Unified Infrastructure Monitoring
As the size of your organization increases, the size of your network infrastructure grows with it. This is why it's no longer sufficient to use a silo-based approach where each network function is monitored by an individual tool for network infrastructure monitoring.
A typical network infrastructure is comprised of multiple processes, and it's vital to have a unified infrastructure monitoring tool to unite all of these individual silos and collectively monitor them to achieve overall efficiency.
Different silos of infrastructure monitoring
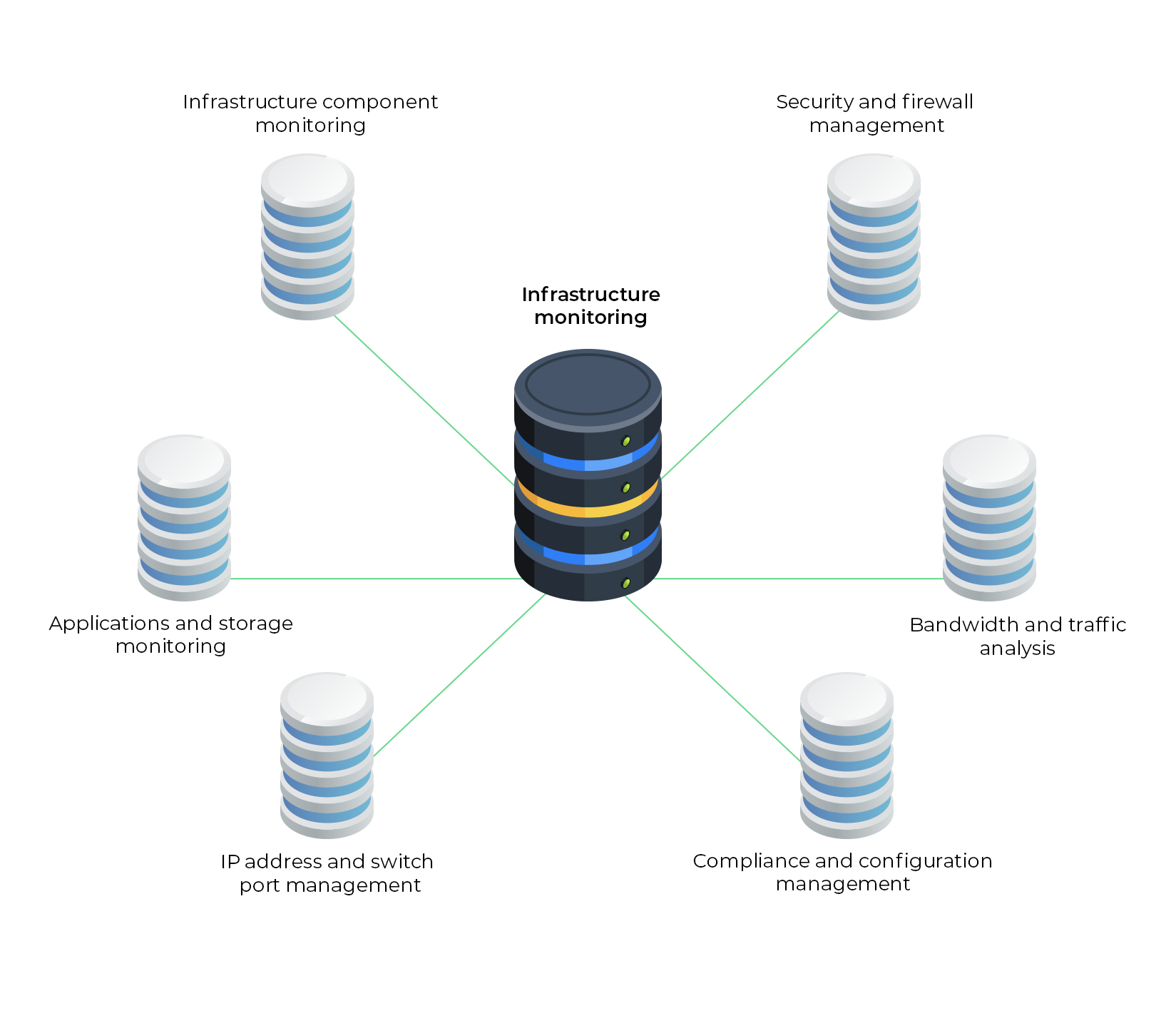
1. Infrastructure component monitoring
Infrastructure components can be broadly classified into physical and virtual components and have to be properly incorporated into your IT infrastructure. These new components need to be carefully configured, and the ones already existing in your infrastructure need to be monitored for health and availability. They also have to be updated with the latest configuration to prevent out-of-sync issues with new devices.
To ensure efficient system performance, the various metrics of these components such as CPU utilization, memory utilization, process monitors, system monitors, etc. are monitored for in-depth analysis. This greatly assists with capacity planning and reducing energy consumption.
2. Security and firewall management
Firewalls are the first line of defense against malware, hackers, viruses, and other cyber threats. Almost every organization is equipped with a firewall because not only does it safeguard your sensitive data, a competent firewall will generate security standards reports that will assist you in complying with security compliance laws such as PCI DSS, ISO 2700, NIST, SANS, NERC-CIP, etc.
Firewalls operate by scrutinizing log activities and monitoring for any spike in activity, identifying and eliminating rogue devices, addressing access point vulnerabilities, and more. Firewalls extend their protection to remote devices via VPNs for a secure work environment away from office.
3. Compliance and configuration management
Security breaches are becoming increasingly common, and even large-scale organizations are struggling to secure their data and prevent data theft. This is why organizations invest in configuration and compliance management tools. Not only will it help you with maintaining compliance with leading standards such as Cisco IOS, SOX, HIPAA, and PCI DSS, but it will also proactively alert you when a compliance breach is about to occur, allowing preventive measures to be employed.
Configuration management is the process of establishing and maintaining system performance. A competent configuration management tool saves your business by preventing critical systems from plunging into unscheduled downtime by keeping a tight leash on your network configurations.
Configuration management involves performing automatic configuration backups that can be deployed as soon as a misconfiguration is detected. This process also involves employing role-based access, restricting critical configuration changes to the super admins, saving human effort by automating device updates, and more to help you better understand the changes that will be implemented in the system and track configuration changes in real time.
4. Bandwidth and traffic analysis
Bandwidth and traffic monitoring is used to understand the bandwidth availability and usage patterns on your infrastructure and understand its traffic flow, usage, bandwidth hogs, and network strains in real time.
By monitoring your bandwidth and traffic, you can keep the application running 24x7, lag-free, with minimal jitter and latency.
Bandwidth analysis and traffic shaping is performed by leveraging flow technologies such as NetFlow, Sflow, and jFlow. With this data, advanced reports (eg: forecast reports) can be generated to facilitate bandwidth capacity planning to better manage your existing IT environment and accommodate its future growth.
5. IP address and switch port management
IP address management (IPAM) is used to plan, track, and manage your infrastructure's IP address space. With this, IT admins can ensure the repository of assignable IP addresses is always updated, gain improved visibility over IP resource management, and perform IP address delegation with better clarity. Having access to IPAM data makes it easier to identify potential data breaches or device misuse within an organization.
IPAM tools periodically scan the routers and subnets for rogue IPs, allowing the admin to flag and block them from accessing the system. Similarly, switch port management is used to track port usage and manage inactive ports.
6. Applications and storage monitoring
In today's digital world, speed is everything. Having applications and websites that are slow to respond will affect end users and have an impact on business productivity and profits alike.
This is where application monitoring comes in handy. It enables you to monitor all your business-critical applications and ensure they're performing properly. It also helps to generate reports for in-depth performance analysis. Applications such as custom web applications, mobile applications, popular technologies across servers, virtual machines, cloud applications, containers, application servers, databases, big data stores, middleware and messaging components, web servers, web services, and ERP suites can be monitored.
Increasing storage can temporarily fix your organization's storage needs, however, in the long run, it's imperative to opt for a storage management system. Employing a storage management process will not only allow you to better manage your storage, but also efficiently make plans to accommodate future requirements.
OpManager Plus: Unified IT infrastructure observability solution
OpManager Plus unites all the individual silos of infrastructure management and offers truly unified IT infrastructure management.
There are many advantages of employing OpManager Plus for your unified IT observability needs:
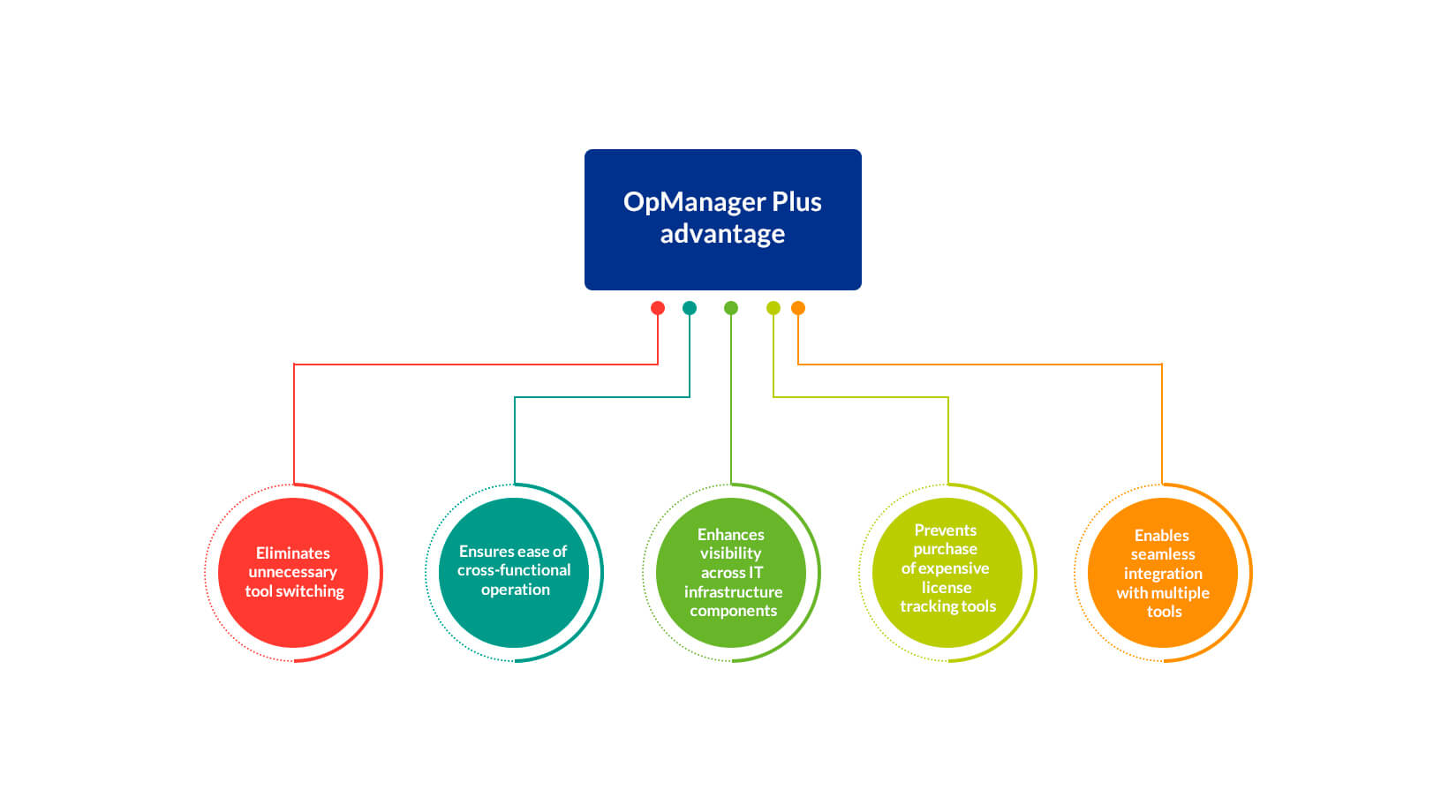
- Eliminates tool switching
- The most common thorn in any IT admin's side is the constant need to switch between various tools that monitor different aspects of the infrastructure. The unified observability solution, OpManager Plus eliminates this by providing a single unified monitoring system for all your IT infrastructure monitoring needs.
- Enables cross-functional IT infrastructure observability through a unified console
- Normally, cross-functional operations such as pushing safe configurations to restore device availability in case of device failure or identifying and restricting devices that consume excess bandwidth require multiple tools working in tandem. However, with OpManager Plus, a unified ITOM tool, this can be easily performed since the entire network's IT operations management is performed by a single UIM monitoring tool, drastically reducing the mean time to repair (MTTR).
- Normally, cross-functional operations such as pushing safe configurations to restore device availability in case of device failure or identifying and restricting devices that consume excess bandwidth require multiple tools working in tandem. However, with OpManager Plus, a unified ITOM tool, this can be easily performed since the entire network's IT operations management is performed by a single UIM monitoring tool, drastically reducing the mean time to repair (MTTR).
- Enhances visibility across all your infrastructure components
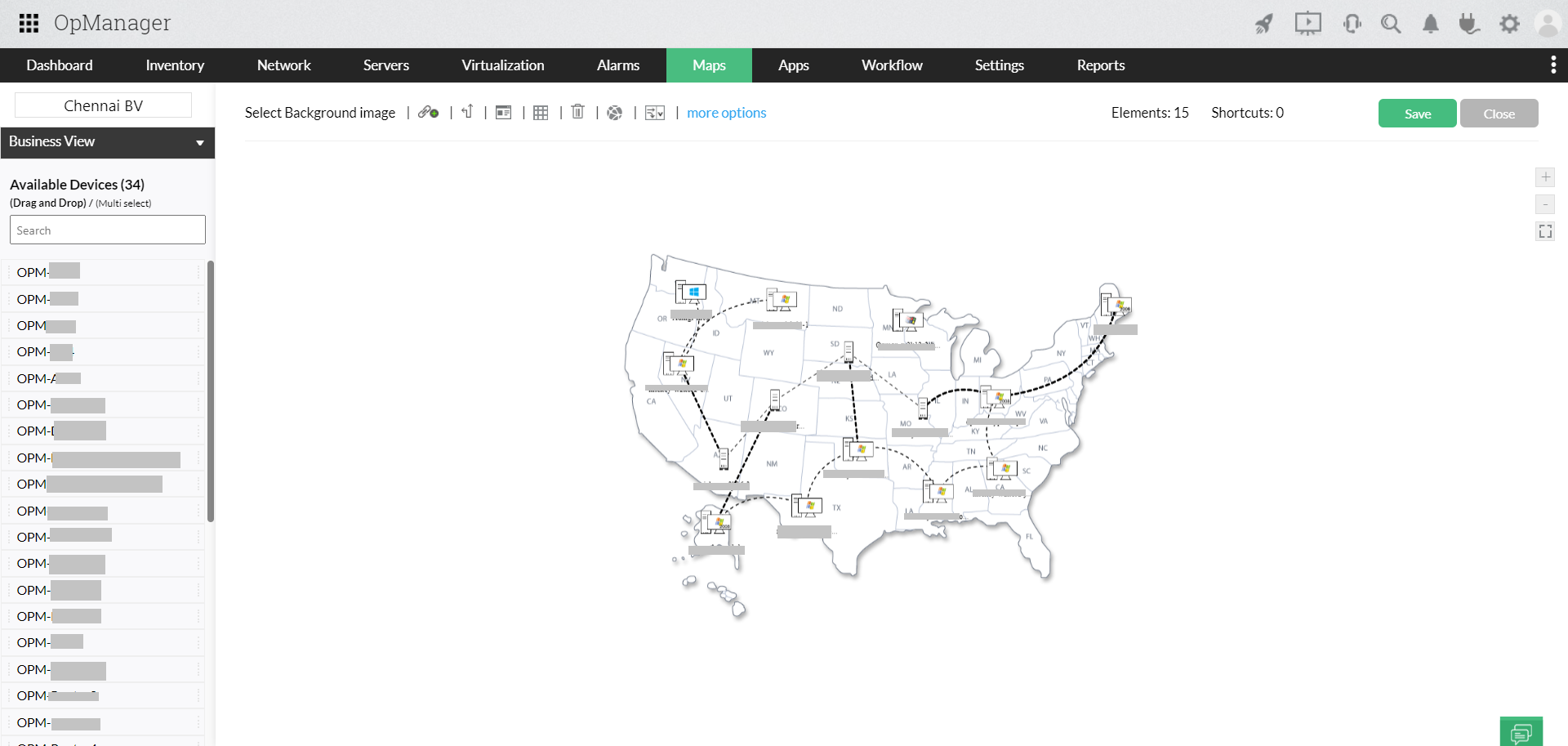
- OpManager Plus offers unified IT monitoring and data center infrastructure management (DCIM) by supervising all your IT infrastructure components and provides in-depth, real-time visibility across all aspects of your network infrastructure. OpManager Plus' UIM monitor can also be employed to present a detailed visual representation of your data center (including 3D rack and floor views), network topology maps, and business views.
- Prevents purchase of expensive tools to track tool licensing
- When a large number of tools are employed to manage the operation of an organization, an individual resource/tool that is capable of monitoring the licensing of all the infrastructure monitoring tools is required, which only adds to the overhead expenses. OpManager Plus' dynamic functions offers unified infrastructure monitoring thus eliminating the need to purchase multiple tools, sparing you from the capital expenses and the need to monitor licenses.
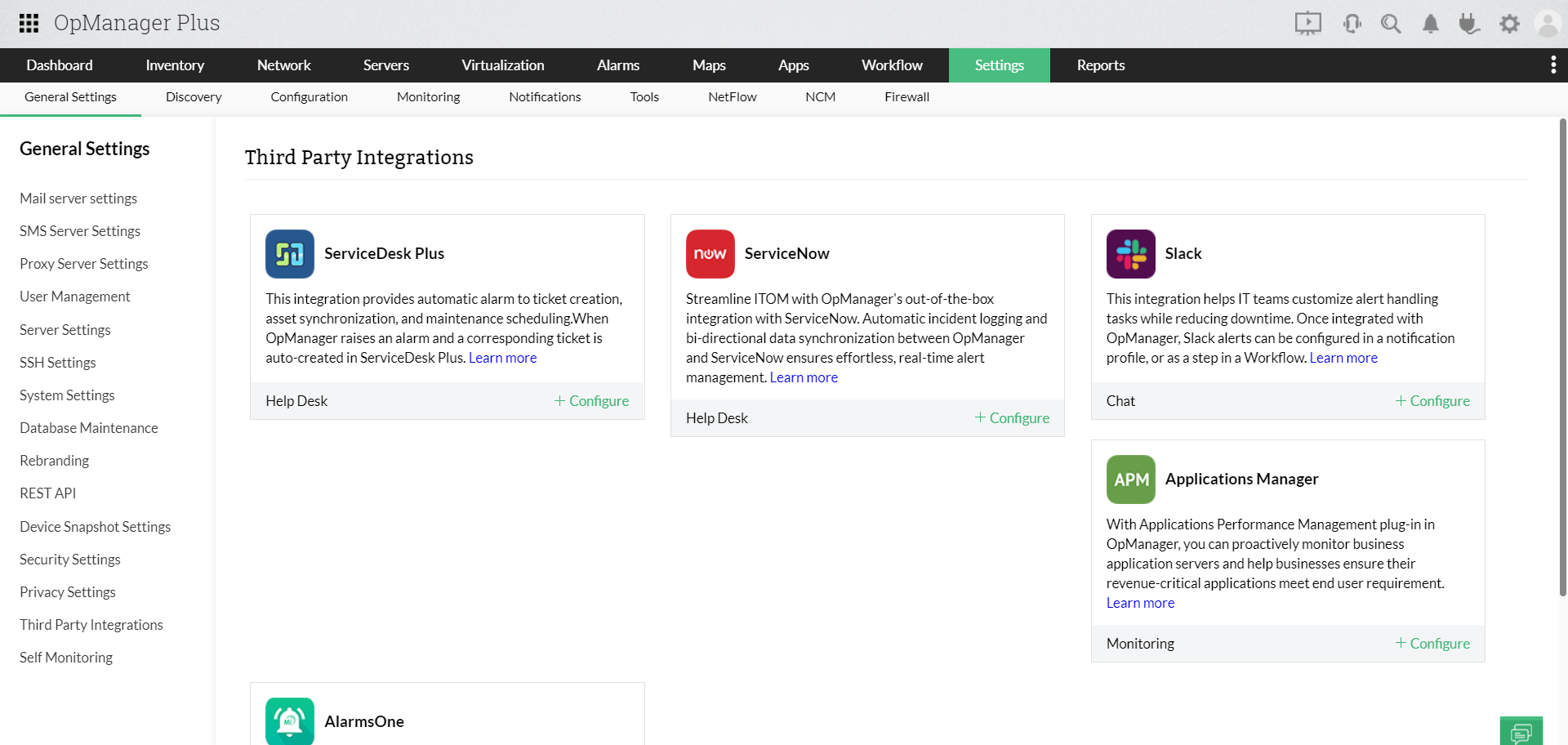
- Enables seamless integration with multiple tools
- Besides seamlessly managing the multiple infrastructure silos in your organization, OpManager Plus, a unified infrastructure management tool, allows you to increase your scope of infrastructure observability by integrating with other third-party tools.
Try our 30 day free trial and learn how implementing an ITOM and unified IT operations management solution like OpManager Plus will increase your network monitoring efficiency.