Compliance
Contents |
Overview
Government and industry regulations require IT organizations conform to some standard practices. To become compliant with the regulations such as CIS, SOX, HIPAA, and others, device configurations should conform to the standards specified. The standards could be anything - ensuring the presence or absence of certain strings, commands or values. Network Configuration Manager helps in automatically checking for compliance to the rules defined. Also, detailed reports on policy compliance and violations are generated.
How does compliance check work?
Users can define a set of rules specifying the mandatory requirements - what the configuration should contain and/or what it should not contain. The rules can be grouped and defined as 'Compliance Policy'. Each device or a group of devices can be associated with the required policy or policies. Upon backing up configurations, Network Configuration Manager will automatically scan the configuration for compliance to the policy defined and report violations. Users can also run manual compliance checks at any given instance. Additionally, compliance checks can be scheduled to run on a hourly, daily weekly and monthly basis.
How does compliance check benefit me?
Compliance check enables network administrators save a lot of time by automating the standards checking process. Besides it helps in
automating the process of ensuring that every device configuration in the network adheres to important security policies and best practices
ensuring that the configuration confirms to standard practices to satisfy Government and industry regulations
simplifying the requirements for standards compliance audit through comprehensive and intuitive reports
How do I enable compliance check?
Enabling compliance check starts with compliance policy creation, which is a three-step process:
1. Add a Rule
Define the line or lines that are to be either compulsorily present or should not be present in the configuration file. A typical example for a rule is checking the access list configuration or checking the community string. Decide what amounts to violation - presence or absence of a particular line or a set of lines in the configuration file
To add a rule,
Click on Compliance tab >> Rule >> "+" icon
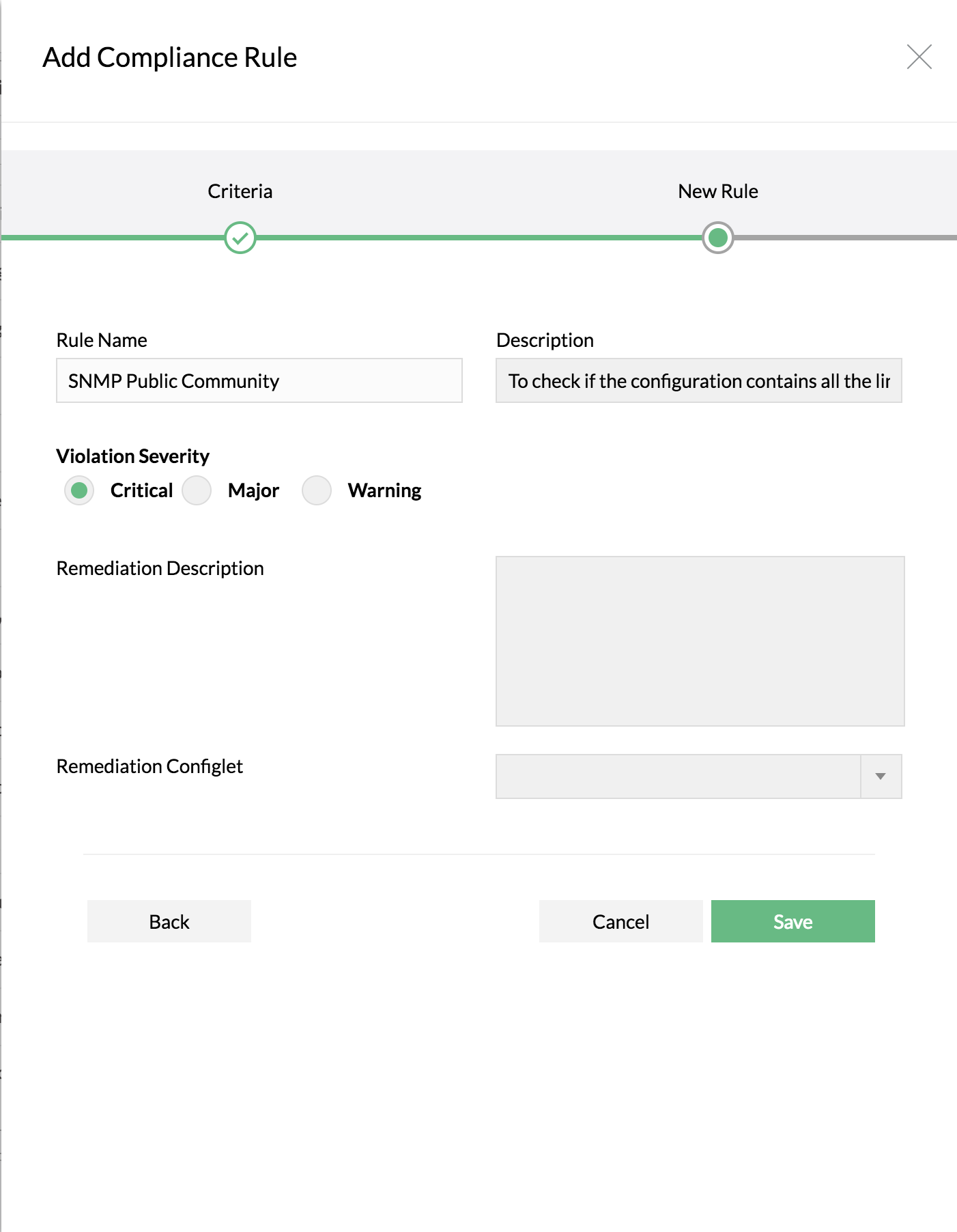
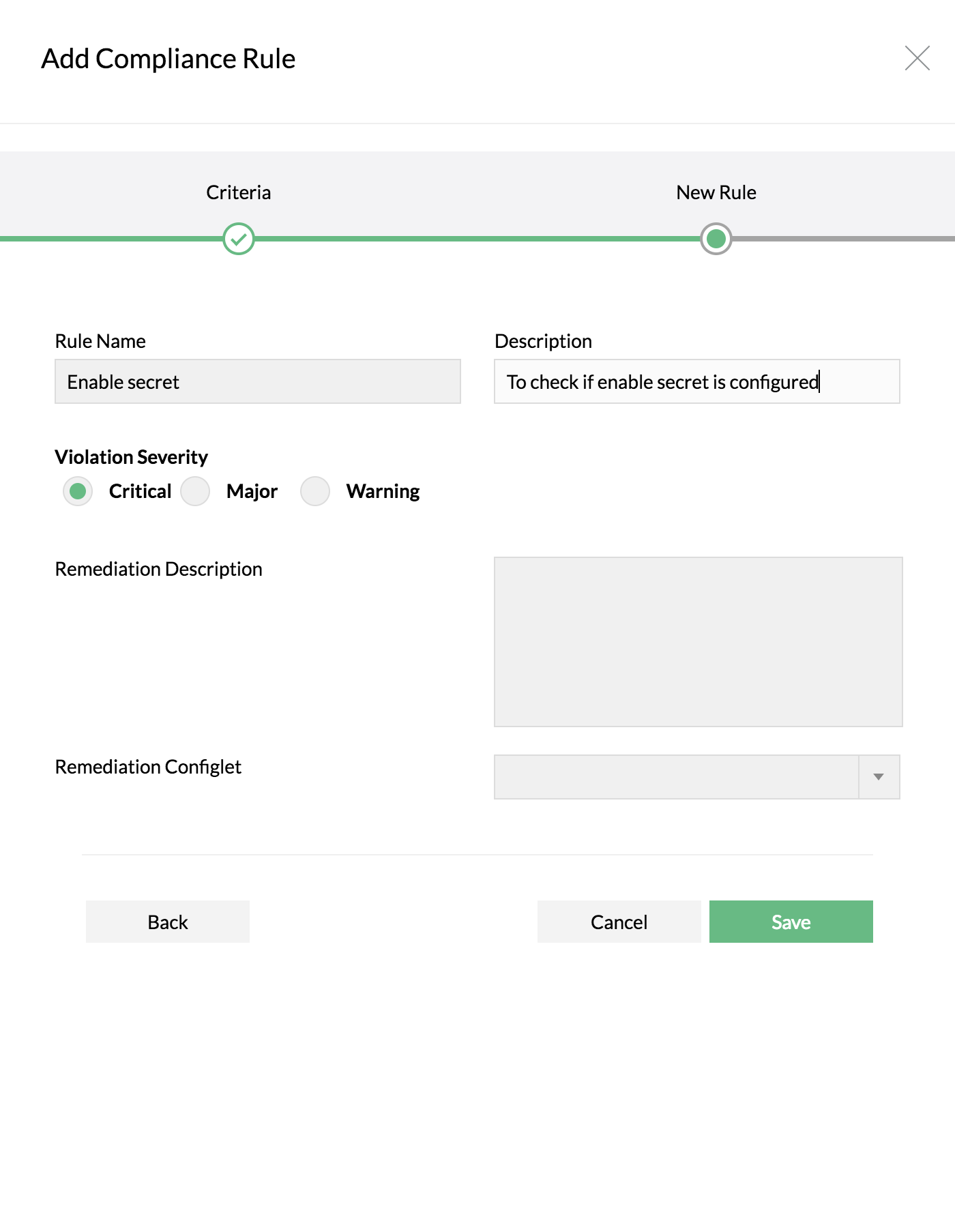
Enter Rule Name, Description and other details
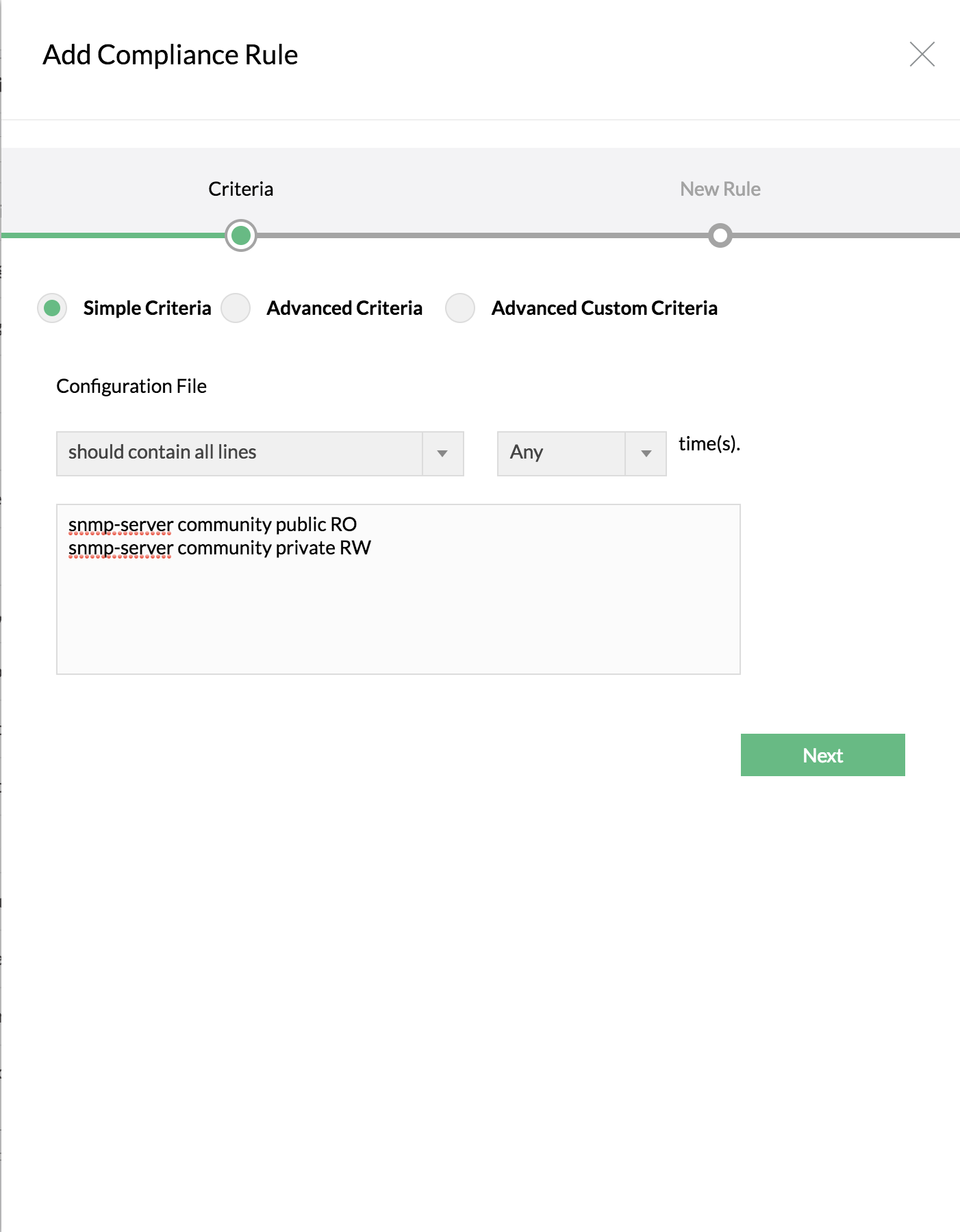
Select 'Simple Criteria' if your requirement is just to check for the presence or absence of a single line or a group of lines in the configuration file
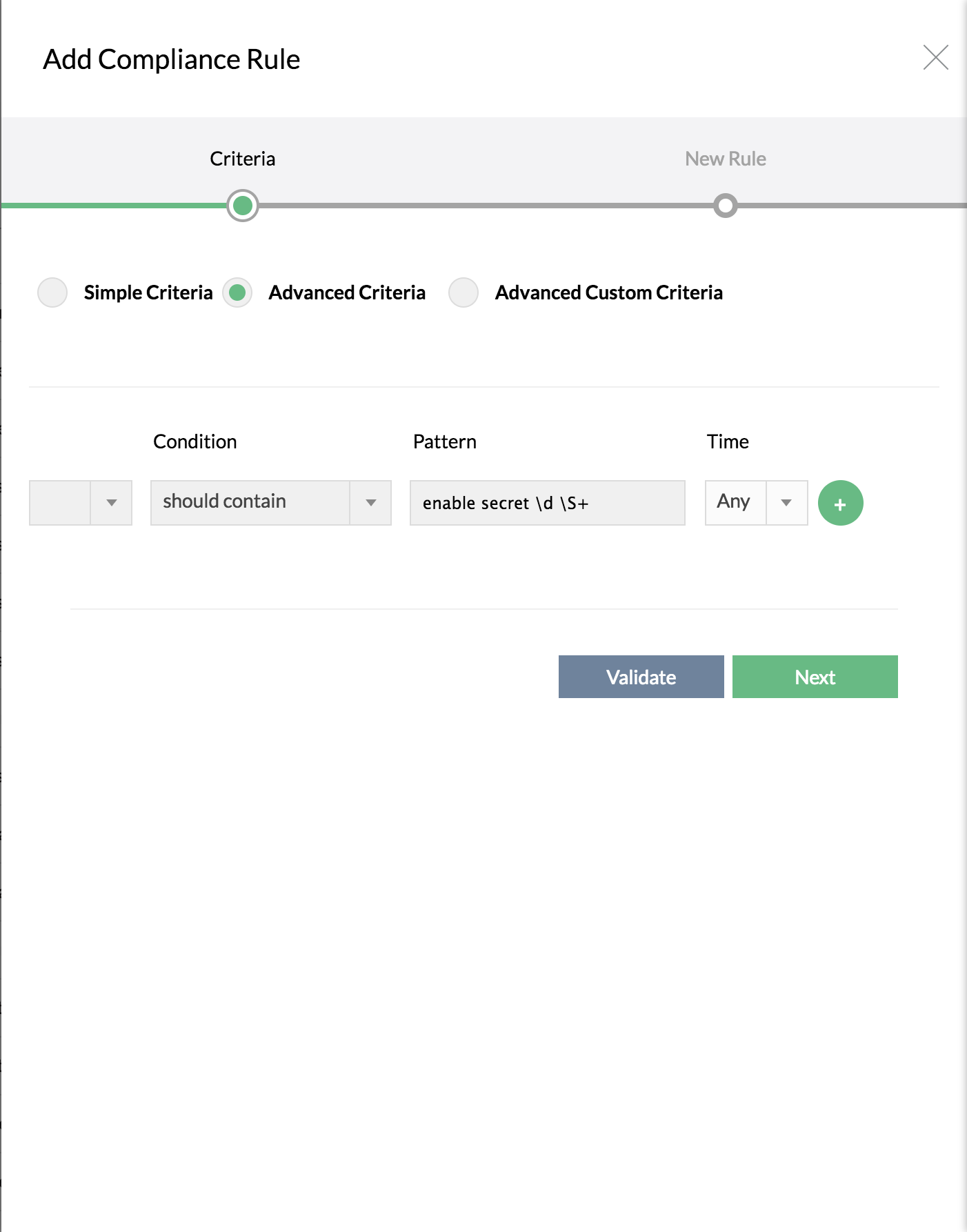
If you want to specify more complex criteria using Regular Expression, select 'Advanced Criteria' and then enter the line in the text field
If you want to define the beginning and the end of the required configuration blocks for selective compliance check, select 'Advanced custom Criteria'. This is just an extension of 'Advanced Criteria'
How to choose the required criteria?
Simple Criteria | Advanced Criteria | Advanced Custom Criteria |
To check for the presence or absence of a single line or a group of lines in the configuration file along with certain conditions. | To specify more complex criteria using regular expression along with certain conditions. You can also add any number of lines which can be separated by and / or.
| To check for the presence or absence of single line block in the configuration file or to define the beginning and the end (optional) of the required configuration blocks (multi line block) along with multiple additional criteria for selective compliance check. This also includes Advanced Criteria options as well.
|
Simple Criteria
To check for the presence or absence of configuration lines (single or group of lines) with certain conditions. Here are some of the conditions in Simple Criteria:
Criteria | Description | Example |
Should contain all lines | The configuration to be checked for compliance should contain all the lines specified by you. Even if a single line is not found, it will be pronounced as 'violation'. Network Configuration Manager goes about checking the lines (specified by you) one-by-one against the configuration file. It is not necessary that the lines should be present exactly in the same order as specified by you. Since the check is done line-by-line, it is enough if the all the lines are present anywhere in the configuration. | Criteria: Should contain all lines Configuration lines to check:
snmp-server community public RO snmp-server community private RW Violation: If any or all the lines are NOT present in the configuration file (irrespective of the order of the presence of the lines) |
Should not contain any line | Exactly opposite to the above. The configuration to be checked for compliance should NOT contain any of the lines specified by you. Even if a single line is found, it will be pronounced as 'violation'. Network Configuration Manager goes about checking the lines (specified by you) one-by-one against the configuration file. The order of the lines are not important. | Criteria: Should not contain any line Configuration lines to check:
snmp-server community public RO snmp-server community private RW
Violation: If any or all the lines are present in the configuration file (irrespective of the order of the presence of the lines) |
Should contain exact set | This is similar to 'Should contain all lines', but the difference is that the order of the lines is taken into consideration. If you have specified four lines, Network Configuration Manager will go about checking if all the four lines are present in the same order as specified. If the lines are not present exactly as specified, it will be pronounced as rule violation. | Criteria: Should contain exact set Configuration lines to check: snmp-server enable traps hsrp snmp-server enable traps config snmp-server enable traps entity
Violation: If all the lines are NOT present in the configuration file in the same order (and same set) as specified |
Should not contain exact set | Exactly opposite to the above. This is similar to 'Should not contain any line', but the difference is that the order of the lines is taken into consideration. If you have specified four lines, Network Configuration Manager will go about checking if the configuration contains the all the four lines in the same order as specified. If the lines are present exactly as specified, it will be pronounced as rule violation. | Criteria: Should not contain exact set Configuration lines to check: snmp-server enable traps hsrp snmp-server enable traps config snmp-server enable traps entity
Violation: If all the lines are present in the configuration file in the same order (and same set) as specified |
Advanced Criteria
You can make use of certain regular expressions in providing the criteria for checking the configuration for compliance along with certain conditions. You can provide multiple lines separated by and/or. Here are some of the conditions in Advanced Criteria:
Criteria | Description | Example |
Should contain | The configuration to be checked for compliance should contain the line matching the RegEx pattern specified by you. | Criteria: Should contain line(s) as per the RegEx pattern defined Configuration lines to check: snmp-server community public RO|RW Violation: If the line "snmp-server community public" followed by either "RO" or "RW" is NOT present |
Should not contain | The configuration to be checked for compliance should not contain the line matching the RegEx pattern specified by you. | Criteria: Should not contain line(s) as per the RegEx pattern defined Configuration lines to check: snmp-server community public RO|RW Violation: If the line "snmp-server community public" followed by either "RO" or "RW" is present |
Usage of AND/OR condition | Two or more RegEx patterns defined for 'Should Contain' or 'Should not contain' could be combined through AND/OR conditions | -- |
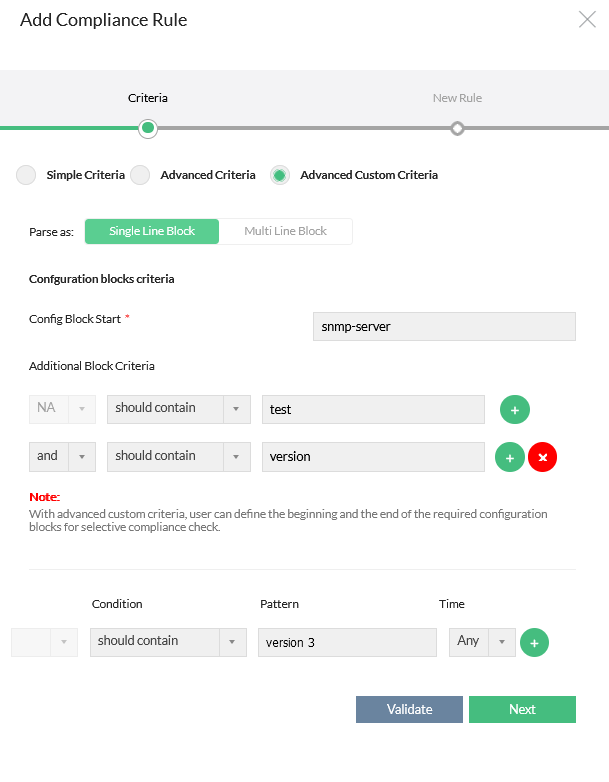
Advanced Custom Criteria
To check for the presence or absence of single line block in the configuration file or to define the beginning and the end (optional) of the required configuration blocks (multi line block) along with additional criteria for selective compliance check. In the Additional Block Criteria, you can add multiple lines separated by and /or. This also includes Advanced Criteria options as well, where you can add multiple lines separated by and / or.
Single Line Block:
Network Configuration Manager now supports Single Line Block as well where you can provide the start block of single line configuration alone along with additional block criteria to check the compliance status.
In Additional Block Criteria, you can also specify some extra conditions such as shutdown. This gives you the option to exclude any configuration block within the interface block specified above for compliance check. Here, you can provide multiple criteria separated by and / or.
Single Line Block example:
To identify a specific block, such as "snmp-server host test community version 2," and ensure its compliance in the given example of three single-line block configurations, please adhere to the following procedure:
- Input "snmp-server" in the "Config Block Start" field.
- In the Additional Block Criteria, from the Condition dropdown menu, choose "should contain" and enter "test" in the value field.
- Add another additional block criteria by clicking the "+" button.
- Select "and" as the logical operator and "should contain" from its respective dropdown menu.
- Enter "version" in the value field for the second additional block criteria.
By following these steps, you will identify the blocks that meet the specified criteria. For precise identification, you can define multiple additional block criteria. If needed, you can utilize the "should not contain" option within the additional block criteria.
Applying these steps will allow you to identify the desired blocks and conduct compliance checks accordingly.
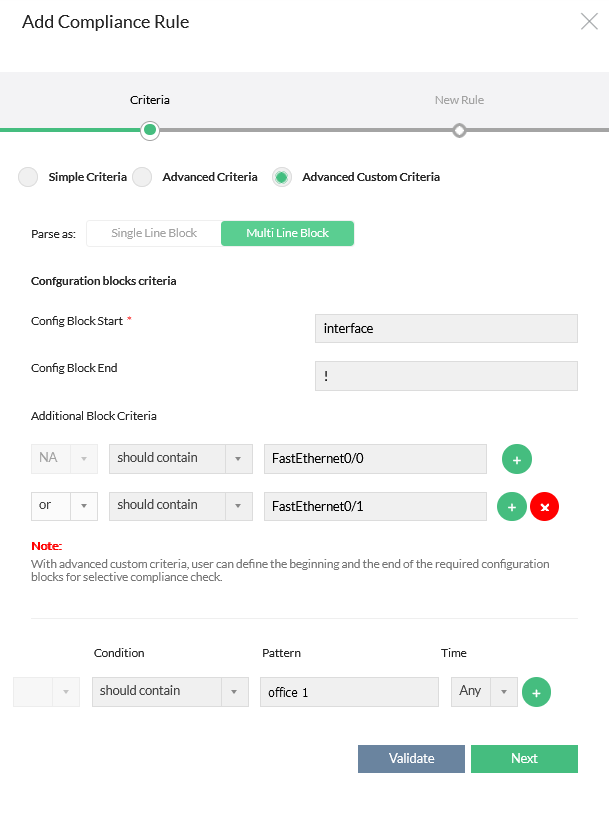
Multi Line Block:
An admin can simply define the starting and ending of the interface blocks (the end block is optional). Once this is done, Network Configuration Manager will split the configuration into configuration blocks and check for compliance. The compliance result for each block will be reported individually. Also, you can add multiple criteria in Additional Block Criteria separated by and / or.
Multi Line Block example:
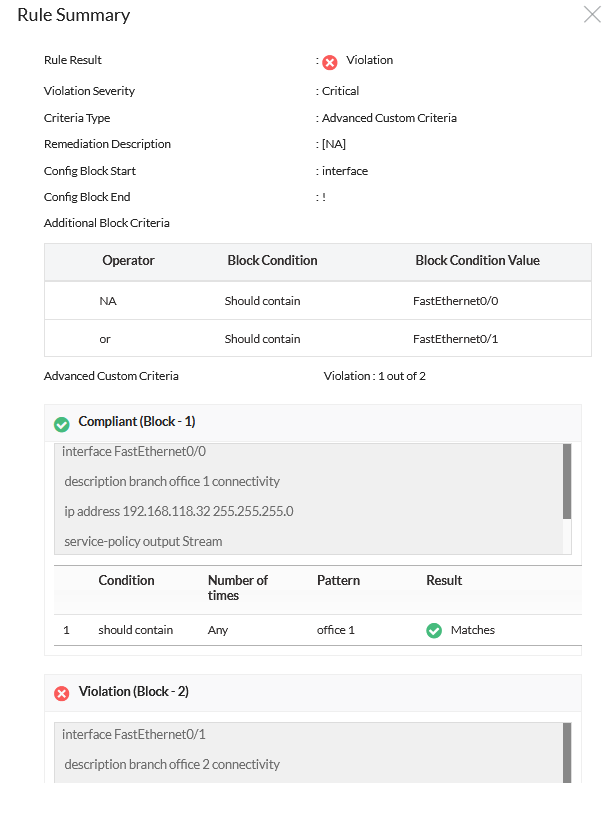
To identify and ensure compliance for the first block in the given example with two multi-line block configurations, please follow these steps:
- Input "interface" in the "Config Block Start" field.
- Input "!" in the "Config Block End" field (this is optional).
- In Additional Block Criteria, select "should contain" from the Condition dropdown menu and enter "FastEthernet0/0" in the value field.
- Add another additional block criteria by clicking the "+" button.
- Choose "or" as the logical operator and "should contain" from its respective dropdown menu.
- Enter "FastEthernet0/1" in the input field for the second additional block criteria.
By following these steps, you will identify the blocks that meet the specified criteria. For accurate identification, you can define multiple additional block criteria. If necessary, you can utilize the "should not contain" option within the additional block criteria.
Applying these steps will allow you to identify the desired blocks and conduct compliance checks accordingly.
Regular expression in compliance rule with examples
Regular Expression Patterns & DescriptionMatching specific characters
Characters inside square brackets can be used to match any of the characters mentioned therein. Example:
Matching a range of characters or numbers
Character range inside square brackets can be used to match any of the characters in the range specified therein. The character range could be alphabets or numbers. The matching is case-sensitive. Examples: [a-zA-Z] - This will match any character a through z or A through Z [0-9] - This will match any digit from 0 to 9
Other Specific Matches . a dot can be used to match any single character, including space. d to match any digit from 0 to 9 D to match any character other than a digit (0-9)
For more details, refer to the "Regular Expression Tutorials" of Java Tutorials. More Examples: |
Description | RegEx Pattern |
To check if enable secret is configured
| enable secret d S+ - to match any line containing the text "enable secret" followed by any single digit from 0 to 9 AND any character other than space appearing at least once |
To check if there is a 'public' community present in the configuration | snmp-server community public RO|RW - to match any line containing the text "snmp-server community public" followed by either "RO" or "RW" |
To check if logging to a syslog server has been configured | logging S+ - to match any line containing the text "logging" followed by an ip address |
How Network Configuration Manager checks compliance?
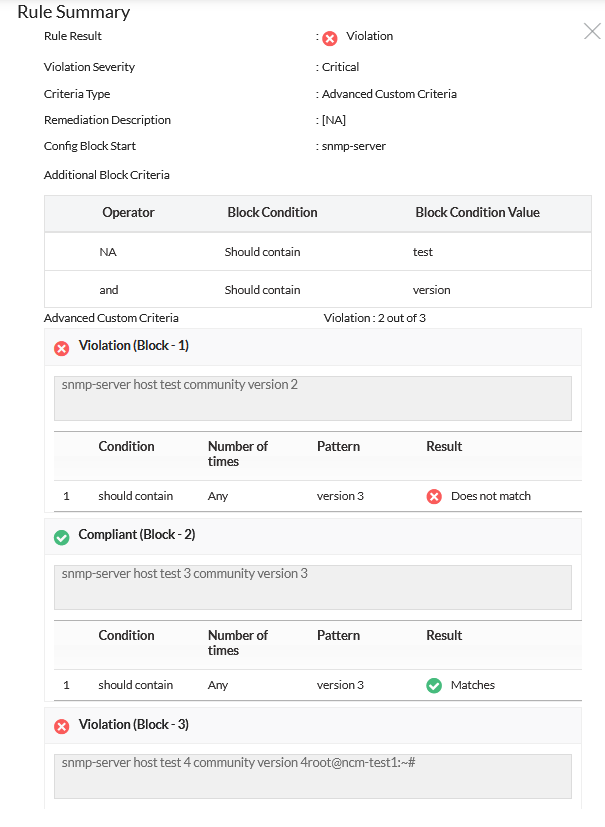
When you specify as above, all the blocks in the configuration starting with the word 'interface' and ending with ! will be tested for compliance to the criteria defined. The compliance result for each such configuration block will be presented individually. Overall result will be presented based on 'AND' of all the individual results. Even if only one configuration block shows violation, the overall result will be 'violation'. You can dig the report deep, analyze the individual results and find out what is wrong with the violations.
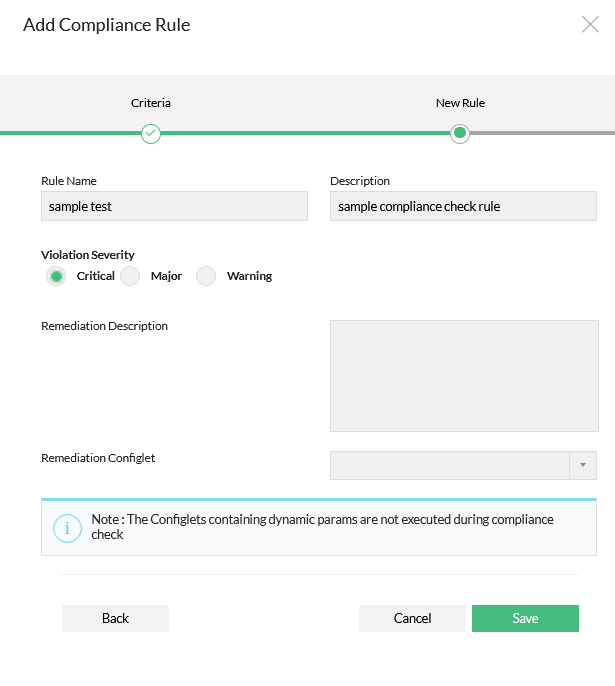
Finally specify the severity for violation. And select the remediation configlet and provide the remediation description if any.
Click on "Save"
2. Group the Rules
You can create many rules to cater to specific requirements. A 'Rule Group' refers to a collection of rules. Create a 'Rule Group' by selecting the required rules.
To create a rule group,
Click on Compliance tab>> Rule Group >> "+". Enter Rule Group Name, Description and other details
Select the rule/rules to be added to this group. Click "Save".
3. Create Policy
Once a rule group is created, you can go ahead to create the required compliance policy by selecting the required Rule Groups. Compliance check is done on all policies associated with a device.
To create a policy,
Click on Compliance tab>> Policies >> "+" Enter Policy Name, Description and other details
Specify the configuration file type (running/startup) against which the rules in this policy should be checked. For example, if you choose 'Running' only the current running configuration of the device will be checked for compliance with this policy
Select the 'Policy Violation Criteria' - i.e specify what amounts to policy violation - your policy might contain different rules with different severities; you can specify here as violation
- if any rule (irrespective of the severity is found violated) (OR)
- only critical or major rules are violated
- Select the required rule groups and click 'Save'
4. Associate Devices with Compliance Policy
After creating a policy, you need to associate it with the required devices/device groups.
To associate a policy with a device/devices,
Click on Compliance >> Policies. Click the link 'Associate devices' present against the policy
Select the devices / device groups and click 'Save'
Running Compliance Check
After associating a policy with a device or device group, you are ready to run compliance check.
To run compliance check for a single device,
Go to "Device Details" page of the specific device
Click "Run Compliance Check" present under "More Actions". You can even add a schedule for compliance check to be executed at a future point of time. To schedule this, goto Settings >> NCM >> All Schedules >> "Schedule Compliance Check" and fill in the details. When you schedule compliance check, you get the option to notify policy violations to desired recipients by email
To run compliance check for a device group,
Go to "Inventory" >> "Device Group" page and click device group for which compliance check has to be run
Click "Run Compliance Check" present under the box "More Actions". You can even add a schedule for compliance check to be executed at a future point of time. To schedule this, goto Settings >> NCM >> All Schedules >> "Schedule Compliance Check" and fill in the details. When you schedule compliance check, you get the option to notify policy violations to desired recipients by email
Running Adhoc Tests
During any stage of compliance policy creation (rule creation, rule group creation & policy creation), you can perform checks on adhoc basis to test the validity of the rule/rule group/policy added by you. The adhoc tests depict the results then and there. After adding a rule, you can perform adhoc test for a device/device group by clicking the "Adhoc Test" button present in Compliance tab >> Rule Similarly, adhoc tests can be performed for rule group from Compliance tab >> Rule Group GUI and for Policy from Compliance >> Policy GUI.
Thank you for your feedback!