Ensure optimal endpoint security with steadfast USB and port control
Ports enhance productivity as they provide easy connection between computers and many peripheral devices. However, they are also easily accessible and expand an organization's attack surface, leading to data theft and leakage. Device Control Plus is a port security solution that enables you to create a list of trusted devices for each of the port types mentioned below and permit only those devices to connect to your organization's computers. Moreover, if an unauthorized device attempts to connect, it will be blocked, and you will immediately receive an alert about the incident.
What types of ports can be secured with Device Control Plus?
Since their invention, the types of ports on computers has changed drastically. The typical ports found on legacy machines versus the ones found on modern computers require specific attention when enforcing security measures.
The types of computer ports include:
USB port security
USB ports are the most prevalent port type found on modern computers. Certain types of input/output devices are used throughout most businesses, such as storage media, imaging devices, CD-ROM, and modems. Although typical USB security software can aid in the granular management of these standard peripheral gadgets, there are still numerous other less common input devices, such as light pens, joysticks, trackballs, and output devices, such as GPS trackers, projectors, and plotters, utilized across various niche industries that may not be detected.
To prevent lesser-known peripheral devices from bypassing your security, it is best practice to protect the device connection interface instead, which is the USB port. While standard devices are individually monitored, Device Control Plus enhances USB security by keeping a close watch on USB ports that serve as entry points to niche peripheral devices.
You need the device IDs of the trusted peripheral devices to add to the allowlist, and only those devices will be permitted to access the computer. With a well-rounded USB port protection in place, unauthorized device access is controlled, keeping your critical enterprise data secure.
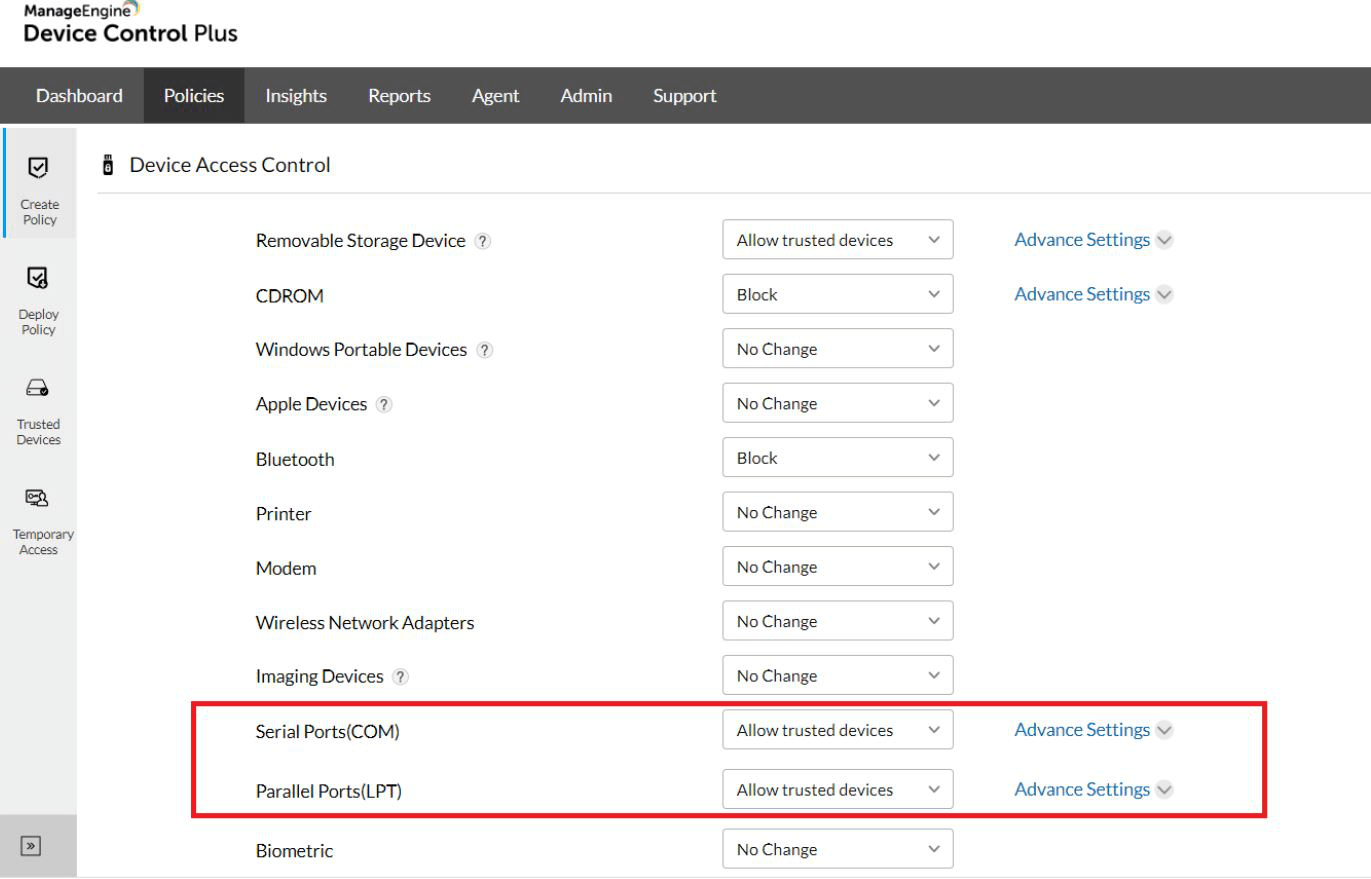
Parallel port security
A common type of parallel port that is found in later versions of PCs is a line printer terminal or LPT for short. These ports serve as an interface between computers and many devices—most notably printers, which are often a silent vector for attacker intrusion. Even printers built by popular manufacturers have a myriad of vulnerabilities, and since parallel ports support older printer models, organizations are likely to run into even more vulnerabilities.
The outcomes of attacks that occur via printers can include:
- Emailing confidential data to external sources.
- Registering the printer as a bot that inundates websites with fraudulent data to redirect internet traffic or deceptively gain clicks.
- Gaining unauthorized network access to perform illicit activities, as many printers are shared by computers in a local office.
- Rendering the printer dysfunctional, resulting in productivity loss.
To prevent attackers from exploiting vulnerable printers and utilizing them for harmful purposes, you should leverage a solution to exercise parallel port control. Device Control Plus, a USB protection solution, stays ahead of traditional port security software by helping you block all unsecured devices and only authorize the devices that you trust. Devices that are appropriately patched with all security updates and do not have any vulnerabilities can be considered trusted devices.
Serial port security
Serial ports, also referred to as COM ports, are legacy interfaces for peripherals such as mice and modems that are found on IBM-compatible computers. In a serial port connection, data is transferred in a bit-by-bit sequence. This makes for a cost-effective interface for scientific instruments such as oscilloscopes and function generators, which only require low-speed, short-range connections to carry out their purposes. For these reasons, serial ports are still used today in industries that specialize in automation, diagnostics, embedded systems, point-of-sale systems, etc.
Why do organizations require USB port security specifically?
Organizations can have sensitive data stored within their endpoints and share folders across their networks. With Device Control Plus, you can effectively manage USB port security on a large scale by enforcing policies that can automatically filter device connections for all managed computers within your enterprise, which ensures that only the devices that are verified as belonging to trusted users are allowed access.
Moreover, if a company has a Bring Your Own Device (BYOD) policy or lets its employees bring their computers to unsupervised environments like their homes or public spaces, their devices’ serial ports will be susceptible to physical exploitation. In these situations, a nearby intruder can plug in a device, infiltrate the computer, and extract sensitive content. Because these ports are only used on occasion, detecting the intrusion may also be delayed. By the time the threat is detected, the organization’s security may already be comprised. For this reason, a robust serial port control solution is necessary to regulate the device connections made on legacy serial ports and immediately detect any potential threats.
How to protect USB ports?
Physical security of computer ports offers to protect USB ports from USB flash drives with a password protection strategy that lets the device be accessible only to the corresponding endpoint user. But in an organization where employees work round the clock and with several shifts, it is difficult to rely on a USB port security software that is incapable of regulating USB device access by differentiating the user roles.
With Device Control Plus, you can configure the USB devices for user groups, and based on the user roles you add devices to the trusted list, granting them complete access while restricting USB port access for normal users. This proactive approach assures your endpoint is protected from malicious intent or data theft and leakage, making Device Control Plus an effective USB port security solution.
How your organization can benefit from Device Control Plus' USB port protection capabilities?
USB ports, if left unprotected, are easy avenues for malware attacks or data theft. It is one of the simplest ports to exploit, since it is compatible with many modern peripheral devices. USB security comprises a set of measures for monitoring USB devices and ports, preventing unauthorized intrusions from various peripheral devices, controlling the actions of all USB devices active within the network, and ensuring that USB devices carrying data are encrypted.
Advantages of implementing USB port security using Device Control Plus
Prevent hardware based attacks
USB ports are often the targets for physical attacks due to their high accessibility. They are a direct avenue to a computer’s internal circuitry. If exploited by malicious users or inadvertently mishandled by negligent ones, USB ports can pave the way for hardware-level attacks like BadUSB attacks. Secure USB ports, being the frontline defense to unprecedented attacks, alleviates insider threats and attacks.
Prohibit unauthorized entry into the network
Another risk with unsecured ports is that they facilitate connections between the computer and external hardware assets. Sometimes these external devices are shared amongst other computers in the immediate vicinity such as a designated printer or scanner. Thus, to some degree, inter-connectivity between different computers in the network can be established through ports. Attackers can leverage this loophole by exploiting an entry point in one computer and gradually infiltrating other endpoints.
Because ports remain physically unguarded, it is vital to have software barricades, such as an effective USB port security solution like Device Control Plus to avert these hazardous intrusions.
Download a 30-day free trial of Device Control Plus to implement high-level port security instantly.