Organizations often manage critical devices running on Linux, Unix, and CISCO IOS which support SSH connections, many of which orchestrate daily business activities. IT teams restrict user access to such devices by granting access to only mission-critical employees. Organizations must enforce granular restrictions that prevent even privileged users from performing unauthorized actions. These actions are executed using SSH commands.
Without SSH command control, administrators have no control over what commands are executed by other privileged users. For example, any user may choose to delete files, remove a critical directory, or access an unauthorized file path at any point in time, and administrators are left with performing damage control due to the lack of a preventive measure.
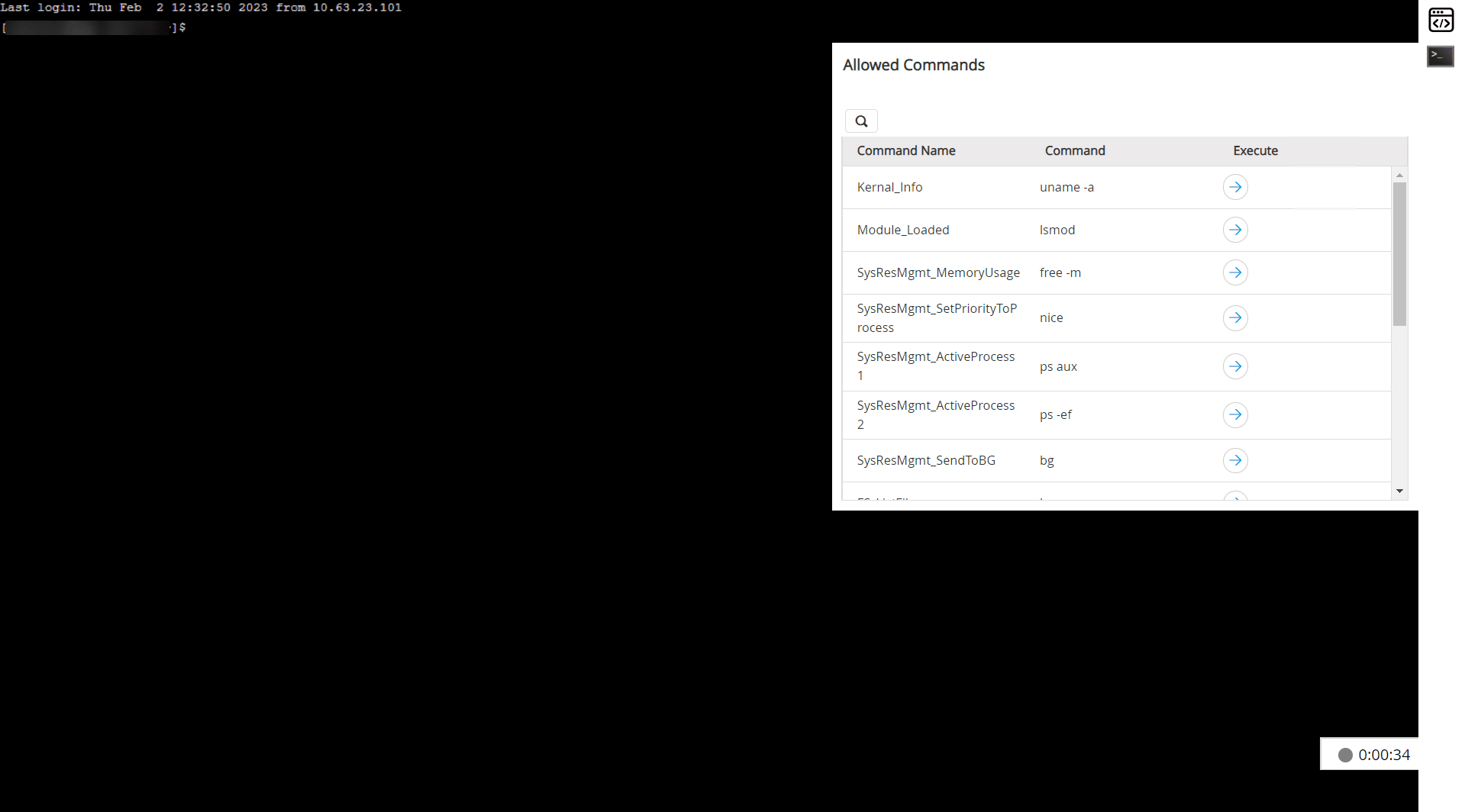
Using PAM360's SSH command filter, IT admins can create and enforce a list of commands that all or a select few employees can run on resources. At any point, PAM360 will prevent users from running commands that are not part of this list.