What is data mirroring?
Data mirroring is the process of replicating the contents of files that have been transferred into or modified within USB devices. Once mirror copies are made, they can be maintained in a password-protected network share. This share folder is best kept in a remote location to save space on local machines. This way, it can be securely accessed and analyzed by only the administrator or trusted users.
Data mirroring software is a tool that you can use to configure policies to ensure that data mirroring happens whenever any file action is carried out on a USB, or just when specific file actions are performed. Details regarding the file operation such as file name, users, devices, endpoints involved as well as the time of action can also be recorded.
Although data mirroring requires considerable bandwidth and disk space, when configured carefully, it is an effective way of safeguarding corporate data that has been transferred out of the network using removable devices.
Data mirroring vs backup
The following are the ways in which data mirroring differs from backup:
- Data mirroring software differs from backup such that it involves creating copies of files in real time rather than periodically scanning and updating changes to data at rest to a different location.
- Data mirroring is also an efficient way to track and maintain recent changes whereas backup is mainly used for preserving an already consolidated set of data for long term.
- Data mirroring software is also highly beneficial to recover data when there are minor hardware failures however backup is useful when there are major hardware malfunctions that render the data completely inaccessible from the original location.
Data mirroring vs replication
Data mirroring is often confused with data replication- a process intrinsic to database management systems. While there can be multiple uses for data replication in an enterprise, such as making data fluid and readily accessible in larger networks, the term database mirroring is specially attributed towards disaster recovery and prevention against hard-deletion of files.
What are the benefits of implementing data mirroring?
Identify compromised data in order to enact remediation protocols.
If and when circumstances do arise where information is lost due to data theft or some other human or hardware-related error after being transferred, the data mirroring software ensures that the share folder can still be utilized. It can be cross-referenced to identify the exact contents of the files that have been compromised. If the information includes crucial details such as passwords, financial records, or even protected personal information (PPI), remediation efforts can be carried out immediately.
Restore critical information and minimize downtime.
It is crucial that data required for critical tasks or data accessed by many employees remains in tact. It is equally important to have the information always available to authorized employees so that they can access it whenever necessary.
However, if data loss occurs due to neglect or theft during file actions involving USB devices, having a data mirroring software in place provides the organization with a cost-effective way to recover. After extracting information from a system, whatever files become corrupted or go missing while being transported in the USB device can be swiftly retrieved from the network share and restored to a location where relevant employees can regain access to them.
Frequently accessed files in highly classified vaults can be directly obtained from share
If a specific file is frequently needed but happens to be indexed in a top security repository containing numerous other classified information, the administrator would have to grant users high-level access each time they would need that particular file. Not only does it mandate tremendous effort on behalf of the administrator to assign permissions and revoke them accordingly once the file has been accessed, it also poses a risk for the organization as it renders the vault and its other files momentarily vulnerable. A simple resolution for this obstacle is to assign the users who require the file on a consistent basis, access to the network file archive remote share instead.
How to implement data mirroring with Device Control Plus
- Select the device or device type on which to perform data mirroring. Next, you can start configuring the options under File Shadow Settings.
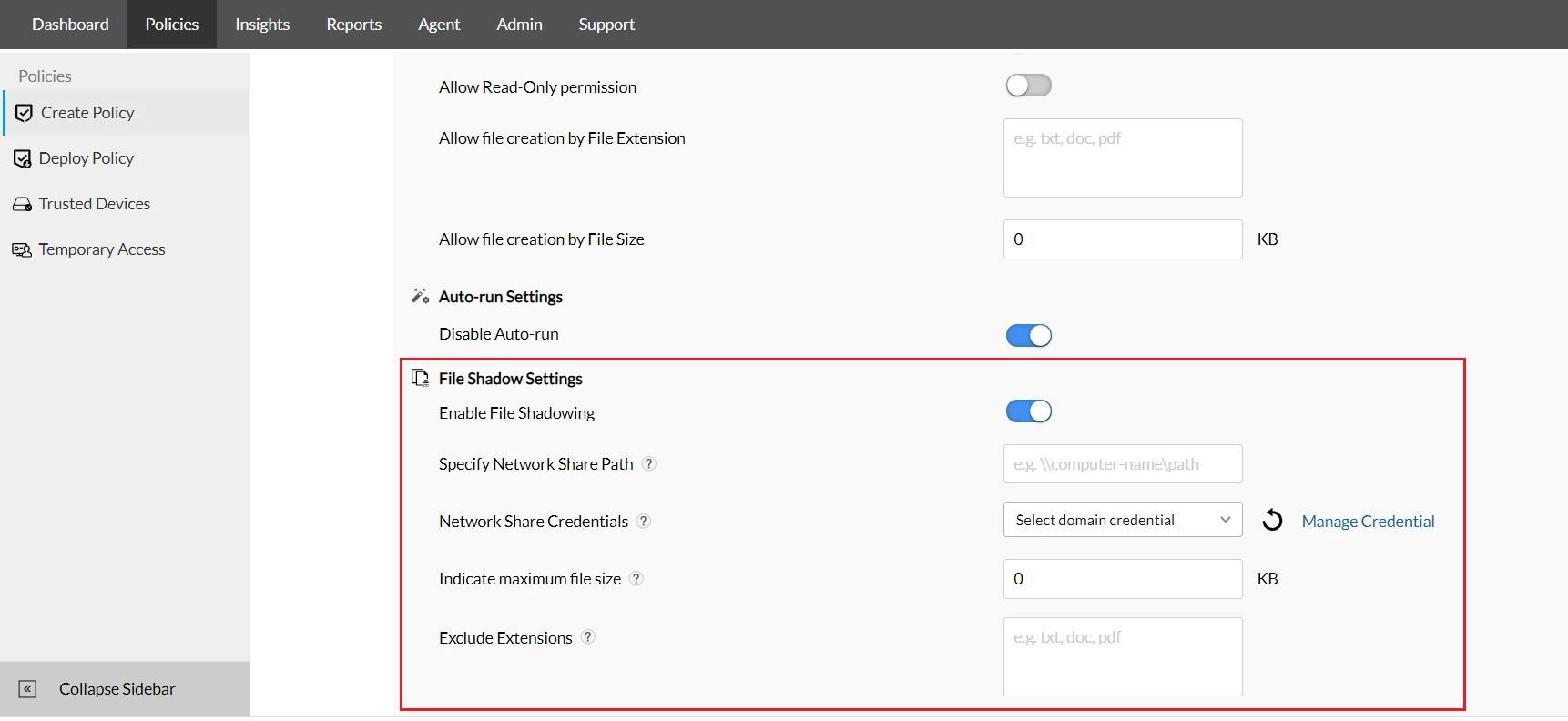
- Since data mirroring requires a considerable amount of storage space and time, to narrow down the information that is to be mirrored, you can also select the file types as well as configure a file size limit.
- You can also specify a folder, so that all the mirrored data can be easily accessed by authorized personnel.
- Once the data mirroring configurations are included in the overall device control policy, you can then associate it with the target group of computers. What will happen is that whenever data is elicited from one of these computers by any of the devices mentioned in the policy, that data (so long as it matches the file extension type and is under the file size limit) will be mirrored. The copies will be then stored in the share folder.
- For later analysis, a summary of all the files that were mirrored will be provided in the data mirroring reports.
To prevent file based attacks due to excessive access privileges, download a 30 day, free trial of Device Control Plus to get acclimated with this data mirroring software