Privileged user credentials are a lucrative target for attackers, as they provide elevated access to confidential accounts and information. The last few years have shown that attackers no longer need to hack accounts to breach data; instead, they can take advantage of weak and otherwise compromised credentials to gain access to profitable information. The central goal of a privileged access management solution should encompass auto discovery and vaulting of credentials, which helps password admins secure and provide restricted access to critical accounts, thereby circumventing the vectors of a privileged access attack.
ManageEngine PAM360 offers a centralized enterprise credential vault to consolidate, store, manage, and rotate shared sensitive information, such as passwords, digital certificates, keys, and proprietary documents. PAM360's advanced password grouping options enable you to organize your passwords into comprehensive hierarchical formats, which helps to eliminate password fatigue. Additionally, you can perform bulk operations, such as password reset, change, and sharing for select groups as required.
Security by design
PAM360 ensures the highest level of data protection by incorporating 256-bit Advanced Encryption Standard (AES), which is recognized by the National Institute of Standards and Technology (NIST), and the National Security Agency (NSA). AES incorporates dual encryption, at the application and database levels. The first level of encryption takes place at the application level, where an auto-generated, unique key encrypts the data using the AES-256 standard. The encrypted data is then be pushed to the database for storage, where second-level encryption takes place.
To enable additional authentication levels to your privileged accounts, PAM360 provides exclusive integrations with Active Directory, Security Assertion Markup Language (SAML)-based single sign-on (SSO) solutions, and trusted multi-factor authentication (MFA) tools.
Auto discovery and vaulting of passwords under one roof
PAM360 facilitates automatic scanning and discovery of critical accounts to onboard privileged accounts into a centralized, secure repository for Windows, Solaris, Mac, Linux, Active Directory, VMWare, and a host of network devices and databases. It also includes an option to set time frames and password discovery attempt limits. Upon discovery, PAM360 allows randomization of resource passwords in accordance with preconfigured password policies.
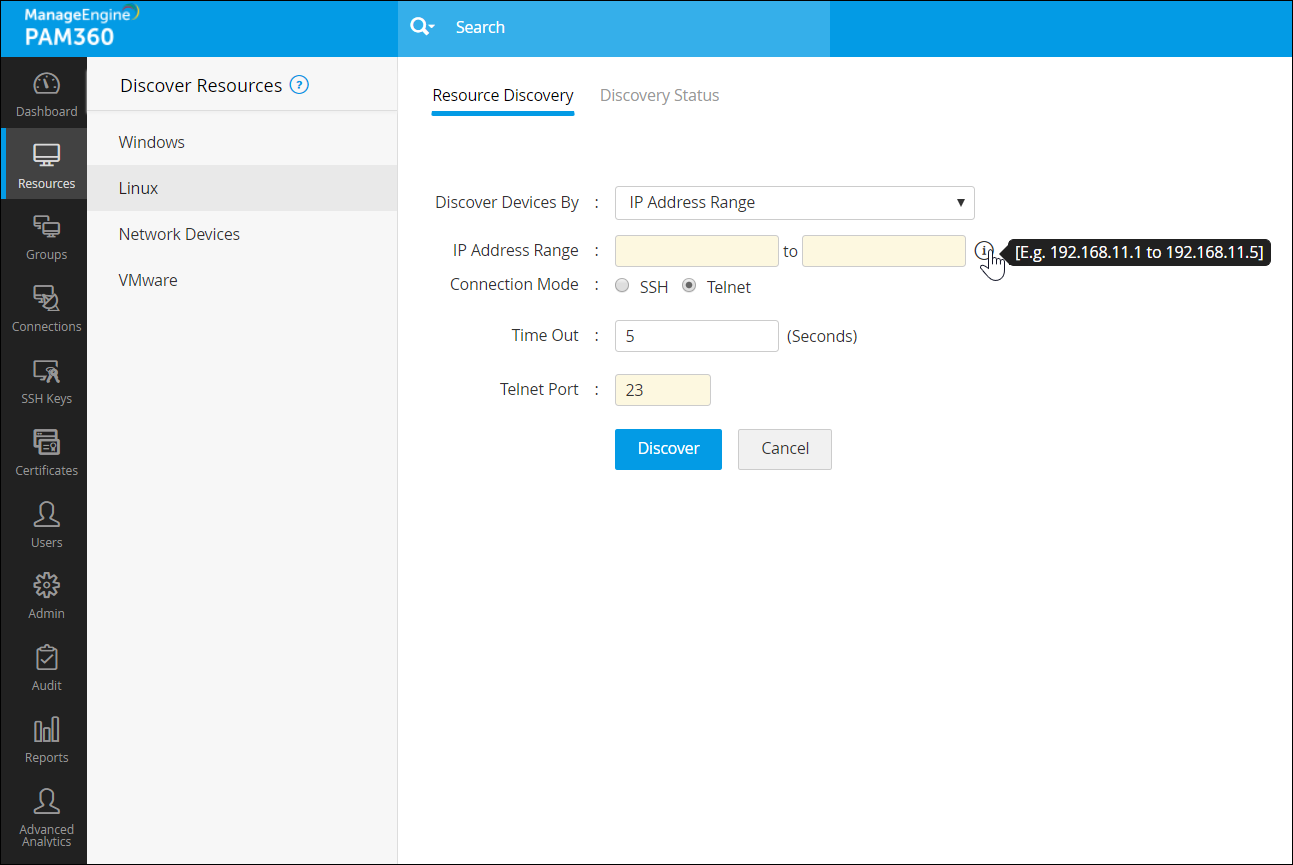
Besides passwords, PAM360 provides a secure storage for digital certificates, images, license keys, and other proprietary documents. In addition, users can import their passwords manually from CSV, TSV, and KeePass files.
Password sharing enabled with layers of security
PAM360 allows sharing of passwords and other sensitive information to select users and groups under varied permission levels, such as View, Modify, and Manage. Admins can also transfer ownership of their passwords to other admins and users at their discretion.
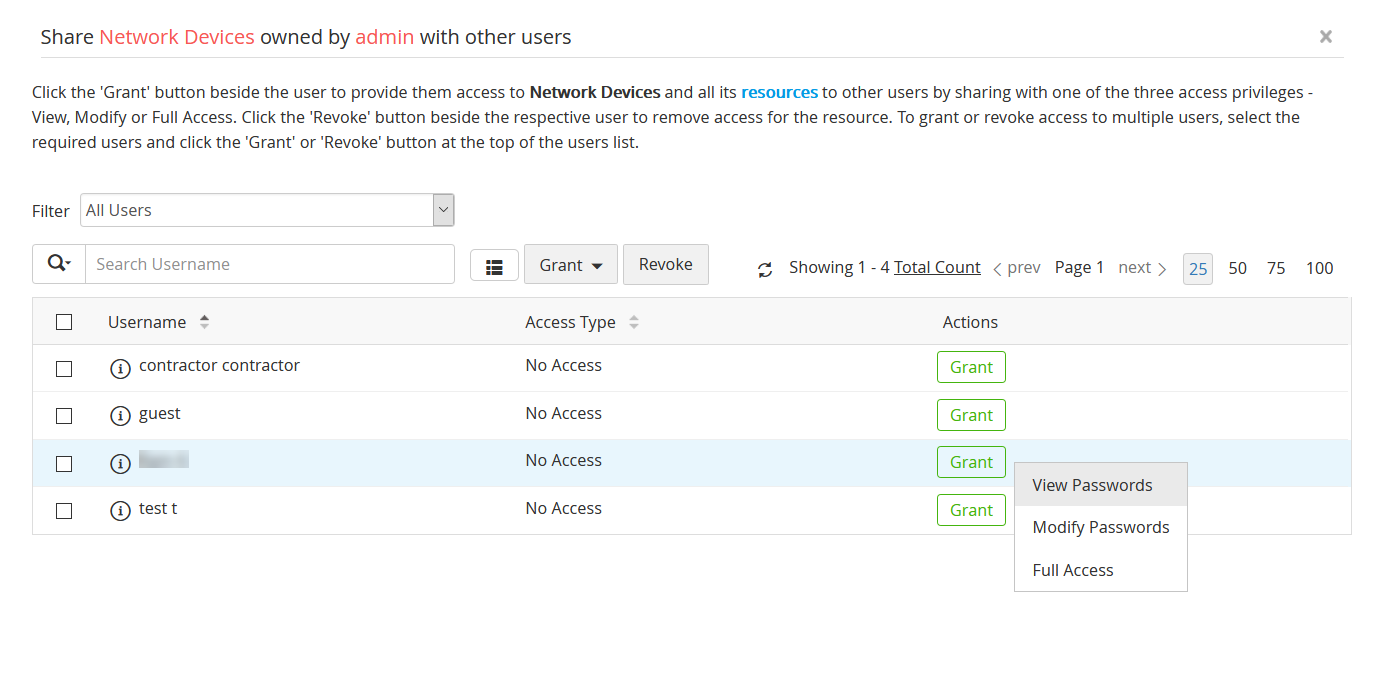
Access to resources can be provisioned without disclosing the passwords in plain-text format. In addition, users can launch one-click connections to shared resources from PAM360's web interface without having to enter the passwords manually.
Implement access restrictions at granular level
PAM360 comes with well-defined access control workflows to enable password sharing with select users based on their roles and responsibilities—for instance, provisioning database credentials only to database admins. PAM360 provides options to delegate access to privileged systems to non-admin users, often based on their requirements and roles. This includes the option to set up a Request-Approve workflow, where end users (read non-admins) can request access to a particular asset/account for a stipulated time frame, and admins can approve/reject requests based on the validity of the request. Once the time frame expires, the passwords to such accounts can be rotated, helping to circumvent the vectors of privilege misuse.
PAM360 provides comprehensive, real-time reports on password access and user activities, which helps admins stay abreast of events pertaining to select passwords and accounts.
When the admin isn't available, PAM360 enables you to schedule automatic approval of access requests for a designated timeframe. You can also provide access as well as revoke access to passwords for a specific period. This ensures passwords will be automatically reset to avoid any unauthorized access attempts to privileged accounts.
Seamless password reset on the go
PAM360 enables you to remotely manage and reset passwords for a host of systems and decides, such as Windows, AIX, UNIX, Linux, Solaris, ESXi, MS SQL Server, Oracle DS Server, HP ProCurve, Cisco devices, Juniper NetScreen, and for cloud-based infrastructure and services such as AWS, Google Apps, Rackspace, and Microsoft Azure.
PAM360 supports 85+ resource types, and for resources and devices that do not belong to the list above, PAM360 offers remote password resets via custom plug-ins, which can be developed using Java, C, PowerShell, Bash, Rust, and others. Alternatively, admins can also run Secure Shell (SSH) batch commands to reset the passwords of SSH-based resources via PAM360's web interface.
One of PAM360's niche capabilities is the option to rotate passwords of privileged accounts discovered on a periodic basis to comply with regulatory standards such as the Payment Card Industry Data Security Standards (PCI-DSS), the International Organization for Standardization (ISO), and North American Electric Reliability Corporation (NERC). PAM360 lets you randomize remote credentials, and assign stronger passwords during automated resets by configuring custom password policies as required. Additionally, PAM360 helps you eliminate hard-coding and manual updating of passwords by including an option to implement password rotation for complex passwords, including Application-to-Database and Application-to-Application passwords.
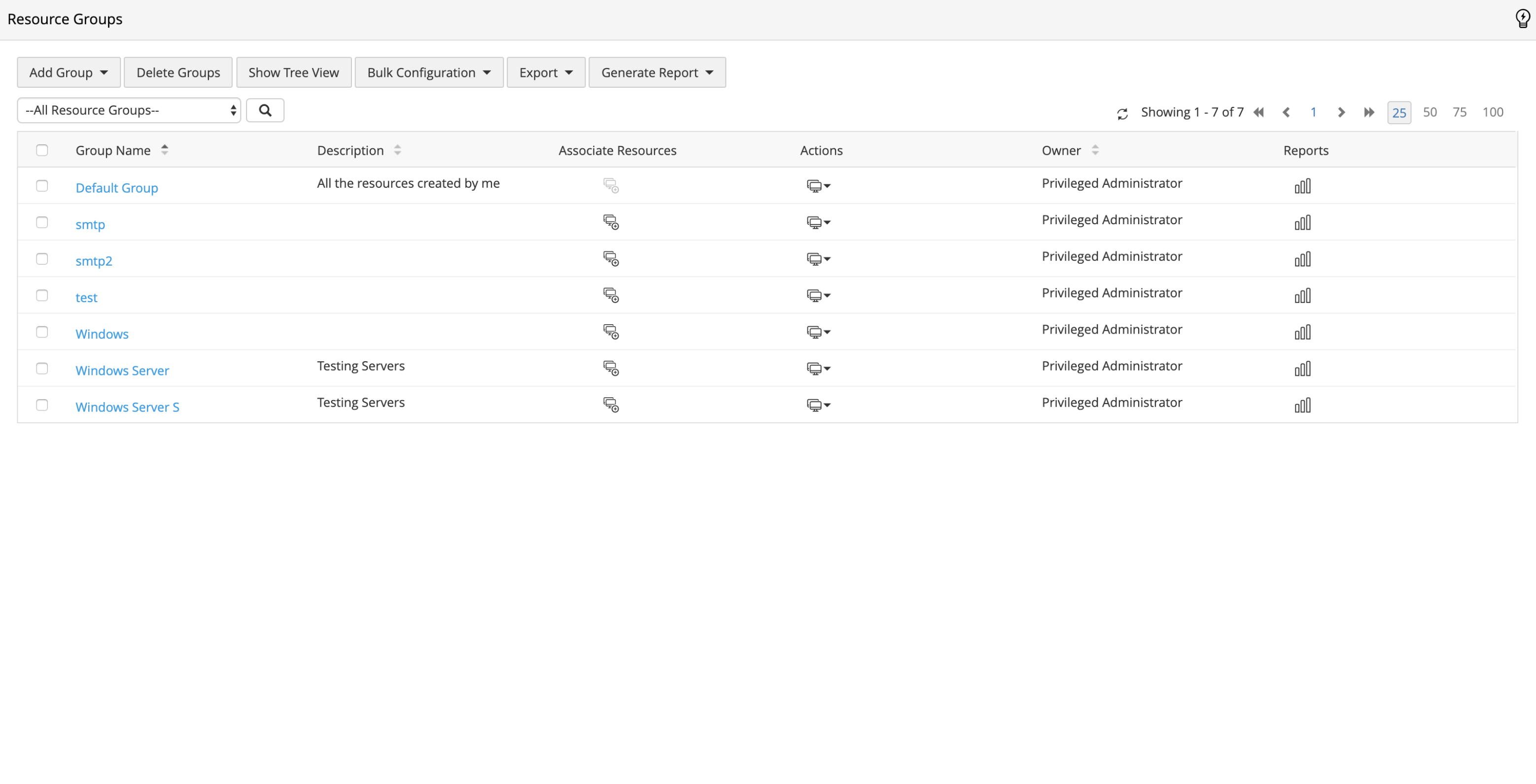
Effortless bulk actions for organized resource groups
PAM360 helps organize your passwords into criteria-based resource groups, which can dynamically update whenever resources matching the group criteria are added to, or removed from the network. Additionally, you can perform bulk operations, such as password sharing, rotation, and update, on select groups as required.