FIPS compliance - ManageEngine Network Configuration Manager
FIPS (Federal Information Processing Standards) compliance is a set of standards developed by the US government that define specific requirements to ensure the security of sensitive and non-sensitive government data in computer systems and networks. It is mandatory for all US federal agencies and contractors that handle sensitive information. It ensures that federal agencies and private organizations that work with the government are using secure cryptographic methods and Key Management Systems (KMS) to protect sensitive data.
Certain encryption and key generation techniques are suggested to be used by the National Institute of Standards and Technology, in order for a tool to be FIPS compliant. The modules conforming to FIPS 140-2, are recognized and used by Federal Agencies of both the U.S. and Canada to protect sensitive information.
Now you can run Network Configuration Manager in FIPS compliant mode to adhering to the standards set by the US government. After enabling FIPS mode, Network Configuration Manager will become FIPS 140 -2 compliant, and can run only FIPS approved algorithms.
Pre-requisites to be FIPS compliant
For your whole environment/organization to be FIPS compliant, the following criteria should be met:
- FIPS mode can only be enabled in a fresh installation setup, so it is recommended to enable FIPS mode in a fresh installation instead of an upgraded Network Configuration Manager version.
- It is recommended to install Network Configuration Manager in a device with a FIPS compliant OS.
- Since only SNMP v3 credentials are FIPS compliant, change all the SNMP credentials to SNMP v3.
- The User's Mail server version should be compatible with TLSv1.2 or TLSv1.3. Only versions TLSv1.2 and TLSv1.3 will be supported if FIPS is enabled.
- All authentication methods and privacy methods in the FIPS compliant environment should be compliant to the FIPS 140-2 standards.
How to configure FIPS in Network Configuration Manager?
“FIPS mode” doesn’t make Network Configuration Manager more secure. It just stops you from using non secure algorithms that aren't FIPS compliant.
To enable FIPS Mode in Network Configuration Manager, follow the below steps,
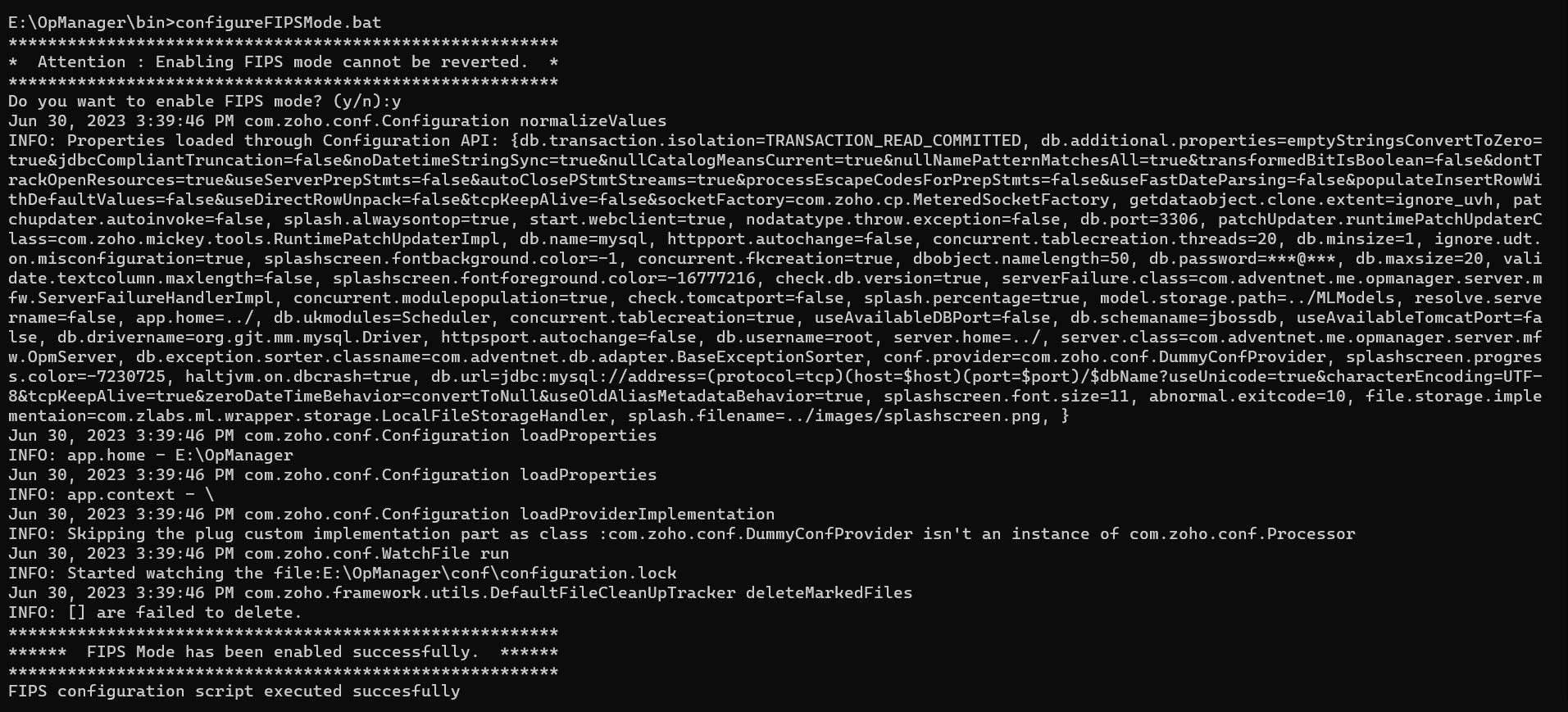
- Open command prompt in administrative mode, navigate to < ncmhome >/bin directory and then run configureFIPSMode.bat / configureFIPSMode.sh file. After successful execution of the batch, the trace "FIPS configuration updated successfully" will be seen.
Note:
- Network Configuration Manager's service should be stopped completely to enable FIPS mode. FIPS mode can only be enabled in a fresh installation, so it is recommended to fresh install the product.
What will change after FIPS mode has been enabled?
Once FIPS mode has been enabled, the following changes will take place in Network Configuration Manager:
Changes in device communication:
- All the communication taking place using SNMP v3 will become FIPS compliant.
- The weak ciphers used by CLI protocol will be disabled and only the FIPS compliant protocols will be used.
- REST API communication will follow FIPS compliance once it is enabled.
- FIPS mode once enabled cannot be disabled.
Communication with third-party integrations:
- For all third-party integrations, HTTPS with only strong ciphers that are FIPS compliant will be used to communicate.
Changes in certificates:
- pfx file format or PKCS12 certificate type are not supported in FIPS mode, so these are restricted. Instead BCFKS keystore type is used in an FIPS compliant version of Network Configuration Manager.
- The pre-configured SSL certificates will be converted to BCFKS format after enabling FIPS mode. The SSL certificate in BCFKS format with ".keystore" extension can be imported from the UI to enable SSL.
Internal communication:
- Data communication between central server and probe server from an application to a database will be secure and FIPS compliant.
- The failover migration process and data transmission between the primary and the secondary server will be encrypted as per FIPS compliance guidelines.
- Communication via mail server also will also follow FIPS compliance.
- Passwords and saved data will be FIPS compliant automatically.
Limitations of FIPS mode
- Radius authentication is not FIPS compliant, so it will be removed if FIPS mode was enabled.
- MSSQL with Windows authentication is not supported in FIPS mode.
- MSSQL versions 2014 & below are not supported in FIPS mode because some Non-FIPS compliance algorithms are used in those versions.
Thank you for your feedback!