Integration with AWS-ACM Certificate Manager
Overview
Key Manager Plus (KMP) integrates with AWS Certificate Manager (ACM) — an SSL certificate manager and private certificate authority. This integration enables you to request and obtain certificates from AWS-ACM into Key Manager Plus. In addition, you can deploy certificates from Key Manager Plus to the AWS-ACM repository.
It also allows you to renew certificate requests and automate the end-to-end lifecycle management of SSL/TLS certificates issued and managed by ACM, directly from the Key Manager Plus web interface.
- How does the KMP — AWS-ACM Integration Work?
- AWS-ACM Certificate Discovery
- Deploying Certificates to AWS-ACM
- Requesting Certificates from AWS-ACM
- Domain Validation, Certificate Issue, and Deployment
- Renew, Revoke, Delete and Fetch Private Key of Certificates
1. How does the KMP — AWS-ACM Integration Work?
Through Key Manager Plus's certificate discovery feature, import AWS-ACM certificates into the KMP repository. Once discovery is done, Key Manager Plus displays all the AWS certificates deployed to all regions under the AWS tab. Click here to learn more about the supported regions in AWS.
There are two types of certificates in AWS-ACM: Public and Private Certificates. AWS-ACM allows you to use public certificates provided by ACM or certificates that are imported into ACM. If you use ACM Private CA to create a CA, ACM can issue certificates and automate certificate renewals from that private CA.
Key Manager Plus allows you to create new certificates and manage them in the product. AWS-ACM does not support the creation of new certificates. However, you can create, request, and import certificates from Key Manager Plus into AWS-ACM and manage them from the AWS Management Console. Click here to learn more about importing certificates into AWS-ACM.
- To perform the AWS-ACM integration, administrators require the following user role permissions in AWS-ACM: AWSCertificateManagerFullAccess - This policy provides full access to all ACM actions and resources. Click here to read more about the user role policies in AWS.
- This integration requires API AccessKey and SecretKey. These credentials are also required to perform AWS certificate discovery to import AWS-ACM certificates into Key Manager Plus.
2. AWS-ACM Certificate Discovery
Key Manager Plus enables you to discover, import, and configure expiry notifications for SSL certificates hosted in the following Amazon Web Services: AWS Certificate Manager (ACM) and AWS Identity and Access Management (IAM). Click here for detailed steps on how to discover AWS-ACM certificates.
Note: When you perform any operation on the AWS certificates added before KMP build 6200, Key Manager Plus automatically performs certificate rediscovery and re-populates the data in the table to get the Amazon Resource Name (ARN) ID. Please note that this automatic rediscovery happens only from KMP build 6200 onwards.
In the Integrations >> Others >> AWS tab, Public Certificates requested from Amazon are marked as Amazon Issued, Private Certificates are marked as Private and certificates are that imported from KMP to AWS-ACM are marked as Imported.
3. Deploying Certificates to AWS-ACM
Key Manager Plus's integration with AWS-ACM facilitates you to deploy certificates to the AWS-ACM and manage them from their console.
To deploy certificates to AWS-ACM, follow the below steps:
- Navigate to SSL >> Certificates.
- Select the required AWS certificate and click Deploy >> AWS-ACM from the top menu.
- In the dialog box that appears, choose the following attributes:
- AWS Credential from the drop-down.
- Select one or more Regions using the check-boxes.
Certificates can be deployed to all the supported regions provided the private keys are available.
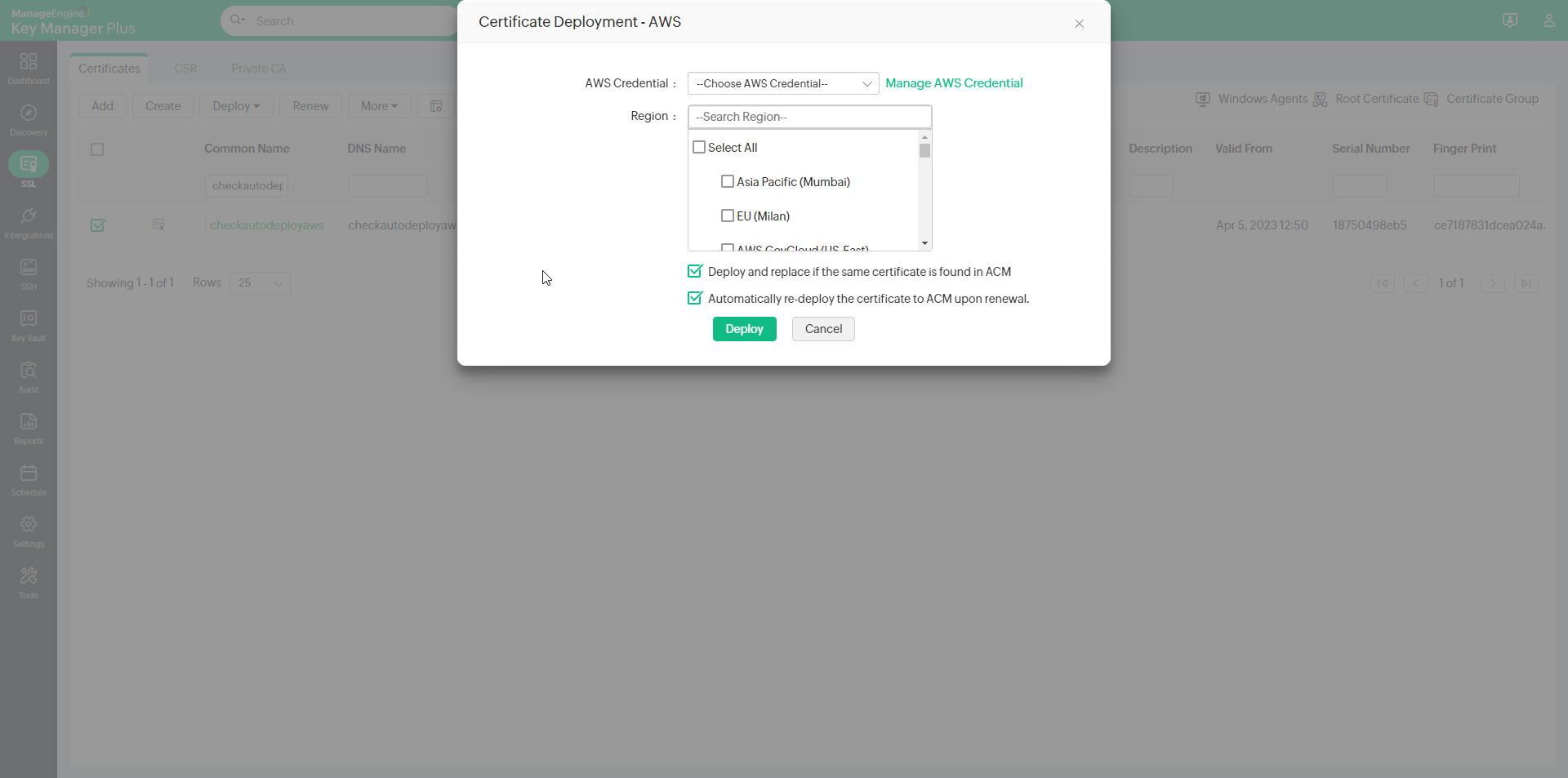
Deploy and replace if the same certificate is found in ACM: If you wish to replace the certificate in ACM after deployment, in case it turns out to be a duplicate, select this option.
Automatically re-deploy the certificate to ACM upon renewal: Select this option to automatically re-deploy the certificate to ACM every time it is renewed so that the certificate in Key Manager Plus and AWS-ACM are always in sync.
If there is a mismatch in the deployed certificates, they will be marked in red in the AWS tab in Key Manager Plus.
4. Requesting Certificates from AWS-ACM
Key Manager Plus allows you to request both Public and Private certificates from AWS-ACM and manage them from the KMP interface.
4.1 Request Public Certificates
- Navigate to Integrations >> Others >> AWS.
- Click the Request Certificate drop-down and click Public Certificate.
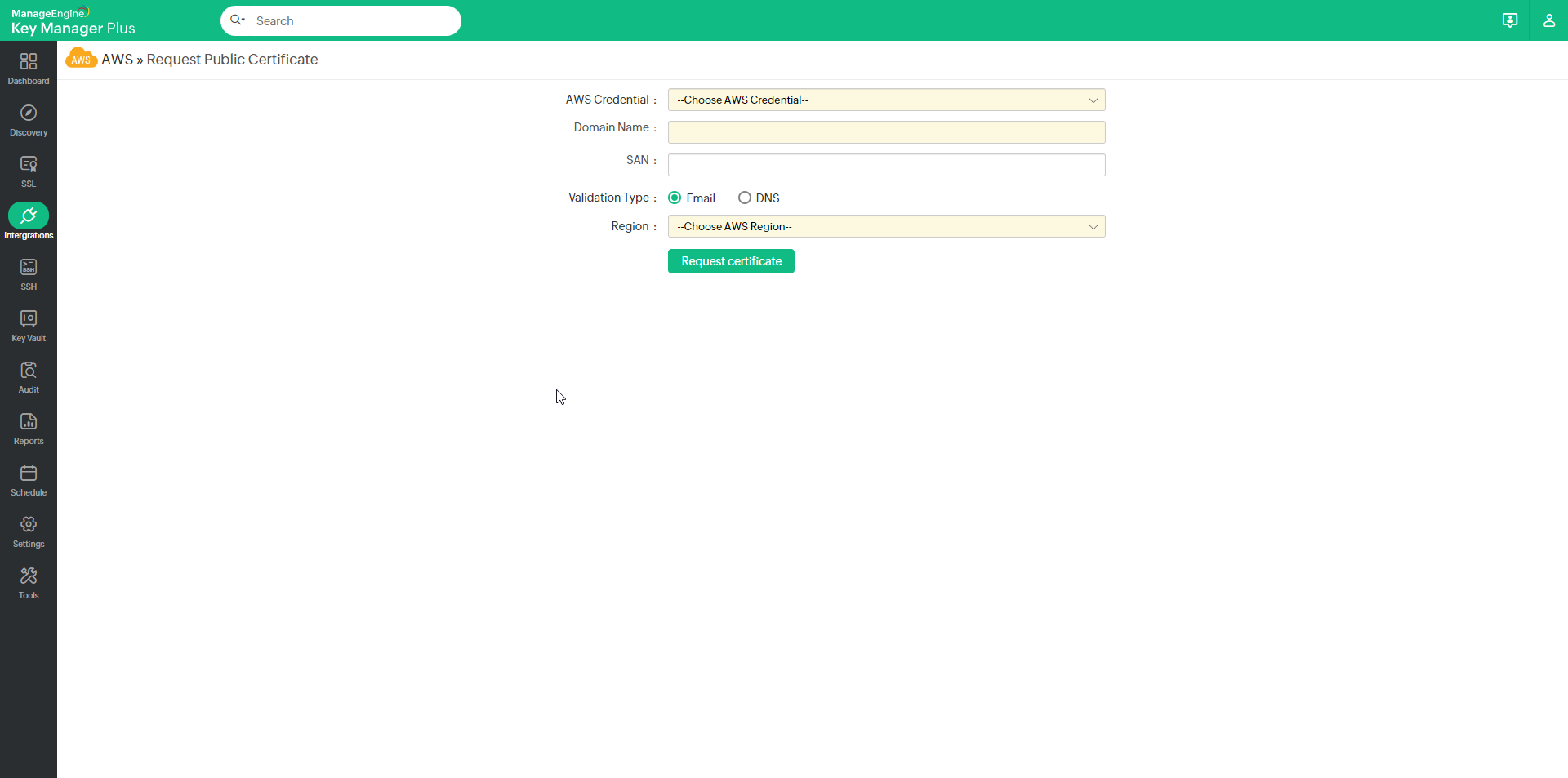
In the page that appears, fill in the following attributes:
- Select your AWS Credential from the drop-down.
- Enter the Domain Name and SAN.
- Choose a Validation Type: Email or DNS.
- Click the Region from the drop-down.
Now, click Request Certificate. The certificate matching the credentials you have provided will be imported into Key Manager Plus. Please note that Public Certificates from AWS-ACM do not have a private key.
4.2 Request Private Certificate
- Navigate to Integrations >> Others >> AWS.
- Click the Request Certificate drop-down and click Private Certificate.
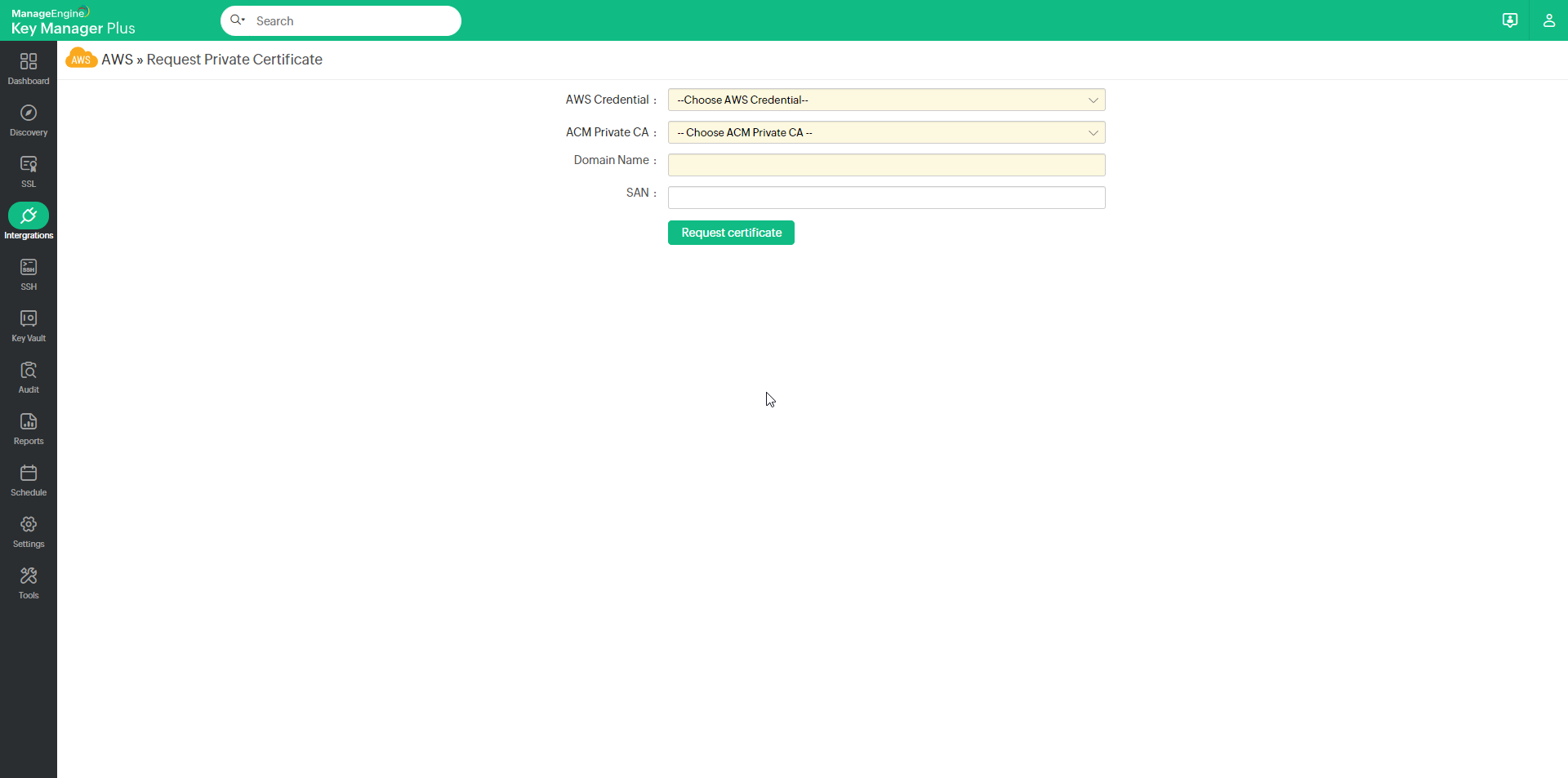
In the page that appears, fill in the following attributes:
- Select your AWS Credential from the drop-down.
- Select an ACM Private CA from the drop-down.
- Enter the Domain Name and SAN.
Now, click Request Certificate. The requested certificates will be issued and added to the repository upon validation.
4.3 Request Status
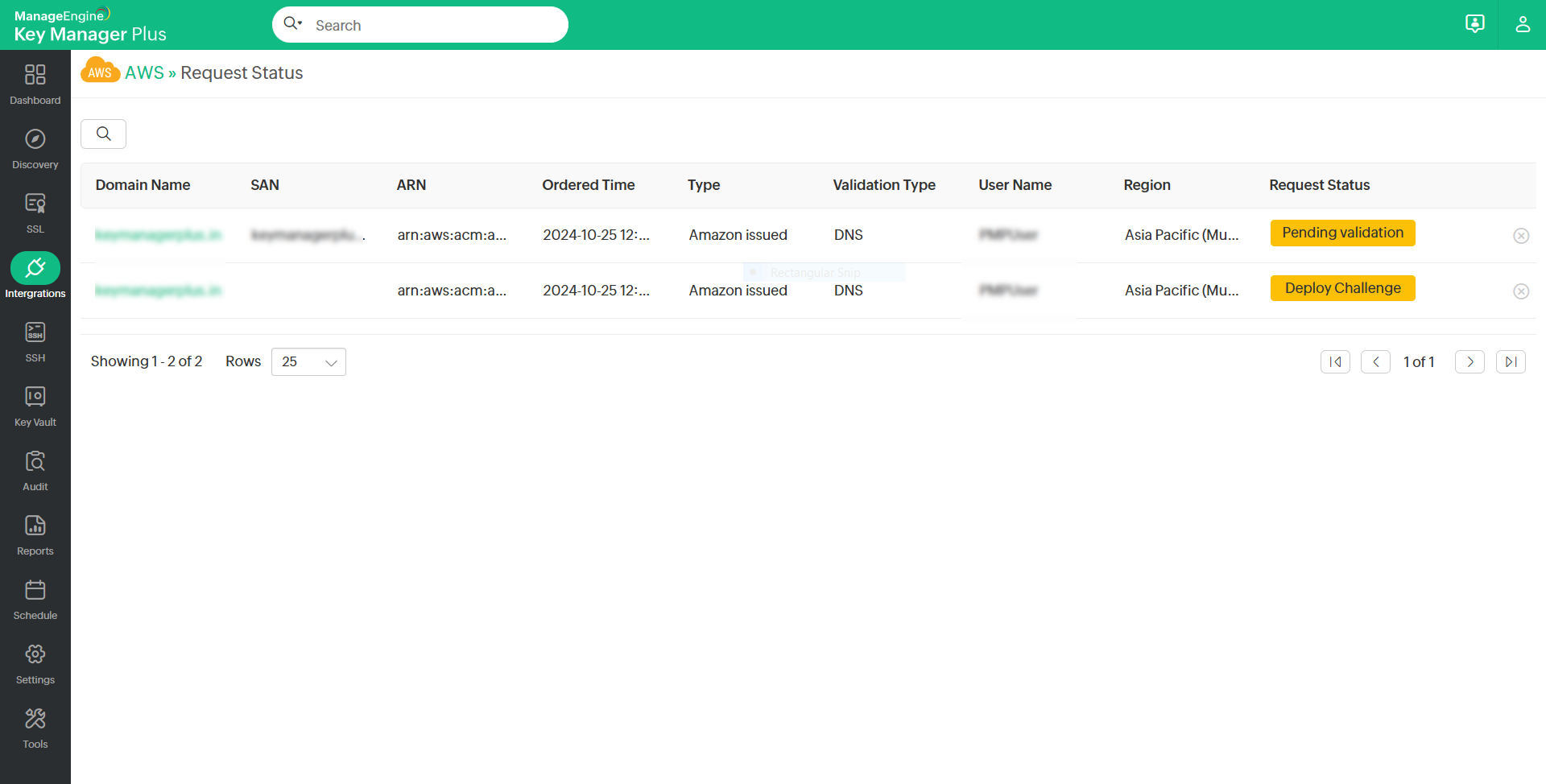
Once you request certificates from AWS-ACM, click the Request Status option from the top menu to view and validate the status of the certificates.
In this page, you can view the request, renewal, and domain validation status of both private and public certificates. Once a certificate request is created, the status of the certificate will appear in this table as Pending Validation.
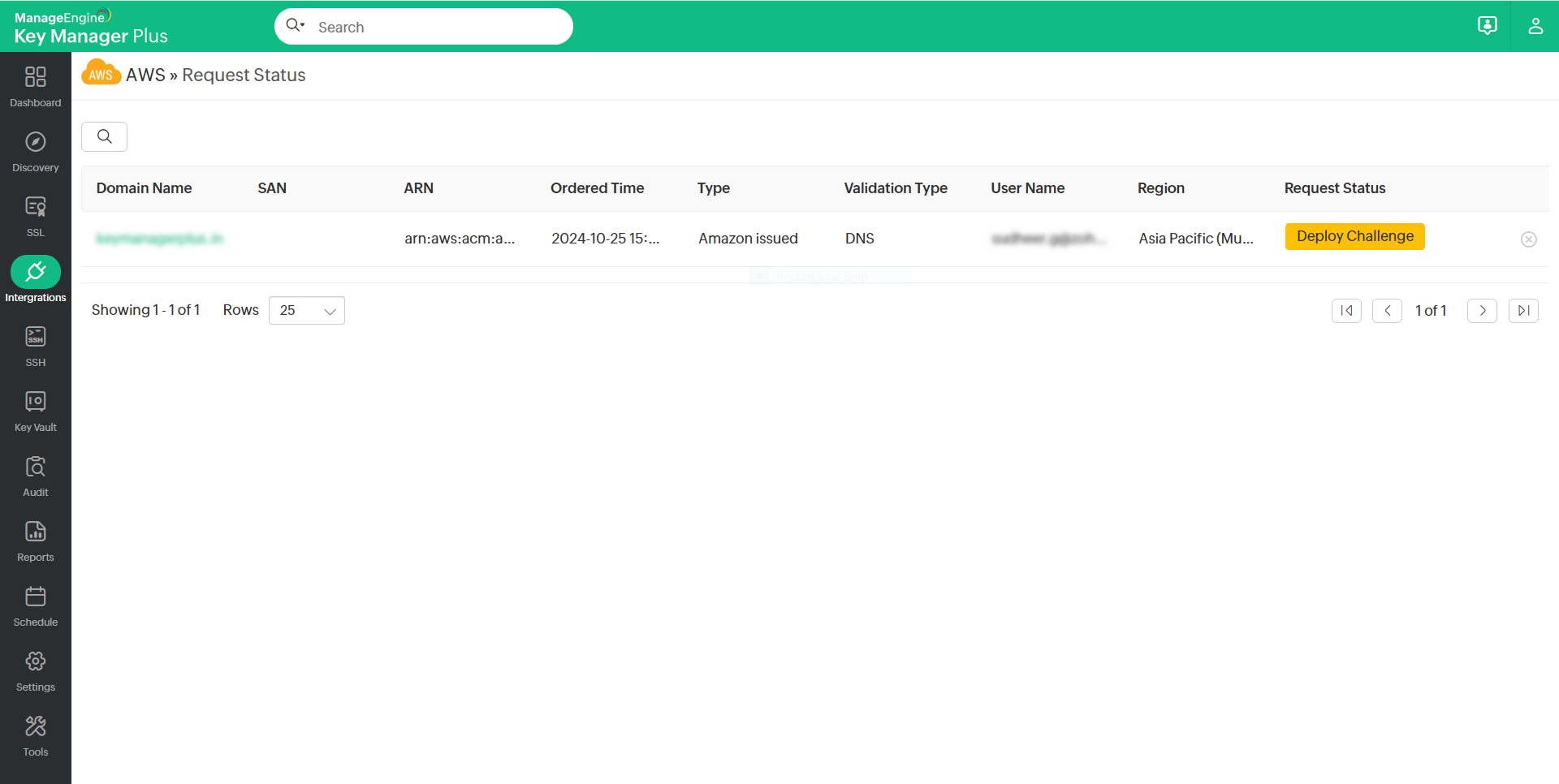
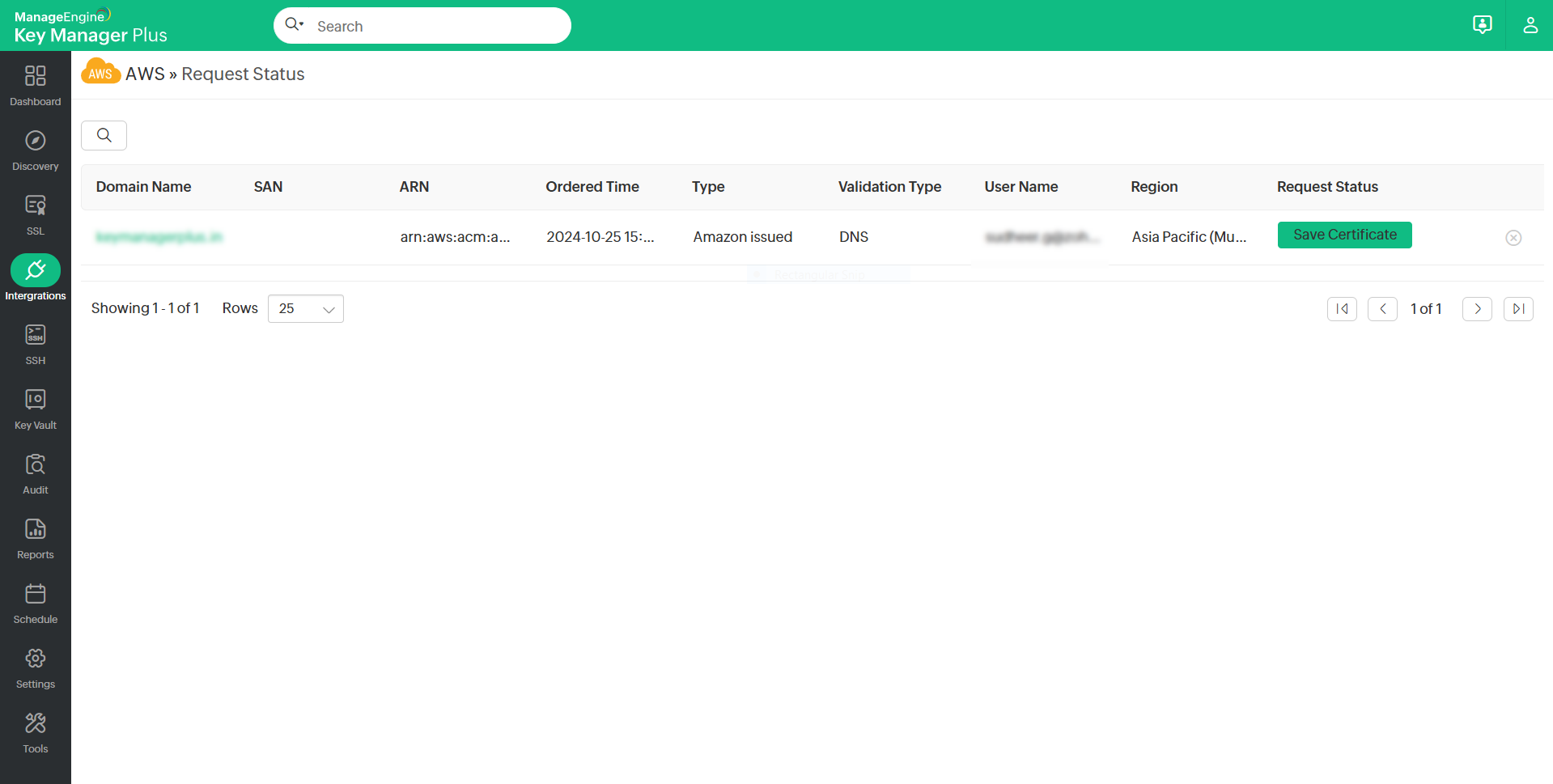
If you have configured DNS-based challenge verification, click the status to deploy the challenge. The status will change to Deploy Challenge and the validation process will begin.
Once it is complete, click Save Certificate to save the certificate to your repository.
5. Domain Validation, Certificate Issue, and Deployment
Once the certificate authority receives your order, you will have to go through a process called domain validation and prove your ownership over the domain upon the completion of which you will receive the certificate. Key Manager Plus supports all the two validation methods:
- Email Validation
- DNS Validation
5.1 Email Validation
- In email validation, the certificate authority sends a verification email to the approver email ID specified when placing the certificate order.
- This email will guide you through the steps that need to be performed to complete the validation procedure. go to verify option and verify via email. go to request status and click pending validation to obtain the cert
- After completing the steps, navigate to the Key Manager Plus server, and switch to the AWS tab.
- Upon successful verification, the certificate authority issues the certificate which is fetched and added to Key Manager Plus' secure repository. You can access the certificate from the SSL >> Certificates tab.
Click here for more details on certificate deployment.
5.2 DNS Validation
- If you have opted for DNS validation, a DNS challenge value and text record are displayed on creating the order.
- Copy and paste the text records manually in the domain server.
The entire challenge verification process can be automated from Key Manager Plus. This can be achieved by configuring the server details under Manage >> Deploy. To automate DNS validation,
- Switch to AWS >> Manage.
- If the end-server is a Windows machine, initially download and install the Key Manager Plus agent for the Windows server from the Windows Agents tab using the steps mentioned in the previous section.
- Switch to the Deploy tab and click Add.
- In the pop-up that opens, choose the challenge type as 'dns-01', specify the domain name, choose the DNS provider (Azure, Cloudflare, Amazon Route 53 DNS, RFC2136 Update, GoDaddy, or ClouDNS) and enter the server details.
- Check the 'Deploy Certificate' option to deploy the certificate to the end-server after procurement. Click Save.
- The DNS challenge values and text records are automatically created in the corresponding DNS servers.
- Once the challenges have been fulfilled, navigate to the Key Manager Plus server, switch to the AWS tab, choose the order and click Check Order Status from the top menu.
- Upon successful DNS validation, the certificate authority issues the certificate which is fetched and automatically added to Key Manager Plus' certificate repository. You can access the certificate from the SSL >> Certificates tab.
- To complete the DNS validation, go to the Request Status page and click Pending Validation to complete the validation process. Please note that DNS validation is done only for Public Certificates.
- If you have already configured the domain and server details under Manage >> Deploy, the challenge verification and the subsequent deployment of certificates is carried out for that specific domain and server alone.
6. Renew, Revoke, Delete and Fetch Private Key of Certificates
Key Manager Plus allows you to renew Private certificates. When a certificate renewal is requested from KMP, the renewed certificate will be retrieved from AWS-ACM. However, if you renew a certificate in AWS-ACM, it is not automatically updated in KMP. To fix the mismatch, rediscover the certificates in Key Manager Plus and re-populate the data.
6.1 Manual Certificate Renewal
To renew the desired certificates manually, perform the steps that follow:
- Navigate to Integrations >> Others >> AWS.
- Select the required order and click Renew Certificate from the top menu.
- Complete the DNS validation procedure if necessary.
- On successful validation, the certificate is issued and the new version is automatically updated in SSL >> AWS tab.
Please note that only the certificates that satisfy all criteria mentioned here will be renewed. Click here to read about AWS's eligibility criteria for certificate renewal.
6.2 Automated Certificate Renewal
To configure the auto-renewal process for the desired certificates, perform the steps that follow:
- Navigate to Integrations >> Others >> AWS and click Manage from the top right pane.
- From the page that appears, navigate to the Auto-Renewal section and enable the auto-renewal process.
- Enter the number of days before expiry in which the auto-renewal process is to be carried out.
- Select the desired certificates that are to be auto-renewed and click Save.
Based on the configured details, the auto-renewal process will be carried out. Click the Auto-Renewal Audit to get insights about the certificates renewed through the auto-renewal process.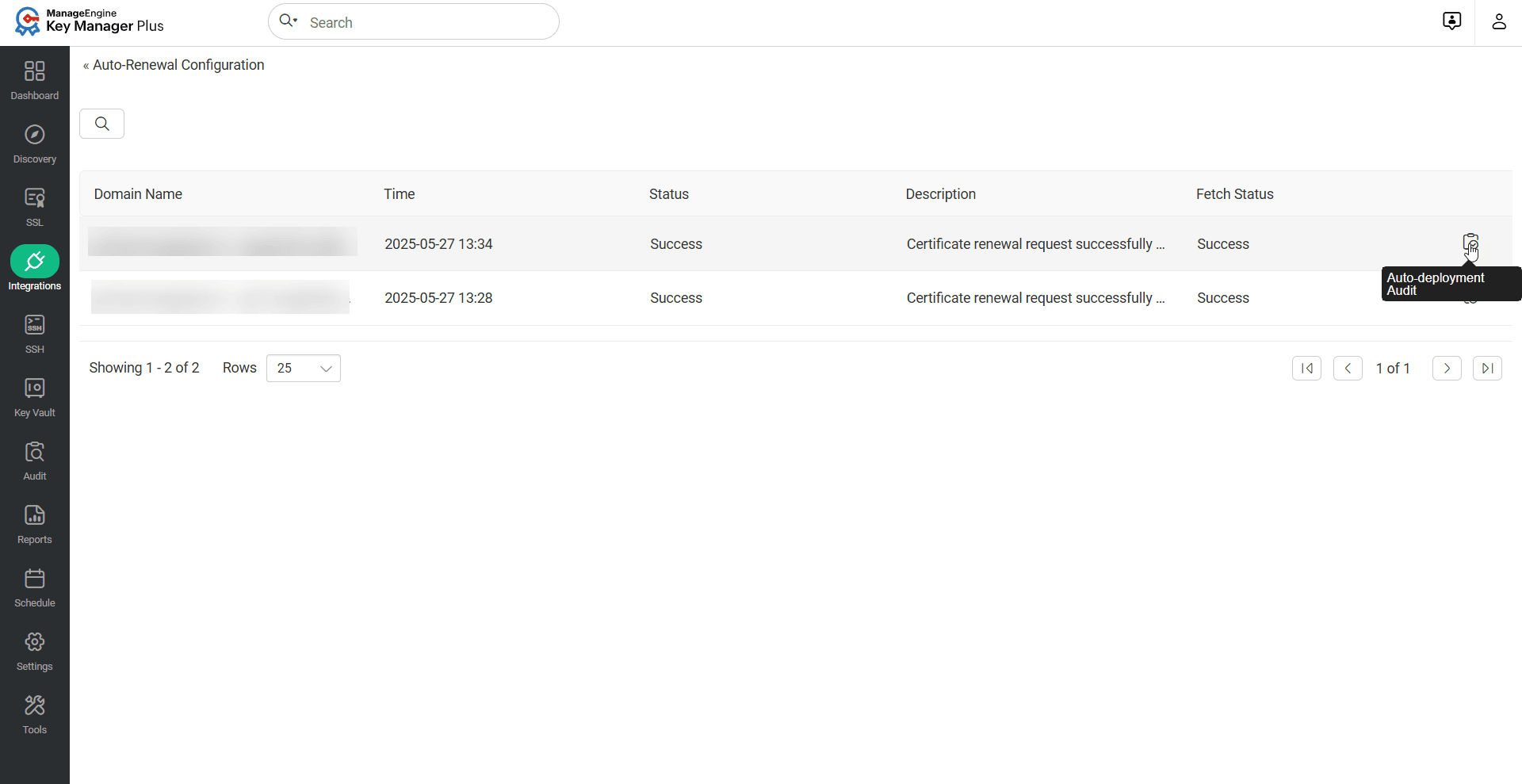
If a certificate has already been deployed to an endpoint or if the deployment has been preconfigured using any of the supported deployment methods, and the Deploy Certificate on Auto-Renewal option is enabled under the Edit Certificate window, Key Manager Plus will automatically deploy the renewed certificate to the respective endpoint upon successful auto-renewal. This auto-deployment follows the system-defined schedule interval, and you can monitor the deployment status for each server in the Auto-Deployment Audit section.
Please note that only the certificates that satisfy all criteria mentioned here will be renewed. Click here to read about AWS's eligibility criteria for certificate renewal.
6.3 Revoke Certificate
To revoke the certificates, do the steps that follow:
- Navigate to Integrations >> Others >> AWS.
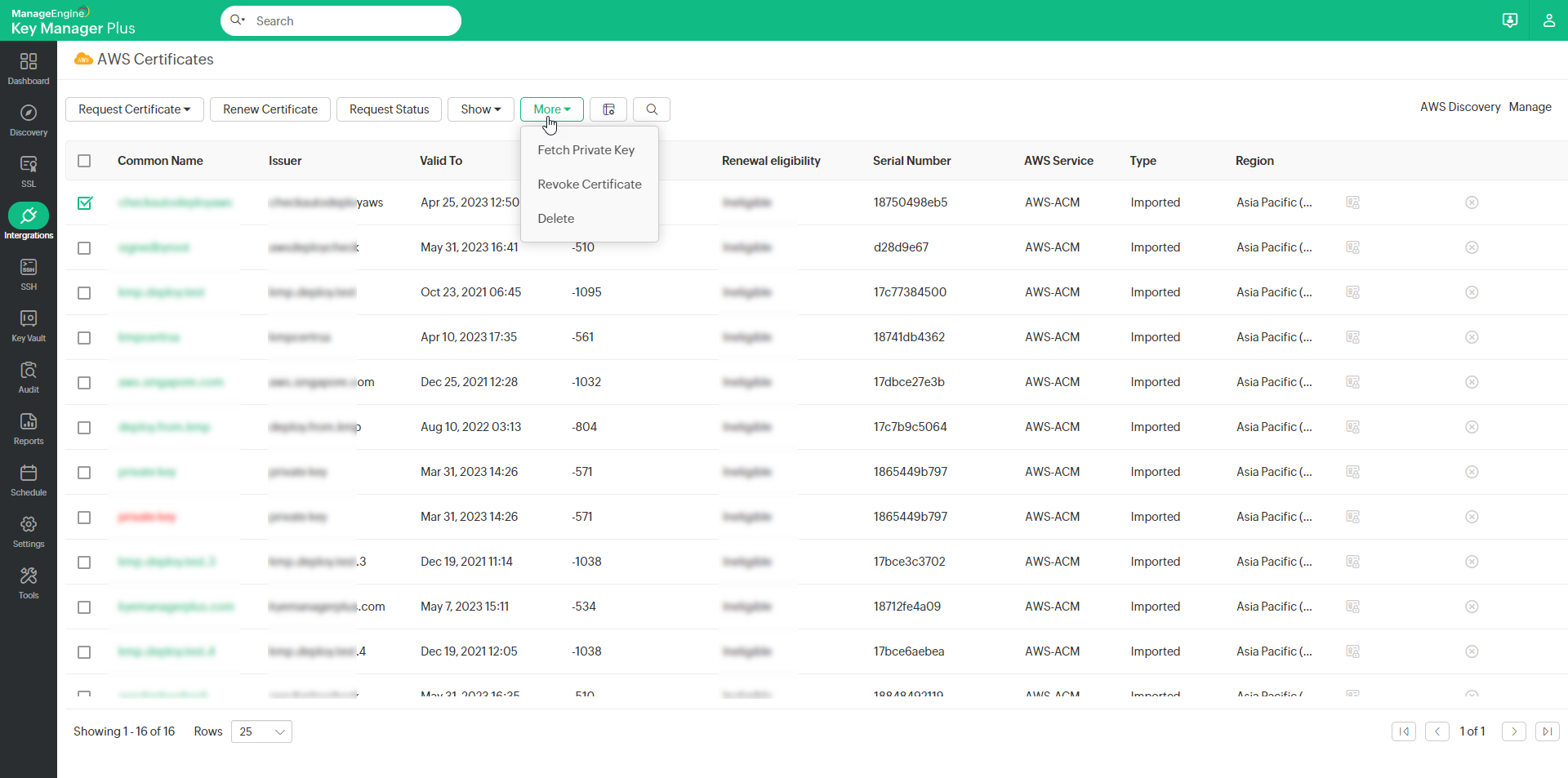
- Select the certificate that needs to be revoked and click More >> Revoke Certificate.
Please note that the revoke option applies only to Private Certificates in AWS-ACM. Revoking a certificate request removes the certificate entry from Key Manager Plus only.
6.4 Fetch Certificate's Private Key
To fetch the private key of a certificate, do the steps that follow:
- Navigate to Integrations >> Others >> AWS.
- Select the required Private Certificate and click More >> Fetch Private Key from the top menu.
This operation fetches the private key of the selected private certificate from AWS-ACM. Please note that is a paid option and might incur costs as per your AWS-ACM license.
6.5 Delete Certificates
To delete the certificates, do the steps that follow:
- Navigate to Integrations >> Others >> AWS.
- Select the required certificate and click More >> Delete from the top menu.
- The certificate request is deleted from the AWS tab.
Please note that using the Delete option simply removes the certificate from the KMP interface, you can no longer manage it from the product. However, it does not delete the certificate from AWS-ACM - the certificate can still be viewed and managed from the AWS console.