ManageEngine PAM360 offers agent-based, self-service privilege elevation controls for Linux environments, which enables users to execute a select set of commands with elevated privileges. These sets of commands provide standard users with administrative privileges to access files, directories, applications, and services. IT administrators can configure and enable self-service privilege elevation for resources to auto-approve user requests, and elevate privileges temporarily to carry out critical tasks.
Elevated permissions to execute allow-listed commands
In addition to administrative access to applications and files, self-service privilege elevation enables standard users to run allow-listed commands as a privileged account pre-configured in PAM360. These accounts come with substitute user, or "su" privileges, that enable users to easily switch to a privileged account to run critical commands.
For resources with self-service privilege elevation configured, users can run commands with elevated privileges using the "pamelevate" command prefix, regardless of the SSH client. In the absence of this prefix, end users, who launched SSH sessions via PAM360, will not be able to execute any privileged commands.
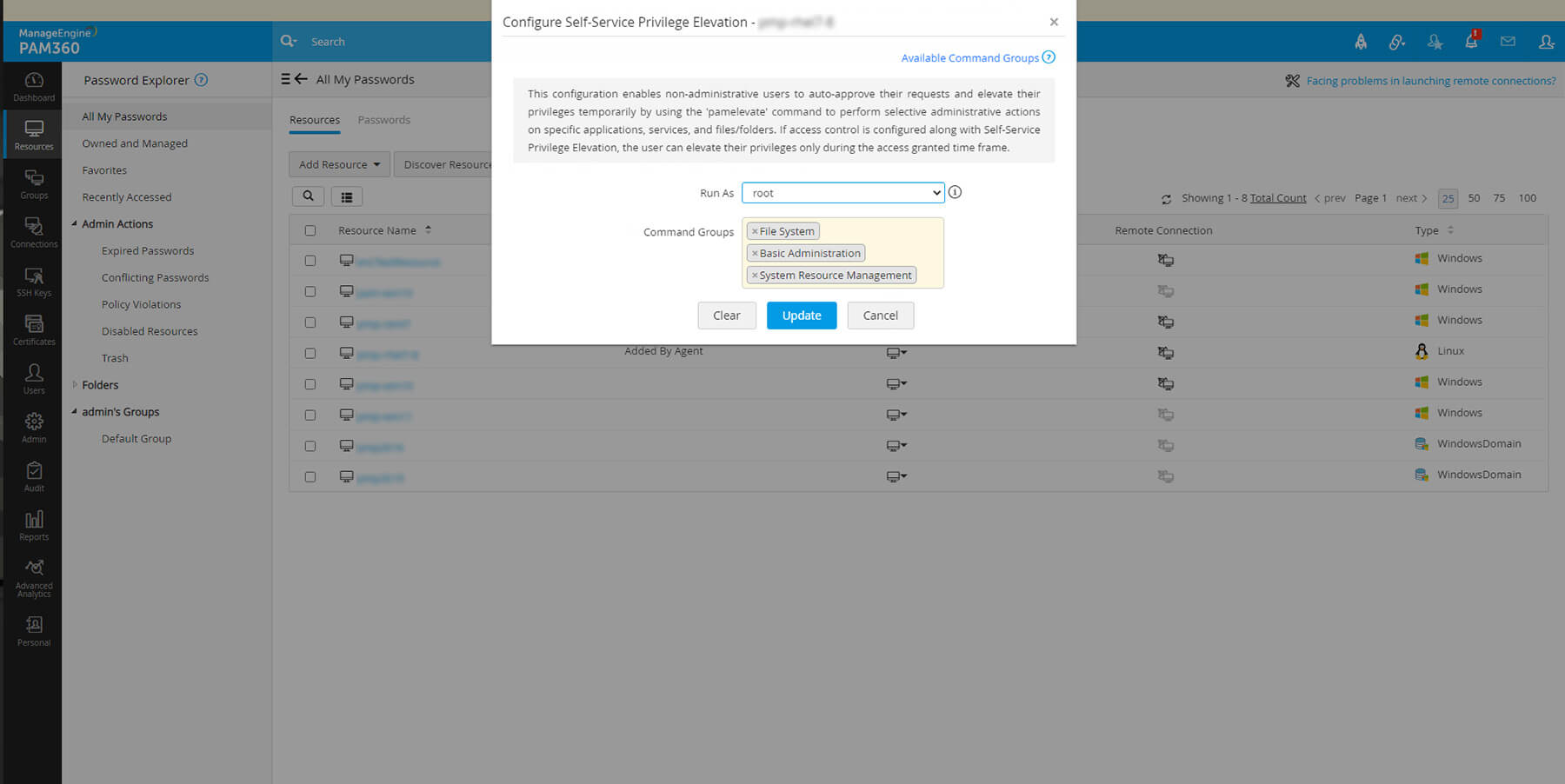
Time-limited administrative access to Linux resources
To ensure tighter security, access control workflows can be enabled for resources with self-service privilege elevation configured. This provides standard users with time-sensitive access to Linux resources, and allows them to execute commands with elevated privileges within their request window. Further, administrators can automatically revoke access and rotate the credentials of these resources, which prevents any unauthorized access attempts in future.
Comprehensive audits and reports on privilege elevation activities
PAM360 provides end-to-end audits pertaining to all privilege elevation activities, such as installing a Linux agent, command allow-listing and grouping, unauthorized command execution, configuring self-service privilege elevation, running commands with "pamelevate" privileges, and more.
This enables administrators to gain complete visibility into the activities performed by users with elevated privileges, and helps to effectively analyze access activities across privileged environments during security audits.