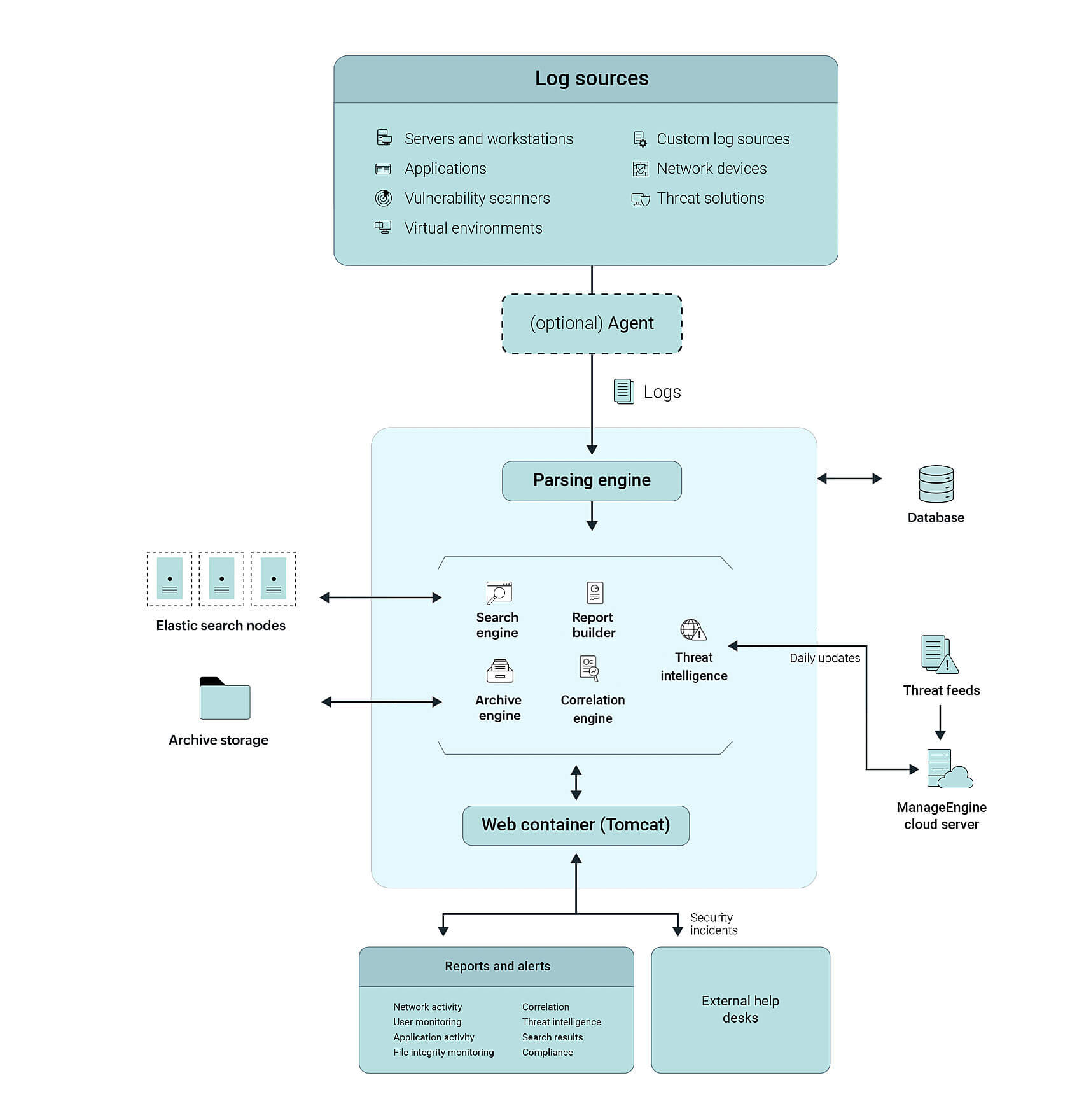
Standalone edition
EventLog Analyzer is a log management and IT compliance solution for your enterprise. It's web-based, and it employs both agentless and agent-based mechanisms to collect logs from log sources across your network while also providing you with in-depth reports, alerts, and security analyses.
The main modules EventLog Analyzer has to offer:
- Log collector: Collects and centralizes log data from various sources in the network via agentless and agent-based mechanisms. It can collect logs from various sources including operating systems, databases, network devices, security devices, applications, and more.
- Parsing engine: Filters logs which aren't needed—as configured by the administrator—and normalizes raw logs into a standard format.
- Central database: Stores user configuration details and log source information. The default database that comes installed with the product is PostgreSQL. Users have the option of migrating to Microsoft SQL Server, based on their organizational requirements and proficiency with the database.
- Report builder: Processes the raw and normalized logs to build over a thousand predefined reports—including compliance reports—and custom reports as well. EventLog Analyzer generates and sends out scheduled reports, and it exports reports when needed.
- Alerts and incident management: Sends out email and SMS notifications based on configured alert profiles; assigns incidents to designated technicians, and stores the statuses and related information for every incident.
- Automated Workflows: Automates incident response through predefined workflows that set off when alerts are triggered.
- Log search engine: The search engine, powered by Elasticsearch, is employed to store parsed logs from all devices and applications across your network, along with the report and alert data. It swiftly searches through millions of logs in seconds, delivering customer-required reports and information.
- Correlation engine: Correlates logs from heterogeneous sources to identify potential attacks, and generates in-depth aggregated incident reports and security alerts.
- Threat intelligence: Regularly retrieves and stores threat data from popular STIX/TAXII-based threat feeds as well as other open source feeds. The module compares this data with network events and then generates threat alerts when malicious entities are discovered interacting with your network.
- Archive engine: Stores compressed raw or parsed logs (based on configuration) from all devices and applications across your network in a specified location. Users can also configure policies for archival based on their requirements.
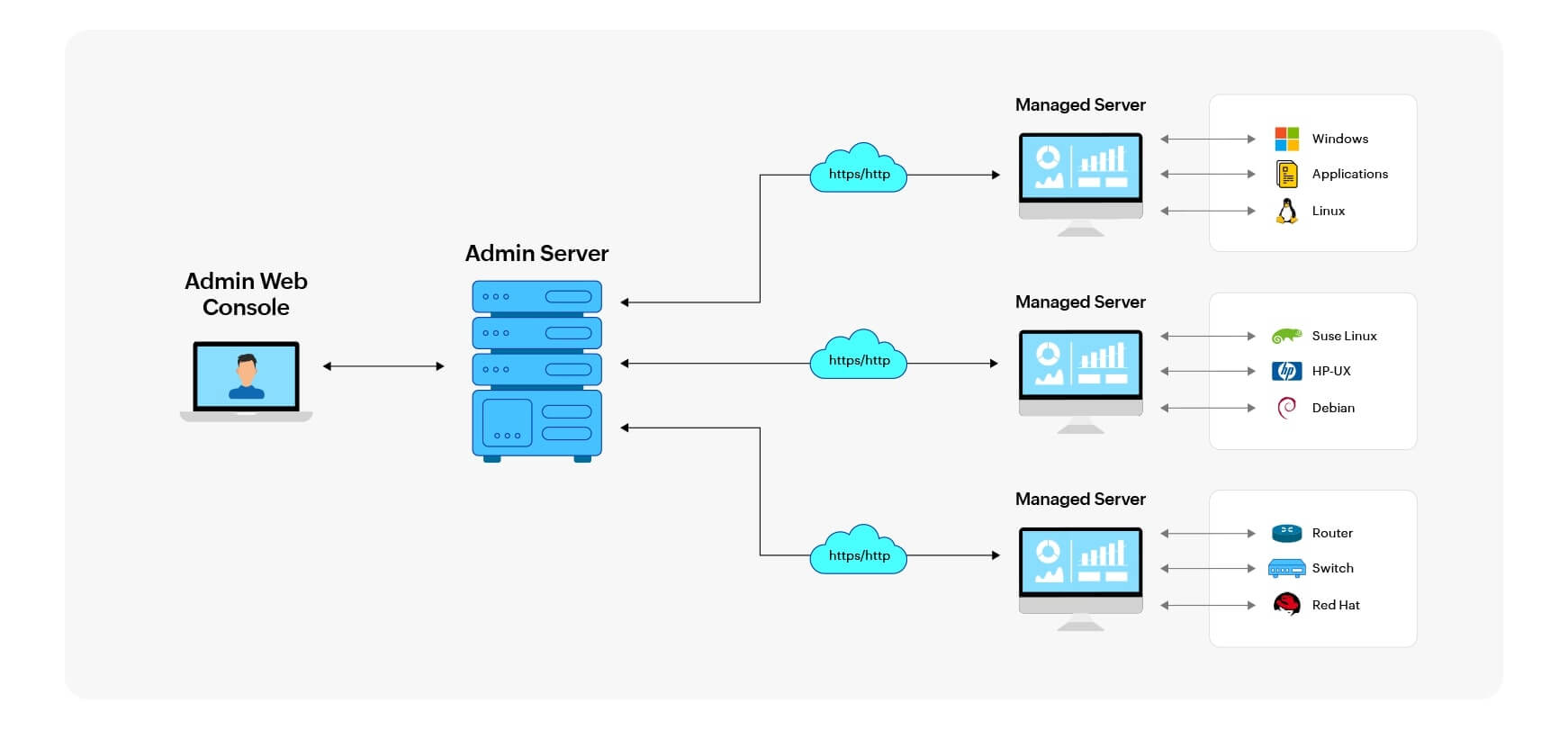
Distributed edition
EventLog Analyzer's distributed edition is useful when your network consists of over a thousand log sources, or if it's spread across multiple geographic regions. It's also the perfect model for managed security service providers (MSSPs) to deploy. It follows a distributed architecture with multiple managed servers being controlled by a single, central admin server.
- Admin server: A central server that provides the administrator with control over the entire network.
- Managed server: Each managed server oversees a smaller portion of the network, and it works exactly like the standalone edition described above.