What is SSH and how it works?
Definition
SSH, or Secure Shell, is a protocol for remote administration, enabling users to manage their remote servers via the Internet. It employs cryptographic methods to guarantee that all communication with the remote server occurs in an encrypted fashion. This protocol establishes a means for authenticating a remote user, transmitting inputs from the client to the host, and forwarding the output back to the client securely.
The primary purposes of SSH are:
- Secure remote login: SSH allows users to log in to remote systems securely, encrypting the authentication and data transfer process. This is particularly important for administrators and users who need to access servers and systems remotely.
- Secure file transfer: SSH also supports secure file transfer protocols, such as SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol). This enables secure, encrypted file transfers between systems.
- Secure remote command execution: Administrators can execute commands on remote systems using SSH, providing a secure way to manage and maintain servers and network devices.
- Secure communication: Any data transmitted over SSH is encrypted, which ensures confidentiality and integrity. This makes it an excellent choice for protecting sensitive data during transmission.
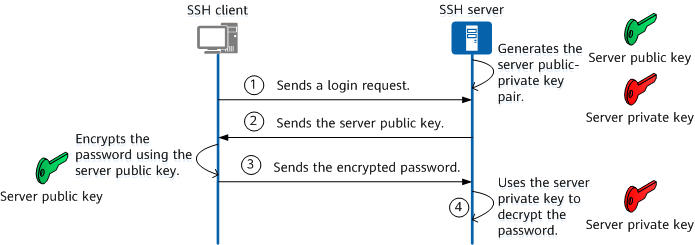
Workflow of SSH
In the process of establishing an SSH connection, both the client and server engage in the transport protocol. The following activities take place within this protocol:
- Key Exchange: This is responsible for authenticating the server and establishing the keys that will secure the connection.
- Encryption Algorithms: These are utilized to ensure data confidentiality through encryption.
- MAC Algorithms: They verify the integrity of the data by appending a message authentication code (MAC) to the packet.
Throughout these tasks, the client and server exchange information about the algorithms to be used for each operation. Once a mutually supported algorithm is identified, an SSH connection is successfully established.
Starting from builds 127131 onwards, in a freshly installed system, upon startup, all available ciphers will be automatically selected. This indicates that all the chosen ciphers will be used for SSH communication.
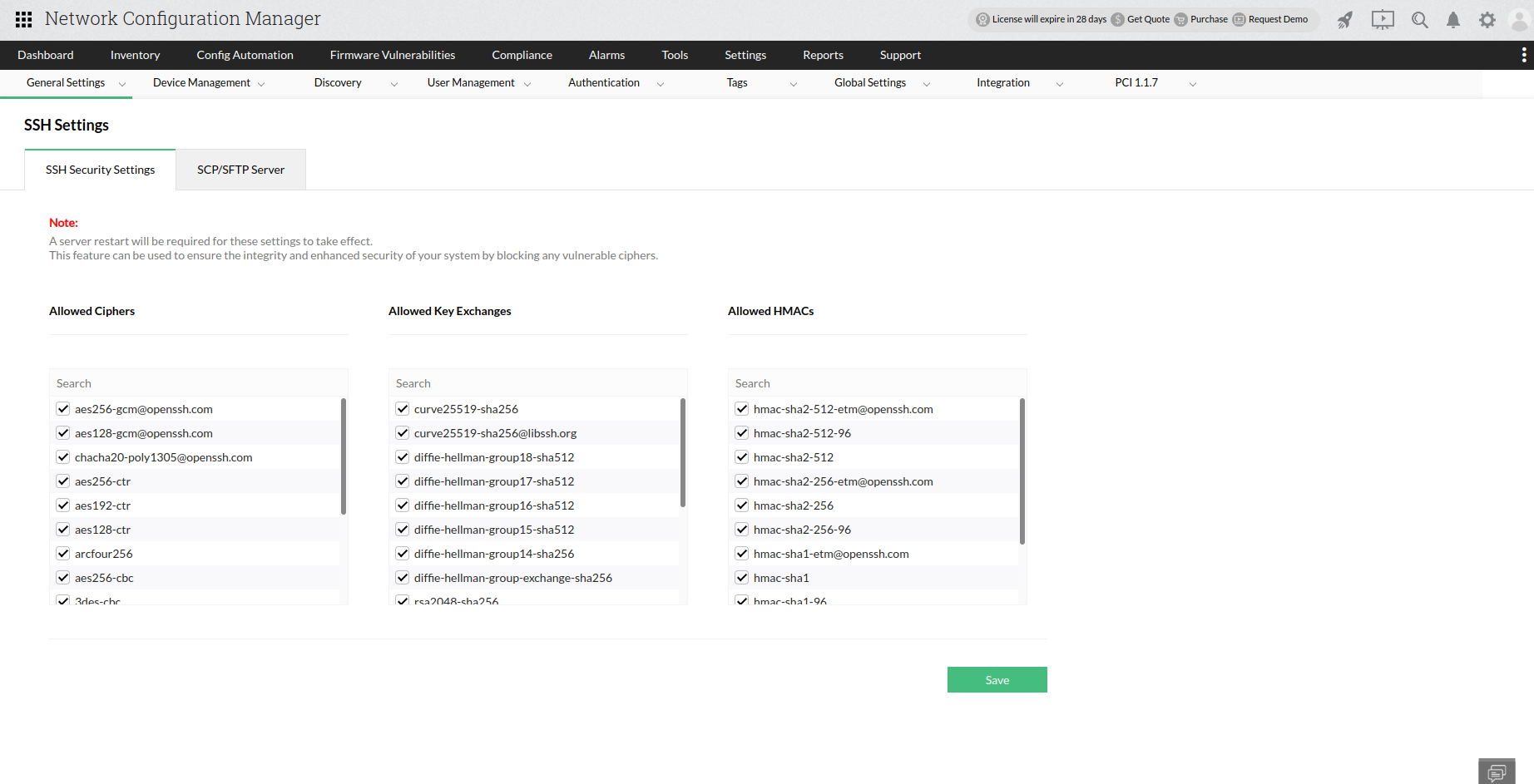
How to block weak ciphers used in SSH?
If weak ciphers are identified during a vulnerability scan in SSH, it is possible to block SSH ciphers, key exchanges, and HMACs by following the steps provided below:
- Go to "Settings" -> "General Settings" -> "SSH Settings".
- Under "Allowed Ciphers" / "Allowed Key Exchange" / "Allowed HMACS", unselect the ciphers to block.
- Click on "Save" button and restart NCM.
Note:
|
FAQ
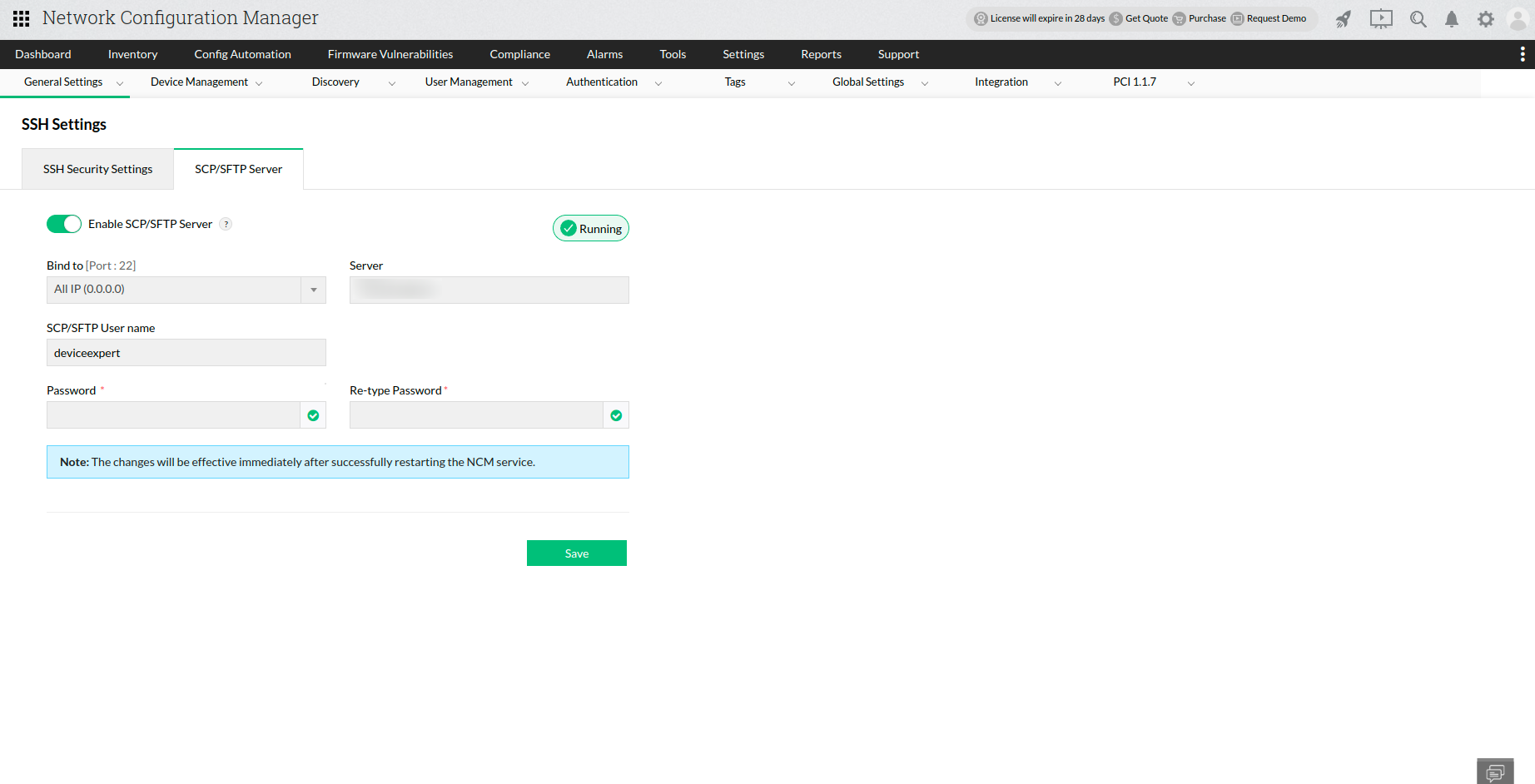
1. How can I disable the SCP/SFTP server?
- Go to Settings -> General Settings -> SSH Settings -> select SCP / SFTP Server tab
- Enter the required details
- Click on "Save" button and restart NCM.
Thank you for your feedback!