entries in ascending or descending order.
Schedule Reports, Export As, and More
- The Schedule Reports option can be used to schedule the generation of reports at specified intervals, and automatically email them to administrators or specific email addresses. Learn to schedule reports here.
- The Export As option at the top-right corner of the page helps export the report in CSV, PDF, XLS, XLSX, HTML, and CSVDE formats.
- The More option at the right corner of the page lists the Printable View, Send Mail, and Export Settings options.
- The Printable View option can be used to preview and print the report.
- The Send Mail option can be used to email the report to the desired email addresses.
- Additionally, you can configure custom Export Settings, such as a personalized title for the report and a header logo that you may wish to display on each page.
Don't see what you're looking for?
-
Visit our community
Post your questions in the forum.
-
Request additional resources
Send us your requirements.
-
Need implementation assistance?
Try OnboardPro



